Estinet open flow network simulator and emulator.
... • Use real devices, run real operating systems and applications. • Can generate more realistic testing results. • Huge cost of building a large experimental. ...
... • Use real devices, run real operating systems and applications. • Can generate more realistic testing results. • Huge cost of building a large experimental. ...
Telefonica Completes Multi-Vendor SDN Proof-of
... completion of a multi-domain and multi-vendor SDN interoperability proof-of-concept trial, which included working with ADVA Optical Networking (Frankfurt: ADV), Ciena (NYSE: CIEN), Huawei and Infinera (NASDAQ: INFN). Telefonica utilized its IETF-based Application Based Network Operations (ABNO) orch ...
... completion of a multi-domain and multi-vendor SDN interoperability proof-of-concept trial, which included working with ADVA Optical Networking (Frankfurt: ADV), Ciena (NYSE: CIEN), Huawei and Infinera (NASDAQ: INFN). Telefonica utilized its IETF-based Application Based Network Operations (ABNO) orch ...
Computer Security - University at Albany
... A 16-year-old music student called Richard Pryce, better known by the hacker alias Datastream Cowboy, is arrested and charged with breaking into hundreds of computers including those at the Griffiths Air Force base, Nasa and the Korean Atomic Research Institute. His online mentor, "Kuji", is ...
... A 16-year-old music student called Richard Pryce, better known by the hacker alias Datastream Cowboy, is arrested and charged with breaking into hundreds of computers including those at the Griffiths Air Force base, Nasa and the Korean Atomic Research Institute. His online mentor, "Kuji", is ...
TCP/IP Internetworking (Part 2)
... The Data Link layer process in Port 1 will de-encapsulate the IP packet from the frame The Physical layer will pass the frame to the Data Link layer process in Port 2 The Data Link layer process in Port 2 will de-encapsulate the IP packet from the frame None of the above ...
... The Data Link layer process in Port 1 will de-encapsulate the IP packet from the frame The Physical layer will pass the frame to the Data Link layer process in Port 2 The Data Link layer process in Port 2 will de-encapsulate the IP packet from the frame None of the above ...
Information Technology Terminology Information Systems Analysts
... Collision Domain - In Ethernet, the network area within which frames that have collided are propagated. Repeaters and hubs propagate collisions; LAN switches, bridges and routers do not. COM - Common equipment describes items used by more than one channel or equipment function. Commercial Backbone - ...
... Collision Domain - In Ethernet, the network area within which frames that have collided are propagated. Repeaters and hubs propagate collisions; LAN switches, bridges and routers do not. COM - Common equipment describes items used by more than one channel or equipment function. Commercial Backbone - ...
Admission Control in IP Multicast over Heterogeneous Access
... – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
... – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
4th Edition: Chapter 1
... customers • Assigns its customers CIDR addresses from that block • Customers, smaller ISPs, and in turn re-allocate portions of their address block to their users • Yet global routing tables for all these networks can be represented by single route entry ...
... customers • Assigns its customers CIDR addresses from that block • Customers, smaller ISPs, and in turn re-allocate portions of their address block to their users • Yet global routing tables for all these networks can be represented by single route entry ...
Physical Layer Repeater
... The FR-50 physical layer repeater is a cost-effective method for extending the distance or increasing the number of nodes on a LONWORKS™ XP/FT-10 Free Topology network channel utilizing any type of Free Topology Transceiver (FT 3120, FT 3150, FT-5000, FTT-10A) or Link Power (LPT-10 ) transceiver. Th ...
... The FR-50 physical layer repeater is a cost-effective method for extending the distance or increasing the number of nodes on a LONWORKS™ XP/FT-10 Free Topology network channel utilizing any type of Free Topology Transceiver (FT 3120, FT 3150, FT-5000, FTT-10A) or Link Power (LPT-10 ) transceiver. Th ...
seminar report - School of Information Technology, IIT kharagpur
... The calling and called parties both have computers that enable them to connect to the Internet, usually via the network of an Internet service provider (ISP). The two correspondents are able to establish voice communication. Both users have to be connected to the Internet at that time and use IP tel ...
... The calling and called parties both have computers that enable them to connect to the Internet, usually via the network of an Internet service provider (ISP). The two correspondents are able to establish voice communication. Both users have to be connected to the Internet at that time and use IP tel ...
10. Communication - Yasar Ahmad ICT Website
... 10. Communication Communicate with other ICT users using email ...
... 10. Communication Communicate with other ICT users using email ...
SONET Overview Randy Eisenach FNTS System
... • Separate networks due to regulatory, operational, or administrative requirements ...
... • Separate networks due to regulatory, operational, or administrative requirements ...
