Microsoft Word - Daviszone.org
... Regularly working with Fortune 500 companies, their administrators and on their servers. Wrote scripts to help resolve issues. Supervisor: Chris Woolsey (contact details available upon request) 08/01/05 til 03/01/07 ...
... Regularly working with Fortune 500 companies, their administrators and on their servers. Wrote scripts to help resolve issues. Supervisor: Chris Woolsey (contact details available upon request) 08/01/05 til 03/01/07 ...
OSCAR-ENGAGE Refactoring – Progress and Future Work
... But not sacrifice demonstration of features Provide pre-installed demonstrations of software using real scientific applications Straightforward, minimum number of steps to use ...
... But not sacrifice demonstration of features Provide pre-installed demonstrations of software using real scientific applications Straightforward, minimum number of steps to use ...
Review Questions
... a vulnerability. A. attack B. threat C. risk D. exploitation 2. _____ is a systematic and structured approach to managing the potential for loss that is related to a threat. A. Asset management B. Risk assessment (RA) C. Threat mitigation D. Risk management 3. Each of the following is a step in risk ...
... a vulnerability. A. attack B. threat C. risk D. exploitation 2. _____ is a systematic and structured approach to managing the potential for loss that is related to a threat. A. Asset management B. Risk assessment (RA) C. Threat mitigation D. Risk management 3. Each of the following is a step in risk ...
CL16: Building Windows Phone Applications with Silverlight (Part 1)
... Application model Out of Browser APIs Browser & plug-in specific APIs HTML Dom Bridge ...
... Application model Out of Browser APIs Browser & plug-in specific APIs HTML Dom Bridge ...
The Java Crypto API - Computer Science
... the IP address for the domain. • DNS can contact another name server and try to find the IP address for the name requested. It may have to do this multiple times. • DNS can say, "I don't know the IP address for the domain you requested, but here's the IP address for a name server that knows more tha ...
... the IP address for the domain. • DNS can contact another name server and try to find the IP address for the name requested. It may have to do this multiple times. • DNS can say, "I don't know the IP address for the domain you requested, but here's the IP address for a name server that knows more tha ...
ServicesResources
... Web documents are created using HTML which is a markup language, or tags, which is used to create Web pages. HTML tells the Web browser how to display the text contained in the Web pages. There are a number of user-friendly web authoring software, such as Dreamweaver, that allow you to generate HTML ...
... Web documents are created using HTML which is a markup language, or tags, which is used to create Web pages. HTML tells the Web browser how to display the text contained in the Web pages. There are a number of user-friendly web authoring software, such as Dreamweaver, that allow you to generate HTML ...
communicate
... • TCP slow start: just do it and get it over with • pipelining as an alternative to multiple connections And some new complexities resulting from their use, e.g.: • request/response framing and pairing • unexpected connection breakage Just ask anyone from Akamai... ...
... • TCP slow start: just do it and get it over with • pipelining as an alternative to multiple connections And some new complexities resulting from their use, e.g.: • request/response framing and pairing • unexpected connection breakage Just ask anyone from Akamai... ...
CHAP10
... using a middleware called Active Data Objects (ADO). The con variable is a connection to the database, which was established in the code of Box C. The rsRes variable contains the result set of the query (the rows returned from the query) ...
... using a middleware called Active Data Objects (ADO). The con variable is a connection to the database, which was established in the code of Box C. The rsRes variable contains the result set of the query (the rows returned from the query) ...
Imperva Incapsula Content Delivery Network
... reduce connection time by managing connections more efficiently. Upon the first request to a website, the pre-pooling opens several TCP connections in advance between Incapsula and the origin server, which remain available in stand-by mode. This saves time by allowing the required website resources ...
... reduce connection time by managing connections more efficiently. Upon the first request to a website, the pre-pooling opens several TCP connections in advance between Incapsula and the origin server, which remain available in stand-by mode. This saves time by allowing the required website resources ...
