The random walk of an electrostatic field using parallel infinite
... experiment like throwing a normal dice. In this case we have six possible outcomes which are 1, 2, 3, 4, 5 or 6. We will denote the set of the possible outcomes with the letter S and name it as the state space. These outcomes define a random variable X which can take values from S. Each outcome can ...
... experiment like throwing a normal dice. In this case we have six possible outcomes which are 1, 2, 3, 4, 5 or 6. We will denote the set of the possible outcomes with the letter S and name it as the state space. These outcomes define a random variable X which can take values from S. Each outcome can ...
M10-200 A Projection Access Scheme for Iterative
... area of PET and SPECT because they produce superior image quality compared with filtered back-projection type algorithms, if the data are very noisy. Typically, these algorithms operate on subsets of the measured data, e. g. they take one projection to calculate an update for the intermediate image. ...
... area of PET and SPECT because they produce superior image quality compared with filtered back-projection type algorithms, if the data are very noisy. Typically, these algorithms operate on subsets of the measured data, e. g. they take one projection to calculate an update for the intermediate image. ...
Final - Academic Information System (KFUPM AISYS)
... (a) Use the acceptance-rejection technique to construct a complete algorithm for generating samples from f by first generating samples from the distribution with density h (x) = 2(1 –x) ...
... (a) Use the acceptance-rejection technique to construct a complete algorithm for generating samples from f by first generating samples from the distribution with density h (x) = 2(1 –x) ...
March 2013 Lecture: Missing Data Part 1 Follow-up
... be less inclined to report their income, and thus reported income will be related to depression. Depressed people might also have a lower income in general, and thus when we have a high rate of missing data among depressed individuals, the existing mean income might be lower than it would be without ...
... be less inclined to report their income, and thus reported income will be related to depression. Depressed people might also have a lower income in general, and thus when we have a high rate of missing data among depressed individuals, the existing mean income might be lower than it would be without ...
November 8 -- Sampling distributions
... for a pollster to predict the exact election result. In the case of these polls, error is possibly introduced because there were fifteen or sixteen per cent undecided. Since a pollster cannot say anything about how these people will vote, the existence of a large undecided group can play havoc with ...
... for a pollster to predict the exact election result. In the case of these polls, error is possibly introduced because there were fifteen or sixteen per cent undecided. Since a pollster cannot say anything about how these people will vote, the existence of a large undecided group can play havoc with ...
Using the BBC micro:bit for Home Security
... Learners to consider ways of attaching the sensors and outputs to the BBC micro:bit. This could involve the use of crocodile clips, block connectors or hard wiring. Learners should consider the advantages and disadvantages of different methods. For example, would it be appropriate to use hardwired s ...
... Learners to consider ways of attaching the sensors and outputs to the BBC micro:bit. This could involve the use of crocodile clips, block connectors or hard wiring. Learners should consider the advantages and disadvantages of different methods. For example, would it be appropriate to use hardwired s ...
Beyond Classical Search
... Whyn times: does it work ??? 1) 1)Pick an initial state S at random with one that queen in each column There are many goal states are 2) Repeat k times: well-distributed over the state space a) If GOAL?(S) then return S 2)b)IfPick no an solution has been found after a few attacked queen Q at random ...
... Whyn times: does it work ??? 1) 1)Pick an initial state S at random with one that queen in each column There are many goal states are 2) Repeat k times: well-distributed over the state space a) If GOAL?(S) then return S 2)b)IfPick no an solution has been found after a few attacked queen Q at random ...
This is convolution!
... Both can describe the data… • …but one is simpler. • Occam’s razor: “Among competing hypotheses, the one with the fewest assumptions should be selected” ...
... Both can describe the data… • …but one is simpler. • Occam’s razor: “Among competing hypotheses, the one with the fewest assumptions should be selected” ...
More data speeds up training time in learning halfspaces over sparse vectors,
... learner a lot of flexibility in choosing an appropriate representation of the problem. This additional freedom to the learner makes it much harder to prove lower bounds in this model. Concretely, it is not clear how to use standard reductions from NP hard problems in order to establish lower bounds ...
