VPN Routers - D-Link
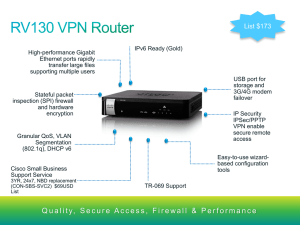
... (SSL) VPN tunnels respectively, as well as 5, 10 or 15 Generic Routing Encapsulation (GRE) tunnels, empowering your mobile users by providing remote access to a central corporate database. Site-to-site VPN tunnels use IP Security (IPSec) Protocol, Point-toPoint Tunneling Protocol (PPTP), or Layer 2 ...
... (SSL) VPN tunnels respectively, as well as 5, 10 or 15 Generic Routing Encapsulation (GRE) tunnels, empowering your mobile users by providing remote access to a central corporate database. Site-to-site VPN tunnels use IP Security (IPSec) Protocol, Point-toPoint Tunneling Protocol (PPTP), or Layer 2 ...
OpenAirInterface: An Open LTE Network in a PC
... N. Nikaein, R. Knopp, F. Kaltenberger, L. Gauthier, C. Bonnet, D. Nussbaum, R. Ghaddab EURECOM, Mobile Communication Department ...
... N. Nikaein, R. Knopp, F. Kaltenberger, L. Gauthier, C. Bonnet, D. Nussbaum, R. Ghaddab EURECOM, Mobile Communication Department ...
Ensuring QoS in Your VoIP Development
... triggers extra network traffics. Total number of packets per hour N = e * x / 60, where e = number of elements, x is minutes. Severity base polling: send a ping to critical elements more often. ...
... triggers extra network traffics. Total number of packets per hour N = e * x / 60, where e = number of elements, x is minutes. Severity base polling: send a ping to critical elements more often. ...
Presentation
... Challenges for an operator Distribution of accurate time synchronization creates new challenges for an operator Operation of the network Handling of asymmetries (at set up and during operation) Planning of proper Redundancy (e.g. Time sync Holdover is only available for limited periods (minutes ins ...
... Challenges for an operator Distribution of accurate time synchronization creates new challenges for an operator Operation of the network Handling of asymmetries (at set up and during operation) Planning of proper Redundancy (e.g. Time sync Holdover is only available for limited periods (minutes ins ...
network
... Advantages and disadvantages of networks Peer-to-peer and client/server LANs Importance of network protocols Most widely used LAN protocol Special components of a WAN The difference between circuit-switching and packet switching networks ...
... Advantages and disadvantages of networks Peer-to-peer and client/server LANs Importance of network protocols Most widely used LAN protocol Special components of a WAN The difference between circuit-switching and packet switching networks ...
Lecture 6: Intra
... • Problem: Find lowest cost path between two nodes - Each node individually computes the cost (some recent research argues against doing this, more on this later) ...
... • Problem: Find lowest cost path between two nodes - Each node individually computes the cost (some recent research argues against doing this, more on this later) ...
Use the following IP address
... – 2. For a wired network: • Connect network cable to Ethernet RJ-45 port and network port (wall jack, router, switch) • Verify lights • Windows should automatically configure connection ...
... – 2. For a wired network: • Connect network cable to Ethernet RJ-45 port and network port (wall jack, router, switch) • Verify lights • Windows should automatically configure connection ...
CCNA 1 Module 6 Ethernet Fundamentals
... Nodes monitor the bus (or Ether) to determine if it is busy. A node wishing to send data waits for an idle condition then transmits its message. Collisions can occur when two nodes transmit at the same time, thus nodes must monitor the cable when they transmit. When a collision occurs, both nodes st ...
... Nodes monitor the bus (or Ether) to determine if it is busy. A node wishing to send data waits for an idle condition then transmits its message. Collisions can occur when two nodes transmit at the same time, thus nodes must monitor the cable when they transmit. When a collision occurs, both nodes st ...
Networking in Linux
... ♦ Introduction A computer network is defined as a number of systems that are connected to each other and exchange information across the network connection. The system network is configured by setting the IP address which is assigned by the system administrator. The IP address provides base services ...
... ♦ Introduction A computer network is defined as a number of systems that are connected to each other and exchange information across the network connection. The system network is configured by setting the IP address which is assigned by the system administrator. The IP address provides base services ...
I R T R ECHNICAL
... access points to be mobile/wireless routers with broadband connection to the infrastructure network, then our assumption becomes more sound. Although we do not have a control over the location of the access points, we will have control over their population: We require the number of ad hoc nodes per ...
