Course Computer Communications Study Period 2, 2012
... Wireless access networks • shared wireless access network connects end system to router – “adhoc” or via base station aka “access point” ...
... Wireless access networks • shared wireless access network connects end system to router – “adhoc” or via base station aka “access point” ...
Wireless and mobile networks
... access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTSs may still collide with each other (but they’re short) ...
... access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTSs may still collide with each other (but they’re short) ...
Linux+ Guide to Linux Certification
... network communications to use IPSec. • Description: In this activity, you learn how to configure IPSec in the local computer security policy for Windows Server 2003. Although this activity is relatively complex, it is a procedure well worth knowing to protect any Windows serverbased network. You nee ...
... network communications to use IPSec. • Description: In this activity, you learn how to configure IPSec in the local computer security policy for Windows Server 2003. Although this activity is relatively complex, it is a procedure well worth knowing to protect any Windows serverbased network. You nee ...
Read more - Digital Empowerment Foundation
... have been kept aside as free spectrum that can be used by anyone without taking a license or paying a fee to the Government. Using the context of unlicensed spectrum, Digital Empowerment Foundation ideated project, Wireless for Communities (W4C) utilizing low-cost wireless technology and unlicensed ...
... have been kept aside as free spectrum that can be used by anyone without taking a license or paying a fee to the Government. Using the context of unlicensed spectrum, Digital Empowerment Foundation ideated project, Wireless for Communities (W4C) utilizing low-cost wireless technology and unlicensed ...
Windows Server 2008
... • Modern computer operating systems use TCP/IP, which is the communications protocol preference for networks and the Internet • IPv4 is in greatest use today, but networks will eventually convert to IPv6 because it offers a greater range of addresses, better security, and other network improvements ...
... • Modern computer operating systems use TCP/IP, which is the communications protocol preference for networks and the Internet • IPv4 is in greatest use today, but networks will eventually convert to IPv6 because it offers a greater range of addresses, better security, and other network improvements ...
Additional Voltages Available 2-year Extended Warranty Main Input
... settings. The NetAgent can monitor the UPS on the network through a standard web browser. A Network Management System software with Alarm Viewer utility shall provide monitoring of multiple units on a single console application. Inverter will notify administrators to specific power events by sending ...
... settings. The NetAgent can monitor the UPS on the network through a standard web browser. A Network Management System software with Alarm Viewer utility shall provide monitoring of multiple units on a single console application. Inverter will notify administrators to specific power events by sending ...
Introduction to Distributed Systems & Networking
... – Call allocated time slots of bandwidth at each link – Fixed path (for call) determined at call setup – Switches maintain lots of per call state: resource allocation ...
... – Call allocated time slots of bandwidth at each link – Fixed path (for call) determined at call setup – Switches maintain lots of per call state: resource allocation ...
Author Guidelines for 8
... In this document we describe an on-going project aimed at the provision of support to mobile devices, equipped with multiple wireless network interfaces (NICs), running multimedia applications. Specifically, we have developed a cross-layer architecture which offers always-connected services by explo ...
... In this document we describe an on-going project aimed at the provision of support to mobile devices, equipped with multiple wireless network interfaces (NICs), running multimedia applications. Specifically, we have developed a cross-layer architecture which offers always-connected services by explo ...
firewalls
... Intended connection from 1.2.3.4 to 5.6.7.8 Figure 9.8: Redialing on a dynamic packet filter. The dashed arrow shows the intended connection; the solid arrows show the actual connections, to and from the relay in the firewall box. The Firewall impersonates each endpoint to the other. ...
... Intended connection from 1.2.3.4 to 5.6.7.8 Figure 9.8: Redialing on a dynamic packet filter. The dashed arrow shows the intended connection; the solid arrows show the actual connections, to and from the relay in the firewall box. The Firewall impersonates each endpoint to the other. ...
11-Operating Systems Security
... • Firewalls, IDS, IPS • White list – If attackers manage to install a program what will happen? ...
... • Firewalls, IDS, IPS • White list – If attackers manage to install a program what will happen? ...
Classification Of Network
... LAN: LAN is an acronym for Local Area Network. A LAN is a kind of network, where the network spans within a range of certain Km, in other words network is local. For Example: Computers communicated to each other in a lab forms a LAN. Infact multiple departmental labs in a campus or university connec ...
... LAN: LAN is an acronym for Local Area Network. A LAN is a kind of network, where the network spans within a range of certain Km, in other words network is local. For Example: Computers communicated to each other in a lab forms a LAN. Infact multiple departmental labs in a campus or university connec ...
Peer 2 Peer Programming - University of Wisconsin
... it wasn’t until the beginning of Napster that file-transfer among home users became popular. Napster was created by Shawn Fanning in late 1999, while attending Northeastern University in Boston [5]. Napster was created as a ‘hybrid’ peer-to-peer network, meaning there was a centralized server typica ...
... it wasn’t until the beginning of Napster that file-transfer among home users became popular. Napster was created by Shawn Fanning in late 1999, while attending Northeastern University in Boston [5]. Napster was created as a ‘hybrid’ peer-to-peer network, meaning there was a centralized server typica ...
