Mobility Issues
... Define a minimum user profile, which can be known by the network operator, applications and services ? A consistent and global approach for user profile is needed ...
... Define a minimum user profile, which can be known by the network operator, applications and services ? A consistent and global approach for user profile is needed ...
E1_Act_2_2_5_in
... The displayed list can help identify data flow problems when trying to access a service such as a website. It can also be useful when performing tasks such as downloading data. If there are multiple websites (mirrors) available for the same file of data, one can trace each mirror to get a good idea ...
... The displayed list can help identify data flow problems when trying to access a service such as a website. It can also be useful when performing tasks such as downloading data. If there are multiple websites (mirrors) available for the same file of data, one can trace each mirror to get a good idea ...
CorportatePresentation(EN)_May07
... Telephone operators are beginning to suffer from revenue attacks on their traditional voice services by cellular network operators and VoIP-bypass phone service providers. ILECs, CLECs and Mobile phone operators compete relentlessly with each other being forced to offer constantly new services and t ...
... Telephone operators are beginning to suffer from revenue attacks on their traditional voice services by cellular network operators and VoIP-bypass phone service providers. ILECs, CLECs and Mobile phone operators compete relentlessly with each other being forced to offer constantly new services and t ...
How to configure Access Point as a Repeater by using
... addresses. The IPv4 default gateway address is the address of your wifi router. In this example, the computer has IP address 192.168.1.101 and the wifi router uses 192.168.1.1. This is a network using 192.168.1.x subnet. All the devices in the network have exactly same numbers for the first three oc ...
... addresses. The IPv4 default gateway address is the address of your wifi router. In this example, the computer has IP address 192.168.1.101 and the wifi router uses 192.168.1.1. This is a network using 192.168.1.x subnet. All the devices in the network have exactly same numbers for the first three oc ...
Chapter 1/Tutorial
... of incoming messages to the target system essentially forces it to shut down, thereby denying service to the system to legitimate users. select target break into hosts around the network .(botent) send packets toward target from compromised hosts ...
... of incoming messages to the target system essentially forces it to shut down, thereby denying service to the system to legitimate users. select target break into hosts around the network .(botent) send packets toward target from compromised hosts ...
Common Hardware Requirements for Computer Networking
... • A file server’s primary task is to make files available to users, although it also makes other resources available, including printers and plotters. • File service allows users to share the files on a server. The server PC can make its whole disk, certain directories, or certain files available. T ...
... • A file server’s primary task is to make files available to users, although it also makes other resources available, including printers and plotters. • File service allows users to share the files on a server. The server PC can make its whole disk, certain directories, or certain files available. T ...
Hacking - Computer Engineering
... Once we have a target, we need to get to know it better. Methods: War Dialing (to find out modem access) Network Mapping Vulnerability Scanning War Driving ...
... Once we have a target, we need to get to know it better. Methods: War Dialing (to find out modem access) Network Mapping Vulnerability Scanning War Driving ...
Slide - Computer Science
... Node places message including destination address on bus. This message is received by all other nodes All nodes check address to see if message is for them. • Nodes who are not addressed discard message ...
... Node places message including destination address on bus. This message is received by all other nodes All nodes check address to see if message is for them. • Nodes who are not addressed discard message ...
Network Topologies
... Introduction to Network – LAN, MAN and WAN – Transmission Media, Network Topologies – Protocols & Internet ...
... Introduction to Network – LAN, MAN and WAN – Transmission Media, Network Topologies – Protocols & Internet ...
Network Fundamentals
... • Must convert to public address for Internet access. • May also have many hosts sharing limited network addresses. – If only 1 network address, then service is called Port Address Translation - PAT ...
... • Must convert to public address for Internet access. • May also have many hosts sharing limited network addresses. – If only 1 network address, then service is called Port Address Translation - PAT ...
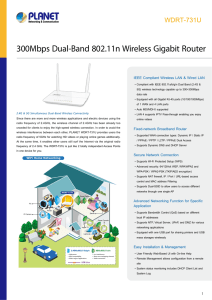
300Mbps Dual-Band 802.11n Wireless Gigabit Router
... e-mail and surf the Internet via the 2.4GHz band and simultaneously watch High-Definition (HD) video or any other multimedia application via 5GHz band. Furthermore, the WDRT-731U supports up to 300 + 300Mbps (download / upload) wireless transmitting rate of 2.4GHz and 5GHz for various wireless appli ...