Introduction to the course and to the world wide web
... • You can choose your user name as a short form of your own name. • It should be all lowercases and can not have spaces. • Please don't choose an insecure password. ...
... • You can choose your user name as a short form of your own name. • It should be all lowercases and can not have spaces. • Please don't choose an insecure password. ...
Chapter04
... An open mail relay occurs when a mail server processes mail messages when neither the sender nor the recipient is a local user. The mail server is used to “bounce” e-mail from one outside source to other sources. In this case the mail server becomes an entirely unrelated third party. Spammers use op ...
... An open mail relay occurs when a mail server processes mail messages when neither the sender nor the recipient is a local user. The mail server is used to “bounce” e-mail from one outside source to other sources. In this case the mail server becomes an entirely unrelated third party. Spammers use op ...
20121101
... • During the stepping from system to system, security controls detected an attack in progress. The race was now on. • Attacker had to move very quickly during this phase of finding a valuable target. ...
... • During the stepping from system to system, security controls detected an attack in progress. The race was now on. • Attacker had to move very quickly during this phase of finding a valuable target. ...
csc4000w_2006_ii_notes_2
... parameters are passed to Web applications. For a GET request, the URL contains ...
... parameters are passed to Web applications. For a GET request, the URL contains ...
Chap 3
... information. (T/F) Name three types of DoS attack. The ping of death works based on using very large ICMP packets that must be fragmented to send and when reassembled are too large for the receiver’s buffer. (T/F) How can a router stop packets from entering the network whose source IP address is spo ...
... information. (T/F) Name three types of DoS attack. The ping of death works based on using very large ICMP packets that must be fragmented to send and when reassembled are too large for the receiver’s buffer. (T/F) How can a router stop packets from entering the network whose source IP address is spo ...
Attacking 802.11 Networks
... • “Crunchy on the outside, soft and chewy on the inside” – Mentos Network Design – Common to many organizations with few security resources to manage client devices – Attacker uses stepping-stone attacks ...
... • “Crunchy on the outside, soft and chewy on the inside” – Mentos Network Design – Common to many organizations with few security resources to manage client devices – Attacker uses stepping-stone attacks ...
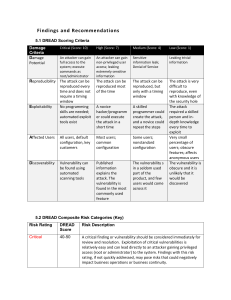
Findings and Recommendations
... A severe finding or vulnerability should be considered for review and resolution within a short time frame. These vulnerabilities can lead to an attacker gaining non-privileged access (standard user) to a system, or the vulnerability can be leveraged to gain elevated level of access. Moderate risk f ...
... A severe finding or vulnerability should be considered for review and resolution within a short time frame. These vulnerabilities can lead to an attacker gaining non-privileged access (standard user) to a system, or the vulnerability can be leveraged to gain elevated level of access. Moderate risk f ...
A Common Language for Computer Security Incidents
... Flexible enough to allow site-specific low-level terms Develop taxonomy for these terms ...
... Flexible enough to allow site-specific low-level terms Develop taxonomy for these terms ...
Client/Server and Middleware
... using a middleware called Active Data Objects (ADO). The con variable is a connection to the database, which was established in the code of Box C. The rsRes variable contains the result set of the query (the rows returned from the query) ...
... using a middleware called Active Data Objects (ADO). The con variable is a connection to the database, which was established in the code of Box C. The rsRes variable contains the result set of the query (the rows returned from the query) ...
Slides - TAMU Computer Science Faculty Pages
... • Authenticity is the identification and assurance of the origin of information • Integrity refers to the trustworthiness of data or resources in terms of preventing improper and unauthorized changes • Preventing unauthorized changes to data or resources. • Availability refers to the ability to use ...
... • Authenticity is the identification and assurance of the origin of information • Integrity refers to the trustworthiness of data or resources in terms of preventing improper and unauthorized changes • Preventing unauthorized changes to data or resources. • Availability refers to the ability to use ...