CMPU1022 Operating Systems 1
... A Wide Area Network (WAN) is a network that a country, or connects countries. The WAN is often owned and run as a public utility, but telephone companies have WANs also. WANs can use anything for satellites to microwaves transmissions. The most common example of a WAN is the Internet, but there are ...
... A Wide Area Network (WAN) is a network that a country, or connects countries. The WAN is often owned and run as a public utility, but telephone companies have WANs also. WANs can use anything for satellites to microwaves transmissions. The most common example of a WAN is the Internet, but there are ...
PPT - National Taiwan University
... Fundamentally a two-way request/response protocol writes have an acknowledgement Issues fixed or variable length (bulk) transfers remote virtual or physical address, where is action performed? deadlock avoidance and input buffer full coherent? consistent? ...
... Fundamentally a two-way request/response protocol writes have an acknowledgement Issues fixed or variable length (bulk) transfers remote virtual or physical address, where is action performed? deadlock avoidance and input buffer full coherent? consistent? ...
Buses and Interfaces - Mahanakorn University of Technology
... interface cable bus. Differential NRZI data is transmitted Isochronous or Asynchronous between devices. Data is transferred at three different rates over a maximum cable length of 4 meters ~ over 4 wires, 2 of which carry data on a balanced twisted pair. USB 3.0 (Super-Speed USB) increases the dat ...
... interface cable bus. Differential NRZI data is transmitted Isochronous or Asynchronous between devices. Data is transferred at three different rates over a maximum cable length of 4 meters ~ over 4 wires, 2 of which carry data on a balanced twisted pair. USB 3.0 (Super-Speed USB) increases the dat ...
download
... LAN Topologies: Ring Repeaters are joined by unidirectional pointto-point links in a ring As a frame circulates past a receiver, the receiver checks its address, and copies those intended for it into a local buffer Frame circulates until it returns to source, which removes it from network ...
... LAN Topologies: Ring Repeaters are joined by unidirectional pointto-point links in a ring As a frame circulates past a receiver, the receiver checks its address, and copies those intended for it into a local buffer Frame circulates until it returns to source, which removes it from network ...
Chapter 14: Local Area Network Technology
... LAN Topologies: Ring Repeaters are joined by unidirectional pointto-point links in a ring As a frame circulates past a receiver, the receiver checks its address, and copies those intended for it into a local buffer Frame circulates until it returns to source, which removes it from network ...
... LAN Topologies: Ring Repeaters are joined by unidirectional pointto-point links in a ring As a frame circulates past a receiver, the receiver checks its address, and copies those intended for it into a local buffer Frame circulates until it returns to source, which removes it from network ...
1 LAN Topologies - theParticle.com
... • Unicast: Addressing is one-to-one, where one computer sends a frame to another computer. Even though many stations can receive the same data, they should ignore it since it is not addressed to them. • Multicast: Addressing is one-to-many, where one computer is sending a frame to many other compute ...
... • Unicast: Addressing is one-to-one, where one computer sends a frame to another computer. Even though many stations can receive the same data, they should ignore it since it is not addressed to them. • Multicast: Addressing is one-to-many, where one computer is sending a frame to many other compute ...
slides
... • Virtualization layer: based on L4-family microkernels (Xen could be used as well) • Trusted software layer: based on PERSEUS security architecture • Application layer: legacy operating system (para-virtualized Linux) and security critical applications ...
... • Virtualization layer: based on L4-family microkernels (Xen could be used as well) • Trusted software layer: based on PERSEUS security architecture • Application layer: legacy operating system (para-virtualized Linux) and security critical applications ...
Network Topologies
... stronger and can cover larger area than some topologies, No hubs / switches required to connect the devices together, If a cable stops working easy to find out where, Can add more computers but need to break the ring and be placed in-between two computers which can be a hassle, Quite a bit of cable ...
... stronger and can cover larger area than some topologies, No hubs / switches required to connect the devices together, If a cable stops working easy to find out where, Can add more computers but need to break the ring and be placed in-between two computers which can be a hassle, Quite a bit of cable ...