... e-mail and surf the Internet via the 2.4GHz band and simultaneously watch High-Definition (HD) video or any other multimedia application via 5GHz band. Furthermore, the WDRT-731U supports up to 300 + 300Mbps (download / upload) wireless transmitting rate of 2.4GHz and 5GHz for various wireless appli ...
NMEICT-Univ-Campus Lan benefits
... infrastructure. • High performance : Maximizing bandwidth and allowing room for future applications • Reliability : Robust network infrastructure with focus on high reliability. • Risk Mitigation : Help mitigate potential risks ...
... infrastructure. • High performance : Maximizing bandwidth and allowing room for future applications • Reliability : Robust network infrastructure with focus on high reliability. • Risk Mitigation : Help mitigate potential risks ...
COEN 350
... Once we have a target, we need to get to know it better. Methods: War Dialing (to find out modem access) Network Mapping Vulnerability Scanning War Driving ...
... Once we have a target, we need to get to know it better. Methods: War Dialing (to find out modem access) Network Mapping Vulnerability Scanning War Driving ...
Communication and Network - International University of Japan
... “Extends a private network across a public network” (Internet) to allow remote users to send and receive data as if they are directly connected to private network. Establish a virtual point-to-point connection ...
... “Extends a private network across a public network” (Internet) to allow remote users to send and receive data as if they are directly connected to private network. Establish a virtual point-to-point connection ...
SinoCDN LinkEasy Solution
... within the LAN, thus it will not be affected even if the WAN link is congested or disconnected – For VLAN configuration, deploying LE-2000 in Hotel/Property premises would allow flexible control and ease of management by Service Provider – Our patented QoS feature can intelligently define and priori ...
... within the LAN, thus it will not be affected even if the WAN link is congested or disconnected – For VLAN configuration, deploying LE-2000 in Hotel/Property premises would allow flexible control and ease of management by Service Provider – Our patented QoS feature can intelligently define and priori ...
Welcome to CS 444/544!
... • An internetwork is typically comprised of many physical networks over which data travels • There are many different types of physical networks: – Circuit-switched vs. packet-switched networks – Local Area Networks (LAN) vs. Wide Area Networks ...
... • An internetwork is typically comprised of many physical networks over which data travels • There are many different types of physical networks: – Circuit-switched vs. packet-switched networks – Local Area Networks (LAN) vs. Wide Area Networks ...
Topics discussed in this section
... A protocol is a set of rules that govern data communications. A protocol defines what is communicated, how it is communicated, and when it is communicated. The key elements of a protocol are syntax, semantics, and timing. Syntax refers to the structure or format of the data, meaning the order in whi ...
... A protocol is a set of rules that govern data communications. A protocol defines what is communicated, how it is communicated, and when it is communicated. The key elements of a protocol are syntax, semantics, and timing. Syntax refers to the structure or format of the data, meaning the order in whi ...
Chapter 8 Intro
... • Switches and Bridges (Bridges are single-port switches) are smarter than hubs. • They make forwarding decisions based upon Mac (Hardware) Addresses • They are good because they block unwanted traffic. ...
... • Switches and Bridges (Bridges are single-port switches) are smarter than hubs. • They make forwarding decisions based upon Mac (Hardware) Addresses • They are good because they block unwanted traffic. ...
network - CCIT131
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
Cognitive Networking
... ◦ Security control - More wireless connection is available, confidential information may be stolen if message pass through bad communication channel ◦ Increase number of mobile device ...
... ◦ Security control - More wireless connection is available, confidential information may be stolen if message pass through bad communication channel ◦ Increase number of mobile device ...
Introduction to Mobile Computing - UF CISE
... – wold-wide deregulation and spectrum auctions – standard communication systems and air link interfaces ...
... – wold-wide deregulation and spectrum auctions – standard communication systems and air link interfaces ...