2011-regulation-iab - Columbia CS
... No blocking. Fixed broadband providers may not block lawful content, applications, services, or non-harmful devices; mobile broadband providers may not block lawful websites, or block applications that compete with their voice or video telephony services ...
... No blocking. Fixed broadband providers may not block lawful content, applications, services, or non-harmful devices; mobile broadband providers may not block lawful websites, or block applications that compete with their voice or video telephony services ...
internetworks - UNC School of Information and Library Science
... When the destination host has been waiting for a particular packet for a certain time (timeout), it will request the source host to retransmit the packet. There is no need to retransmit all data packets. Instead, only the missing packet, which is identified by the sequence number, needs to be re ...
... When the destination host has been waiting for a particular packet for a certain time (timeout), it will request the source host to retransmit the packet. There is no need to retransmit all data packets. Instead, only the missing packet, which is identified by the sequence number, needs to be re ...
Chapter 4 Computer Networks – Part 2
... represented by light pulses at speeds of billions of bits per second. ...
... represented by light pulses at speeds of billions of bits per second. ...
Communications Networks II: Design and Algorithms
... multiplexing/de-multiplexing at edge, shared network core ...
... multiplexing/de-multiplexing at edge, shared network core ...
Types of networks based on physical scope Local area network
... transmission facilities provided by common carriers, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer. STC support this service by using Aamal Net , this services prov ...
... transmission facilities provided by common carriers, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer. STC support this service by using Aamal Net , this services prov ...
Northland Communications
... our network. 1. General restrictions on types of devices to connect to network: Our Internet Services work with most types of PCs and laptops including Macs and other Internet-compatible devices like game systems and Internet enabled TVs. If a wireless router is connected to our Internet Services, w ...
... our network. 1. General restrictions on types of devices to connect to network: Our Internet Services work with most types of PCs and laptops including Macs and other Internet-compatible devices like game systems and Internet enabled TVs. If a wireless router is connected to our Internet Services, w ...
Improving Performance of ALM Systems with Bayesian
... 10 active at same time is less than .0004 * ...
... 10 active at same time is less than .0004 * ...
Acronym Chart and Networking Vocabulary Monroe County Library
... Designed for telephone and network installations: STP-shielded twisted pair; UTPunshielded twisted-pair; use RJ-11 plugs for telephone or RJ-45 plugs for computer networks Cable categories (CAT) indicate carrying capacity: CAT-1 is sufficient for telephone cabling, CAT-5 provides more capacity for n ...
... Designed for telephone and network installations: STP-shielded twisted pair; UTPunshielded twisted-pair; use RJ-11 plugs for telephone or RJ-45 plugs for computer networks Cable categories (CAT) indicate carrying capacity: CAT-1 is sufficient for telephone cabling, CAT-5 provides more capacity for n ...
Telecommunication
... square of the number of users If there are only 2 users on the network, it’s not very useful; if there are 200 it’s much more useful. So the Internet with millions of computers is incredibly useful. ...
... square of the number of users If there are only 2 users on the network, it’s not very useful; if there are 200 it’s much more useful. So the Internet with millions of computers is incredibly useful. ...
csci5211: Computer Networks and Data Communications
... “reliability” – no congestion, in order data in circuit-switching • packet switching: better bandwidth use • state, resources: packet switching has less state ...
... “reliability” – no congestion, in order data in circuit-switching • packet switching: better bandwidth use • state, resources: packet switching has less state ...
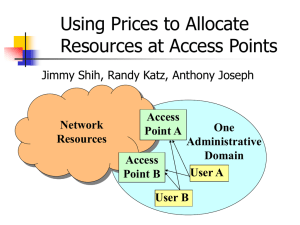
Design Review of Using Prices to Allocate Resources at a H
... Measure how quickly a user can obtain large amount of bandwidth if he is willing to pay for them. Measure users’ willingness to pay at any given time. Measure a user’ willingness to pay throughout a day. ...
... Measure how quickly a user can obtain large amount of bandwidth if he is willing to pay for them. Measure users’ willingness to pay at any given time. Measure a user’ willingness to pay throughout a day. ...
Lecture 3: Introduction to net
... thousands of other servers, and impacted a multitude of systems ranging from (bank) ATM systems to air traffic control to emergency (911) systems (25 Jan) ...
... thousands of other servers, and impacted a multitude of systems ranging from (bank) ATM systems to air traffic control to emergency (911) systems (25 Jan) ...
PPP - Ivailo Chakarov
... The available speed/power of the requesting machine (Client) The available speed/power of the responding machine (server) Routing delays within the network Design and topology of the networks transferring the data Type of data being transferred Time of day (other users on the network) ...
