Security and Availability of Client Data
... content serving, and reporting activities taking place. Network security is ensured based upon the following approaches: ...
... content serving, and reporting activities taking place. Network security is ensured based upon the following approaches: ...
Employee Internet Use Monitoring and Filtering Policy
... 1.7 1836 Technologies will monitor all user activity on the Internet at network level for the purposes specified in Section 4.1. Information recorded as part of this automated monitoring process includes user identification, domain names of websites visited, duration of visits, and files uploaded to ...
... 1.7 1836 Technologies will monitor all user activity on the Internet at network level for the purposes specified in Section 4.1. Information recorded as part of this automated monitoring process includes user identification, domain names of websites visited, duration of visits, and files uploaded to ...
Auditing (cont'd.) - Elgin Community College
... • Stop logged-on users from accessing files and folders that they are not assigned read or write permission to • Relatively easy to work around NTFS permissions • When you have physical access to the computer • To secure data on desktop computers and laptops, ...
... • Stop logged-on users from accessing files and folders that they are not assigned read or write permission to • Relatively easy to work around NTFS permissions • When you have physical access to the computer • To secure data on desktop computers and laptops, ...
Introduction
... intentional actions from occuring in a system. – These potential actions are threats. – Threats that are carried out are attacks. – Intentional attacks are carried out by an attacker. – Objects of attacks are assets. ...
... intentional actions from occuring in a system. – These potential actions are threats. – Threats that are carried out are attacks. – Intentional attacks are carried out by an attacker. – Objects of attacks are assets. ...
Security & Cryptography
... A new IPSec SA is defined for the ESP tunnel, and data begins to be transferred New term: Selector- a logical construct similar to a route, that allows the gateway to determine if an inbound packet is to be encrypted and passed over a particular SA ...
... A new IPSec SA is defined for the ESP tunnel, and data begins to be transferred New term: Selector- a logical construct similar to a route, that allows the gateway to determine if an inbound packet is to be encrypted and passed over a particular SA ...
Managing the Digital Firm
... 1. Achieving a sensible balance between too little control and too much. ...
... 1. Achieving a sensible balance between too little control and too much. ...
FAKEM RAT: Malware Disguised as Windows Messenger and
... The perpetrators of targeted attacks aim to maintain persistent presence in a target network in order to extract sensitive data when needed. To maintain persistent presence, attackers seek to blend in with normal network traffic and use ports that are typically allowed by firewalls. As a result, man ...
... The perpetrators of targeted attacks aim to maintain persistent presence in a target network in order to extract sensitive data when needed. To maintain persistent presence, attackers seek to blend in with normal network traffic and use ports that are typically allowed by firewalls. As a result, man ...
Defending Office 365 Against Denial-of-Service Attacks
... Microsoft’s DoS Defense Strategy Microsoft’s strategy for defending against DoS is somewhat unique due to our scale and global footprint. This scale allows Microsoft to utilize strategies and techniques that few organizations (providers or customer organizations) can match. The cornerstone of our Do ...
... Microsoft’s DoS Defense Strategy Microsoft’s strategy for defending against DoS is somewhat unique due to our scale and global footprint. This scale allows Microsoft to utilize strategies and techniques that few organizations (providers or customer organizations) can match. The cornerstone of our Do ...
e-Security extra notes
... Security Technologies (cont.) Virtual private networks (VPNs)—use public Internet to carry information but remains private Encryption—scramble communications Authentication—ensure information remains untampered with and comes from legitimate source Access control—verify identity of anyone using net ...
... Security Technologies (cont.) Virtual private networks (VPNs)—use public Internet to carry information but remains private Encryption—scramble communications Authentication—ensure information remains untampered with and comes from legitimate source Access control—verify identity of anyone using net ...
CSCI6268L37
... – Key generation, encryption – Security • Basic RSA bad, factoring is best known attack, factoring technology ...
... – Key generation, encryption – Security • Basic RSA bad, factoring is best known attack, factoring technology ...
Firewalls
... Identify the various approaches to remote and dial-up access protection—that is, how these connection methods can be controlled to assure confidentiality of information, and the authentication and authorization of users Explain content filtering technology Describe the technology that enables ...
... Identify the various approaches to remote and dial-up access protection—that is, how these connection methods can be controlled to assure confidentiality of information, and the authentication and authorization of users Explain content filtering technology Describe the technology that enables ...
Public Presentation - Academic Conferences
... – Joel Brenner, counterintelligence executive in CNN.com, October 19, 2007 ...
... – Joel Brenner, counterintelligence executive in CNN.com, October 19, 2007 ...
MALWARE ALERT: PROTECT YOUR BUSINESS AND RAISE
... In this case, the malware creates a beneficiary account on your online banking tool and then enters a fraudulent transfer debited from your firm's bank account. If need be, it will display a fake page prompting the accountant to enter a code that is required to execute the transfer (such as an SMS c ...