Network Transactions - Parallel Programming Laboratory
... one-way transfer of information from a source output buffer to a dest. input buffer ...
... one-way transfer of information from a source output buffer to a dest. input buffer ...
Network Topologies
... Offers opportunities for expansion Most popular topology in use; wide variety of equipment available ...
... Offers opportunities for expansion Most popular topology in use; wide variety of equipment available ...
II. General presentation of Voice over IP
... interconnection schema, thus a MASTER initiates a bus cycle to a target SLAVE. The target SLAVE then participates in one or more bus cycles with the MASTER. An arbiter (not shown in the Figure) determines when a MASTER may gain access to the shared bus. The main advantage to this technique is that s ...
... interconnection schema, thus a MASTER initiates a bus cycle to a target SLAVE. The target SLAVE then participates in one or more bus cycles with the MASTER. An arbiter (not shown in the Figure) determines when a MASTER may gain access to the shared bus. The main advantage to this technique is that s ...
Cisco Discovery 1 Module 03 Quiz Picture Descriptions
... Which three pieces of information are included in a network physical map? (Choose three) ...
... Which three pieces of information are included in a network physical map? (Choose three) ...
University of Ottawa - School of Electrical Engineering and
... This communication pattern requires us to send 3 (64 – 8) or 168 total packets— that is, 56 packets in each of the three communication phases: northward, eastward, westwards. The number of hops suffered by packets depends on the topology. Here are the various cases: _ Bus—The mapping of the 8 ...
... This communication pattern requires us to send 3 (64 – 8) or 168 total packets— that is, 56 packets in each of the three communication phases: northward, eastward, westwards. The number of hops suffered by packets depends on the topology. Here are the various cases: _ Bus—The mapping of the 8 ...
cable-replacement
... hopping sequence). • It allows one master device to interconnect with up to seven active slave devices. • Up to 255 further slave devices can be inactive, or parked, which the master device can bring into active status at any time, but an active station must go into parked first. ...
... hopping sequence). • It allows one master device to interconnect with up to seven active slave devices. • Up to 255 further slave devices can be inactive, or parked, which the master device can bring into active status at any time, but an active station must go into parked first. ...
Error Frame - Personal Web Pages
... Tradeoff: CAN bus versus point-to-point connections • By introducing one single bus as the only means of communication as opposed to the point-to-point network, we traded off the channel access simplicity for the circuit simplicty • Since two devices might want to transmit simultaneously, we need t ...
... Tradeoff: CAN bus versus point-to-point connections • By introducing one single bus as the only means of communication as opposed to the point-to-point network, we traded off the channel access simplicity for the circuit simplicty • Since two devices might want to transmit simultaneously, we need t ...
Elektromotus CAN bus topology recommendations v0.2 rc2 Table of
... CAN bus does not support star or even a multi star topologies. The nodes are connected via unterminated drop lines to the main bus. The bus line is terminated at both furthest ends with a single termination resistor(characteristic line impedance) as it is shown in Figure 2. Otherwise signal reflecti ...
... CAN bus does not support star or even a multi star topologies. The nodes are connected via unterminated drop lines to the main bus. The bus line is terminated at both furthest ends with a single termination resistor(characteristic line impedance) as it is shown in Figure 2. Otherwise signal reflecti ...
Network Access Technologies
... Address that memory/peripherals are available at Non-volatile memory typically mapped at the reset location Use combinatorial function of high-order address bits to generate enable signals Devise memory map for decoding convenience ...
... Address that memory/peripherals are available at Non-volatile memory typically mapped at the reset location Use combinatorial function of high-order address bits to generate enable signals Devise memory map for decoding convenience ...
Lecture 3 - Network hardware, Ethernet
... – So in minimal case an adaptor sends 96 bits: 64 bit preamble and 32 bit jamming sequence (this is called a runt frame) – Runt frame only occurs if senders are near. In worst case they may need to send as many as 512 bits (64) bytes past preamble to detect collision (thus the 46 data byte miminum: ...
