ControlWave HART Device Interface (HDI) Instruction
... completing the transmit cycle. At 1200 baud, one character time is 11 x 0.833 milliseconds or 10 milliseconds. The remote device starts to transmits the preamble 10 milliseconds (one character time) after the end of the last character sent from the host device. The total delay from the end of the la ...
... completing the transmit cycle. At 1200 baud, one character time is 11 x 0.833 milliseconds or 10 milliseconds. The remote device starts to transmits the preamble 10 milliseconds (one character time) after the end of the last character sent from the host device. The total delay from the end of the la ...
2005-guest-leture
... the sender would apply CS and CD, but the collisions happen at the receiver it might be the case that a sender cannot “hear” the collision, i.e., CD does not work furthermore, CS might not work if, e.g., a terminal is “hidden” ...
... the sender would apply CS and CD, but the collisions happen at the receiver it might be the case that a sender cannot “hear” the collision, i.e., CD does not work furthermore, CS might not work if, e.g., a terminal is “hidden” ...
SPI - Personal Web Pages
... History • CAN was first developed by Robert Bosch GmbH, Germany in 1986 when they were requested to develop a communication system between three ECUs (electronic control units) in vehicles by Mercedes. • They found that an UART is no longer suitable in this situation because it is used in point-to- ...
... History • CAN was first developed by Robert Bosch GmbH, Germany in 1986 when they were requested to develop a communication system between three ECUs (electronic control units) in vehicles by Mercedes. • They found that an UART is no longer suitable in this situation because it is used in point-to- ...
F RTA155E
... The kind of FOI provides a WDM STM-1 (155.52 Mbps) interface. In order to maintain transportation stability, FOI also provides 1+1 protection switching, and a SCNP protection mechanism which meets ITU-T.G.841 standards. In addition, FOI can support the manual set-up switch mode. Based on performance ...
... The kind of FOI provides a WDM STM-1 (155.52 Mbps) interface. In order to maintain transportation stability, FOI also provides 1+1 protection switching, and a SCNP protection mechanism which meets ITU-T.G.841 standards. In addition, FOI can support the manual set-up switch mode. Based on performance ...
74-3468-3 - XM500 TCP/IP Modem
... NOTE: The 25 to 9 pin adapter is required for the XL50/100/500 controllers. A XW571 cable (purchased separately) is required for XDM506 and XM100A. ...
... NOTE: The 25 to 9 pin adapter is required for the XL50/100/500 controllers. A XW571 cable (purchased separately) is required for XDM506 and XM100A. ...
A Comparative Study of Wireless Technologies: Zigbee, Bluetooth
... 2012. In Europe it operates on 868MHz frequency by using Amplitude Shift Key (ASK), whereas in North America it operates on 315 MHz frequency. Enocean protocol stack composed of four main layers: physical layer, data link layer and network layer. On physical layer secured data is transmitted by usin ...
... 2012. In Europe it operates on 868MHz frequency by using Amplitude Shift Key (ASK), whereas in North America it operates on 315 MHz frequency. Enocean protocol stack composed of four main layers: physical layer, data link layer and network layer. On physical layer secured data is transmitted by usin ...
Figure F: Power line communications from low voltage network into
... entertainment used by companies and homes worldwide. Home users, who often have more than one computer, are looking to data communication networks to share information between computers. They are also looking to networks for the ‘automation’ of their home – including applications such as security sy ...
... entertainment used by companies and homes worldwide. Home users, who often have more than one computer, are looking to data communication networks to share information between computers. They are also looking to networks for the ‘automation’ of their home – including applications such as security sy ...
5 Data Communication and Networking
... LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distance are limited, and there is also a limit on the number of computers that can be attached to a single LAN. Wide Area Network (WAN) A WAN is a computer network that ...
... LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distance are limited, and there is also a limit on the number of computers that can be attached to a single LAN. Wide Area Network (WAN) A WAN is a computer network that ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... A MAC protocol plays a crucial role in determining the throughput, efficiency, delay, energy efficiency of a network [3]. The various MAC protocols which help in mitigating the hidden and exposed terminal effect are discussed below: BTMA (Busy Tone Multiple Access): It was the first protocol to comb ...
