Set 1 File
... LAN system, but with lower bandwidth and is used in a wide area systems. - Three generations of Wireless WAN : the first one was analog and for voice only the second one was digital and for voice only the third one is digital and for both voice and data - IEEE 802.16 (WiMAX) is a standard for ...
... LAN system, but with lower bandwidth and is used in a wide area systems. - Three generations of Wireless WAN : the first one was analog and for voice only the second one was digital and for voice only the third one is digital and for both voice and data - IEEE 802.16 (WiMAX) is a standard for ...
Chapter 6 slides, Computer Networking, 3rd edition
... wireless link typically used to connect mobile(s) to base station also used as backbone link multiple access protocol coordinates link access various data rates, ...
... wireless link typically used to connect mobile(s) to base station also used as backbone link multiple access protocol coordinates link access various data rates, ...
Malwares – Types & Defense
... A software installed on a PC Part of OS to protect user machines Learning filter Annoying at times ...
... A software installed on a PC Part of OS to protect user machines Learning filter Annoying at times ...
- Caon
... representatives from ministry of industry, universities, companies). – It was very effective in disseminating projects results to communities who do not participate to commission events or scientific conferences. ...
... representatives from ministry of industry, universities, companies). – It was very effective in disseminating projects results to communities who do not participate to commission events or scientific conferences. ...
Computer Networks & The Internet
... – Hard for humans to deal with IP address. – DNS addresses are also used for user convenience which uses words instead of ...
... – Hard for humans to deal with IP address. – DNS addresses are also used for user convenience which uses words instead of ...
Document
... standards, and internet became reality • 1990’s - Commercial networks such as CompuServe and Prodigy became part of the internet; users of these networks could only communicate with those using the same service. ...
... standards, and internet became reality • 1990’s - Commercial networks such as CompuServe and Prodigy became part of the internet; users of these networks could only communicate with those using the same service. ...
domain name system
... together with long distance lines and gateways • Often one particular node on a LAN is set up to serve as a gateway between that LAN and other networks • Communication between networks is called internetworking with a lowercase “i” • The Internet, with a capital “I” the ultimate wide-area network, s ...
... together with long distance lines and gateways • Often one particular node on a LAN is set up to serve as a gateway between that LAN and other networks • Communication between networks is called internetworking with a lowercase “i” • The Internet, with a capital “I” the ultimate wide-area network, s ...
ppt - MMLab
... checking credentials so that only that user can install and modify the software running in its slice. 3. An owner trusts PLC to install software that is able to map network activity to the responsible slice. 4. PLC trusts owners to keep their nodes physically secure. ...
... checking credentials so that only that user can install and modify the software running in its slice. 3. An owner trusts PLC to install software that is able to map network activity to the responsible slice. 4. PLC trusts owners to keep their nodes physically secure. ...
IST101 - Test 6 – Ch 7,12 Test 6 consists of 50 questions drawn from
... What are keystroke loggers? A. Programs that disrupt the flow of information from the keyboard to the PC. B. Programs that delay information traveling from the keyboard to the PC. C. Programs that record everything that is typed on a computer and store it in a file to be retrieved later D. A log of ...
... What are keystroke loggers? A. Programs that disrupt the flow of information from the keyboard to the PC. B. Programs that delay information traveling from the keyboard to the PC. C. Programs that record everything that is typed on a computer and store it in a file to be retrieved later D. A log of ...
tia3_ppt_ch07 - School of Computer and Information Sciences
... • Software programs or hardware designed to close logical ports to invaders – A firewall is built into Windows XP – More robust firewalls are available from other vendors. – Firewalls are critical if you have an always-on broadband connection. ...
... • Software programs or hardware designed to close logical ports to invaders – A firewall is built into Windows XP – More robust firewalls are available from other vendors. – Firewalls are critical if you have an always-on broadband connection. ...
iwlan: an implementation model for high density smart intranet
... The IEEE 802.11 standard 3 defines the protocol and compatible interconnections of data communication equipment via the “air” (radio or infrared) in a local area network (LAN). It encompasses the physical (PHY) and the media access control (MAC) layers of the ISO seven-layer network model. The autho ...
... The IEEE 802.11 standard 3 defines the protocol and compatible interconnections of data communication equipment via the “air” (radio or infrared) in a local area network (LAN). It encompasses the physical (PHY) and the media access control (MAC) layers of the ISO seven-layer network model. The autho ...
