* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Slide title goes here
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed firewall wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
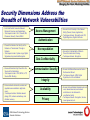
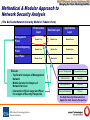
Track 5.4 -- Emerging Network Security Technology: A Lucent Bell Labs Prospective Bell Labs Network Security Model Andrew R. McGee Distinguished Member of Technical Staff Lucent Technologies Bell Labs April 2, 2003 GSA Federal Technology Service Smarter Solutions GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Topics Building the Network Security Model: • Security Threats. • Security Layers. • Security Planes. • Security Dimensions. Applying the Network Security Model to Network Security Assessments: • Network, Host and Service Discovery. • Data Fusion - Putting it All Together. • Producing Meaningful Results. GSA Federal Technology Service Smarter Solutions GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Types of Network Security Threats1 Interruption (An Attack on Availability): – Network Becomes Unavailable or Unusable – Examples: • Malicious Destruction of a Network Element • Erasure of a Software Program or Data File • Cutting of a Communication Facility Interception (An Attack on Confidentiality): – An Unauthorized Access to an Asset – Examples: • Unauthorized Data Capture (Data Sniffing) • Discovery of Unprotected WLAN Access Points Modification (An Attack on Integrity): – An Unauthorized Tampering with an Asset – Examples: • Changing Network Configuration Information • Changing Data as it is Being Transmitted Across the Network Fabrication (An Attack on Authenticity): – Unauthorized Creation, Modification, or Deletion of Objects on a Network – Examples: • Unauthorized Access to the Network • Insertion of Spurious Messages on the Network • Addition of Records to a Database 1C. Pfleeger, Security in Computing, Prentice Hall, Upper Saddle River, NJ, 1997. GSA Federal Technology Service Smarter Solutions GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Security Layers Applications Security THREATS Interruption Services Security Interception VULNERABILITIES Modification Vulnerabilities Can Exist In Each Layer Fabrication Infrastructure Security ATTACKS Infrastructure Security Layer: • Fundamental Building Blocks of Networks, Services, and Applications. • Individual Network Elements and the Interconnecting Communications Facilities • Examples: – Individual Routers, Switches, Servers – Point-to-Point WAN Links – Ethernet Links GSA Federal Technology Service Smarter Solutions Applications Security Layer: • Network-Based Applications Accessed by End-Users • Includes: – Fundamental Applications (e.g., Web Browsing) – Basic Applications (e.g., Directory Assistance and Email) – High-End Applications (e.g., E-Commerce) Services Security Layer: • Services Provided to Customers or End-Users • Range from Basic Transport to High-End, ValueAdded Services. • Examples: – Carrier Facilities (DS-1, DS-3, etc.) – Frame Relay, ATM, IP Connectivity – VoIP, QoS, IM, Location Services – 800-Services GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Security Layers Apply to Every Protocol Layer Example - Applying Security Layers to ATM Networks (Layer 2): Infrastructure Security Layer: – Individual ATM Switches – Point-to-Point Communication Links Between Switches (e.g., DS-3 links, OC-48 links, etc.) Services Security Layer: – ATM Services Classes: CBR, VBR-RT, VBR-nRT, ABR, UBR Applications Security Layer: – ATM-Based Video Conferencing Application GSA Federal Technology Service Smarter Solutions Example - Applying Security Layers to IP Networks (Layer 3): Infrastructure Security Layer: – Wireline NEs: Individual Routers, Servers – Wireless NEs: PDSN, SGSN, GGSN. – Communication Links Between NEs Note: Could be ATM PVCs Services Security Layer: – Basic IP Transport – IP Support Services (e.g., AAA, DNS, DHCP) – Value-Added Services: (e.g., VPN, VoIP, QoS) Applications Security Layer: – Basic Applications (e.g., ftp, Web Access) – Fundamental Applications (e.g., Email) – High-End Applications (e.g., E-Commerce, Training) GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Security Planes Vulnerabilities Can Exist In Each Layer and Plane Management Security Plane: • Concerned with OAM&P of Network Elements, Transmission Facilities, Operations/Business Systems • Concerned with Management and Provisioning of Network Services and Applications • Supports the FCAPS Functions • May Be In-Band or Out-of-Band GSA Federal Technology Service Smarter Solutions End-User Security Plane: • How Customers Access and Use the Network • Represents End-User Data At Rest and In Motion • End-Users May Use the Network For: – Basic Connectivity/Transport – Value-Added Services (VPN, VoIP, etc.) – Access to Network-Based Applications (e.g., Email). Control/Signaling Security Plane: • Enables the Efficient Delivery of Information, Services, and Applications Across the Network • Machine-to-Machine Communications to Determine How to Best Route or Switch Traffic Across the Network • May Be In-Band or Out-of-Band GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Example: Applying Security Planes to Network Activities/Protocols End User Security Plane: Activities • End-User Data Transfer • End-User – Application Interactions Protocols • HTTP, RTP, POP, IMAP • TCP, UDP, FTP • IPSec, TLS Control/Signaling Security Plane: Activities Protocols • Update of Routing/Switching Tables • Service Initiation, Control, and Teardown • Application Control • • • • BGP, OSPF, IS-IS, RIP, PIM SIP, RSVP, H.323, SS7. IKE, ICMP PKI, DNS, DHCP, SMTP Management Security Plane: • • • • Activities Operations Administration Management Provisioning GSA Federal