... access points to be mobile/wireless routers with broadband connection to the infrastructure network, then our assumption becomes more sound. Although we do not have a control over the location of the access points, we will have control over their population: We require the number of ad hoc nodes per ...
Module 12 - SaigonTech
... allow two or more computers to communicate with one another. Most networks rely upon wires or cables to transmit data between machines as electrical impulses, but some devices use radio waves or even light to do the job. UNIX Operating System I ...
... allow two or more computers to communicate with one another. Most networks rely upon wires or cables to transmit data between machines as electrical impulses, but some devices use radio waves or even light to do the job. UNIX Operating System I ...
Internetworking
... • Requires that lower level protocols provide services… • And therefore was designed to be undemanding… • In this way, IP can make use of a wide variety of underlying networks ...
... • Requires that lower level protocols provide services… • And therefore was designed to be undemanding… • In this way, IP can make use of a wide variety of underlying networks ...
07/08 Semester B - City University of Hong Kong
... outgoing trunks, estimate the grade of service. State any assumptions you make. [5 marks] (c) Redesign the above network by increasing the number of the secondary switches to provide a grade of service better than 1 in 500. How many crosspoints does this network require? Draw the resulting design. [ ...
... outgoing trunks, estimate the grade of service. State any assumptions you make. [5 marks] (c) Redesign the above network by increasing the number of the secondary switches to provide a grade of service better than 1 in 500. How many crosspoints does this network require? Draw the resulting design. [ ...
Enterprise Council Comms overview
... Distribution Layer • In smaller networks or single building backbones, the distribution layer may be omitted • The goal of the Distribution layer is to aggregate wiring closet, provide greater segmentation across the campus and provide higher throughput for localised traffic • Distribution layer sw ...
... Distribution Layer • In smaller networks or single building backbones, the distribution layer may be omitted • The goal of the Distribution layer is to aggregate wiring closet, provide greater segmentation across the campus and provide higher throughput for localised traffic • Distribution layer sw ...
Networks on Chip (NoC)
... • minimizing logic and routing tables to achieve a lower area footprint • increasing performance by reducing delay and maximizing traffic utilization of the network • improving robustness to better adapt to changing traffic needs • Routing schemes can be classified into several categories • sta ...
... • minimizing logic and routing tables to achieve a lower area footprint • increasing performance by reducing delay and maximizing traffic utilization of the network • improving robustness to better adapt to changing traffic needs • Routing schemes can be classified into several categories • sta ...
Recognition of Control Chart Patterns Using Self Organization Models
... wnew.] . = W0 ld -I . + at] ...
... wnew.] . = W0 ld -I . + at] ...
14-InternetRouting - Rose
... – AS-PATH: contains the ASs through which the advert for the prefix passed: AS 67 AS 17 – NEXT-HOP: Indicates the specific internal-AS router to next-hop AS. (There may be multiple links from current AS to next-hop-AS.) ...
... – AS-PATH: contains the ASs through which the advert for the prefix passed: AS 67 AS 17 – NEXT-HOP: Indicates the specific internal-AS router to next-hop AS. (There may be multiple links from current AS to next-hop-AS.) ...
01_NF_CH08_OSIPhysicalLayer
... the binary digits of data communications. As a networking medium, wireless is not restricted to conductors or pathways, as are copper and fiber media. Wireless data communication technologies work well in open environments. However, certain construction materials used in buildings and structures, an ...
... the binary digits of data communications. As a networking medium, wireless is not restricted to conductors or pathways, as are copper and fiber media. Wireless data communication technologies work well in open environments. However, certain construction materials used in buildings and structures, an ...
100-101 (ICND1) - Galaxy Computer Education
... exam includes topics on the Operation of IP Data Networks; LAN Switching Technologies; IP Addressing (IPv4 & IPv6); IP Routing Technologies; IP Services (DHCP, NAT, ACLs); Network ...
... exam includes topics on the Operation of IP Data Networks; LAN Switching Technologies; IP Addressing (IPv4 & IPv6); IP Routing Technologies; IP Services (DHCP, NAT, ACLs); Network ...
Introducing the CRU WiebeTech Ditto™ Forensic FieldStation
... • StringGrab™ – Search source data for given strings (Data Carving) • HashGrab™ – Search source data for user supplied hashes (File Carving) • SDK – Linux VM, plug-in architecture to allow user to operate own tools • Management Console - Monitor multiple Ditto devices on network • Multiple Destinati ...
... • StringGrab™ – Search source data for given strings (Data Carving) • HashGrab™ – Search source data for user supplied hashes (File Carving) • SDK – Linux VM, plug-in architecture to allow user to operate own tools • Management Console - Monitor multiple Ditto devices on network • Multiple Destinati ...