(Simple) Preprocessor for Adding Multi
... We have provided a simple transformation-based approach to incorporating multivalued propositions into ASP. Our translation is modular and heavily benefits from the expressive input language of ASP, providing variables and aggregate statements such as cardinality constraints. Once multi-valued propo ...
... We have provided a simple transformation-based approach to incorporating multivalued propositions into ASP. Our translation is modular and heavily benefits from the expressive input language of ASP, providing variables and aggregate statements such as cardinality constraints. Once multi-valued propo ...
Certified Automated Theorem Proving for Type Inference.
... provers, to prove that a system Γ entails theorem A, we need to construct proof p as inhabitant of type A. ...
... provers, to prove that a system Γ entails theorem A, we need to construct proof p as inhabitant of type A. ...
Dept. of CSE, BUAA
... Robustness is the child of transparency and simplicity. Design for simplicity; add complexity only where you must. Design for transparency; spend effort early to save effort later. In interface design, obey the Rule of Least Surprise. Programmer time is expensive; conserve it in preference to m ...
... Robustness is the child of transparency and simplicity. Design for simplicity; add complexity only where you must. Design for transparency; spend effort early to save effort later. In interface design, obey the Rule of Least Surprise. Programmer time is expensive; conserve it in preference to m ...
160-Lab06BKG - Western Oregon University
... strategies. It should be noted that there is no single set of rules that, if followed, always leads to an effective and efficient algorithm. In fact, problem solving relies so much on creativity and ingenuity that some people regard computer programming as an art form! Looking for better algorithms ...
... strategies. It should be noted that there is no single set of rules that, if followed, always leads to an effective and efficient algorithm. In fact, problem solving relies so much on creativity and ingenuity that some people regard computer programming as an art form! Looking for better algorithms ...
Dialectic proof procedures for assumption
... Our proof procedures are presented at three levels of abstraction. We derive one from the other by successive refinement, thereby simplifying the proofs and clarifying the relationship between seemingly different proof procedures. Our final refinement can be viewed as a generalisation of logic progr ...
... Our proof procedures are presented at three levels of abstraction. We derive one from the other by successive refinement, thereby simplifying the proofs and clarifying the relationship between seemingly different proof procedures. Our final refinement can be viewed as a generalisation of logic progr ...
Survey on Fuzzy Expert System
... In case if the input data does not match any patters in the rule base, an appropriate message stating that the system cannot find the answer is displayed. The system is implemented by using Microsoft Visual Studio .NET 2010. MVC and Microsoft SQL Server 2012. “Literature Review on Fuzzy Expert Syste ...
... In case if the input data does not match any patters in the rule base, an appropriate message stating that the system cannot find the answer is displayed. The system is implemented by using Microsoft Visual Studio .NET 2010. MVC and Microsoft SQL Server 2012. “Literature Review on Fuzzy Expert Syste ...
Dialectic proof procedures for assumption
... showed how it can be used for the semantics of default reasoning. We showed that the stable semantics of many logics for default reasoning can be understood as sanctioning a belief if the belief is the conclusion of an argument whose set of supporting assumptions can be extended to a set of assumpti ...
... showed how it can be used for the semantics of default reasoning. We showed that the stable semantics of many logics for default reasoning can be understood as sanctioning a belief if the belief is the conclusion of an argument whose set of supporting assumptions can be extended to a set of assumpti ...
Redalyc.Rational versus Intuitive Outcomes of Reasoning with
... The scenario is described as follows. Example 1 (Cakes). There are three pieces of cakes on a table: a piece of Almond cake, a Brownie, and a piece of Cheesecake. You want to get as many cakes as possible, and the following are the rules of the game. a) You can take cakes from the table in two ’roun ...
... The scenario is described as follows. Example 1 (Cakes). There are three pieces of cakes on a table: a piece of Almond cake, a Brownie, and a piece of Cheesecake. You want to get as many cakes as possible, and the following are the rules of the game. a) You can take cakes from the table in two ’roun ...