Technology Service Smarter Solutions • • • • Protocols SNMP Telnet FTP HTTP GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Security Dimensions Address the Breadth of Network Vulnerabilities • Limit and Control Access to Network Elements, Services, and Applications. • Techniques Include: ACL, Firewall, IDS, Password, Security Token, RBAC. Access Management Authentication • Prevent the Denial of an Activity on the Network or Transmission Through a Network. • Techniques Include: System Logs, Digital Signatures, Asymmetrical Encryption. • Ensure Information Only Flows from the Source to the Destination. • Techniques Include: VPN, MPLS, L2TP, Source Path Routing. Non-repudiation Data Confidentiality Communication Security Integrity • Ensure network elements, services and application are available to legitimate users. • Techniques Include: Reliable network design, IDS, network redundancy, and disaster recovery. GSA Federal Technology Service Smarter Solutions Availability Privacy • Ensure Proof of Identity of the Claimed Entity (Person, Device, Application). • Techniques Include: Shared Secret, PKI, Digital Signature, Digital Certificate. • Ensure the Confidentiality of Data to Prevent Unauthorized Viewing. • Techniques Include: Encryption. • Ensure that Data is Received as Sent or Retrieved as Stored. • Techniques Include: MD5, Digital Signature, Anti-Virus Software. • Ensure that confidential information of end user, network element, and network architecture is not disclosed to unauthorized entity. • Techniques Include: Encryption, Service Level agreement, etc. GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Infrastructure Security Privacy Availability THREATS Integrity Data Confidentiality Vulnerabilities Can Exist In Each Layer, Plane, Dimension Non- repudiation VULNERABILITIES Authentication Services Security Access Management Security Layers Applications Security Communication Security Bell Labs Network Security Model Interruption Interception Modification Fabrication ATTACKS End User Security Control/Signaling Security Security Planes 8 Security Dimensions Management Security Supported by Government Agencies & Standards Bodies: NSIE NSTAC NRIC DHS ITU-T SG17 Industry Canada GSA Federal Technology Service Smarter Solutions Applicable To: • Wireless, Wireline and Optical Networks • Voice, Data, and Converged Networks • Any Layer of the Protocol Stack • Management, Administrative and Data Center Networks • SP Infrastructure Networks • Enterprise Networks GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Methodical & Modular Approach to Network Security Analysis (The Bell Labs Network Security Model in Tabular Form) Infrastructure Layer Services Layer Applications Layer Management Plane Module One Module Four Module Seven Control/Signaling Plane Module Two Module Five Module Eight Module Three Module Six Module Nine User Plane Execute – Top Row for Analysis of Management Network – Middle Column for Analysis of Network Services – Intersection of Each Layer and Plane for analysis of Security Perspective Access Management Communication Security Authentication Integrity Non-repudiation Availability Data Confidentiality Privacy The Eight Security Dimensions Are Applied to Each Security Perspective GSA Federal Technology Service Smarter Solutions GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Applying the Bell Labs Network Security Model to Security Programs Can Apply to Every Aspect of a Network Security Program • Definition & Planning: Helps define comprehensive Security Policies, Incident Response & Recovery Plans and Technology Architectures by taking Security Dimensions, Layers and Planes into account • Implementation: Forms basis of an assessment that examines how the Security Dimensions, Layers and Planes are addressed as Policies and Procedures are rolled out and technology is deployed • Maintenance: Assists in managing the Security Policies & Procedures, Incident Response & Recovery Plans and Technology Architectures by ensuring modifications to the Security Program address Security Dimensions, Layers and Planes GSA Federal Technology Service Smarter Solutions GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze BL Network Security Model in Action: Network Survivability Assessment Service Bell Labs Net w ork Securit y M odel Quest ionnaire M odule Cust om er Input M odule Assessm ent M odule Netw ork Survivabil ity Assessm ent Recom m endat ion M odule Im plem ent at ion/ Operat ion M odule Int ernal Test M odule1 Ext ernal Test M odule2 Data collection Phase Analysis Phase Health Check Iteration GSA Federal Technology Service Smarter Solutions Recom mendation Im plem entation/ Health Phase operation Check GSA/FTS Network Services Conference 2003 Managing the Future: Mastering the Maze Conclusion Bell Labs Network Security Model • • • • • Provides Comprehensive, End-to-End View of Network Security. Applies to Any Networking Technology: – Wireless, Wireline and Optical Networks. – Voice, Data and Converged Networks. Applies to Any Layer of the Protocol Stack. Applies to Any Portion of a Network: – Management, Administrative and Data Center Networks. – Infrastructure Networks. – Enterprise Networks. Widely Accepted by Government Agencies and Standards Bodies: – National Security Information Exchange (NSIE). – National Security Telecommunications Advisory Committee (NSTAC). – National Reliability and Interoperability Council (NRIC). – U.S. Department of Homeland Security (DHS). – Industry Canada. – ITU-T. Comprehensive Network Security Assessments Based on BL Network Security Model • • Tools and Techniques are used to Assess Security Layers, Planes, Dimensions. Results are Provided in Terms of Network and Business Impact. GSA Federal Technology Service Smarter Solutions