Security: Protection Mechanisms, Trusted Systems
... – What does x without r mean for a directory? • Can access file if you know the name, but cannot list names ...
... – What does x without r mean for a directory? • Can access file if you know the name, but cannot list names ...
Cybersecurity Chapter 3 Test Review
... In order to provide flexible working conditions, a company has decided to allow some employees remote access into corporate headquarters. Which of the following security technologies could be used to provide remote access? (Select TWO). Subnetting NAT Firewall NAC VPN ...
... In order to provide flexible working conditions, a company has decided to allow some employees remote access into corporate headquarters. Which of the following security technologies could be used to provide remote access? (Select TWO). Subnetting NAT Firewall NAC VPN ...
Get a WIF of this!
... This presentation will focus on how WIF: Can be used with websites as well as web services. Makes life much easier for the developer. Opens up possibilities that normally have been prohibitively complex. Now to introduce the participants of this presentation: ...
... This presentation will focus on how WIF: Can be used with websites as well as web services. Makes life much easier for the developer. Opens up possibilities that normally have been prohibitively complex. Now to introduce the participants of this presentation: ...
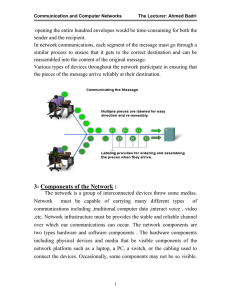
1-Introduction :
... The management of data as it flows through the network is also a role of the intermediary devices. These devices use the destination host address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Processes runnin ...
... The management of data as it flows through the network is also a role of the intermediary devices. These devices use the destination host address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Processes runnin ...
Best Practices for Wireless LAN Security & Operational Support
... Product was purchased by security for security purposes – but the reality is that it’s been as much a WLAN performance & management tool ...
... Product was purchased by security for security purposes – but the reality is that it’s been as much a WLAN performance & management tool ...
Scuba by Imperva - Database Vulnerability Scanner
... insiders and want to assess the risks they face. Unsure how to automate the discovery of database vulnerabilities, they often rely on manual work or wait for a vendor fix. Scuba is a free tool that scans leading enterprise databases for security vulnerabilities and configuration flaws, including pat ...
... insiders and want to assess the risks they face. Unsure how to automate the discovery of database vulnerabilities, they often rely on manual work or wait for a vendor fix. Scuba is a free tool that scans leading enterprise databases for security vulnerabilities and configuration flaws, including pat ...
MYDIGIPASS for Healthcare
... permit patient access to patient portals via username and password plus knowledge-based attributes or emerging technologies in lieu of passwords to reduce vulnerabilities in identity theft. HHS’s 2018-2020 milestone is to have at least 50% of health care organizations have implemented identity proof ...
... permit patient access to patient portals via username and password plus knowledge-based attributes or emerging technologies in lieu of passwords to reduce vulnerabilities in identity theft. HHS’s 2018-2020 milestone is to have at least 50% of health care organizations have implemented identity proof ...
Preparation Identification Containment
... - Select what kind of files can be lost / stolen and restrict the access for confidential files; - Create fake documents with watermarking that could be use as a proof of theft; - Notify targeted business users about what must be done and what is forbidden; - Configure logging capabilities in verbos ...
... - Select what kind of files can be lost / stolen and restrict the access for confidential files; - Create fake documents with watermarking that could be use as a proof of theft; - Notify targeted business users about what must be done and what is forbidden; - Configure logging capabilities in verbos ...
Intrusion Detection
... signature detection attack patterns are defined and they are used to decide on ...
... signature detection attack patterns are defined and they are used to decide on ...
Newfield National Bank > Home
... call the victim and pretend to be Internal Revenue Service (IRS) agents. In addition, there are malicious actors who use the tax season to spread malware and phishing emails. Tax scams where the malicious actor files the return in the victim’s name include both identity theft and identity fraud, as ...
... call the victim and pretend to be Internal Revenue Service (IRS) agents. In addition, there are malicious actors who use the tax season to spread malware and phishing emails. Tax scams where the malicious actor files the return in the victim’s name include both identity theft and identity fraud, as ...
Decision Support System
... A wrong configuration: a data path exists that allows an user in the 'visualization station' to re-write the sensor firmware. An unsatisfied employee: he/she discovers this vulnerability and he/she want to exploit it to perform a serious attack to the hydroelectric dam. Thus, he/she obtains the admi ...
