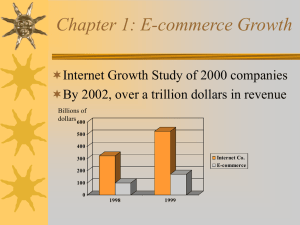
Network Emulation
... Model of interaction between application and delivered quality from network Environment for evaluation of existing applications Capture process to apply to existing / ...
... Model of interaction between application and delivered quality from network Environment for evaluation of existing applications Capture process to apply to existing / ...
Chapters 1-8 notes - SRU Computer Science
... – Ticket Granting Service maintains DB of valid users ...
... – Ticket Granting Service maintains DB of valid users ...
CHAPTER 7 - McGraw Hill Higher Education
... Unified Communication (UC)—The integration of communication channels into a single service Peer-to-Peer (P2P)—A computer network that relies on the computing power and bandwidth of the participants in the network rather than a centralized server Voice over IP (VoIP)—Uses IP technology to trans ...
... Unified Communication (UC)—The integration of communication channels into a single service Peer-to-Peer (P2P)—A computer network that relies on the computing power and bandwidth of the participants in the network rather than a centralized server Voice over IP (VoIP)—Uses IP technology to trans ...
Circuit Switched vs. Packet Switched Technology
... Is used for modem connections across PSTN, ISDN, and T-carriers ...
... Is used for modem connections across PSTN, ISDN, and T-carriers ...
A Study on Quality of Service Issues
... Can be reduced by using Jitter buffers – To allow for variable packet arrival times and still achieve steady stream of packets, the receiver holds the first packet in a jitter buffer , before playing it out. ...
... Can be reduced by using Jitter buffers – To allow for variable packet arrival times and still achieve steady stream of packets, the receiver holds the first packet in a jitter buffer , before playing it out. ...
Objectives Configure routing in Windows Server 2008 Configure
... • Can force authentication between routers when announcements are sent • Password for authentication is plain text • Can configure which incoming and outgoing routes are accepted • Split-horizon processing stops information from going back in the direction it was received from • Poison-reverse proce ...
... • Can force authentication between routers when announcements are sent • Password for authentication is plain text • Can configure which incoming and outgoing routes are accepted • Split-horizon processing stops information from going back in the direction it was received from • Poison-reverse proce ...
Accounting Management - University of Wollongong
... • As part of Accounting management you need to – Decide which resources to measure – Collect metrics about their use ...
... • As part of Accounting management you need to – Decide which resources to measure – Collect metrics about their use ...
New Hampshire Department of Transportation I
... strategic plan to improve and consolidate the existing statewide point-to-point microwave analog and time-division multiplexing (TDM) network that existed on 20 mountaintop sites throughout the state. Being one of the first states to integrate multiple stakeholders using existing traffic management ...
... strategic plan to improve and consolidate the existing statewide point-to-point microwave analog and time-division multiplexing (TDM) network that existed on 20 mountaintop sites throughout the state. Being one of the first states to integrate multiple stakeholders using existing traffic management ...
Security+ Guide to Network Security Fundamentals
... within packets carried by second network Best-known example: virtual private networks Replacing WAN links because of security and low cost An option for most IP connectivity requirements ...
... within packets carried by second network Best-known example: virtual private networks Replacing WAN links because of security and low cost An option for most IP connectivity requirements ...
Chap 11: Network Security Topologies
... Include demilitarized zones (DMZs) extranets, and intranets continued… ...
... Include demilitarized zones (DMZs) extranets, and intranets continued… ...
EECP 0442
... TCP/IP uses IP-addresses, which are 32-bit numbers. To make it easier to memorize such IP-addresses, they are usually expressed as 4 8-bit numbers (example: 192.168.10.1), where each of the 4 numbers is within the range of '0' to '255' (there are restriction on using '0' and '255', avoid using them. ...
... TCP/IP uses IP-addresses, which are 32-bit numbers. To make it easier to memorize such IP-addresses, they are usually expressed as 4 8-bit numbers (example: 192.168.10.1), where each of the 4 numbers is within the range of '0' to '255' (there are restriction on using '0' and '255', avoid using them. ...
Email Slides - University of San Francisco
... Internet & E-mail Mary Vattavayalil University of San Francisco ...
... Internet & E-mail Mary Vattavayalil University of San Francisco ...
Lecture01
... (1 ms vs. 100 ms propagation time) is more important than bandwidth (1 Mbps vs. 100 Mbps) for a large message (e.g., 25 Mbyte), bandwidth is more important than distance ...
... (1 ms vs. 100 ms propagation time) is more important than bandwidth (1 Mbps vs. 100 Mbps) for a large message (e.g., 25 Mbyte), bandwidth is more important than distance ...