... The available speed/power of the requesting machine (Client) The available speed/power of the responding machine (server) Routing delays within the network Design and topology of the networks transferring the data Type of data being transferred Time of day (other users on the network) ...
A6_Oct_07_08 - Raadio- ja sidetehnika instituut
... Internet protocol • Provides best effort, connectionless packet delivery – motivated by need to keep routers simple and by adaptibility to failure of network elements – packets may be lost, out of order, or even duplicated – higher layer protocols must deal with these, if necessary ...
... Internet protocol • Provides best effort, connectionless packet delivery – motivated by need to keep routers simple and by adaptibility to failure of network elements – packets may be lost, out of order, or even duplicated – higher layer protocols must deal with these, if necessary ...
Lesson 7 - GEOCITIES.ws
... and the person talking on the other end can still be heard by the other party while they are talking. Digital subscriber line (DSL), two-way cable modem, and other broadband technologies operate in full-duplex mode. ...
... and the person talking on the other end can still be heard by the other party while they are talking. Digital subscriber line (DSL), two-way cable modem, and other broadband technologies operate in full-duplex mode. ...
Optimizing Your Network Design
... Prioritization and Traffic Management on WAN Switches • WAN switch features: – Advanced Class of Service (CoS) management provides dedicated queues and queuing algorithms for the different sub-classes of serviced defined in a network – Optimized Bandwidth Management - an implementation of version 4 ...
... Prioritization and Traffic Management on WAN Switches • WAN switch features: – Advanced Class of Service (CoS) management provides dedicated queues and queuing algorithms for the different sub-classes of serviced defined in a network – Optimized Bandwidth Management - an implementation of version 4 ...
EoC Head-End Unit - Billion Electric
... Extends a high-speed Internet connection through existing CATV network EoC network system establishes a network within a building or community, enabling broadband connectivity over existing coaxial cables already in place. It provides fast reliable and cost effective distribution of broadband Intern ...
... Extends a high-speed Internet connection through existing CATV network EoC network system establishes a network within a building or community, enabling broadband connectivity over existing coaxial cables already in place. It provides fast reliable and cost effective distribution of broadband Intern ...
Unleashing Infrastructure Synergies Across Sectors Abu Saeed Khan Senior Policy Fellow
... Arabia, Bahrain and Qatar. Its final destination is Turkey via Iraq. – The consortium is yet to disclose its mode of transport while crossing the highly challenging (in every respect) terrains of Iraq. ...
... Arabia, Bahrain and Qatar. Its final destination is Turkey via Iraq. – The consortium is yet to disclose its mode of transport while crossing the highly challenging (in every respect) terrains of Iraq. ...
Introduction - Communications
... organization that provides administrative support for the Internet. Founded in 1992, ISOC is the organizational home for the standardization bodies of the Internet. Internet Engineering Task Force (IETF): Forum that coordinates the development of new protocols and standards. Organized into working g ...
... organization that provides administrative support for the Internet. Founded in 1992, ISOC is the organizational home for the standardization bodies of the Internet. Internet Engineering Task Force (IETF): Forum that coordinates the development of new protocols and standards. Organized into working g ...
presentation source
... GARR-B High-bandwidth infrastructure (34-155M) based on ATM VPs (CBR), with high-speed links to European research network and the Internet 15 PoP throughout Italy - the PoPs are in the Telecom premises, but the network is managed by the GARR consortium (practically speaking, at the moment, by ...
... GARR-B High-bandwidth infrastructure (34-155M) based on ATM VPs (CBR), with high-speed links to European research network and the Internet 15 PoP throughout Italy - the PoPs are in the Telecom premises, but the network is managed by the GARR consortium (practically speaking, at the moment, by ...
The Internet: Co-Evolution of Technology and Society
... 3. support multiple types of communications service 4. accommodate a variety of network types 5. permit distributed management of resources 6. cost effective 7. low effort to attach a host 8. account for resources ...
... 3. support multiple types of communications service 4. accommodate a variety of network types 5. permit distributed management of resources 6. cost effective 7. low effort to attach a host 8. account for resources ...
Plutarch
... Key components to our architecture are contexts and IFs. Also important is the accompanying infrastructure to make it work. ...
... Key components to our architecture are contexts and IFs. Also important is the accompanying infrastructure to make it work. ...
1 Course Outline Computing Science Department Faculty of Science
... distance vector, link state, routing protocols RIP, OSPF, BGP, IP addressing, subnetting and supernetting, variable length subnet masking. ...
... distance vector, link state, routing protocols RIP, OSPF, BGP, IP addressing, subnetting and supernetting, variable length subnet masking. ...
Network Emulation
... Correlated loss and delay, natural induced jitter Topology or environment changes (e.g. wireless) ...
... Correlated loss and delay, natural induced jitter Topology or environment changes (e.g. wireless) ...