PPT
... Relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers, 802.11 access points ...
... Relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers, 802.11 access points ...
Securitizing the Internet – Political Economy Analysis
... Downstream liability vs. No-liability (virtual pollution laws) Enforcement – Public vs. Self help (corporate – ISP, IP owner, conditional) Service providers’ role – Liability vs. Immunity (vis-à-vis user, but regulated) {Fair information practices vs. Contractual freedom} ...
... Downstream liability vs. No-liability (virtual pollution laws) Enforcement – Public vs. Self help (corporate – ISP, IP owner, conditional) Service providers’ role – Liability vs. Immunity (vis-à-vis user, but regulated) {Fair information practices vs. Contractual freedom} ...
ppt
... – Stronger error detection and recovery • More powerful error detection codes • Link-layer retransmission of corrupted frames ...
... – Stronger error detection and recovery • More powerful error detection codes • Link-layer retransmission of corrupted frames ...
Troubleshooting your PC - Hill City SD 51-2
... A network links computers for communicating and sharing information and resources. A network must provide ...
... A network links computers for communicating and sharing information and resources. A network must provide ...
7845i, Data Sheet
... (supported through DHCP services on most routers and firewalls) • Highest levels of data security are assured: - 1,024 bit encryption standard - Two-way authentication is automatically applied - No key exchange occurs for maximum data protection - Change central station receiver IP address without n ...
... (supported through DHCP services on most routers and firewalls) • Highest levels of data security are assured: - 1,024 bit encryption standard - Two-way authentication is automatically applied - No key exchange occurs for maximum data protection - Change central station receiver IP address without n ...
Chapter 2 The Internet and Multimedia
... Three inventions that spread the use of the Internet were: The personal computer (early 1980s) The World Wide Web (1989) The browser (1991) ...
... Three inventions that spread the use of the Internet were: The personal computer (early 1980s) The World Wide Web (1989) The browser (1991) ...
Internet - Introduction
... infrastructure for the use of E-mail, bulletin boards, file archives, hypertext documents, databases and other computational resources. ...
... infrastructure for the use of E-mail, bulletin boards, file archives, hypertext documents, databases and other computational resources. ...
ppt
... – Hold onto packets until another hop can take it from you – Eventually reach its destination ...
... – Hold onto packets until another hop can take it from you – Eventually reach its destination ...
Network Engineer
... Work with the network manager to coordinate the management of a wide area network consisting of multi‐ platform voice, video and data. Administration of an enterprise network environment including the installation, monitoring, maintenance, support, and optimization of all network hardware, sof ...
... Work with the network manager to coordinate the management of a wide area network consisting of multi‐ platform voice, video and data. Administration of an enterprise network environment including the installation, monitoring, maintenance, support, and optimization of all network hardware, sof ...
Definition of the characteristics of telecommunication and network
... Today there are many portable device users world-wide. Those users need wireless access to some kind of personal, local or wide network in order to use their devices effectively. In a wireless LAN the connection between devices is accomplished by the use of a medium such as Radio Frequency (RF) or I ...
... Today there are many portable device users world-wide. Those users need wireless access to some kind of personal, local or wide network in order to use their devices effectively. In a wireless LAN the connection between devices is accomplished by the use of a medium such as Radio Frequency (RF) or I ...
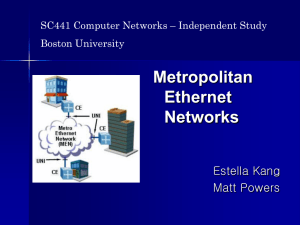
Metro Ethernet Networks
... Scalability Network Reliability Co-existence with existing infrastructure Topological flexibility Reduction in operational and network costs ...
... Scalability Network Reliability Co-existence with existing infrastructure Topological flexibility Reduction in operational and network costs ...
Wireless and Mobile Networks Reading: Sec7ons 2.8 and 4.2.5 Mike Freedman
... – Today’s users tolerate disrup7ons as they move – … and applica7ons try to hide the effects – Tomorrow’s users expect seamless mobility ...
... – Today’s users tolerate disrup7ons as they move – … and applica7ons try to hide the effects – Tomorrow’s users expect seamless mobility ...
powerpoint
... lab (and all of the ICT I labs) are considered LAN segments because the computers in each lab are connected together in a kind of smaller network. • The computer workstations in each ICT I lab and each ICT II lab are connected by ethernet cables. The cables plug into the network card in each compute ...
