E10 Quick Reference
... WebEye with an IP address that is not compatible with the local network or that is already in use by another computer or similar device. Please refer below example and assign an IP address to WebEye. ...
... WebEye with an IP address that is not compatible with the local network or that is already in use by another computer or similar device. Please refer below example and assign an IP address to WebEye. ...
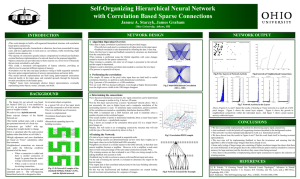
Self-Organizing Hierarchical Neural Network
... •This work attempts to build a self-organized hierarchical structure with correlation based sparse connectivity. •Self-organizing networks, hierarchical or otherwise, have been researched for many years, and have applications in such areas as: surveillance, traffic monitoring, flight control, rescue ...
... •This work attempts to build a self-organized hierarchical structure with correlation based sparse connectivity. •Self-organizing networks, hierarchical or otherwise, have been researched for many years, and have applications in such areas as: surveillance, traffic monitoring, flight control, rescue ...
Undergraduate Curriculum SIGCOMM 2002 Education Workshop Russell J Clark College of Computing
... • 4270 Data Communications Laboratory Hands On Labs - 24 students, 2/year August 20, 2002 - [email protected] ...
... • 4270 Data Communications Laboratory Hands On Labs - 24 students, 2/year August 20, 2002 - [email protected] ...
implementation of trust modeling scheme for artificial
... Each node in an operation must be stored a routing table, which records all the possible links with the nodes in the node and the distance like the number of hops, routing table within each record also contains a sequence number, which is used to determine are there any more old path in order to avo ...
... Each node in an operation must be stored a routing table, which records all the possible links with the nodes in the node and the distance like the number of hops, routing table within each record also contains a sequence number, which is used to determine are there any more old path in order to avo ...
No Slide Title
... Internet Protocol Every computer on the Internet has a unique address. Information sent across IP networks is broken up into bite-sized pieces, called packets. The information within a packet is usually between 1 and about 1500 characters long. ...
... Internet Protocol Every computer on the Internet has a unique address. Information sent across IP networks is broken up into bite-sized pieces, called packets. The information within a packet is usually between 1 and about 1500 characters long. ...
Evaluation of network distance properties
... For instance, IDMaps should not be used with bandwidth in our test ...
... For instance, IDMaps should not be used with bandwidth in our test ...
2060-Text notes Chapter 1 -software: the programs that give
... -connectivity ports- give you access to networks and the internet -Ethernet port-used to connect to a cable modem or network -expansion cards (adapter cards)-circuit boards with specific functions that augment the computer's basic functions as well as provide connections to other devices -network in ...
... -connectivity ports- give you access to networks and the internet -Ethernet port-used to connect to a cable modem or network -expansion cards (adapter cards)-circuit boards with specific functions that augment the computer's basic functions as well as provide connections to other devices -network in ...
In this project, we plan to establish a complete communications loop:
... TCP algorithms developed during the last two decades are mostly empirical and based on assumptions that hold in wired networks [1], but not necessarily in wireless environment. One of the assumptions is that transmission channels only incur low bit error rate (BER). As a result, the TCP flow control ...
... TCP algorithms developed during the last two decades are mostly empirical and based on assumptions that hold in wired networks [1], but not necessarily in wireless environment. One of the assumptions is that transmission channels only incur low bit error rate (BER). As a result, the TCP flow control ...
5G Use Cases
... LTE. This is the LTE evolution effect and 5G will improve performance and make things more flexible ...
... LTE. This is the LTE evolution effect and 5G will improve performance and make things more flexible ...
the school board of broward county
... 3.1.5.2. Input the WINS address4 3.1.5.3. Click the “Add” button. 3.1.5.4. Input 10.251.192.90 as the secondary address. 3.1.5.5. Click “OK”. 3.1.6. Click “OK”. 3.1.7. Click “OK”. 3.2. For a DHCP IP Address: 3.2.1. Click the radio button “Obtain and IP address automatically”. 3.2.2. Input the follow ...
... 3.1.5.2. Input the WINS address4 3.1.5.3. Click the “Add” button. 3.1.5.4. Input 10.251.192.90 as the secondary address. 3.1.5.5. Click “OK”. 3.1.6. Click “OK”. 3.1.7. Click “OK”. 3.2. For a DHCP IP Address: 3.2.1. Click the radio button “Obtain and IP address automatically”. 3.2.2. Input the follow ...
UC510 520_QIG
... use, please observe the following rules. Keep the power off during the installation. Use only the power cord provided with IP Office for SOHO . Make sure that the supply voltage matches the specifications indicated on the rear panel of IP Office for SOHO. Confirm not to bring about the overload of p ...
... use, please observe the following rules. Keep the power off during the installation. Use only the power cord provided with IP Office for SOHO . Make sure that the supply voltage matches the specifications indicated on the rear panel of IP Office for SOHO. Confirm not to bring about the overload of p ...
Worm Hole Attack Detection in Wireless Sensor Network
... reason, prior works based on graph analysis cannot be applied. Introduced by wormhole attacks to detect them unfortunately, this type of solutions cannot work with network coding either. They require either to use an established route that does not exist with network coding, or to calculate the dela ...
... reason, prior works based on graph analysis cannot be applied. Introduced by wormhole attacks to detect them unfortunately, this type of solutions cannot work with network coding either. They require either to use an established route that does not exist with network coding, or to calculate the dela ...