... learner a lot of flexibility in choosing an appropriate representation of the problem. This additional freedom to the learner makes it much harder to prove lower bounds in this model. Concretely, it is not clear how to use standard reductions from NP hard problems in order to establish lower bounds ...
Here - BCIT Commons
... x or z as defined just above will be useful. While this notation seems to focus on right-hand tail areas, the phrase "pth percentile" still refers strictly to the definition illustrated in the figure above. Thus, for example, the 80th percentile of a random variable x is the value of x that divide ...
... x or z as defined just above will be useful. While this notation seems to focus on right-hand tail areas, the phrase "pth percentile" still refers strictly to the definition illustrated in the figure above. Thus, for example, the 80th percentile of a random variable x is the value of x that divide ...
Homework 3 - Daniel Llamocca
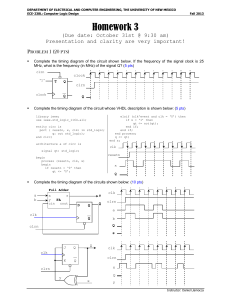
... We want to connect the output bits of the circuits in Problem 5 to LEDs in the NEXYS3 Board. And we want to see the output transitions before our eyes. In the NEXYS3 Board, the input clock frequency is 100 MHz (Period: 10 ns), making it impossible for our eyes to perceive the transitions. ...
... We want to connect the output bits of the circuits in Problem 5 to LEDs in the NEXYS3 Board. And we want to see the output transitions before our eyes. In the NEXYS3 Board, the input clock frequency is 100 MHz (Period: 10 ns), making it impossible for our eyes to perceive the transitions. ...
Untersuchungen zur MAC Address Translation (MAT)
... Packet Classification and Hash Functions Packet Classification Problem: In huge rule sets a search takes much time and/or demands huge memories Hash functions have a search complexity of ideally O(1) and memory demand of O(N) Problem when using (hardware) hash functions: High performance fo ...
... Packet Classification and Hash Functions Packet Classification Problem: In huge rule sets a search takes much time and/or demands huge memories Hash functions have a search complexity of ideally O(1) and memory demand of O(N) Problem when using (hardware) hash functions: High performance fo ...
Hardware random number generator

In computing, a hardware random number generator (TRNG, True Random Number Generator) is an apparatus that generates random numbers from a physical process, rather than a computer program. Such devices are often based on microscopic phenomena that generate low-level, statistically random ""noise"" signals, such as thermal noise, the photoelectric effect, and other quantum phenomena. These processes are, in theory, completely unpredictable, and the theory's assertions of unpredictability are subject to experimental test. A hardware random number generator typically consists of a transducer to convert some aspect of the physical phenomena to an electrical signal, an amplifier and other electronic circuitry to increase the amplitude of the random fluctuations to a measurable level, and some type of analog to digital converter to convert the output into a digital number, often a simple binary digit 0 or 1. By repeatedly sampling the randomly varying signal, a series of random numbers is obtained. The main application for electronic hardware random number generators is in cryptography, where they are used to generate random cryptographic keys to transmit data securely. They are widely used in Internet encryption protocols such as Secure Sockets Layer (SSL).Random number generators can also be built from ""random"" macroscopic processes, using devices such as coin flipping, dice, roulette wheels and lottery machines. The presence of unpredictability in these phenomena can be justified by the theory of unstable dynamical systems and chaos theory. Even though macroscopic processes are deterministic under Newtonian mechanics, the output of a well-designed device like a roulette wheel cannot be predicted in practice, because it depends on the sensitive, micro-details of the initial conditions of each use. Although dice have been mostly used in gambling, and in more recent times as ""randomizing"" elements in games (e.g. role playing games), the Victorian scientist Francis Galton described a way to use dice to explicitly generate random numbers for scientific purposes in 1890.Hardware random number generators generally produce a limited number of random bits per second. In order to increase the data rate, they are often used to generate the ""seed"" for a faster Cryptographically secure pseudorandom number generator, which then generates the pseudorandom output sequence.