W3Perl A free logfile analyzer
... – Check traffic by file extension (find easily unsolicited files) ...
... – Check traffic by file extension (find easily unsolicited files) ...
dreamweaver_ch01
... Keeps track of relationships between pages Graphical representation of pages Shows the folder structure ...
... Keeps track of relationships between pages Graphical representation of pages Shows the folder structure ...
Hacking Overview Pres.
... software such as PCAnywhere without setting the software up correctly. War Dialer finds these numbers by going through a range of phone numbers listening for a modem. Demon Dialer tries a brute force password attack on a found connection. Typically: war dialing will find an unsecured connectio ...
... software such as PCAnywhere without setting the software up correctly. War Dialer finds these numbers by going through a range of phone numbers listening for a modem. Demon Dialer tries a brute force password attack on a found connection. Typically: war dialing will find an unsecured connectio ...
Intrusion Detection Systems
... them and inserts them back into the network. There are few programs/source codes available for doing a TCP hijack. Juggernaut, T-Sight and Hunt are some these programs. http://www.sans.org/infosecFAQ/threats/middle.htm ...
... them and inserts them back into the network. There are few programs/source codes available for doing a TCP hijack. Juggernaut, T-Sight and Hunt are some these programs. http://www.sans.org/infosecFAQ/threats/middle.htm ...
Chapter 7 E-commerce: The Internet, intranets, and extranets
... An extranet is similar to an intranet but it enables the firm’s business partners (e.g., suppliers or customers) to access the firm’s intranet Once an organization links its network to the Internet theoretically anyone can access the firm’s network. With respect to an extranet, firms want to restric ...
... An extranet is similar to an intranet but it enables the firm’s business partners (e.g., suppliers or customers) to access the firm’s intranet Once an organization links its network to the Internet theoretically anyone can access the firm’s network. With respect to an extranet, firms want to restric ...
Building an in-depth defense with Vectra and sandbox security
... command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from hosts under his control as a result of downloading the exploit. Cyber attacks that are targeted differ from bo ...
... command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from hosts under his control as a result of downloading the exploit. Cyber attacks that are targeted differ from bo ...
INTRODUCTION TO INFORMATION SYSTEMS TECHNOLOGY
... Ping messages (To know if a potential victim exist) Supervisory messages (To know if victim available) Tracert, Traceroute (to know about security systems) Check the Internet (e.g. www.cert.org) for latest systems vulnerabilities Trying millions of usernames and passwords ...
... Ping messages (To know if a potential victim exist) Supervisory messages (To know if victim available) Tracert, Traceroute (to know about security systems) Check the Internet (e.g. www.cert.org) for latest systems vulnerabilities Trying millions of usernames and passwords ...
Chapter 2: Attackers and Their Attacks
... Download automated hacking software from Web sites and use it to break into computers Tend to be young computer users with large amounts of leisure time, which they can use to attack systems ...
... Download automated hacking software from Web sites and use it to break into computers Tend to be young computer users with large amounts of leisure time, which they can use to attack systems ...
Creating web pages using html
... • (Note: there are different ways of embedding content, this is one of the easier ways). • Like text, multi-media such as images and videos can be embedded into a website. • The multi-media can either be local (on the same computer as your web page document) or external (an external website such as: ...
... • (Note: there are different ways of embedding content, this is one of the easier ways). • Like text, multi-media such as images and videos can be embedded into a website. • The multi-media can either be local (on the same computer as your web page document) or external (an external website such as: ...
BLADE: An Attack-Agnostic Approach for Preventing Drive
... • BLADE, a system that effectively immunizes a host against all forms of drive-by download malware installs. – BLADE is both attack and browser agnostic. – BLADE relies on limited semantic knowledge about a handful of user interface (UI) elements common across web browser applications. – BLADE focus ...
... • BLADE, a system that effectively immunizes a host against all forms of drive-by download malware installs. – BLADE is both attack and browser agnostic. – BLADE relies on limited semantic knowledge about a handful of user interface (UI) elements common across web browser applications. – BLADE focus ...
html
... Now, all you need to do is learn these tags: http://www.w3schools.com/tags/ref_byfunc.asp (Ignore the ones marked “new” for now) (Ignore the “not supported” ones) ...
... Now, all you need to do is learn these tags: http://www.w3schools.com/tags/ref_byfunc.asp (Ignore the ones marked “new” for now) (Ignore the “not supported” ones) ...
Remote Access - York Technical College
... Asymmetric – two keys – public key encrypts the message; the private key decrypts. ...