CCNA 2.0TM 1.800.865.0165
... • Interconnectivity • Interoperability • Internetworking & Types of Networks • Key Network Characteristics Section B: The OSI Model • OSI Basics • Encapsulation • OSI Layers 1 & 2 • OSI Layer 3 & 4 • OSI Layers 5, 6 & 7 Section C: LAN Networking Topologies • Ethernet & Token Ring • ANSI FDDI ...
... • Interconnectivity • Interoperability • Internetworking & Types of Networks • Key Network Characteristics Section B: The OSI Model • OSI Basics • Encapsulation • OSI Layers 1 & 2 • OSI Layer 3 & 4 • OSI Layers 5, 6 & 7 Section C: LAN Networking Topologies • Ethernet & Token Ring • ANSI FDDI ...
Wireless Control That Simply Works
... consumption in extended networks like cluster tree or mesh – Allows all clients in a local piece of the network the ability to know when to communicate with each other – PAN has a coordinator that manages the channel and arranges the calls – Significant value will be in system power consumption for ...
... consumption in extended networks like cluster tree or mesh – Allows all clients in a local piece of the network the ability to know when to communicate with each other – PAN has a coordinator that manages the channel and arranges the calls – Significant value will be in system power consumption for ...
DHCP snooping
... server An attacker broadcasts a large number of DHCP requests using spoofed MAC addresses The DHCP server will lease its IP addresses one by one to the attacker until it runs out of available IPs for new, normal clients Leads to DoS ...
... server An attacker broadcasts a large number of DHCP requests using spoofed MAC addresses The DHCP server will lease its IP addresses one by one to the attacker until it runs out of available IPs for new, normal clients Leads to DoS ...
Using Heterogeneous Wireless Sensor Networks in
... systems’ functionalities, overcharging, or limiting their capabilities. Classical functional architectures are characterized by trying to find modularity and a structure oriented to the system itself. Modern functional architectures like SOA, consider integration and performance aspects that must be ...
... systems’ functionalities, overcharging, or limiting their capabilities. Classical functional architectures are characterized by trying to find modularity and a structure oriented to the system itself. Modern functional architectures like SOA, consider integration and performance aspects that must be ...
Network+ Guide to Networks 6th Edition
... – Facilitates communication between software applications and lower-layer network services – Network interprets application request – Application interprets data sent from network ...
... – Facilitates communication between software applications and lower-layer network services – Network interprets application request – Application interprets data sent from network ...
DS35676681
... networks. The multi hop support makes communication between nodes outside the direct range of each other possible. 1.2 Some Issues in MANET Network An ad hoc network is a dynamic type of network with similarities and great differences to its parent fixed communication network. The properties of an a ...
... networks. The multi hop support makes communication between nodes outside the direct range of each other possible. 1.2 Some Issues in MANET Network An ad hoc network is a dynamic type of network with similarities and great differences to its parent fixed communication network. The properties of an a ...
network
... good: less control-plane processing resources along the way More dataplane (address lookup) processing ...
... good: less control-plane processing resources along the way More dataplane (address lookup) processing ...
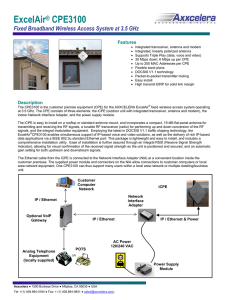
ExcelAir® CPE3100
... at 3.5 GHz. The CPE consists of three elements: the iCPE (outdoor unit with integrated transceiver, antenna and modem), the indoor Network Interface Adapter, and the power supply module. The iCPE is easy to install on a rooftop or standard antenna mount, and incorporates a compact, 19 dBi flat-panel ...
... at 3.5 GHz. The CPE consists of three elements: the iCPE (outdoor unit with integrated transceiver, antenna and modem), the indoor Network Interface Adapter, and the power supply module. The iCPE is easy to install on a rooftop or standard antenna mount, and incorporates a compact, 19 dBi flat-panel ...
DSL Installation Guide
... or firewall. For instructions on how to assign the static IP address to your router or firewall, please refer to your router or firewall documentation. Your computers must be set to automatically receive IP addresses using the instructions in the configuration found on the pages indicated below. ...
... or firewall. For instructions on how to assign the static IP address to your router or firewall, please refer to your router or firewall documentation. Your computers must be set to automatically receive IP addresses using the instructions in the configuration found on the pages indicated below. ...
Implementing IEEE802.16 WiMAX in OPNET
... Technology based on evolving standard for point-tomultipoint wireless broadband networking Solution for Wireless Metropolitan Area Network BWA (Broadband Wireless Access) solution Why need WiMax?? Alternative from DSL broadband access services – expensive installation cable in long distance Provide ...
... Technology based on evolving standard for point-tomultipoint wireless broadband networking Solution for Wireless Metropolitan Area Network BWA (Broadband Wireless Access) solution Why need WiMax?? Alternative from DSL broadband access services – expensive installation cable in long distance Provide ...