Extending Python
... corresponding C program: enumdivs.c. Write the factors to screen instead of into a list. Modify the enumdivs.c from the previous exercise so that the factors are written into a string. Use the modified enumdivs.c from the previous exercise to build a Python extension EnumDivs. Take a Python function ...
... corresponding C program: enumdivs.c. Write the factors to screen instead of into a list. Modify the enumdivs.c from the previous exercise so that the factors are written into a string. Use the modified enumdivs.c from the previous exercise to build a Python extension EnumDivs. Take a Python function ...
On Revising Fuzzy Belief Bases
... The original AGM theory was a theory about how to revise deductively closed sets of formulas, but the more general case of revising arbitrary (crisp) bases has also been studied, notably by Hansson [13, 15], who axiomatically characterised partial meet base revision. We will generalise this operatio ...
... The original AGM theory was a theory about how to revise deductively closed sets of formulas, but the more general case of revising arbitrary (crisp) bases has also been studied, notably by Hansson [13, 15], who axiomatically characterised partial meet base revision. We will generalise this operatio ...
Programming with Multiple Paradigms in Lua - DI PUC-Rio
... scoping is with the use of closures. Most implementations of closures neglect assignment. Pure functional languages do not have assignment. In ML assignable cells have no names, so the problem of assignment to lexical-scoped variables does not arise. Since Rabbit [14], most Scheme compilers do assig ...
... scoping is with the use of closures. Most implementations of closures neglect assignment. Pure functional languages do not have assignment. In ML assignable cells have no names, so the problem of assignment to lexical-scoped variables does not arise. Since Rabbit [14], most Scheme compilers do assig ...
TCP/UDP Sockets
... buff is the address of a buffer (nbytes long) from is the address of a sockaddr Return value is the number of bytes received and put into buff, or -1 on error ...
... buff is the address of a buffer (nbytes long) from is the address of a sockaddr Return value is the number of bytes received and put into buff, or -1 on error ...
Machine Learning meets Knowledge Representation in the
... S. Ceri, G. Gottlob, L. Tanca (1989). "What you always wanted to know about Datalog (and never dared to ask)". IEEE Transactions on Knowledge and Data Engineering 1(1): 146–66. S. Ceri, G. Gottlob, L. Tanca (1990). Logic Programming and databases. Springer-Verlag. T. Eiter, G. Gottlob, H. Mann ...
... S. Ceri, G. Gottlob, L. Tanca (1989). "What you always wanted to know about Datalog (and never dared to ask)". IEEE Transactions on Knowledge and Data Engineering 1(1): 146–66. S. Ceri, G. Gottlob, L. Tanca (1990). Logic Programming and databases. Springer-Verlag. T. Eiter, G. Gottlob, H. Mann ...
FS-FOIL: An Inductive Learning Method for Extracting Interpretable
... hand, it is often necessary to identify regions of similarity or other dependencies from unstructured data sets—without any explicit goal information. This class of data mining problems is often called unsupervised. Typical clustering problems like market segmentation etc. can be assigned to this ca ...
... hand, it is often necessary to identify regions of similarity or other dependencies from unstructured data sets—without any explicit goal information. This class of data mining problems is often called unsupervised. Typical clustering problems like market segmentation etc. can be assigned to this ca ...
TCP/UDP Sockets
... buff is the address of a buffer (nbytes long) from is the address of a sockaddr Return value is the number of bytes received and put into buff, or -1 on error ...
... buff is the address of a buffer (nbytes long) from is the address of a sockaddr Return value is the number of bytes received and put into buff, or -1 on error ...
Default reasoning by deductive planning
... iterative way instead of by using the usual fixpoint construction. This observation is the starting point of our analysis. During the past decade, several calculi designed for classical logic have been applied to define proof theories for (variants of) default logic, for example, the resolution prin ...