... In this case, the malware creates a beneficiary account on your online banking tool and then enters a fraudulent transfer debited from your firm's bank account. If need be, it will display a fake page prompting the accountant to enter a code that is required to execute the transfer (such as an SMS c ...
Web Security Security+ Guide to Network Security Fundamentals
... • Buffer overflow attacks are common ways to gain unauthorized access to Web servers • SMTP relay attacks allow spammers to send thousands of e-mail messages to users • Web programming tools provide another foothold for Web attacks • Dynamic content can also be used by attackers – Sometimes called r ...
... • Buffer overflow attacks are common ways to gain unauthorized access to Web servers • SMTP relay attacks allow spammers to send thousands of e-mail messages to users • Web programming tools provide another foothold for Web attacks • Dynamic content can also be used by attackers – Sometimes called r ...
Security Services Gateways
... Networks firewall/VPN gateway, the antispam engine filters incoming email from known spam and phishing users, acting as a first line of defense. When a known malicious email arrives, it is blocked and/or flagged so that the email server can take appropriate action. Integrated antispam is available o ...
... Networks firewall/VPN gateway, the antispam engine filters incoming email from known spam and phishing users, acting as a first line of defense. When a known malicious email arrives, it is blocked and/or flagged so that the email server can take appropriate action. Integrated antispam is available o ...
PCI Self-Assessment Questionnaire
... other electronic data gathered by the merchant/agent, and so on). This term also accounts for other personal insights gathered about the cardholder ‘i.e., addresses, telephone numbers, and so on). ...
... other electronic data gathered by the merchant/agent, and so on). This term also accounts for other personal insights gathered about the cardholder ‘i.e., addresses, telephone numbers, and so on). ...
Document
... Introduction to Cyber Network Defense • Cyber Network Defense (CND) is continuously improving process for defending IT assets • The CND approach in this Chapter includes: – Lightweight process for CND – Set of open source scripts for network monitoring and Advanced Log Analysis (ALA) on Backtrack – ...
... Introduction to Cyber Network Defense • Cyber Network Defense (CND) is continuously improving process for defending IT assets • The CND approach in this Chapter includes: – Lightweight process for CND – Set of open source scripts for network monitoring and Advanced Log Analysis (ALA) on Backtrack – ...
Web Site Development Tools
... only during the current session and discarded afterward • In the U.S., session keys usually consist of 16 digits equaling 128 bits, also called 128-bit keys E-Business Technologies ...
... only during the current session and discarded afterward • In the U.S., session keys usually consist of 16 digits equaling 128 bits, also called 128-bit keys E-Business Technologies ...
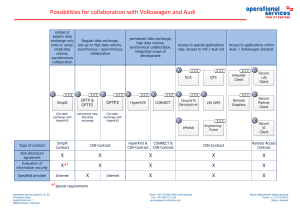
Possibilities for collaboration with Volkswagen
... The users in the partner company are the company's own internal permanent employees. In particular, no loan and temporary staff or subcontractors are deployed. All users are managed in a room reservation plan with reference to the workplace (room/ network socket) and the terminal used. Only authoriz ...
... The users in the partner company are the company's own internal permanent employees. In particular, no loan and temporary staff or subcontractors are deployed. All users are managed in a room reservation plan with reference to the workplace (room/ network socket) and the terminal used. Only authoriz ...
Firewall and VPNs - Ohio State Computer Science and Engineering
... Like filtering firewalls, do not usually look at data traffic flowing between two networks, but prevent direct connections between one network and another Accomplished by creating tunnels connecting specific processes or systems on each side of the firewall, and allow only authorized traffic in ...
... Like filtering firewalls, do not usually look at data traffic flowing between two networks, but prevent direct connections between one network and another Accomplished by creating tunnels connecting specific processes or systems on each side of the firewall, and allow only authorized traffic in ...
6 - Computer Science and Engineering
... Like filtering firewalls, do not usually look at data traffic flowing between two networks, but prevent direct connections between one network and another Accomplished by creating tunnels connecting specific processes or systems on each side of the firewall, and allow only authorized traffic in ...
... Like filtering firewalls, do not usually look at data traffic flowing between two networks, but prevent direct connections between one network and another Accomplished by creating tunnels connecting specific processes or systems on each side of the firewall, and allow only authorized traffic in ...
Chap 12
... Identify active detection and passive detection features of both host- and network-based IDS products continued… ...
... Identify active detection and passive detection features of both host- and network-based IDS products continued… ...
Computer Security and Penetration Testing Chapter 17 Linux
... • Basic hacks for a Linux system begin with physical access • Some Linux and UNIX-based operating systems store encrypted login passwords in a file called /etc/passwd • Some UNIX and Linux distros store passwords in a file called /etc/shadow Computer Security and Penetration Testing ...
... • Basic hacks for a Linux system begin with physical access • Some Linux and UNIX-based operating systems store encrypted login passwords in a file called /etc/passwd • Some UNIX and Linux distros store passwords in a file called /etc/shadow Computer Security and Penetration Testing ...