The Packet Filter: A Basic Network Security Tool
... What is a packet filter? According to the internet.com webopedia, packet filtering is “controlling access to a network by analyzing the incoming and outgoing packets and letting them pass or halting them based on the IP address of the source and destination. Packet filtering is one technique, among ...
... What is a packet filter? According to the internet.com webopedia, packet filtering is “controlling access to a network by analyzing the incoming and outgoing packets and letting them pass or halting them based on the IP address of the source and destination. Packet filtering is one technique, among ...
A Platform for Unobtrusive Measurements on PlanetLab Rob Sherwood Neil Spring Abstract
... PlanetLab web servers don’t implement persistent millions requests per day [3]. Of the 13,447,011 unique connections. RedHat Fedora Core 2, PlanetLab’s base IP addresses, we ran a Sidecar based traceroute scan back distribution, ships with persistent web connections disto each client, using the algo ...
... PlanetLab web servers don’t implement persistent millions requests per day [3]. Of the 13,447,011 unique connections. RedHat Fedora Core 2, PlanetLab’s base IP addresses, we ran a Sidecar based traceroute scan back distribution, ships with persistent web connections disto each client, using the algo ...
THE NETWORK LAYER 5.2 ROUTING ALGORITHMS
... else forward datagram to default-Router Basis: Routing table of the IP layer; each entry contains: destination address: network or host address (specified by the flag G or H) IP address of the next-hop router (Flag G) or address of directly connected network flags for the route (if set): G - r ...
... else forward datagram to default-Router Basis: Routing table of the IP layer; each entry contains: destination address: network or host address (specified by the flag G or H) IP address of the next-hop router (Flag G) or address of directly connected network flags for the route (if set): G - r ...
Presenting
... a bad load ratio because once the weights of the links are determined, the routing is insensitive to the load already routed through a link. • Thus we suggest a centralized algorithm that is given as input a network graph and a flow demand matrix. The demand matrix is build from long term gathered s ...
... a bad load ratio because once the weights of the links are determined, the routing is insensitive to the load already routed through a link. • Thus we suggest a centralized algorithm that is given as input a network graph and a flow demand matrix. The demand matrix is build from long term gathered s ...
ANALYSIS OF RED PACKET LOSS PERFORMANCE IN A SIMULATED IP WAN
... The Internet supports a diverse number of applications, which have different requirements for a number of services. Next generation networks provide high speed connectivity between hosts, which leaves the service provider to configure network devices appropriately, in order to maximize network perfo ...
... The Internet supports a diverse number of applications, which have different requirements for a number of services. Next generation networks provide high speed connectivity between hosts, which leaves the service provider to configure network devices appropriately, in order to maximize network perfo ...
Wavelength - Allstream
... Carriers looking to provide advanced IP solutions to business customers in Canada face many challenges. The Global Carrier Solutions team helps carriers around the world simplify operations to improve productivity, maximize performance and manage costs. Allstream is the only national communications ...
... Carriers looking to provide advanced IP solutions to business customers in Canada face many challenges. The Global Carrier Solutions team helps carriers around the world simplify operations to improve productivity, maximize performance and manage costs. Allstream is the only national communications ...
Implementation of IPv6 ToS over ATM Network
... instead of the original implementation that could support only one SVC per node. This modification is required in order to allow the packet generator to transmit IPv6 packets over multiple SVC’s within the same node. A new user attribute called “IPv6 ToS Mapping” is also added to the source. This ne ...
... instead of the original implementation that could support only one SVC per node. This modification is required in order to allow the packet generator to transmit IPv6 packets over multiple SVC’s within the same node. A new user attribute called “IPv6 ToS Mapping” is also added to the source. This ne ...
3rd Edition: Chapter 4
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
SDN - RedIRIS
... MASSIVE PARADIGM SHIFT FROM CLOSED, STATIC CONFIGURATION TO OPEN, DYNAMIC ADAPTATION ...
... MASSIVE PARADIGM SHIFT FROM CLOSED, STATIC CONFIGURATION TO OPEN, DYNAMIC ADAPTATION ...
GRIDs - Desy
... restrict access to my data to users from my experiment only“) • reliable and (sometimes) SLA guaranteed network access („I want to contribute data from my repositiory to an evaluation algorithm at site x with guaranteed minimum delay“) ...
... restrict access to my data to users from my experiment only“) • reliable and (sometimes) SLA guaranteed network access („I want to contribute data from my repositiory to an evaluation algorithm at site x with guaranteed minimum delay“) ...
network layer
... Implementation of Connectionless Service • Packets are injected into the subnet individually • Routed independently of each other. • Packets are called datagrams (in analogy with telegrams) and the subnet is called a datagram subnet. . • Each datagram contains full destination addrs • Every router ...
... Implementation of Connectionless Service • Packets are injected into the subnet individually • Routed independently of each other. • Packets are called datagrams (in analogy with telegrams) and the subnet is called a datagram subnet. . • Each datagram contains full destination addrs • Every router ...