... – So in minimal case an adaptor sends 96 bits: 64 bit preamble and 32 bit jamming sequence (this is called a runt frame) – Runt frame only occurs if senders are near. In worst case they may need to send as many as 512 bits (64) bytes past preamble to detect collision (thus the 46 data byte miminum: ...
Vehicle Bus_final
... demands on a communication system’s availability. Decentralized bus access, so that each bus node has the right to access the bus. That is why a CAN network is based on a combination of multi-master architecture and line topology: essentially each CAN node is authorized to place CAN messages on the ...
... demands on a communication system’s availability. Decentralized bus access, so that each bus node has the right to access the bus. That is why a CAN network is based on a combination of multi-master architecture and line topology: essentially each CAN node is authorized to place CAN messages on the ...
Document
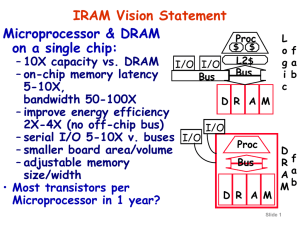
... Conclusion and Status 1/2 • IRAM attractive for both drivers of Next Generation: Mobile Consumer Electronic Devices and Scaleable Infrastructure – Small size, low power, high bandwidth ...
... Conclusion and Status 1/2 • IRAM attractive for both drivers of Next Generation: Mobile Consumer Electronic Devices and Scaleable Infrastructure – Small size, low power, high bandwidth ...
24-ensembles
... • Mobile devices do not interact as seamless ensembles yet. • Highlight: Captured user needs within their social context. • Question: Do users feel the need to maintain multiple devices so we need to enable that coordination? Can we combine functionality in some ways? ...
... • Mobile devices do not interact as seamless ensembles yet. • Highlight: Captured user needs within their social context. • Question: Do users feel the need to maintain multiple devices so we need to enable that coordination? Can we combine functionality in some ways? ...
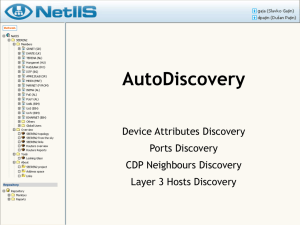
3 - Terena
... CDP offers the information about models of these devices, as well as connected ports ...
... CDP offers the information about models of these devices, as well as connected ports ...
Denial of Service Attack on Automotive CAN Networks
... CAN is a central networking system that connects all modules working throughout the vehicle so that they can work together to run effectively and efficiently as automobiles have become more technologically advanced and intelligent. For example, the engine reports the vehicle’s speed to the transmiss ...
... CAN is a central networking system that connects all modules working throughout the vehicle so that they can work together to run effectively and efficiently as automobiles have become more technologically advanced and intelligent. For example, the engine reports the vehicle’s speed to the transmiss ...
How do I run an Activation using ACEmanager on
... How do I run an Activation using ACEmanager on CDMA networks? This document describes the steps required to manually provision various models of AirLink devices that run on CDMA/EVDO networks. While most AirLink devices support some form of automatic, over-the-air (OTA) account activation, the proce ...
... How do I run an Activation using ACEmanager on CDMA networks? This document describes the steps required to manually provision various models of AirLink devices that run on CDMA/EVDO networks. While most AirLink devices support some form of automatic, over-the-air (OTA) account activation, the proce ...
Low Pin Count

The Low Pin Count bus, or LPC bus, is used on IBM-compatible personal computers to connect low-bandwidth devices to the CPU, such as the boot ROM, ""legacy"" I/O devices (integrated into a super I/O chip), and Trusted Platform Module (TPM). ""Legacy"" I/O devices usually include serial and parallel ports, PS/2 keyboard, PS/2 mouse, and floppy disk controller.Most PC motherboards with a LPC bus have either a Platform Controller Hub (PCH) or a southbridge chip, which acts as the host and controls the LPC bus. All other devices connected to the physical wires of the LPC bus are peripherals.