... A wrong configuration: a data path exists that allows an user in the 'visualization station' to re-write the sensor firmware. An unsatisfied employee: he/she discovers this vulnerability and he/she want to exploit it to perform a serious attack to the hydroelectric dam. Thus, he/she obtains the admi ...
Whitepaper: Network Penetration Testing
... tify the security exposures that are used to surface when ...
... tify the security exposures that are used to surface when ...
Chapter 4
... 5 : allows inter-realm authentication, in beta test Kerberos v5 is an Internet standard specified in RFC1510, and used by many utilities To use Kerberos: need to have a KDC on your network need to have Kerberised applications running on all participating systems major problem - US export restriction ...
... 5 : allows inter-realm authentication, in beta test Kerberos v5 is an Internet standard specified in RFC1510, and used by many utilities To use Kerberos: need to have a KDC on your network need to have Kerberised applications running on all participating systems major problem - US export restriction ...
Detailed Overview of Security and Privacy lecture slides
... receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security ...
... receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security ...
Security & Privacy on the WWW
... receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security ...
... receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security ...
Cutting Edge VoIP Security Issues Color
... Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: ...
... Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: ...
PowerPoint Template - IP
... • Snapshot History • Completely record screen history for future analyze • Set different snapshot frequency on different application to focus on some sensitive information ...
... • Snapshot History • Completely record screen history for future analyze • Set different snapshot frequency on different application to focus on some sensitive information ...
Cyber Solutions for NEI 08-09 Whitepaper 119 KB
... The SecurityST Active Directory user and management functions can be used to limit functions for operators while enabling security functions for administrative users only. There is physical partitioning in the network levels between the Control Network (UDH) and the Supervisory Network (PDH). In add ...
... The SecurityST Active Directory user and management functions can be used to limit functions for operators while enabling security functions for administrative users only. There is physical partitioning in the network levels between the Control Network (UDH) and the Supervisory Network (PDH). In add ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... buyer’s experience. - Measures taken to protect information systems and their processes against all risks. In other words assure the systems’ availability when needed. The assurance includes all tools and defense methods. ...
... buyer’s experience. - Measures taken to protect information systems and their processes against all risks. In other words assure the systems’ availability when needed. The assurance includes all tools and defense methods. ...
Logical attack advisory for U.S. and Canada
... Other Dispenser Security Authentication levels WILL NOT protect against Black Box attacks. The only protection against Black Box attacks is a combination of Level 3 Authentication AND USB dispenser component from APTRA XFS 06.03. For Personas ATMs: Fleet modernization is an important part of sta ...
... Other Dispenser Security Authentication levels WILL NOT protect against Black Box attacks. The only protection against Black Box attacks is a combination of Level 3 Authentication AND USB dispenser component from APTRA XFS 06.03. For Personas ATMs: Fleet modernization is an important part of sta ...
Discovering Computers Fundamentals 3rd Edition
... Identify ways to safeguard against computer viruses, worms, Trojan horses, denial of service attacks, back doors, and spoofing Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways to protect against software thef ...
... Identify ways to safeguard against computer viruses, worms, Trojan horses, denial of service attacks, back doors, and spoofing Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways to protect against software thef ...
PHP Security
... http://examp.com/edit.php?update_table_submit=1&table=users+set+passw ord%3Daaa+where+user%3D%27admin%27%+%23 update users set password=aaa where user=“admin” # set name=$name ...
... http://examp.com/edit.php?update_table_submit=1&table=users+set+passw ord%3Daaa+where+user%3D%27admin%27%+%23 update users set password=aaa where user=“admin” # set name=$name ...
Security Features in Windows CE
... Setting FILE_ATTRIBUTE_SYSTEM on the volume file helps protect database volumes. System databases cannot be created inside database volumes that do not have FILE_ATTRIBUTE_SYSTEM set to block untrusted applications from accessing and/or deleting a file containing a system database using the Microsof ...
... Setting FILE_ATTRIBUTE_SYSTEM on the volume file helps protect database volumes. System databases cannot be created inside database volumes that do not have FILE_ATTRIBUTE_SYSTEM set to block untrusted applications from accessing and/or deleting a file containing a system database using the Microsof ...