Mobile RFID of Wireless Mesh Network for Intelligent Safety Care
... multiple SSIDs, allowing the creation of Virtual Access Points-partitioning a single physical access point into several logical access points, each of which can have a different set of security and network settings. B. ...
... multiple SSIDs, allowing the creation of Virtual Access Points-partitioning a single physical access point into several logical access points, each of which can have a different set of security and network settings. B. ...
Dr. Larry Stotts - Freedom Technologies Inc
... expressed or implied, of the Defense Advanced Research Projects Agency or the Department of Defense Approved for Public Release, Distribution Unlimited ...
... expressed or implied, of the Defense Advanced Research Projects Agency or the Department of Defense Approved for Public Release, Distribution Unlimited ...
Binod_nepalPresentation
... Quality of Service Issues Compressed RTP As networks evolve to provide more bandwidth, applications, services and consumers of those applications all compete for that bandwidth. As for wireless networks with their high bit error rates and high latency, it is difficult to attain those high bandw ...
... Quality of Service Issues Compressed RTP As networks evolve to provide more bandwidth, applications, services and consumers of those applications all compete for that bandwidth. As for wireless networks with their high bit error rates and high latency, it is difficult to attain those high bandw ...
Sisteme cu microprocesoare
... of symbolic names for network addresses (IP addresses) - NFS (Network File System) - is a mapping service that allows remote file folders in your local directory, this service provides a uniform access to files regardless of their location - NIS (Network Information System) - is a service providing ...
... of symbolic names for network addresses (IP addresses) - NFS (Network File System) - is a mapping service that allows remote file folders in your local directory, this service provides a uniform access to files regardless of their location - NIS (Network Information System) - is a service providing ...
Part I: Introduction - Northwestern University
... interference possible: channel can be same as that chosen by neighboring AP! ...
... interference possible: channel can be same as that chosen by neighboring AP! ...
Computers in Society
... UUCP. It was a distributed network and content was not centralized. It was the start of recreational use of the ...
... UUCP. It was a distributed network and content was not centralized. It was the start of recreational use of the ...
The protocol
... •Multiple host, multiple channels? •TDM and FDM (fixed allocation) •impractical •not scaleable ...
... •Multiple host, multiple channels? •TDM and FDM (fixed allocation) •impractical •not scaleable ...
Networking Vocabulary 2 Directions: 1. Go to Word. 2. Insert a Blank
... Client –Any part of the network that receives data such as a workstation Communications media – How nodes in a network are connected together (by cable, by fiber optics, radio waves, etc.) Computer network – Computers connected together for the purpose of sharing information and resources Host – Any ...
... Client –Any part of the network that receives data such as a workstation Communications media – How nodes in a network are connected together (by cable, by fiber optics, radio waves, etc.) Computer network – Computers connected together for the purpose of sharing information and resources Host – Any ...
Crowd Management System
... Temperature and humidity information also collected periodically People count will be decided at server, by subtracting the 2 counts Suitable contraption will be designed to ensure no other light gets to sensor Advantage over single entry/exit Single entry/exit system may not be able to hand ...
... Temperature and humidity information also collected periodically People count will be decided at server, by subtracting the 2 counts Suitable contraption will be designed to ensure no other light gets to sensor Advantage over single entry/exit Single entry/exit system may not be able to hand ...
Software Defined Networks - Informatica
... Networks are Hard to Manage ! Operating a network is expensive – More than half the cost of a network – Yet, operator error causes most outages ...
... Networks are Hard to Manage ! Operating a network is expensive – More than half the cost of a network – Yet, operator error causes most outages ...
Subnet and Packet Tracer Task
... administrator. Your first assignment is to setup the local network and make everything function correctly. You have decided to first build your simulated network using packet tracer and test the setup before modifying the live network. ...
... administrator. Your first assignment is to setup the local network and make everything function correctly. You have decided to first build your simulated network using packet tracer and test the setup before modifying the live network. ...
Network Registration – Summer 2014 - Orientation
... All computing devices connecting to the University of Chicago network within the residence halls must complete the network registration process before getting full internet access. Registration is an important part of network security, and can additionally help you retrieve your computer if it is lo ...