Internet Protocol
... network portion of an IP address in a classful network. Subnetting an IP network allows you to break down what appears (logically) to be a single large network into smaller ones. It was introduced to allow a single site to have a number of local area networks. It reduces the number of entries in the ...
... network portion of an IP address in a classful network. Subnetting an IP network allows you to break down what appears (logically) to be a single large network into smaller ones. It was introduced to allow a single site to have a number of local area networks. It reduces the number of entries in the ...
Downloads
... Business Continuity and Disaster Recovery Maintain the ability to make and receive important business phone calls and voicemails through any major catastrophic disasters, storms, power grid failures etc. You have the power to divert your calls wherever you like via the Web Portal. Other popular feat ...
... Business Continuity and Disaster Recovery Maintain the ability to make and receive important business phone calls and voicemails through any major catastrophic disasters, storms, power grid failures etc. You have the power to divert your calls wherever you like via the Web Portal. Other popular feat ...
eMachines Wireless Supplement - Gateway Computer, Server
... When you are ready to set up your home network, you must first consider which computers or other devices you want to include. Because most home networks look like the example shown on the previous page (with a notebook computer, a desktop computer, a broadband Internet connection, and a printer), th ...
... When you are ready to set up your home network, you must first consider which computers or other devices you want to include. Because most home networks look like the example shown on the previous page (with a notebook computer, a desktop computer, a broadband Internet connection, and a printer), th ...
Inferring Networks of Diffusion
... Plan for the talk: 1. Define a continuous time model of diffusion 2. Define the likelihood of the observed cascades given a network 3. Show how to efficiently compute the likelihood of cascades 4. Show how to efficiently find a graph G that maximizes the ...
... Plan for the talk: 1. Define a continuous time model of diffusion 2. Define the likelihood of the observed cascades given a network 3. Show how to efficiently compute the likelihood of cascades 4. Show how to efficiently find a graph G that maximizes the ...
Intro To Networking Part B Chapter 3
... Open the Cisco folder upper right hand corner of your desktop) and select the router e-sim icon. Router e-sim will allow us to simulate router configuration within a network and also check our results. We will practice together to get everyone on the same page with commands and features within rou ...
... Open the Cisco folder upper right hand corner of your desktop) and select the router e-sim icon. Router e-sim will allow us to simulate router configuration within a network and also check our results. We will practice together to get everyone on the same page with commands and features within rou ...
Document
... Using Passwords • Strong passwords: – Sufficient length – Variety of characters – Upper and lowercase letters – Numbers – Special characters Computing Concepts – Part 2 ...
... Using Passwords • Strong passwords: – Sufficient length – Variety of characters – Upper and lowercase letters – Numbers – Special characters Computing Concepts – Part 2 ...
Connecting to IPv6 ...for Mac OS X
... Note: The following instructions require administrator or equivalent privileges on the computer that is being configured for IPv6. The following instructions cover both Mac OS X 10.4 (Tiger) and Mac OS X 10.5 (Leopard). The older Mac OS X versions 10.2 and 10.3 also include IPv6 support, and the pro ...
... Note: The following instructions require administrator or equivalent privileges on the computer that is being configured for IPv6. The following instructions cover both Mac OS X 10.4 (Tiger) and Mac OS X 10.5 (Leopard). The older Mac OS X versions 10.2 and 10.3 also include IPv6 support, and the pro ...
Type of Networks (Continued)
... • The packet continues its flow around the ring back to the sender which removes the packet and compares the received packet with the packet sent for error control • If two or more NICs attempt to transmit simultaneously ...
... • The packet continues its flow around the ring back to the sender which removes the packet and compares the received packet with the packet sent for error control • If two or more NICs attempt to transmit simultaneously ...
FTTH Explained
... to the feeder cable “feeds”) and drop cable used to physically connect the users to the FTTH network. As a medium, optical fiber’s bandwidth is only limited by the transmitters of the OLT and hence future proofs the access network due to its tremendous bandwidth capacity. The ONT receives the signal ...
... to the feeder cable “feeds”) and drop cable used to physically connect the users to the FTTH network. As a medium, optical fiber’s bandwidth is only limited by the transmitters of the OLT and hence future proofs the access network due to its tremendous bandwidth capacity. The ONT receives the signal ...
PE.WSNi Gateway
... Gateway can work as stand-alone equipment or can be connected to Paradox Engineering’s NMS system that allowing to manage complex networks. All functions can be handled via Web interface that provides a stand-alone host interface to manage your wireless network, without a dedicated host system. Data ...
... Gateway can work as stand-alone equipment or can be connected to Paradox Engineering’s NMS system that allowing to manage complex networks. All functions can be handled via Web interface that provides a stand-alone host interface to manage your wireless network, without a dedicated host system. Data ...
CS578 IT Architecture
... • Coaxial cable is the kind of copper cable used by cable TV companies between the community antenna and user homes and businesses. Coaxial cable is sometimes used by telephone companies from their central office to the telephone poles near users. It is also widely installed for use in business and ...
... • Coaxial cable is the kind of copper cable used by cable TV companies between the community antenna and user homes and businesses. Coaxial cable is sometimes used by telephone companies from their central office to the telephone poles near users. It is also widely installed for use in business and ...
PPTX
... – What about the other problems listed? – War story: Byte swapping problem while routing @ MIT ...
... – What about the other problems listed? – War story: Byte swapping problem while routing @ MIT ...