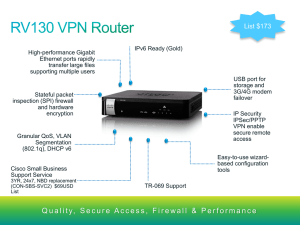
Cisco RV130/RV130W Product Overview
... • Require reliable, secure platform to access Internet • Business-class security (robust firewall) • Secure remote-access connection between sites (SSL/PPTP/IPsec VPN) • Secure remote access for mobile workers and teleworkers (three VPN clients) • Capability to optimize application performance over ...
... • Require reliable, secure platform to access Internet • Business-class security (robust firewall) • Secure remote-access connection between sites (SSL/PPTP/IPsec VPN) • Secure remote access for mobile workers and teleworkers (three VPN clients) • Capability to optimize application performance over ...
Routing on the Internet - Swarthmore`s CS
... • BGP (Border Gateway Protocol): The de facto inter-domain routing protocol • BGP provides each AS a means to: – external BGP: obtain subnet reachability information from neighboring ASs. – internal BGP: propagate reachability information to all AS-internal routers. – determine “good” routes to othe ...
... • BGP (Border Gateway Protocol): The de facto inter-domain routing protocol • BGP provides each AS a means to: – external BGP: obtain subnet reachability information from neighboring ASs. – internal BGP: propagate reachability information to all AS-internal routers. – determine “good” routes to othe ...
The End of Australia`s National Broadband Network?
... operate a wholesale network to encourage competition on that retail fixed broadband and achieve faster infrastructure buildout with higher quality and lower retail prices. The NBN aimed to connect 93 percent of Australian households and businesses (13 million premises) to a wholesale fiber-to-the-pr ...
... operate a wholesale network to encourage competition on that retail fixed broadband and achieve faster infrastructure buildout with higher quality and lower retail prices. The NBN aimed to connect 93 percent of Australian households and businesses (13 million premises) to a wholesale fiber-to-the-pr ...
Certification Exam Objectives: N10-005
... Copyright 2011 by the Computing Technology Industry Association. All rights reserved. The CompTIA Network+ Certification Exam Objectives are subject to change without notice. ...
... Copyright 2011 by the Computing Technology Industry Association. All rights reserved. The CompTIA Network+ Certification Exam Objectives are subject to change without notice. ...
Part 1
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
ppt - Worcester Polytechnic Institute
... Other Nodes Can Overhear Transmission If Receiving Node is Nexthop - Continue Else Store Packet in Buffer More Reliable Than Pure Broadcast Packets Have Several Tries To Get To Destination Snooping Nodes Get More Chances to Update Their ...
... Other Nodes Can Overhear Transmission If Receiving Node is Nexthop - Continue Else Store Packet in Buffer More Reliable Than Pure Broadcast Packets Have Several Tries To Get To Destination Snooping Nodes Get More Chances to Update Their ...
Cabernet: Connectivity Architecture for Better Network Services Yaping Zhu Rui Zhang-Shen
... The virtual machines provide isolated address space and resources for each control-plane process. Routing tables computed by the control planes are populated in run time at the corresponding data plane, as illustrated by the vertical arrows in Figure 3. Figure 3 illustrates how the data planes of di ...
... The virtual machines provide isolated address space and resources for each control-plane process. Routing tables computed by the control planes are populated in run time at the corresponding data plane, as illustrated by the vertical arrows in Figure 3. Figure 3 illustrates how the data planes of di ...
Internet Communications Module 7845i
... A single downstream 6 MHz television channel may support up to 27 Mbps of downstream data throughput from the cable headend using 64 QAM (quadrature amplitude modulation) transmission technology. Speeds can be boosted to 36 Mbps using 256 QAM. Upstream channels may deliver 500 kbps to 10 Mbps from h ...
... A single downstream 6 MHz television channel may support up to 27 Mbps of downstream data throughput from the cable headend using 64 QAM (quadrature amplitude modulation) transmission technology. Speeds can be boosted to 36 Mbps using 256 QAM. Upstream channels may deliver 500 kbps to 10 Mbps from h ...
PPT
... • Real-Time Interactive requirements on delay and its jitter have been satisfied by over-provisioning (providing plenty of bandwidth), what will happen when the load increases?... Lecture 20: 11/13/2001 ...
... • Real-Time Interactive requirements on delay and its jitter have been satisfied by over-provisioning (providing plenty of bandwidth), what will happen when the load increases?... Lecture 20: 11/13/2001 ...
pptx - Brown CS
... When does router start transmitting packet i? – If arrived before Fi-1, Si = Fi-1 – If no current packet for this flow, start when packet arrives (call this Ai): Si = Ai ...
... When does router start transmitting packet i? – If arrived before Fi-1, Si = Fi-1 – If no current packet for this flow, start when packet arrives (call this Ai): Si = Ai ...
Chapter 2 Lecture Presentation
... Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type field and then delivers packet to its IP layer IP layer examines IP packet destination address and determines IP packet should be routed to (2,2) Router’s table indicates (2,2) is directly connected via P ...
... Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type field and then delivers packet to its IP layer IP layer examines IP packet destination address and determines IP packet should be routed to (2,2) Router’s table indicates (2,2) is directly connected via P ...
Common WAN Components and Issues
... If using a local DNS server, a technician should verify the settings and make corrections accordingly. If the network is using the WAN provider's DNS settings, technicians should attempt to ping the IP address. If that works, then there is a WAN connection. The next test is to use the ping utility w ...
... If using a local DNS server, a technician should verify the settings and make corrections accordingly. If the network is using the WAN provider's DNS settings, technicians should attempt to ping the IP address. If that works, then there is a WAN connection. The next test is to use the ping utility w ...