... All computing devices connecting to the University of Chicago network within the residence halls must complete the network registration process before getting full internet access. Registration is an important part of network security, and can additionally help you retrieve your computer if it is lo ...
Plutarch
... Where are these IFs going to run? IFs live on gateway nodes – these nodes must be accessible from both contexts involved. Small matter of deployment. ;) Need a platform for gateways to execute IFs in a reliable, accountable manner… (Have I mentioned XenoServers?) ...
... Where are these IFs going to run? IFs live on gateway nodes – these nodes must be accessible from both contexts involved. Small matter of deployment. ;) Need a platform for gateways to execute IFs in a reliable, accountable manner… (Have I mentioned XenoServers?) ...
Connectivity, the Wireless Revolution, and Communications
... Chapter 7 Connectivity, The Wireless Revolution, and Communications 2. The Wireless Revolution ...
... Chapter 7 Connectivity, The Wireless Revolution, and Communications 2. The Wireless Revolution ...
ECE 117-2426
... Management (IEM) in the consumers' side. For an IEM system we need to knowledge, but how knowledge obtained? Data collection is the first step to knowledge and whatever data is a more comprehensive, decisions are more accurate. In the data collection layer, WSN can help you to obtain the best result ...
... Management (IEM) in the consumers' side. For an IEM system we need to knowledge, but how knowledge obtained? Data collection is the first step to knowledge and whatever data is a more comprehensive, decisions are more accurate. In the data collection layer, WSN can help you to obtain the best result ...
Event Based Routing In Delay Tolerant Networks
... • Delay And Disruption Tolerant Networking, By Stephen Farrell and Vinny Cahill. ...
... • Delay And Disruption Tolerant Networking, By Stephen Farrell and Vinny Cahill. ...
Enterprise Solutions for Small Business
... businesses install Voice over Internet Protocol networks for voice applications such as telephony, voice, instant messaging, and teleconferencing. A well-conceived VoIP network allows customers to simplify their networks and improve IP telephony. ...
... businesses install Voice over Internet Protocol networks for voice applications such as telephony, voice, instant messaging, and teleconferencing. A well-conceived VoIP network allows customers to simplify their networks and improve IP telephony. ...
Convergence of Wireline IP and Wireless Networks
... Wireless – Wireline Convergence Voice convergence is already happening with the introduction of Unified Communication. That trend will continue with SIP forming a common foundation. Data convergence is following WiFi and Edge/GPRS deployment. Hosted ...
... Wireless – Wireline Convergence Voice convergence is already happening with the introduction of Unified Communication. That trend will continue with SIP forming a common foundation. Data convergence is following WiFi and Edge/GPRS deployment. Hosted ...
Introduction - Jigar Pandya
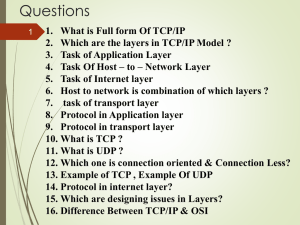
... 2. Which are the layers in TCP/IP Model ? 3. Task of Application Layer 4. Task Of Host – to – Network Layer 5. Task of Internet layer 6. Host to network is combination of which layers ? 7. task of transport layer 8. Protocol in Application layer 9. Protocol in transport layer 10. What is TCP ? 11. W ...
... 2. Which are the layers in TCP/IP Model ? 3. Task of Application Layer 4. Task Of Host – to – Network Layer 5. Task of Internet layer 6. Host to network is combination of which layers ? 7. task of transport layer 8. Protocol in Application layer 9. Protocol in transport layer 10. What is TCP ? 11. W ...
2016-10 Computer Network and Internet Access Policy
... information. Users are cautioned that many of these pages include offensive, sexually explicit and inappropriate material. In general, it is difficult to avoid at least some contact with this material while using the lnternet. Even innocuous search requests may lead to sites with highly offensive co ...
... information. Users are cautioned that many of these pages include offensive, sexually explicit and inappropriate material. In general, it is difficult to avoid at least some contact with this material while using the lnternet. Even innocuous search requests may lead to sites with highly offensive co ...
Networking Basics - Henry County Schools
... Fiber optic cable – used by much of the internet to send data quickly over long distances underground ...
... Fiber optic cable – used by much of the internet to send data quickly over long distances underground ...