N44096972
... monitoring system to stop an intrusion attempt. The typical work of IDS is to record information related to observed events, notify the security administrators of important observed events, and generate reports, as in [1]. Many IDS also detect a threat and attempt to prevent it from succeeding. Seve ...
... monitoring system to stop an intrusion attempt. The typical work of IDS is to record information related to observed events, notify the security administrators of important observed events, and generate reports, as in [1]. Many IDS also detect a threat and attempt to prevent it from succeeding. Seve ...
Networking Chapter 18
... Verify network adapter and its drivers installed Try updating the device drivers Try uninstalling/reinstalling network adapter drivers Run network adapter diagnostic programs Update or reinstall onboard network port drivers If Device Manager still reports errors: • Run antivirus software, and update ...
... Verify network adapter and its drivers installed Try updating the device drivers Try uninstalling/reinstalling network adapter drivers Run network adapter diagnostic programs Update or reinstall onboard network port drivers If Device Manager still reports errors: • Run antivirus software, and update ...
Changes in Power System Communications
... • Up to 127 devices can connect to the host, either directly or by way of USB hubs. • Individual USB cables can run as long as 5 meters; with hubs, devices can be up to 30 meters away from the host. • With USB 2.,the bus has a maximum data rate of 480 Mb per second. • With USB 3.,the bus has a maxim ...
... • Up to 127 devices can connect to the host, either directly or by way of USB hubs. • Individual USB cables can run as long as 5 meters; with hubs, devices can be up to 30 meters away from the host. • With USB 2.,the bus has a maximum data rate of 480 Mb per second. • With USB 3.,the bus has a maxim ...
DDoS, Internet Self-Regulation, and the consequences
... „large networks“ (like Akamai or Cloudflare) have seen – and weathered – attacks over 500 Gbit/s so, in the long run, customers will (need to!) migrate to large service providers, or pay extra for external DDoS mitigation services that have „lots of bandwidth“ ...
... „large networks“ (like Akamai or Cloudflare) have seen – and weathered – attacks over 500 Gbit/s so, in the long run, customers will (need to!) migrate to large service providers, or pay extra for external DDoS mitigation services that have „lots of bandwidth“ ...
CCNA Security 1.1 Instructional Resource
... devices to use Cisco Configuration Professional (CCP). Since CCP is used extensively throughout the labs, it is critical that all students perform this lab. This is also a good time for students to practice basic configuration and cabling. If you are short on time or equipment, pre-configure Part 1 ...
... devices to use Cisco Configuration Professional (CCP). Since CCP is used extensively throughout the labs, it is critical that all students perform this lab. This is also a good time for students to practice basic configuration and cabling. If you are short on time or equipment, pre-configure Part 1 ...
ch13
... systems, bus-based Ethernet is occasionally seen because the cost of a hub used to be much less expensive than the cost of a switch, but this is no longer the case. Bus-based Ethernet requires that all nodes share the bus; thus the speed of the bus is, at best, inversely proportional to the number o ...
... systems, bus-based Ethernet is occasionally seen because the cost of a hub used to be much less expensive than the cost of a switch, but this is no longer the case. Bus-based Ethernet requires that all nodes share the bus; thus the speed of the bus is, at best, inversely proportional to the number o ...
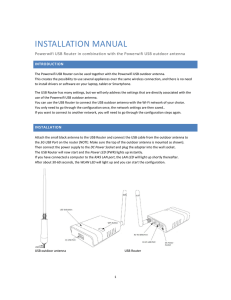
installation manual
... selected network should be stated as “None”. In such a situation you don’t fill a password during configuration of the router in the next step but you will continue with Next immediately. After you’ve properly configured the USB router you should automatically be redirected to the Hotspot login page ...
... selected network should be stated as “None”. In such a situation you don’t fill a password during configuration of the router in the next step but you will continue with Next immediately. After you’ve properly configured the USB router you should automatically be redirected to the Hotspot login page ...
3.2 Network Camera Installation
... 3.4 Focusing your Camera ................................................................................................................... 8 4 Connecting the Camera to the Network................................................................................................... 9 5 Assign IP using ...
... 3.4 Focusing your Camera ................................................................................................................... 8 4 Connecting the Camera to the Network................................................................................................... 9 5 Assign IP using ...
Measuring the Performance of Packet size and Data rate for
... Abstract—Since 2004, Vehicular Ad-hoc Networks (VANETs) is core technology of Intelligent Transportation System (ITS), in which standardize the Wireless Access in Vehicle Environments (WAVE) based on IEEE 1609 and IEEE 802.11p. WAVE is a field of study to provide safety service and information to pe ...
... Abstract—Since 2004, Vehicular Ad-hoc Networks (VANETs) is core technology of Intelligent Transportation System (ITS), in which standardize the Wireless Access in Vehicle Environments (WAVE) based on IEEE 1609 and IEEE 802.11p. WAVE is a field of study to provide safety service and information to pe ...