... A MAC protocol plays a crucial role in determining the throughput, efficiency, delay, energy efficiency of a network [3]. The various MAC protocols which help in mitigating the hidden and exposed terminal effect are discussed below: BTMA (Busy Tone Multiple Access): It was the first protocol to comb ...
Applying FPGA to Biological Problems
... Converts C code to a Hardware Descriptive Language which is then converted to a net list and then the place and route tools make a FPGA ...
... Converts C code to a Hardware Descriptive Language which is then converted to a net list and then the place and route tools make a FPGA ...
CoBox-DR1-IAP
... IAP Device Servers, adapted to the three factory environments, can unite any mixture of equipment from industrial automation vendors into a single reliable pipeline. This new and open infrastructure opens the way for data to flow in real time from all your plant devices up to your IT layer. The IAP ...
... IAP Device Servers, adapted to the three factory environments, can unite any mixture of equipment from industrial automation vendors into a single reliable pipeline. This new and open infrastructure opens the way for data to flow in real time from all your plant devices up to your IT layer. The IAP ...
Unit 2 Lesson 2
... sending device because the timing information is embedded within the preamble of the frame. Synchronous transmissions are common in internal computer communications and usually are sent as entire frames. Synchronous transmission is common when large blocks of data are transferred. ...
... sending device because the timing information is embedded within the preamble of the frame. Synchronous transmissions are common in internal computer communications and usually are sent as entire frames. Synchronous transmission is common when large blocks of data are transferred. ...
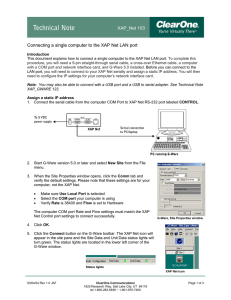
Connecting a Single Computer to the XAP Net LAN Port
... connects, a XAP Net icon appears in the Site pane. The Site Data and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net h ...
... connects, a XAP Net icon appears in the Site pane. The Site Data and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net h ...
Network4 - Rhema Impact Ministries
... Bit rate (link speed): Defines number of bits sent over link per second (bps). Impacts how nodes send data over circuit. ...
... Bit rate (link speed): Defines number of bits sent over link per second (bps). Impacts how nodes send data over circuit. ...
SMS based remote control system
... the Tx pin . We could not get the pulses on the DSO . We also tried sending a particular byte sequence to the mobile phone , that asks for its software version and still we did not get any response . We could not check the working of the nokia cell phone with already available softwares on computer ...
... the Tx pin . We could not get the pulses on the DSO . We also tried sending a particular byte sequence to the mobile phone , that asks for its software version and still we did not get any response . We could not check the working of the nokia cell phone with already available softwares on computer ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... parameter acquisition and multi level monitoring and networking. It can reduce operation pressure on data reduction and ensures real-time monitoring of system performance. On the other hand, our proposed web server requires only a very low d.c. supply of 3.3V for its operation. This system ensures p ...
... parameter acquisition and multi level monitoring and networking. It can reduce operation pressure on data reduction and ensures real-time monitoring of system performance. On the other hand, our proposed web server requires only a very low d.c. supply of 3.3V for its operation. This system ensures p ...
Integrating Process Weighing Data
... programming errors. 5. Troubleshooting communications Data communication troubleshooting for a weighing terminal and automation system depends on the communication method being used. For serial or EtherNet TCP/IP to PC, simple connection using a PC application such as HyperTerminal can verify basic ...
... programming errors. 5. Troubleshooting communications Data communication troubleshooting for a weighing terminal and automation system depends on the communication method being used. For serial or EtherNet TCP/IP to PC, simple connection using a PC application such as HyperTerminal can verify basic ...
Lecture 6 (Architecture, Functions and Protocols)
... – Network security and access control are provided by the Authentication Center (AUC) and by the Equipment Identity Register (EIR): • AUC: to ensure that only authorized users have access to the network, • EIR: to maintain lists of stolen, faulty and valid equipment identities. ...