Voice over IP
... particular area, it should discuss with the local PSAPs or their coordinator (as identified on the NENA website) the approach to providing access. (For example, if routing to 10-digit number, confirm the correct number with the PSAP.) This obligation does not apply to any “roaming” by customers. ...
... particular area, it should discuss with the local PSAPs or their coordinator (as identified on the NENA website) the approach to providing access. (For example, if routing to 10-digit number, confirm the correct number with the PSAP.) This obligation does not apply to any “roaming” by customers. ...
Introduction to Evolved Packet Core: Protocols and
... A guaranteed bit rate for the whole duration of the CS call (even in case of congestion) ...
... A guaranteed bit rate for the whole duration of the CS call (even in case of congestion) ...
3rd Edition: Chapter 4
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered fo ...
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered fo ...
Marina Papatriantafilou – Network layer part 1 (Data Plane)
... Switching Via an Interconnection Network • Overcome bus bandwidth limitations • Banyan networks, other interconnection nets (also used in processors-memory interconnects in multiprocessors) – Cisco 12000: switches at 60 Gbps – Example Banyan interconnect: using 3-bit link address ...
... Switching Via an Interconnection Network • Overcome bus bandwidth limitations • Banyan networks, other interconnection nets (also used in processors-memory interconnects in multiprocessors) – Cisco 12000: switches at 60 Gbps – Example Banyan interconnect: using 3-bit link address ...
Solution
... physical network through which the frame has just traveled. The format and size of the sent frame depend on the protocol used by the physical network through which the frame is going to travel. For example, if a router connects a LAN to a WAN, it receives a frame in the LAN format and sends a frame ...
... physical network through which the frame has just traveled. The format and size of the sent frame depend on the protocol used by the physical network through which the frame is going to travel. For example, if a router connects a LAN to a WAN, it receives a frame in the LAN format and sends a frame ...
18. Protocols for QoS Support
... Desired QoS Used to set parameters in node’s packet scheduler Service class, Rspec (reserve), Tspec (traffic) ...
... Desired QoS Used to set parameters in node’s packet scheduler Service class, Rspec (reserve), Tspec (traffic) ...
ppt - The Fengs
... – Program that promiscuously monitors and injects network traffic to/from machines it is protecting – Monitors net for SYN packets not acknowledged after a certain period of time – If it detects problems with a half-open connection it can • Send RST packets to the sender to release destination resou ...
... – Program that promiscuously monitors and injects network traffic to/from machines it is protecting – Monitors net for SYN packets not acknowledged after a certain period of time – If it detects problems with a half-open connection it can • Send RST packets to the sender to release destination resou ...
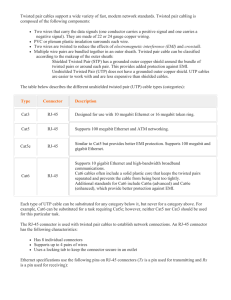
Description
... certificates to devices. If the U2000 cannot communicate with the CA, users can manually apply for a device certificate. The procedure is as follows: Users fill in a certificate application form on the U2000 and the U2000 accordingly generates an application file; users submit the application file t ...
... certificates to devices. If the U2000 cannot communicate with the CA, users can manually apply for a device certificate. The procedure is as follows: Users fill in a certificate application form on the U2000 and the U2000 accordingly generates an application file; users submit the application file t ...
Secure Network Infrastructure
... issue through use of timestamps, a synchronized dependable mechanism of obtaining time is needed. ...
... issue through use of timestamps, a synchronized dependable mechanism of obtaining time is needed. ...
IP_Suite - Virginia Tech
... •Fragment Offset: offset of fragment in this datagram in 8-byte units •Flags (DF and MF): indicate if last fragment, and If datagram should not be fragmented (What happens if need to fragment and DF is set?) •Time To Live: maximum number of routers through which the datagram may pass Decremented at ...
... •Fragment Offset: offset of fragment in this datagram in 8-byte units •Flags (DF and MF): indicate if last fragment, and If datagram should not be fragmented (What happens if need to fragment and DF is set?) •Time To Live: maximum number of routers through which the datagram may pass Decremented at ...
CCNA testout unit 2
... each switch port. Create separate collision domains. Provide guaranteed bandwidth between devices if dedicated ports are used. Enable full-duplex communication. Can simultaneously switch multiple messages. Support rate adaptation, which allows devices that run at different speeds to communicate with ...
... each switch port. Create separate collision domains. Provide guaranteed bandwidth between devices if dedicated ports are used. Enable full-duplex communication. Can simultaneously switch multiple messages. Support rate adaptation, which allows devices that run at different speeds to communicate with ...
Advances in Natural and Applied Sciences
... QoS metrics modeling which is based on QoS parameters. In the NoC nodes he quantifies the buffer requirements and packet switching technique by done analysis on End-to-End delays and packet loss. Their work is fully focused on flit losses which is occur because of buffer congestion for a network loa ...
... QoS metrics modeling which is based on QoS parameters. In the NoC nodes he quantifies the buffer requirements and packet switching technique by done analysis on End-to-End delays and packet loss. Their work is fully focused on flit losses which is occur because of buffer congestion for a network loa ...