WaveDeploy
... client devices (laptops, mobile phones, scanners, patient monitors, etc.) Powered by WaveAgent installed on each device Setup and test run within less than 5 minutes Results are reported over time ...
... client devices (laptops, mobile phones, scanners, patient monitors, etc.) Powered by WaveAgent installed on each device Setup and test run within less than 5 minutes Results are reported over time ...
Section A - SAITM Gurgaon
... Advertising tool: Nowadays, many individuals and companies are using the e-mail service to advertise their products, services, etc. Info at your fingertips: Storing data online means less large, space taking file cabinets, folders and shelves. You can access information far quicker if you learn how ...
... Advertising tool: Nowadays, many individuals and companies are using the e-mail service to advertise their products, services, etc. Info at your fingertips: Storing data online means less large, space taking file cabinets, folders and shelves. You can access information far quicker if you learn how ...
Network Mobility
... When Mobile Router acquires a Care-of Address from Foreign Agent, it sends a Binding Update to its Home Agent, and Home Agent creates a cache entry binding the Mobile Router’s Home Address to its Care-of Address. If the Mobile Router Seeks to act as a Mobile Router and provide connectivity to nodes ...
... When Mobile Router acquires a Care-of Address from Foreign Agent, it sends a Binding Update to its Home Agent, and Home Agent creates a cache entry binding the Mobile Router’s Home Address to its Care-of Address. If the Mobile Router Seeks to act as a Mobile Router and provide connectivity to nodes ...
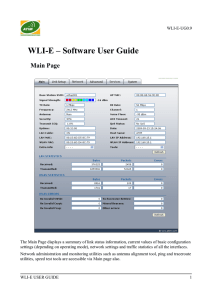
WLI-E – Software User Guide
... LAN Statistics: section displays the detailed receive and transmit statistics (Bytes, Packets, Errors) of LAN (Ethernet) interface. This statistics represents the total amount of data and packets transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversa ...
... LAN Statistics: section displays the detailed receive and transmit statistics (Bytes, Packets, Errors) of LAN (Ethernet) interface. This statistics represents the total amount of data and packets transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversa ...
Lektion 1-Introduktion
... A program that displays visually (on a map) traceroute Trial version can be obtained free from www.visualroute.com ...
... A program that displays visually (on a map) traceroute Trial version can be obtained free from www.visualroute.com ...
Chapter 7
... to close logical ports to invaders – A firewall is built into Windows Vista – More robust firewalls are available from other vendors – Firewalls are critical if you have an alwayson broadband connection ...
... to close logical ports to invaders – A firewall is built into Windows Vista – More robust firewalls are available from other vendors – Firewalls are critical if you have an alwayson broadband connection ...
Modeling Signal Attenuation in IEEE 802.11 Wireless LANs
... The ability to predict the signal strength provided by access points in a wireless LAN (WLAN) is not only useful to researchers but is also a convenient capability in practice. For instance, it gives operators an idea of the coverage provided by a set of access points (APs) based only on their locat ...
... The ability to predict the signal strength provided by access points in a wireless LAN (WLAN) is not only useful to researchers but is also a convenient capability in practice. For instance, it gives operators an idea of the coverage provided by a set of access points (APs) based only on their locat ...
Framework for Network Management to Support Simulation of
... At present, ShaPy is only capable of emulating homogenous virtual network in terms of link latency. This means each node has fixed delay in all directions and thus it is not possible to create clusters of nodes that are close to each other but distant to other nodes outside the group. The required f ...
... At present, ShaPy is only capable of emulating homogenous virtual network in terms of link latency. This means each node has fixed delay in all directions and thus it is not possible to create clusters of nodes that are close to each other but distant to other nodes outside the group. The required f ...
Slide title goes here
... GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze ...
... GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze ...
IPv4 to IPv6 Migration strategies
... Managed by IANA Low government involvement Need for international cooperation Policy for addresses was for first come, first serve. Pre occupation of large amount of addresses by early users ...
... Managed by IANA Low government involvement Need for international cooperation Policy for addresses was for first come, first serve. Pre occupation of large amount of addresses by early users ...
Mobile Communications
... typically very low bandwidth compared to wired networks (1-10 Mbit/s) due to shared medium many proprietary solutions, especially for higher bit-rates, standards take their time (e.g. IEEE 802.11) products have to follow many national restrictions if working wireless, it takes a vary long time t ...
... typically very low bandwidth compared to wired networks (1-10 Mbit/s) due to shared medium many proprietary solutions, especially for higher bit-rates, standards take their time (e.g. IEEE 802.11) products have to follow many national restrictions if working wireless, it takes a vary long time t ...
20019-Small_Business_Wireless_Portfolio
... network and Guest Access 802.1q VLANs - Multiple VLANs keep traffic separate on the LAN ...
... network and Guest Access 802.1q VLANs - Multiple VLANs keep traffic separate on the LAN ...