Document
... lower level LAN a specific IP address where it can be reached. This assignment is periodically checked by sending Address Resolution Protocol (ARP) packets. These packets make sure that the device given a certain IP is still available and at the location intended. Firewalls are an added bonus that a ...
... lower level LAN a specific IP address where it can be reached. This assignment is periodically checked by sending Address Resolution Protocol (ARP) packets. These packets make sure that the device given a certain IP is still available and at the location intended. Firewalls are an added bonus that a ...
slides 1
... It is much easier to share resources Allows a whole set of distributed applications A whole set of future problems need machine communication • Collaboration: Much easier for users to collaborate through network resources (such as network file systems) ...
... It is much easier to share resources Allows a whole set of distributed applications A whole set of future problems need machine communication • Collaboration: Much easier for users to collaborate through network resources (such as network file systems) ...
Check Your Understanding Chapter 7 Part 1 For a quick review to
... 1. The current standard for home wireless Ethernet networks is a. WiGig. b. 802.3. c. 802.11ac. d. all of the above. 2. The type of network used for communication among a laptop and smartphone using Bluetooth is a a. WAN. b. PAN. c. LAN. d. MAN. 3. The fastest broadband Internet service is usually a ...
... 1. The current standard for home wireless Ethernet networks is a. WiGig. b. 802.3. c. 802.11ac. d. all of the above. 2. The type of network used for communication among a laptop and smartphone using Bluetooth is a a. WAN. b. PAN. c. LAN. d. MAN. 3. The fastest broadband Internet service is usually a ...
Networking
... Switches Consider packing sniffing software threat for people who share a hub and have not activated network encryption Data sent “in the clear” means it has not been encrypted, and therefore is vulnerable to eavesdropping via a hub ...
... Switches Consider packing sniffing software threat for people who share a hub and have not activated network encryption Data sent “in the clear” means it has not been encrypted, and therefore is vulnerable to eavesdropping via a hub ...
Internet and WWW - Computer Science Department
... digital subscription line (DSL), a TV cable company, or a phone line. DSL and cable connections are high speed (also called broad band) connections. The phone line is much lower speed, but you do not pay any extra charges over the cost of your phone connection. ...
... digital subscription line (DSL), a TV cable company, or a phone line. DSL and cable connections are high speed (also called broad band) connections. The phone line is much lower speed, but you do not pay any extra charges over the cost of your phone connection. ...
CHAPTER 6
... Refers to the amount of time that it takes a packet to get to its destination. It represents the lag, or delay in communications, between your computer and another (target) computer. A ping test can be used to measure latency. Having low latency (i.e. fast response) is especially important where ...
... Refers to the amount of time that it takes a packet to get to its destination. It represents the lag, or delay in communications, between your computer and another (target) computer. A ping test can be used to measure latency. Having low latency (i.e. fast response) is especially important where ...
CARNIVORE
... Windows NT (or Windows 2000) computer system with 128-megabytes of RAM, a Pentium III, 4-18 gigabytes of disk space, and a 2G Jaz drive where evidence is saved. The software is written in C++. The box has no TCP/IP protocol use (so it cannot get hacked into). A hardware authentication device is used ...
... Windows NT (or Windows 2000) computer system with 128-megabytes of RAM, a Pentium III, 4-18 gigabytes of disk space, and a 2G Jaz drive where evidence is saved. The software is written in C++. The box has no TCP/IP protocol use (so it cannot get hacked into). A hardware authentication device is used ...
CS514: Intermediate Course in Operating Systems
... typically sent for every other TCP data segment. These “overhead” packets are necessary for reliability and congestion control; similarly, RON’s active probes may be viewed as “overhead” that help achieve rapid recovery from failures.” ...
... typically sent for every other TCP data segment. These “overhead” packets are necessary for reliability and congestion control; similarly, RON’s active probes may be viewed as “overhead” that help achieve rapid recovery from failures.” ...
Internet Measurements - Computer Science & Engineering
... Grows with no central authority Autonomous Systems optimize local communication efficiency The building blocks are engineered and studied in depth Global entity has not been characterized ...
... Grows with no central authority Autonomous Systems optimize local communication efficiency The building blocks are engineered and studied in depth Global entity has not been characterized ...
Name: Leo Mendoza WAN (used to be slow, noisy)
... between sender and reciever and all data passes over this circuit (bandwidth reserved, using Synchronous Time Division Multiplexing [TDM])-example, telephone system (dedicated connection until termination) Packet switched subnet - subnet in which all data messages are transmitted using fixed-size pa ...
... between sender and reciever and all data passes over this circuit (bandwidth reserved, using Synchronous Time Division Multiplexing [TDM])-example, telephone system (dedicated connection until termination) Packet switched subnet - subnet in which all data messages are transmitted using fixed-size pa ...