... Asymmetric – two keys – public key encrypts the message; the private key decrypts. ...
Information Assurance Presentation
... adjacent memory area, overwriting what was already there, including data or instructions. Malicious hackers have become proficient at leveraging such overflows to introduce their own code into programs, effectively hijacking the computer. At the same time, overflows occur when programmers do not i ...
... adjacent memory area, overwriting what was already there, including data or instructions. Malicious hackers have become proficient at leveraging such overflows to introduce their own code into programs, effectively hijacking the computer. At the same time, overflows occur when programmers do not i ...
Lazy Garbage Collection of Recovery State for Fault – Tolerant
... A buffer is a contiguous allocated chunk of memory, such as an array or a pointer in C Buffer overflow occurs when a program or process tries to store more data in a buffer than it was intended to hold Buffer overflows are exploited to change the flow of a program in execution Buffer overflows are b ...
... A buffer is a contiguous allocated chunk of memory, such as an array or a pointer in C Buffer overflow occurs when a program or process tries to store more data in a buffer than it was intended to hold Buffer overflows are exploited to change the flow of a program in execution Buffer overflows are b ...
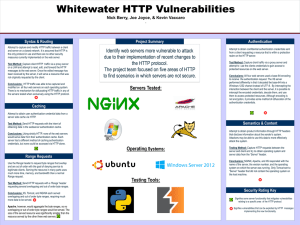
Here is the Original File
... the only protocol in use and there are no other security measures currently implemented on the web server. Test Method: Capture client HTTP traffic via a proxy server on a LAN and attempt to read, edit, and forward the HTTP messages to the web server. Once the edited message has been received by the ...
... the only protocol in use and there are no other security measures currently implemented on the web server. Test Method: Capture client HTTP traffic via a proxy server on a LAN and attempt to read, edit, and forward the HTTP messages to the web server. Once the edited message has been received by the ...
Unit 2 c. The Internet
... A web page is a file that is loaded by a web browser. It is written in HTML code, and contains hyperlinks. When you click on to a hyperlink, it takes you to another web page, either on the same site or a different one. Most web sites are several pages linked together which you navigate through using ...
... A web page is a file that is loaded by a web browser. It is written in HTML code, and contains hyperlinks. When you click on to a hyperlink, it takes you to another web page, either on the same site or a different one. Most web sites are several pages linked together which you navigate through using ...
Unit 2 c. The Internet
... A web page is a file that is loaded by a web browser. It is written in HTML code, and contains hyperlinks. When you click on to a hyperlink, it takes you to another web page, either on the same site or a different one. Most web sites are several pages linked together which you navigate through using ...
... A web page is a file that is loaded by a web browser. It is written in HTML code, and contains hyperlinks. When you click on to a hyperlink, it takes you to another web page, either on the same site or a different one. Most web sites are several pages linked together which you navigate through using ...
Powerpoint
... – Machines require low-level specific instructions – Humans require high-level abstraction ...
... – Machines require low-level specific instructions – Humans require high-level abstraction ...
The Top Ten of Security
... 1. CISSP – Certified information systems security professional – general security knowledge – ...
... 1. CISSP – Certified information systems security professional – general security knowledge – ...
Using port pairing to simplify transparent mode
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
us-16-Price-Building-a-Product-Security-Incident
... • How do you want to capture investigation details? • Case management db (doesn’t have to be complicated, can be specific fields captured in Jira) ...
... • How do you want to capture investigation details? • Case management db (doesn’t have to be complicated, can be specific fields captured in Jira) ...
The World Wide Web (WWW)
... keywords and web addresses where these keywords were already found the web crawler is working in the background and does only actualize the database when you invoke Google, you search in Google's database, not in the Web! not all Web pages can be found, because not all are in the database ...
... keywords and web addresses where these keywords were already found the web crawler is working in the background and does only actualize the database when you invoke Google, you search in Google's database, not in the Web! not all Web pages can be found, because not all are in the database ...
Chapter 1: Security Problems in Computing
... This story was told me by a banker whom I have every reason to trust. It shows the dangers of incorrect data in the computer system, though I seriously doubt that a computer was directly involved in the event. The event probably took place in the early 1960’s. The proprietor of a small pool hall was ...
... This story was told me by a banker whom I have every reason to trust. It shows the dangers of incorrect data in the computer system, though I seriously doubt that a computer was directly involved in the event. The event probably took place in the early 1960’s. The proprietor of a small pool hall was ...