Extracting Baseline Patterns in Internet Traffic Using Robust Principal Components
... is discussed in Section II.F. A. Data Arrangement The scheme extracts the baseline of a traffic trace, arranged in a matrix, referred as Y. Two arrangements are possible: data traces of multiple links over the same period of time, or data on a single link broken into windows. When data traces of mul ...
... is discussed in Section II.F. A. Data Arrangement The scheme extracts the baseline of a traffic trace, arranged in a matrix, referred as Y. Two arrangements are possible: data traces of multiple links over the same period of time, or data on a single link broken into windows. When data traces of mul ...
for TCP
... • Receiver may also buffer – Difficult to decide buffer size as TPDUs – Dynamic buffer allocation may be best strategy – Buffer size negotiated by exchange of control packets – Deadlock can occur if control packets get lost • Solution is periodic sending of control TPDUs containing acknowledgements ...
... • Receiver may also buffer – Difficult to decide buffer size as TPDUs – Dynamic buffer allocation may be best strategy – Buffer size negotiated by exchange of control packets – Deadlock can occur if control packets get lost • Solution is periodic sending of control TPDUs containing acknowledgements ...
Multi-layer Traffic Engineering in Data-centric Optical
... assumed that STE processes react passively to MTE actions, it may be more rewarding to consider both STE and MTE actions on the same level. Finally, the capabilities of the strategy are influenced by the granularity by which grooming decisions are made [8]. With a per-flow granularity, each flow can ...
... assumed that STE processes react passively to MTE actions, it may be more rewarding to consider both STE and MTE actions on the same level. Finally, the capabilities of the strategy are influenced by the granularity by which grooming decisions are made [8]. With a per-flow granularity, each flow can ...
ATM
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
ppt - Carnegie Mellon School of Computer Science
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
Linux+ Guide to Linux Certification
... fiber-optic, wireless communication – Data Link layer: TCP compatible with IEEE 802.2 LLC and MAC addressing – Network layer: TCP/IP equivalent is IP – Transport layer: both TCP and UDP operate here – Upper layers of OSI correspond to TCP/IP ...
... fiber-optic, wireless communication – Data Link layer: TCP compatible with IEEE 802.2 LLC and MAC addressing – Network layer: TCP/IP equivalent is IP – Transport layer: both TCP and UDP operate here – Upper layers of OSI correspond to TCP/IP ...
Computer Networks and the Internet
... multiplexing gains to be had, and by using circuits, each connection will get a constant amount of bandwidth that matches its CBR rate. On the other hand, circuit-switching has more overhead in terms of signaling needed to set up the call, so there is an argument that packet-switching is preferable ...
... multiplexing gains to be had, and by using circuits, each connection will get a constant amount of bandwidth that matches its CBR rate. On the other hand, circuit-switching has more overhead in terms of signaling needed to set up the call, so there is an argument that packet-switching is preferable ...
NetScreen Technologies, Inc. NetScreen-5 versus
... load for 64-byte packets on 10 Mbit/s Ethernet discards 99.95% of the packets; for 512-byte packets, it discards 8.099% packets; and for 1,024-byte packets, it discards 0.005% of the packets. The WatchGuard SOHO was unable to pass 1,518-byte packets through the VPN tunnel because it must fragment th ...
... load for 64-byte packets on 10 Mbit/s Ethernet discards 99.95% of the packets; for 512-byte packets, it discards 8.099% packets; and for 1,024-byte packets, it discards 0.005% of the packets. The WatchGuard SOHO was unable to pass 1,518-byte packets through the VPN tunnel because it must fragment th ...
Tata Consultancy Services
... a diverse range of technologies and systems. The Cisco data network had evolved over many years, resulting in fragmented VLAN Trunk Protocol (VTP) domain networks with multiple core switches and a mix of two-tier and flat network architectures. Point-to-point WAN links connected three data centers a ...
... a diverse range of technologies and systems. The Cisco data network had evolved over many years, resulting in fragmented VLAN Trunk Protocol (VTP) domain networks with multiple core switches and a mix of two-tier and flat network architectures. Point-to-point WAN links connected three data centers a ...
22-InternetCloudTech.. - Systems and Computer Engineering
... Paul Baron “On Distributed Communications Networks” RAND Corp. ...
... Paul Baron “On Distributed Communications Networks” RAND Corp. ...
IP address of a network
... • The original classful address scheme had a number of problems – Problem 1. Too few network addresses for large networks • Class A and Class B addresses are gone – Problem 2. Two-layer hierarchy is not appropriate for large networks with Class A and Class B addresses. • Fix #1: Subnetting ...
... • The original classful address scheme had a number of problems – Problem 1. Too few network addresses for large networks • Class A and Class B addresses are gone – Problem 2. Two-layer hierarchy is not appropriate for large networks with Class A and Class B addresses. • Fix #1: Subnetting ...
slides #2 - The Fengs
... If another host broadcasted a response before you had the chance to, unschedule your response ...
... If another host broadcasted a response before you had the chance to, unschedule your response ...
IP Multimedia Subsystem and Its Future Perspectives
... receivers used to communicate directly with the User Equipment (UE). The eNodeB connects the UE of the subscriber (mobile device) to the LTE network. The Evolved Packet Core (EPC) is the IP-based packet only Core Network for LTE. The EPC carries all kind of traffic (video, voice, and data) in packet ...
... receivers used to communicate directly with the User Equipment (UE). The eNodeB connects the UE of the subscriber (mobile device) to the LTE network. The Evolved Packet Core (EPC) is the IP-based packet only Core Network for LTE. The EPC carries all kind of traffic (video, voice, and data) in packet ...