GSM/UMTS Network
... Flexible architecture that is possible to use for any connectivity (ATM, IP, STM) Keep the N-ISDN/GSM service paradigm. Use MAP, ISUP, etc. All devices needed for user plane manipulation are moved to the Media Gateway (echo cancellers, codecs, etc.) Possible to place infrequently used equipment in c ...
... Flexible architecture that is possible to use for any connectivity (ATM, IP, STM) Keep the N-ISDN/GSM service paradigm. Use MAP, ISUP, etc. All devices needed for user plane manipulation are moved to the Media Gateway (echo cancellers, codecs, etc.) Possible to place infrequently used equipment in c ...
MAC layer
... Receiver of frag1 answers after SIFS with ACK1 including reservation for next transmission. A set of nodes may receive this reservation and adjust their NAV frag2 is last fragment; Sender does not reserve the medium; Receiver acknowledges frag2, not reserving the medium. After ACK2, all nodes compet ...
... Receiver of frag1 answers after SIFS with ACK1 including reservation for next transmission. A set of nodes may receive this reservation and adjust their NAV frag2 is last fragment; Sender does not reserve the medium; Receiver acknowledges frag2, not reserving the medium. After ACK2, all nodes compet ...
authors(v7) - IDA.LiU.se
... Basic Service Set (BSS) (aka “cell”) in infrastructure mode contains: • wireless hosts • access point (AP): base station • ad hoc mode: hosts only ...
... Basic Service Set (BSS) (aka “cell”) in infrastructure mode contains: • wireless hosts • access point (AP): base station • ad hoc mode: hosts only ...
Network protocols - VCE IT Lecture Notes
... NETWORKING TECHNOLOGIES A “Networking Technology” defines how packets are handled and what the hardware is like. The only networking technology to know is ...
... NETWORKING TECHNOLOGIES A “Networking Technology” defines how packets are handled and what the hardware is like. The only networking technology to know is ...
NETWORK CONNECTION HARDWARE
... Network interface adapters provide the physical link between computers and the network. Hubs are physical layer devices that amplify and repeat signals out all ports except the one they were received through. Bridges and switches are data-link layer devices that use destination addresses to forward ...
... Network interface adapters provide the physical link between computers and the network. Hubs are physical layer devices that amplify and repeat signals out all ports except the one they were received through. Bridges and switches are data-link layer devices that use destination addresses to forward ...
The Politics of the Internet
... The Politics of the Internet – Week Two Creation of the World Wide Web Key step in bringing the Internet to the masses was the World Wide Web Invented in CERN by Tim Berners-Lee Idea was to create a way in which documents could be organized on the Internet And could link to each other – with ...
... The Politics of the Internet – Week Two Creation of the World Wide Web Key step in bringing the Internet to the masses was the World Wide Web Invented in CERN by Tim Berners-Lee Idea was to create a way in which documents could be organized on the Internet And could link to each other – with ...
Active Networks
... "Patrol" and "first-aid" packets can track a problem and rectify it respectively. Code moved to node rather than data to management center Example:Delegated Management. Decentralization helps in scalability, reducing delays from responses and effective bandwidth utilization. ...
... "Patrol" and "first-aid" packets can track a problem and rectify it respectively. Code moved to node rather than data to management center Example:Delegated Management. Decentralization helps in scalability, reducing delays from responses and effective bandwidth utilization. ...
PPTX - SJTU CS
... visualization and analysis: UCInet - user friendly social network visualization and analysis software (suitable smaller networks) iGraph - if you are familiar with R, you can use iGraph as a module to analyze or create large networks, or you can directly use the C functions Jung - comprehensive Java ...
... visualization and analysis: UCInet - user friendly social network visualization and analysis software (suitable smaller networks) iGraph - if you are familiar with R, you can use iGraph as a module to analyze or create large networks, or you can directly use the C functions Jung - comprehensive Java ...
Internetworking I - Carnegie Mellon School of Computer Science
... Build a single network (an interconnected set of networks, or internetwork, or internet) out of a large collection of separate networks. – Each network must stand on its own, with no internal changes allowed to connect to the internet. – Communications would be on a best-effort basis. – “black boxes ...
... Build a single network (an interconnected set of networks, or internetwork, or internet) out of a large collection of separate networks. – Each network must stand on its own, with no internal changes allowed to connect to the internet. – Communications would be on a best-effort basis. – “black boxes ...
Building Survivable Systems based on Intrusion Detection and
... most intrusion signatures expressed on these papers can be easily captured in our language as well ...
... most intrusion signatures expressed on these papers can be easily captured in our language as well ...
Basic Concepts of Computer Networks
... of systems on a computer network. It defines how the computers, or nodes, within the network are arranged and connected to each other. (TechTerms.com, 2007) ...
... of systems on a computer network. It defines how the computers, or nodes, within the network are arranged and connected to each other. (TechTerms.com, 2007) ...
CSCI3421_Ch4
... Issue: How do you know which exit gateway to use unless you know everything connected to each gateway Need an inter-AS routing protocol (as well as intra-AS protocols) ...
... Issue: How do you know which exit gateway to use unless you know everything connected to each gateway Need an inter-AS routing protocol (as well as intra-AS protocols) ...