system call
... OS also needs to ensure that the use of resources by programs is safe. Safe from software faults and malicious action and safe from errors that the operating system may produce as a result of its actions. Thus the OS needs to provide software that is part of OS for security and protection to prevent ...
... OS also needs to ensure that the use of resources by programs is safe. Safe from software faults and malicious action and safe from errors that the operating system may produce as a result of its actions. Thus the OS needs to provide software that is part of OS for security and protection to prevent ...
DISTRIBUTED OPERATING SYSTEM
... processing resources between that system's distributed processes. These policies and mechanisms support operations involving the allocation and de-allocation of processes and ports to processors, as well as provisions to run, suspend, migrate, halt, or resume execution of processes. While these dist ...
... processing resources between that system's distributed processes. These policies and mechanisms support operations involving the allocation and de-allocation of processes and ports to processors, as well as provisions to run, suspend, migrate, halt, or resume execution of processes. While these dist ...
Section for Related Work % \section{Related Work} Rootkit detection
... Gibraltar, another behavior-based kernel inspection rootkit detection tool, detects kernel level rootkits by using an initial training period in which invariants on kernel data structures are created \cite{baliga2008automatic}. Due to the way that Gilbratar monitors the kernel, it must reside on a s ...
... Gibraltar, another behavior-based kernel inspection rootkit detection tool, detects kernel level rootkits by using an initial training period in which invariants on kernel data structures are created \cite{baliga2008automatic}. Due to the way that Gilbratar monitors the kernel, it must reside on a s ...
3D Shape Correspondence
... Controls processes (program in execution) so that they don’t harm each other; single CPU, memory, etc. shared robustly. OS has the low level code that knows how to access devices, which makes program development easy for us. Your printf() triggers some OS routine to run in the CPU to do the ac ...
... Controls processes (program in execution) so that they don’t harm each other; single CPU, memory, etc. shared robustly. OS has the low level code that knows how to access devices, which makes program development easy for us. Your printf() triggers some OS routine to run in the CPU to do the ac ...
System Programs - Bilkent University Computer Engineering
... devices, etc. – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information should be able to control use of that information; concurrent processes should not interfere with each other • Access control to resources ...
... devices, etc. – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information should be able to control use of that information; concurrent processes should not interfere with each other • Access control to resources ...
Computer components
... 1. I have two laptops, both running Windows 7. One takes 32 seconds to boot and the other takes nearly 3 minutes. What could explain the difference? 2. In this example, we loaded and executed Microsoft Word by double-clicking the name of the program in the Start menu. What would we have done if inst ...
... 1. I have two laptops, both running Windows 7. One takes 32 seconds to boot and the other takes nearly 3 minutes. What could explain the difference? 2. In this example, we loaded and executed Microsoft Word by double-clicking the name of the program in the Start menu. What would we have done if inst ...
our Jeffrey C. Mogul HP Labs, Palo Alto, CA, 94304
... we care about, and are pre-packaged to run easily (without a lot of thought about parameters) on cycle-level simulators. There are a lot of possibilities for OS-relevant benchmarks; in addition to those listed above, one might include Hadoop, or a virtualization management workload [6]. (Micro-bench ...
... we care about, and are pre-packaged to run easily (without a lot of thought about parameters) on cycle-level simulators. There are a lot of possibilities for OS-relevant benchmarks; in addition to those listed above, one might include Hadoop, or a virtualization management workload [6]. (Micro-bench ...
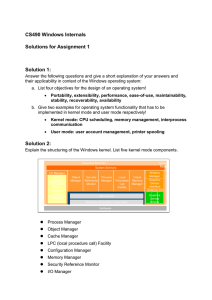
Unit OS2: Operating Systems Principles
... running in the context of the Windows Subsystem process to a set of callable services running in kernel mode. The primary reason for this shift was to improve overall system performance. Having a separate server process that contains the Windows graphics subsystem required multiple thread and proces ...
... running in the context of the Windows Subsystem process to a set of callable services running in kernel mode. The primary reason for this shift was to improve overall system performance. Having a separate server process that contains the Windows graphics subsystem required multiple thread and proces ...
Report
... systems): DR-DOS, FreeDOS, MS-DOS, Novell DOS, OpenDOS, PC-DOS, PTS-DOS, ROM-DOS, JMOS and several others. They are single-user, single-task operating systems. These operating systems run on IBM PC compatible type hardware using the Intel x86 or compatible CPU. (Operating Systems) ...
... systems): DR-DOS, FreeDOS, MS-DOS, Novell DOS, OpenDOS, PC-DOS, PTS-DOS, ROM-DOS, JMOS and several others. They are single-user, single-task operating systems. These operating systems run on IBM PC compatible type hardware using the Intel x86 or compatible CPU. (Operating Systems) ...