... lab (and all of the ICT I labs) are considered LAN segments because the computers in each lab are connected together in a kind of smaller network. • The computer workstations in each ICT I lab and each ICT II lab are connected by ethernet cables. The cables plug into the network card in each compute ...
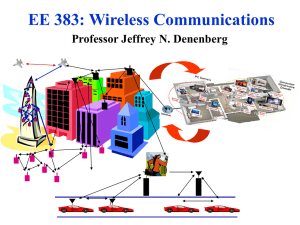
Wireless Communications Research Overview
... Adaptive OFDM /MIMO in 20/40 MHz (2-4 antennas) Speeds up to 600Mbps, approx. 200 ft range Other advances in packetization, antenna use, etc. ...
... Adaptive OFDM /MIMO in 20/40 MHz (2-4 antennas) Speeds up to 600Mbps, approx. 200 ft range Other advances in packetization, antenna use, etc. ...
slides - IEEE HPSR 2012
... The core of Google’s Infrastructure The core of Google’s Infrastructure Warehouse-size Computer ...
... The core of Google’s Infrastructure The core of Google’s Infrastructure Warehouse-size Computer ...
1 - IFAD Asia
... etc) is handled in the traditional manner. However, the output is fed to a low power FM transmitter and it is this signal that each receiver collects and converts to low volume audio. The total listening experience is amazingly unique and different from any other form of aural reproduction, deliveri ...
... etc) is handled in the traditional manner. However, the output is fed to a low power FM transmitter and it is this signal that each receiver collects and converts to low volume audio. The total listening experience is amazingly unique and different from any other form of aural reproduction, deliveri ...
02. Network Hardware..
... antenna with which the computer can communicate with other systems The antenna may be on the ceiling so that the machines talk to it If the systems are close enough, they can communicate directly with one another in a peer-to-peer configuration Wireless LANs - common in small offices and homes, avoi ...
... antenna with which the computer can communicate with other systems The antenna may be on the ceiling so that the machines talk to it If the systems are close enough, they can communicate directly with one another in a peer-to-peer configuration Wireless LANs - common in small offices and homes, avoi ...
joinfacts
... chart pulls, phone calls, and other efforts to locate or send immunization histories. How do I get Started with MIIC? First, set up an initial meeting with your regional registry staff. Second, before your meeting, identify up to three key staff who will manage login names and passwords, train and s ...
... chart pulls, phone calls, and other efforts to locate or send immunization histories. How do I get Started with MIIC? First, set up an initial meeting with your regional registry staff. Second, before your meeting, identify up to three key staff who will manage login names and passwords, train and s ...
Lecture Note
... One of the Internet’s high-speed, long distance communications links. IP Address/Port IP address is the unique identification on a computer that is connecting to the Internet. Ports are the input/output locations of a computer where messages should send in or out. If an IP address is analogy ...
... One of the Internet’s high-speed, long distance communications links. IP Address/Port IP address is the unique identification on a computer that is connecting to the Internet. Ports are the input/output locations of a computer where messages should send in or out. If an IP address is analogy ...
Datanet Studiu de caz
... q UniCredit Tiriac Bank at a glance (as at 31 December 2010) q Total assets: RON 20.8 billion q Total revenues: RON 1,363 million q Net profit: RON 171 million q Customers: over 500,000 q UniCredit is a major international financial institution with strong roots in 22 European countries ...
... q UniCredit Tiriac Bank at a glance (as at 31 December 2010) q Total assets: RON 20.8 billion q Total revenues: RON 1,363 million q Net profit: RON 171 million q Customers: over 500,000 q UniCredit is a major international financial institution with strong roots in 22 European countries ...
EECP 0442
... Each Ethernet board worldwide has a unique Ethernet-address, it is a 48 bit number (the first 24 bits indicate the manufacturer, the last 24 bits are a unique number for each Ethernet board/controller-chip assigned by the manufacturer). This is also called the MAC-address. ...
... Each Ethernet board worldwide has a unique Ethernet-address, it is a 48 bit number (the first 24 bits indicate the manufacturer, the last 24 bits are a unique number for each Ethernet board/controller-chip assigned by the manufacturer). This is also called the MAC-address. ...