Captain James Mills â Cyber Operations
... taken through the use of computer networks to disrupt, deny, degrade, manipulate, or destroy information resident in the target information system or computer networks, or the systems / networks themselves. ...
... taken through the use of computer networks to disrupt, deny, degrade, manipulate, or destroy information resident in the target information system or computer networks, or the systems / networks themselves. ...
V-NetLab: An Approach for Realizing Logically Isolated Networks for Security Experiments
... of the sending host network interface and receiving host interface2 . On the receiving host, the packet handler simply removes the encapsulated header and forwards the packet to corresponding vmnet interfaces according to the PT. 2.3 Controlled Remote Access to Virtual Networks V-NetLab allows tunne ...
... of the sending host network interface and receiving host interface2 . On the receiving host, the packet handler simply removes the encapsulated header and forwards the packet to corresponding vmnet interfaces according to the PT. 2.3 Controlled Remote Access to Virtual Networks V-NetLab allows tunne ...
DCN-7-Network_Security
... –At least 8 characters long and, »Including all types of symbols such as lowercase, uppercase, numbers and special characters. ...
... –At least 8 characters long and, »Including all types of symbols such as lowercase, uppercase, numbers and special characters. ...
Stego Intrusion Detection System (SIDS)
... • An attacker / virus could create (seemingly normal) HTTP traffic that contains important* data – Instructions for the program – Proprietary / sensitive information (secrets, credit card numbers, etc) ...
... • An attacker / virus could create (seemingly normal) HTTP traffic that contains important* data – Instructions for the program – Proprietary / sensitive information (secrets, credit card numbers, etc) ...
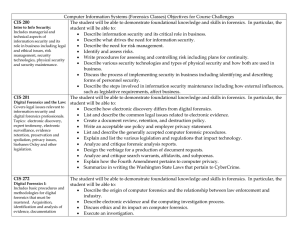
Computer Information Systems (Forensics Classes) Objectives for
... • Describe authentication, integrity and confidentiality and how they relate to security systems. • Describe the use of public key technology in networks and the issues associated with key management. • Compare and contrast the various mechanisms that provide authentication services, authentication, ...
... • Describe authentication, integrity and confidentiality and how they relate to security systems. • Describe the use of public key technology in networks and the issues associated with key management. • Compare and contrast the various mechanisms that provide authentication services, authentication, ...
AVOCENT DATA CENTER SOLUTIONS Secure, Centralized Data Center Management ®
... for global, enterprise IT. ...
... for global, enterprise IT. ...
Defense - Northwestern Networks Group
... Difficulties/Tasks for the attacker: 1. Need to find out where the target VM is located 2. Need to be co-resident with the target 3. Need to compromise valuable information from the target What we do: 1. Explore how to map the cloud and understand instance creation parameters to establish co-residen ...
... Difficulties/Tasks for the attacker: 1. Need to find out where the target VM is located 2. Need to be co-resident with the target 3. Need to compromise valuable information from the target What we do: 1. Explore how to map the cloud and understand instance creation parameters to establish co-residen ...
(FIPS) 140-2 - Aviat Networks
... Example: Lab can check code submitted by manufacturer. Well known code library function Glibc function is OK for general use but not quite random enough for encryption ...
... Example: Lab can check code submitted by manufacturer. Well known code library function Glibc function is OK for general use but not quite random enough for encryption ...
Towards a Trustworthy Android Ecosystem
... • Useful for malware detection • Most root-capable malware can be logged for vulnerability conditions • Rage-against-the-cage – Number of live processes for a user reaches a threshold ...
... • Useful for malware detection • Most root-capable malware can be logged for vulnerability conditions • Rage-against-the-cage – Number of live processes for a user reaches a threshold ...
XML Security Standards — Overview for the Non - Events
... Defines rules to encrypt XML and record parameters Support all technologies in common use Key problem: Encrypted data not Schema-valid Solution: None ...
... Defines rules to encrypt XML and record parameters Support all technologies in common use Key problem: Encrypted data not Schema-valid Solution: None ...
Ibrahim Aljubayri`s presentation on Secure Network Channel among
... needed for SOSTC into kernel memory at the system boot-time. The initial data are an encryption key for packet encryption, an authentication key for packet authentication and IP addresses of secure OS to be applied to SOSTC. An encryption key and an authentication key are self-encoded within kernel ...