... iterative way instead of by using the usual fixpoint construction. This observation is the starting point of our analysis. During the past decade, several calculi designed for classical logic have been applied to define proof theories for (variants of) default logic, for example, the resolution prin ...
Dynamic domain splitting for numeric CSPs
... Identifying the splitting constraint to reconsider upon a failure can be done in a way similar as mac-cbj identifies the point where to backtrack [22]. 2B-consistency filtering algorithm works by shrinking the domains, which are intervals: it does not remove values one by one but it removes a subint ...
... Identifying the splitting constraint to reconsider upon a failure can be done in a way similar as mac-cbj identifies the point where to backtrack [22]. 2B-consistency filtering algorithm works by shrinking the domains, which are intervals: it does not remove values one by one but it removes a subint ...
A Functional Programming Approach to AI Search Algorithms
... mented col value. When col reaches N+1, all N queens have been placed on the table, i.e., a solution is found. We print the solution, and continue with the search by backtracking (i.e., returning to the previous function in the call stack) until we return to the main function, which means that a bac ...
... mented col value. When col reaches N+1, all N queens have been placed on the table, i.e., a solution is found. We print the solution, and continue with the search by backtracking (i.e., returning to the previous function in the call stack) until we return to the main function, which means that a bac ...
ASP - User pages
... related data, typically stored on disk, and accessible by possibly many concurrent users. Most common is relational database, which is a tabular database in which the data is defined so that it can reorganized and accessed in a number of different ways Server Side Programming ASP ...
... related data, typically stored on disk, and accessible by possibly many concurrent users. Most common is relational database, which is a tabular database in which the data is defined so that it can reorganized and accessed in a number of different ways Server Side Programming ASP ...
What is a Knowledge Representation
... Viewing representations as surrogates leads naturally to two important questions. The first question about any surrogate is its intended identity: what is it a surrogate for? There must be some form of correspondence specified between the surrogate and its intended referent in the world; the corresp ...
... Viewing representations as surrogates leads naturally to two important questions. The first question about any surrogate is its intended identity: what is it a surrogate for? There must be some form of correspondence specified between the surrogate and its intended referent in the world; the corresp ...
PS14
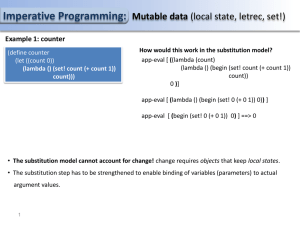
... Imperative Programming: Mutable data (local state, letrec, set!) Example 2: A chess player object: A chase player object is represent by a dispatch procedure. Based on a given message it invokes internal procedures of the object. total and steps which keep track of the player’s points and the numbe ...
... Imperative Programming: Mutable data (local state, letrec, set!) Example 2: A chess player object: A chase player object is represent by a dispatch procedure. Based on a given message it invokes internal procedures of the object. total and steps which keep track of the player’s points and the numbe ...
Automated Theorem Proving in a First
... of first-order formulas are usually implemented as separate procedures. Despite the complexity of automated reasoning in first-order logic, several methods were found to be efficient for finding unsatisfiability for non-trivial problems. Modern state-or-the-art automated theorem provers are based on ...
... of first-order formulas are usually implemented as separate procedures. Despite the complexity of automated reasoning in first-order logic, several methods were found to be efficient for finding unsatisfiability for non-trivial problems. Modern state-or-the-art automated theorem provers are based on ...
Awareness, negation and logical omniscience
... logically incomplete deduction rules. In [13], Konolige presents a Deductive Belief System, in which an agent’s beliefs are described as a set of sentences in some formal language, together with a deductive process for deriving consequence of those beliefs. In Konolige’s deductive belief system, the ...
... logically incomplete deduction rules. In [13], Konolige presents a Deductive Belief System, in which an agent’s beliefs are described as a set of sentences in some formal language, together with a deductive process for deriving consequence of those beliefs. In Konolige’s deductive belief system, the ...