... – Network security and access control are provided by the Authentication Center (AUC) and by the Equipment Identity Register (EIR): • AUC: to ensure that only authorized users have access to the network, • EIR: to maintain lists of stolen, faulty and valid equipment identities. ...
SIGNALS AND THE PHYSICAL LAYER
... of a signal to become weak or distorted during transmission. This is to be avoided. The other factors are self-explanatory. 2.6 SWITCHING For transmitting data between two or more devices on a network, they must be connected by either point-to-point links between every two devices or between a centr ...
... of a signal to become weak or distorted during transmission. This is to be avoided. The other factors are self-explanatory. 2.6 SWITCHING For transmitting data between two or more devices on a network, they must be connected by either point-to-point links between every two devices or between a centr ...
Cable Testing and Cabling LANs and WANs
... • Describe the ten copper cable tests defined in TIA/EIA-568-B. • Describe the difference between Category 5 and Category 6 cable. ...
... • Describe the ten copper cable tests defined in TIA/EIA-568-B. • Describe the difference between Category 5 and Category 6 cable. ...
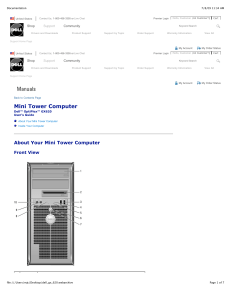
Mini Tower Computer
... connector on the back panel of your computer. A click indicates that the network cable has been securely attached. NOTE: Do not plug a telephone cable into the network connector. On computers with a network connector card, use the connector on the card. It is recommended that you use Category 5 wiri ...
... connector on the back panel of your computer. A click indicates that the network cable has been securely attached. NOTE: Do not plug a telephone cable into the network connector. On computers with a network connector card, use the connector on the card. It is recommended that you use Category 5 wiri ...
Team Epimetheus Wireless Robot Module
... • PIC communication with A/D – PIC to MAXIM A/D communication performed using Serial Peripheral Interface (SPI) compatible bus through SSP module. – PIC acts as the master and generates the clock at a rate of Fosc/4. – Data is simultaneously clocked in/out of SSP buffer. – RPM and Battery Voltage da ...
... • PIC communication with A/D – PIC to MAXIM A/D communication performed using Serial Peripheral Interface (SPI) compatible bus through SSP module. – PIC acts as the master and generates the clock at a rate of Fosc/4. – Data is simultaneously clocked in/out of SSP buffer. – RPM and Battery Voltage da ...
Week_Ten_Network_ppt
... OSI model used in example. TCP takes large blocks of information from an application and breaks them into segments. It numbers and sequences each segment so that the destination ‘s TCP protocol can put the segments back into the order the application intended. After the segments are sent, TCP (trans ...
... OSI model used in example. TCP takes large blocks of information from an application and breaks them into segments. It numbers and sequences each segment so that the destination ‘s TCP protocol can put the segments back into the order the application intended. After the segments are sent, TCP (trans ...
RS-232
In telecommunications, RS-232 is a standard for serial communication transmission of data. It formally defines the signals connecting between a DTE (data terminal equipment) such as a computer terminal, and a DCE (data circuit-terminating equipment, originally defined as data communication equipment), such as a modem. The RS-232 standard is commonly used in computer serial ports. The standard defines the electrical characteristics and timing of signals, the meaning of signals, and the physical size and pinout of connectors. The current version of the standard is TIA-232-F Interface Between Data Terminal Equipment and Data Circuit-Terminating Equipment Employing Serial Binary Data Interchange, issued in 1997.An RS-232 serial port was once a standard feature of a personal computer, used for connections to modems, printers, mice, data storage, uninterruptible power supplies, and other peripheral devices. However, RS-232 is hampered by low transmission speed, large voltage swing, and large standard connectors. In modern personal computers, USB has displaced RS-232 from most of its peripheral interface roles. Many computers do not come equipped with RS-232 ports and must use either an external USB-to-RS-232 converter or an internal expansion card with one or more serial ports to connect to RS-232 peripherals. Nevertheless, RS-232 devices are still used, especially in industrial machines, networking equipment and scientific instruments.