A Home Mobile Healthcare System for Wheelchair Users
... Intelligent actuators: IR, RFID, Bluetooth etc. ...
... Intelligent actuators: IR, RFID, Bluetooth etc. ...
VOIP - Archive - Peter Cochrane
... We can only guess/imagine what our networks will be expected to support in the next decade/s…and it is the customers who decide and not the companies Peter Cochrane ...
... We can only guess/imagine what our networks will be expected to support in the next decade/s…and it is the customers who decide and not the companies Peter Cochrane ...
Networks
... speed Server – needs a lot of RAM and a fast hard drive Location of the files and software – if they are all on the server it creates a lot of traffic on the network. ...
... speed Server – needs a lot of RAM and a fast hard drive Location of the files and software – if they are all on the server it creates a lot of traffic on the network. ...
Campground and RV Park Wi-Fi Planning
... data wirelessly to and from wireless client devices such as smartphones, laptops, printers, tablets, other APs and client bridges to facilitate connectivity between these devices and the Internet or a network. Power-over-Ethernet4 (PoE) – A technology for wired Ethernet LANs that allows the electric ...
... data wirelessly to and from wireless client devices such as smartphones, laptops, printers, tablets, other APs and client bridges to facilitate connectivity between these devices and the Internet or a network. Power-over-Ethernet4 (PoE) – A technology for wired Ethernet LANs that allows the electric ...
Current State Of The Literature Related To The Proposed Topic
... The network topology is in general dynamic, because the connectivity among the nodes may vary with time due to node departures, new node arrivals, and the possibility of having mobile nodes. Hence, there is a need for efficient routing protocols to allow the nodes to communicate over multihop paths ...
... The network topology is in general dynamic, because the connectivity among the nodes may vary with time due to node departures, new node arrivals, and the possibility of having mobile nodes. Hence, there is a need for efficient routing protocols to allow the nodes to communicate over multihop paths ...
IPTV for People who AREN`T Engineers
... DO expect: •to have basic familiarity with what an IPTV system involves •to better appreciate the technical jargon used by your engineering team •a network engineer to be annoyed by all of your new questions after this session ...
... DO expect: •to have basic familiarity with what an IPTV system involves •to better appreciate the technical jargon used by your engineering team •a network engineer to be annoyed by all of your new questions after this session ...
Accounts and Authentication
... Kerberos requires the clocks of the involved hosts to be synchronized. The tickets have time availability period and, if the host clock is not synchronized with the clock of Kerberos server, the authentication will fail. Secret keys for all users are stored on the central server, a compromise of ...
... Kerberos requires the clocks of the involved hosts to be synchronized. The tickets have time availability period and, if the host clock is not synchronized with the clock of Kerberos server, the authentication will fail. Secret keys for all users are stored on the central server, a compromise of ...
Technology Directions for IP Infrastructure
... network-specific egress label of a packet, and then uses this for each hop-by-hop switching decision • Originally thought of as a faster switching technology than IP-level switching. This is not the case • Now thought of as a more robust mechanism of network-specific encap than “IP in IP”, or “IP in ...
... network-specific egress label of a packet, and then uses this for each hop-by-hop switching decision • Originally thought of as a faster switching technology than IP-level switching. This is not the case • Now thought of as a more robust mechanism of network-specific encap than “IP in IP”, or “IP in ...
Higher Computing Unit 1 – Peripherals and Interfaces
... A local council sets up an intranet within their headquarters. Internet access is made available through a web server on the intranet. Apart from allowing shared Internet access, state two functions that the web server is likely to provide the local council. ...
... A local council sets up an intranet within their headquarters. Internet access is made available through a web server on the intranet. Apart from allowing shared Internet access, state two functions that the web server is likely to provide the local council. ...
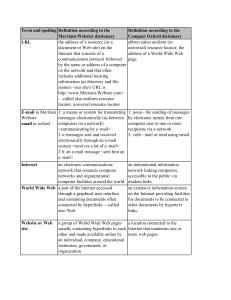
Table 9.1 Spelling and definitions.pdf
... networks and organizational computer facilities around the world World Wide Web a part of the Internet accessed through a graphical user interface and containing documents often connected by hyperlinks —called also Web ...
... networks and organizational computer facilities around the world World Wide Web a part of the Internet accessed through a graphical user interface and containing documents often connected by hyperlinks —called also Web ...