![[edit] Methods of attack](http://s1.studyres.com/store/data/021898195_1-cd36b3b46913bad45bc8311de7b00618-300x300.png)
[edit] Methods of attack
... Attackers have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks. The most aggressive of these peer-to-peer-DDoS attacks exploits DC++. Peer-to-peer attacks are different from regular botnet-based attacks. With peer-to-peer there is no botnet and the attacker d ...
... Attackers have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks. The most aggressive of these peer-to-peer-DDoS attacks exploits DC++. Peer-to-peer attacks are different from regular botnet-based attacks. With peer-to-peer there is no botnet and the attacker d ...
Using PowerCenter as a RESTful Web Service Client
... support REST-based calls. However, you can use PowerCenter as a web service client to a RESTful web service outside of PowerCenter. In this example, you create a PowerCenter mapping and use an HTTP Transformation to invoke HTTP commands to access the web service resources. The workflow searches a we ...
... support REST-based calls. However, you can use PowerCenter as a web service client to a RESTful web service outside of PowerCenter. In this example, you create a PowerCenter mapping and use an HTTP Transformation to invoke HTTP commands to access the web service resources. The workflow searches a we ...
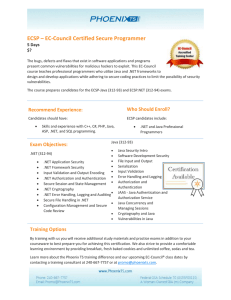
ECSP – EC-Council Certified Secure Programmer
... The bugs, defects and flaws that exist in software applications and programs present common vulnerabilities for malicious hackers to exploit. This EC-Council course teaches professional programmers who utilize Java and .NET frameworks to design and develop applications while adhering to secure codin ...
... The bugs, defects and flaws that exist in software applications and programs present common vulnerabilities for malicious hackers to exploit. This EC-Council course teaches professional programmers who utilize Java and .NET frameworks to design and develop applications while adhering to secure codin ...
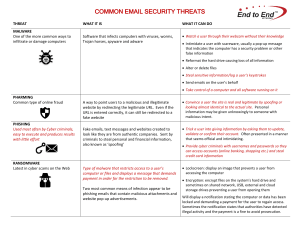
COMMON EMAIL SECURITY THREATS
... Watch a user through their webcam without their knowledge Intimidate a user with scareware, usually a pop-up message that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive i ...
... Watch a user through their webcam without their knowledge Intimidate a user with scareware, usually a pop-up message that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive i ...
Web Essentials: Clients, Servers, and Communication
... Guy-Vincent Jourdan :: CSI 3140 :: based on Jeffrey C. Jackson’s slides ...
... Guy-Vincent Jourdan :: CSI 3140 :: based on Jeffrey C. Jackson’s slides ...
18_DataCenter_Security_Overview
... Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - The term of probe refers to an individua ...
... Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - The term of probe refers to an individua ...
18_DataCenter_Security_Overview
... Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - The term of probe refers to an individua ...
... Common attacks – After talking about Threats and Vulnerabilities, we will discuss how they are exploited by the most frequent attacks. •Scanning or Probing – this activity precedes an attack to gain access by discovering information about system or network. - The term of probe refers to an individua ...
Implementing Security for Electronic Commerce
... one of the most serious threats to client computers Threats can hide in Web pages Downloaded graphics and plug-ins E-mail attachments ...
... one of the most serious threats to client computers Threats can hide in Web pages Downloaded graphics and plug-ins E-mail attachments ...
internet
... includes two or more words (labels). • The last label in a domain name is usually a two- or three-letter code called a top-level ...
... includes two or more words (labels). • The last label in a domain name is usually a two- or three-letter code called a top-level ...
General IT Auditing Techniques
... What risk does the vulnerability present? What is the source of the vulnerability? What is the potential impact of the vulnerability? What is the likelihood of the vulnerability being exploited? What should be done to mitigate the vulnerability? ...