... needed for SOSTC into kernel memory at the system boot-time. The initial data are an encryption key for packet encryption, an authentication key for packet authentication and IP addresses of secure OS to be applied to SOSTC. An encryption key and an authentication key are self-encoded within kernel ...
Green-Aware Security
... sophisticated user-interfaces, specific design patterns are adopted. But, they increase the risk of attacks such as request forgeries; ...
... sophisticated user-interfaces, specific design patterns are adopted. But, they increase the risk of attacks such as request forgeries; ...
InfoSec Acceptable Use Policy. (nd). SANS Institute. Retrieved from
... permissions on non-default CIFS shares, which allows remote authenticated users to read, modify, create, or delete arbitrary files via standard filesystem operations” (Common Vulnerabilities and Exposures,2013). 2. Policy is not enforced to mobile users: “IBM Lotus Notes Traveler before 8.5.1.3, whe ...
... permissions on non-default CIFS shares, which allows remote authenticated users to read, modify, create, or delete arbitrary files via standard filesystem operations” (Common Vulnerabilities and Exposures,2013). 2. Policy is not enforced to mobile users: “IBM Lotus Notes Traveler before 8.5.1.3, whe ...
PPT_ch02
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
Security+ Guide to Network Security Fundamentals, Third Edition
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
Introduction to Information Security Chapter N
... Broad category of activities that breach confidentiality – Unauthorized accessing of information – Competitive intelligence (the legal and ethical collection and analysis of information regarding the capabilities, vulnerabilities, and intentions of business competitors) vs. espionage – Shoulder su ...
... Broad category of activities that breach confidentiality – Unauthorized accessing of information – Competitive intelligence (the legal and ethical collection and analysis of information regarding the capabilities, vulnerabilities, and intentions of business competitors) vs. espionage – Shoulder su ...
Slides - School of Information Sciences
... Composed of a sequence of instructions that is interpreted rather than executed directly Infected “executable” isn’t machine code Relies on something “executed” inside application data Example: Melissa virus infected Word 97/98 docs ...
... Composed of a sequence of instructions that is interpreted rather than executed directly Infected “executable” isn’t machine code Relies on something “executed” inside application data Example: Melissa virus infected Word 97/98 docs ...
Information security in a youth organisation?
... Securing computer networks in youth houses The information security policy in the youth houses ...
... Securing computer networks in youth houses The information security policy in the youth houses ...
Playing it Safe: Document Destruction Best Practices - Shred-it
... It means a department or companywide commitment to shredding all documents on a regular basis. Standardising document destruction procedures will allow your organisation to align its rules and regulations with its information security goals and needs. A shred-all policy is a way to make sure there a ...
... It means a department or companywide commitment to shredding all documents on a regular basis. Standardising document destruction procedures will allow your organisation to align its rules and regulations with its information security goals and needs. A shred-all policy is a way to make sure there a ...
12_Auth_nemo
... – User provides one or more samples of biometric – Raw data are normalized and entered as a template – Tolerances for noise are set (FRR vs. FAR) ...
... – User provides one or more samples of biometric – Raw data are normalized and entered as a template – Tolerances for noise are set (FRR vs. FAR) ...
The Importance of Computer Network Incident Reporting
... In order to assure its information assets the DoD adopted an Information Assurance (IA) posture designated to protect and defend its electronic information and information systems’ integrity, availability, authentication, confidentiality, and nonrepudiation (NSTISSI No. 4009, 1999). IA encompasses p ...
... In order to assure its information assets the DoD adopted an Information Assurance (IA) posture designated to protect and defend its electronic information and information systems’ integrity, availability, authentication, confidentiality, and nonrepudiation (NSTISSI No. 4009, 1999). IA encompasses p ...
pps - AquaLab - Northwestern University
... The security environment Security – General problem involved in making sure files are not read/modified by unauthorized people; – It includes technical, administrative, legal and political issues ...
... The security environment Security – General problem involved in making sure files are not read/modified by unauthorized people; – It includes technical, administrative, legal and political issues ...
ATLAS® Intelligence Feed
... threats from entering the network, it enables other security devices to do the jobs they were intended to do. • Pravail® Network Security Intelligence: Security intelligence provided by ATLAS Intelligence Feed detects security events immediately upon compromise. With Pravail Network Security Intelli ...
... threats from entering the network, it enables other security devices to do the jobs they were intended to do. • Pravail® Network Security Intelligence: Security intelligence provided by ATLAS Intelligence Feed detects security events immediately upon compromise. With Pravail Network Security Intelli ...