Chapter 4: Network Layer
... – (in contrast, transport-layer connection only involved two end systems) ...
... – (in contrast, transport-layer connection only involved two end systems) ...
Effective Enterprise Java: Architecture
... – If the component doesn’t straddle the network, it’s much easier to control – Ask yourself, “How do we react if the schema and code need to evolve independently?” – Prefer to define contracts, not shared types ...
... – If the component doesn’t straddle the network, it’s much easier to control – Ask yourself, “How do we react if the schema and code need to evolve independently?” – Prefer to define contracts, not shared types ...
network
... project, sponsored by the Advanced Research Projects Agency (ARPA) originally it was called the ARPANET © 2006 Pearson Education ...
... project, sponsored by the Advanced Research Projects Agency (ARPA) originally it was called the ARPANET © 2006 Pearson Education ...
Basic Operations of the SIP-Based Mobile Network
... global reachability of a device without interruption even when it is moving around. • However, these host mobility management schemes manage the mobility and connectivity of mobile devices in an individual manner. • Supporting host mobility when users exhibit group mobility causes significant costs. ...
... global reachability of a device without interruption even when it is moving around. • However, these host mobility management schemes manage the mobility and connectivity of mobile devices in an individual manner. • Supporting host mobility when users exhibit group mobility causes significant costs. ...
Network
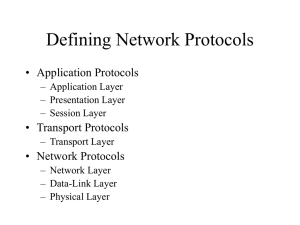
... voltage levels. Examples are RS-232-C and X.21 • Datalink layer ensures reliable transfer of data across the physical medium. It also provides access control to the media in the case of local area networks. Examples are High-level Data Link Control (HDLC), LLC and SDLC • Network layer provides the u ...
... voltage levels. Examples are RS-232-C and X.21 • Datalink layer ensures reliable transfer of data across the physical medium. It also provides access control to the media in the case of local area networks. Examples are High-level Data Link Control (HDLC), LLC and SDLC • Network layer provides the u ...
To start with, the Internet of Things is new
... cellular network has become the first access point to the internet for many mobile devices, however, this network is based on an addressing and transport architecture derived from switching technology, then from routing technology based on the IPv4. ...
... cellular network has become the first access point to the internet for many mobile devices, however, this network is based on an addressing and transport architecture derived from switching technology, then from routing technology based on the IPv4. ...
summary notes basic 6 (term 2)
... 5. Cost. Networkable versions of many popular software programs are available at considerable savings compared to buying individual licensed copies. Its allows easier upgrading of the program. 6. Security. Files and programs on a network are more secure as the users do not have to worry about illeg ...
... 5. Cost. Networkable versions of many popular software programs are available at considerable savings compared to buying individual licensed copies. Its allows easier upgrading of the program. 6. Security. Files and programs on a network are more secure as the users do not have to worry about illeg ...
Lecture 1 - Project Open
... Mid 60s: Publications on packet switching from RAND (Paul Baran) and the National Physical Lab in the U.K. (Donald Davies). RAND was studying network survivability after nuclear war: ―If war does not mean the end of the earth in a black and white manner, then it follows that we should do those thin ...
... Mid 60s: Publications on packet switching from RAND (Paul Baran) and the National Physical Lab in the U.K. (Donald Davies). RAND was studying network survivability after nuclear war: ―If war does not mean the end of the earth in a black and white manner, then it follows that we should do those thin ...
Part I: Introduction
... packet of L bits on to link or R bps Entire packet must arrive at router before it can be transmitted on next link: store and ...
... packet of L bits on to link or R bps Entire packet must arrive at router before it can be transmitted on next link: store and ...
CS514-lec
... on the net and slow the transfer down by 7% for this purpose! • But the end-to-end argument would not apply if: – p or n is large, hence (1-p)n approaches 0 – cost of recovery when a problem occurs is very high – reliability property is hard for users to implement ...
... on the net and slow the transfer down by 7% for this purpose! • But the end-to-end argument would not apply if: – p or n is large, hence (1-p)n approaches 0 – cost of recovery when a problem occurs is very high – reliability property is hard for users to implement ...