Unix History, and Background
... • small; Unix consists of many small modules that can be combined into more complex objects. • consistent; modules that make up Unix interact in a consistent way. e.g. things are represented as files (files, programs, directories, ...
... • small; Unix consists of many small modules that can be combined into more complex objects. • consistent; modules that make up Unix interact in a consistent way. e.g. things are represented as files (files, programs, directories, ...
Computers: Understanding Technology, 3e
... Server Operating Systems Windows – Windows 2000 Server – Datacenter Server can support up to 23 processors and 64 gigabytes of data – Windows 2003 Server – Standard Edition intended for small- to medium-sized business; Datacenter Edition supports multiple servers – Windows Longhorn Server – has Win ...
... Server Operating Systems Windows – Windows 2000 Server – Datacenter Server can support up to 23 processors and 64 gigabytes of data – Windows 2003 Server – Standard Edition intended for small- to medium-sized business; Datacenter Edition supports multiple servers – Windows Longhorn Server – has Win ...
Lec1
... run on another one (e.g., Windows programs on a Macintosh), perhaps even running several VMs concurrently. Useful for OS research and development (much easier to debug) Protection and portability (e.g., Java VM) The project in this course is to build some of the portable components of an OS on top o ...
... run on another one (e.g., Windows programs on a Macintosh), perhaps even running several VMs concurrently. Useful for OS research and development (much easier to debug) Protection and portability (e.g., Java VM) The project in this course is to build some of the portable components of an OS on top o ...
Page 1 •Program Execution •I/O Operation •File System
... • Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources. • Protection System is responsible for: distinguish between authorised and unauthorised useage. Specify the control to be imposed provide a means for enforcement. ...
... • Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources. • Protection System is responsible for: distinguish between authorised and unauthorised useage. Specify the control to be imposed provide a means for enforcement. ...
CS307-slides01
... UNIX-family: BSD(Berkeley Software Distribution), System-V Linux-family: Red Hat, Debian, Ubuntu, Fedora, openSUSE, Linux Mint, ...
... UNIX-family: BSD(Berkeley Software Distribution), System-V Linux-family: Red Hat, Debian, Ubuntu, Fedora, openSUSE, Linux Mint, ...
History of OS - EECG Toronto
... • In 1991, Linus Torvalds, then a student of Univ. of Helsinki, wanted to learn OS • But at that time, no free, open-source OS is available • Decided to write his own OS and “open-source” it • Open-source is the key behind its popularity today ...
... • In 1991, Linus Torvalds, then a student of Univ. of Helsinki, wanted to learn OS • But at that time, no free, open-source OS is available • Decided to write his own OS and “open-source” it • Open-source is the key behind its popularity today ...
4.1 Introduction to the Operating System
... the OS is stored on a ROM chip designed to manage hardware and applications with less memory than a personal computer operating system, yet runs fast and efficiently often manages input from a touchscreen and/or voice command and routes data to/from wireless connections including web browsing ...
... the OS is stored on a ROM chip designed to manage hardware and applications with less memory than a personal computer operating system, yet runs fast and efficiently often manages input from a touchscreen and/or voice command and routes data to/from wireless connections including web browsing ...
Windows NT Operating System
... that provides an API specific to an operating system. • When an application calls an API routine, the call is delivered through LPC facility to the environment subsystem. • The environment subsystem executes the API routine and returns the result to the application process by sending another LPC. • ...
... that provides an API specific to an operating system. • When an application calls an API routine, the call is delivered through LPC facility to the environment subsystem. • The environment subsystem executes the API routine and returns the result to the application process by sending another LPC. • ...
1. Introduction about operating system. 2. What is 32 bit
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
Booting process is in progress
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
Introduction
... to ask the operating system to perform tasks reserved for the operating system on behalf of user It takes the form of a trap to a specific location in the interrupt vector The system call is taken by the hardware as a software interrupt Control passes through the interrupt vector to a service vector ...
... to ask the operating system to perform tasks reserved for the operating system on behalf of user It takes the form of a trap to a specific location in the interrupt vector The system call is taken by the hardware as a software interrupt Control passes through the interrupt vector to a service vector ...
Working with Images - Faculty of Computer Science and
... system software that dictate what other software can run ...
... system software that dictate what other software can run ...
Operating Systems Principles Lecture 1: Introduction
... that programs were often entered one bit at time on rows of mechanical switches (plugboards). Programming languages were unknown (not even assembly languages). Operating systems were unheard of. ...
... that programs were often entered one bit at time on rows of mechanical switches (plugboards). Programming languages were unknown (not even assembly languages). Operating systems were unheard of. ...