... What risk does the vulnerability present? What is the source of the vulnerability? What is the potential impact of the vulnerability? What is the likelihood of the vulnerability being exploited? What should be done to mitigate the vulnerability? ...
coms3995 - Computer Science, Columbia University
... • How can I sign a contract without a pen? • How can I prove to a computer that it's really me? ...
... • How can I sign a contract without a pen? • How can I prove to a computer that it's really me? ...
O New Remote File Access:
... authenticate connecting users or their computers. In addition, SSL encrypts the data that you send, and incorporates a mechanism for detecting any alteration in transit, so that eavesdropping on or tampering with Web traffic is almost impossible. This is essential for safely transmitting highly conf ...
... authenticate connecting users or their computers. In addition, SSL encrypts the data that you send, and incorporates a mechanism for detecting any alteration in transit, so that eavesdropping on or tampering with Web traffic is almost impossible. This is essential for safely transmitting highly conf ...
.NET Framework Overview and Base Classes
... – Integrate with Shopping Cart – Amazon Associates Program ...
... – Integrate with Shopping Cart – Amazon Associates Program ...
PowerPoint
... contains information about the page contains the page content
... contains information about the page contains the page content
contains inline elements that make up a heading ...
David Mannies resume
... Principal developer of a report generator for kiosk utilization. The report generator, a Java applet this is accessed via HTML and JavaScript, compiles report data from the kiosk application logs and returns the report as a XML document. A XSL template displays the report in Internet Explorer. Techn ...
... Principal developer of a report generator for kiosk utilization. The report generator, a Java applet this is accessed via HTML and JavaScript, compiles report data from the kiosk application logs and returns the report as a XML document. A XSL template displays the report in Internet Explorer. Techn ...
Introduction to Internet (Vadim)
... Cookie is sent in HTTP header Cookie is sent with each HTTP request Can last for only one session (until browser is closed) or can persist across sessions Can expire some time in the future ...
... Cookie is sent in HTTP header Cookie is sent with each HTTP request Can last for only one session (until browser is closed) or can persist across sessions Can expire some time in the future ...
Lecture 5
... Please enter your comment below which will be sent anonymously to [email protected]. If you want to be extra cautious, access this page through Anonymizer. ...
... Please enter your comment below which will be sent anonymously to [email protected]. If you want to be extra cautious, access this page through Anonymizer. ...
computer security - GH Raisoni Polytechnic, Nagpur
... susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw. •To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface. In a ...
... susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw. •To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface. In a ...
Internet Terms for Internet Class PPLS (1025/12dsg) :// -
... Router -- is the hardware device that acts as the traffic cop for network signals into your home. A router can be wired or wireless or both. Your router provides both a defense against hackers, and the redirection service of deciding which specific computer or printer should get which signals in you ...
... Router -- is the hardware device that acts as the traffic cop for network signals into your home. A router can be wired or wireless or both. Your router provides both a defense against hackers, and the redirection service of deciding which specific computer or printer should get which signals in you ...
A generic Data Mart architecture to support Web mining
... Visits in a Web site leave behind important information about the behavior of the visitors. This information is stored in log files, which can contain many registers but part of them do not contain relevant information. In such cases, user behavior analysis turns out to be a complex and time-consumi ...
... Visits in a Web site leave behind important information about the behavior of the visitors. This information is stored in log files, which can contain many registers but part of them do not contain relevant information. In such cases, user behavior analysis turns out to be a complex and time-consumi ...
Lecture 5
... Please enter your comment below which will be sent anonymously to [email protected]. If you want to be extra cautious, access this page through Anonymizer. ...
... Please enter your comment below which will be sent anonymously to [email protected]. If you want to be extra cautious, access this page through Anonymizer. ...
Hacking - Computer Engineering
... machine, request send there. Step 4: Attacker’s site receives request, acts as proxy, forwards it to real website. Step 5: Real website answers, attackers site forwards to victim. ...
... machine, request send there. Step 4: Attacker’s site receives request, acts as proxy, forwards it to real website. Step 5: Real website answers, attackers site forwards to victim. ...