Packet switching
... • Also on some networking devices, like routers and switches • Runs on port 23 • Allows clients access to a more powerful computer, or a computer without screen (like a router) ...
... • Also on some networking devices, like routers and switches • Runs on port 23 • Allows clients access to a more powerful computer, or a computer without screen (like a router) ...
Connecting to the RUTH ENLOW LIBRARY Wireless Internet
... The Library's wireless network is not secure. Due to the technical nature of configuring laptop pc’s, as well as for liability reasons, the library staff is not permitted to provide technical assistance. No guarantee can be provided that you will be able to make a wireless connection. The Library as ...
... The Library's wireless network is not secure. Due to the technical nature of configuring laptop pc’s, as well as for liability reasons, the library staff is not permitted to provide technical assistance. No guarantee can be provided that you will be able to make a wireless connection. The Library as ...
Review the ppt notes
... something (person, group, department, etc.) outside the system that interacts with the system by providing input or receiving information. Data storage Used to store data in the system. Represents a file, a database, etc. ...
... something (person, group, department, etc.) outside the system that interacts with the system by providing input or receiving information. Data storage Used to store data in the system. Represents a file, a database, etc. ...
Internet Backplane Protocol API and Applications
... Enter the exNode • In the Unix file system, blocks are aggregated into files using the intermediate node data structure, or inode • We implement file semantics on top of IBP using the external node (exNode) data ...
... Enter the exNode • In the Unix file system, blocks are aggregated into files using the intermediate node data structure, or inode • We implement file semantics on top of IBP using the external node (exNode) data ...
3Com® OfficeConnect® Internet Firewall
... Inspection technology to deny unauthorized access to the LAN and prevent Denial of Service (DoS) and hacker attacks, including Ping of Death, SYN Flood, LAND Attack, IP Spoofing, Teardrop, and Bonk. Hackers may try to use Java, ActiveX, and Cookie technologies to attack networks, so the Internet Fir ...
... Inspection technology to deny unauthorized access to the LAN and prevent Denial of Service (DoS) and hacker attacks, including Ping of Death, SYN Flood, LAND Attack, IP Spoofing, Teardrop, and Bonk. Hackers may try to use Java, ActiveX, and Cookie technologies to attack networks, so the Internet Fir ...
Topology generators
... join u to existing node v with probability d(v)/d(w) Connect degree 1 nodes using preferential connectivity ...
... join u to existing node v with probability d(v)/d(w) Connect degree 1 nodes using preferential connectivity ...
Internet_structure
... ‘IT law’ is broader than when computers are networked, but the most interesting issues arise because of the networking Why start with the architecture of the Internet? - Because it both limits and enables what law can achieve in regulating cyberspace ...
... ‘IT law’ is broader than when computers are networked, but the most interesting issues arise because of the networking Why start with the architecture of the Internet? - Because it both limits and enables what law can achieve in regulating cyberspace ...
presentation source
... Internet application in which two or more users in different locations can view and edit the same document on line at the same time. Changes show up automatically on each user’s computer screen as they are made. ...
... Internet application in which two or more users in different locations can view and edit the same document on line at the same time. Changes show up automatically on each user’s computer screen as they are made. ...
NAME: EBIENYIE SEMAEDIONG COLLEGE: ENGINEERING
... A wireless access point allows mobile users to connect to a central network node without using any wires. Wireless connectivity is useful for mobile workstations, since there is no wiring involved. The wireless access standards are broadly divided into 802.11a, 802.11b, and 802.11g. 802.11g is most ...
... A wireless access point allows mobile users to connect to a central network node without using any wires. Wireless connectivity is useful for mobile workstations, since there is no wiring involved. The wireless access standards are broadly divided into 802.11a, 802.11b, and 802.11g. 802.11g is most ...
SAVAH: Source address validation with Host Identity Protocol
... • During HIP base exchange a source HIT found in signaling packets (I1 and I2) is present in the list of allowed HITs • After base exchange completes a database of previously seen locators (IP addresses) does not contain a record with a source IP address of a registrar ...
... • During HIP base exchange a source HIT found in signaling packets (I1 and I2) is present in the list of allowed HITs • After base exchange completes a database of previously seen locators (IP addresses) does not contain a record with a source IP address of a registrar ...























