catalogs - Avara Technologies
... reliable, feature rich and cost effective integrated access devices (IAD) with multiple broadband 10/100Base-T and narrow band POTS, E1/T1/J1 & serial data (X.21, RS232) interfaces for use over single mode or multi mode optical fibre cables in point to point, linear or ring network topologies. ...
... reliable, feature rich and cost effective integrated access devices (IAD) with multiple broadband 10/100Base-T and narrow band POTS, E1/T1/J1 & serial data (X.21, RS232) interfaces for use over single mode or multi mode optical fibre cables in point to point, linear or ring network topologies. ...
rural access in Nepal
... Underdeveloped physical infrastructure Low-income levels/ poverty Low population density Low level of computer education Little public awareness about internet and use of computer Absence of local content / language barrier to transfer information, with Nepali font not yet standardized Inadequate hu ...
... Underdeveloped physical infrastructure Low-income levels/ poverty Low population density Low level of computer education Little public awareness about internet and use of computer Absence of local content / language barrier to transfer information, with Nepali font not yet standardized Inadequate hu ...
View Sample PDF - IRMA
... network model ensures stability, which is important for quick and reliable communication between nodes. By this build-up, the system remains useful over the unstable network. ...
... network model ensures stability, which is important for quick and reliable communication between nodes. By this build-up, the system remains useful over the unstable network. ...
IPv4/6 - RIT IST - Rochester Institute of Technology
... – Reservation set up protocols • Routing agents decide on the routes when such messages come by • Passed to Reservation set up agent • Communicates with the admission control • Who check if the call can be supported • If so – reservation agents makes bookings ...
... – Reservation set up protocols • Routing agents decide on the routes when such messages come by • Passed to Reservation set up agent • Communicates with the admission control • Who check if the call can be supported • If so – reservation agents makes bookings ...
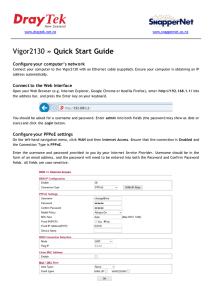
Vigor2130 » Quick Start Guide
... Configure your PPPoE settings On the left-hand navigation menu, click WAN and then Internet Access. Ensure that the connection is Enabled and the Connection Type is PPPoE. Enter the username and password provided to you by your Internet Service Provider. Username should be in the form of an email ad ...
... Configure your PPPoE settings On the left-hand navigation menu, click WAN and then Internet Access. Ensure that the connection is Enabled and the Connection Type is PPPoE. Enter the username and password provided to you by your Internet Service Provider. Username should be in the form of an email ad ...
UTP
... within buildings (local area networks), between sites (wide area networks), and to the Internet ...
... within buildings (local area networks), between sites (wide area networks), and to the Internet ...
pptx - Cornell Computer Science
... Intermediate project report due Mar 24. BOOM proposal due Mar 31. Spring break, week of April 2nd Intermediate project report 2 due April 12th. ...
... Intermediate project report due Mar 24. BOOM proposal due Mar 31. Spring break, week of April 2nd Intermediate project report 2 due April 12th. ...
01.1-Overview
... everything we currently use is a paragon of engineering, rather than a snapshot of our understanding at the time. We build great myths of spin about how what we have done is the only way to do it to the point that our universities now teach the flaws to students (and professors and textbook authors) ...
... everything we currently use is a paragon of engineering, rather than a snapshot of our understanding at the time. We build great myths of spin about how what we have done is the only way to do it to the point that our universities now teach the flaws to students (and professors and textbook authors) ...
Hardware Building Blocks and Encoding
... Real communication have some measure of noise. This theorem tells us the limits to a channel’s capacity (in bits per second) in the presence of noise. Shannon’s theorem uses the notion of signal-to-noise ratio (S/N), which is usually expressed in decibels (dB): ...
... Real communication have some measure of noise. This theorem tells us the limits to a channel’s capacity (in bits per second) in the presence of noise. Shannon’s theorem uses the notion of signal-to-noise ratio (S/N), which is usually expressed in decibels (dB): ...
Set 1 File
... - The Internet today is run by private companies, not the government. - The national Internet service providers are backbone networks created and maintained by specialized companies. - These backbone networks are connected by complex switching stations (normally run by a third party) called network ...
... - The Internet today is run by private companies, not the government. - The national Internet service providers are backbone networks created and maintained by specialized companies. - These backbone networks are connected by complex switching stations (normally run by a third party) called network ...
Part I: Introduction
... transport transport network link physical application transport network link physical ...
... transport transport network link physical application transport network link physical ...
Lecture 2
... transport transport network link physical application transport network link physical ...
... transport transport network link physical application transport network link physical ...
electronic-commerce-9th-edition-gary-schneider-test-bank
... 45. ____ lets users create and manipulate e-mail folders and individual e-mail messages while the messages are still on the e-mail server. ...
... 45. ____ lets users create and manipulate e-mail folders and individual e-mail messages while the messages are still on the e-mail server. ...
Commonly used techniques to “solve” reliability
... • The end effect at the terminal is also heavily dependent upon issues such as compression algorithms, coding schemes, the presence of protocols for security, data recovery, re-transmission, etc., and the ability of applications to adapt to network congestion. • However, network providers need perfo ...
... • The end effect at the terminal is also heavily dependent upon issues such as compression algorithms, coding schemes, the presence of protocols for security, data recovery, re-transmission, etc., and the ability of applications to adapt to network congestion. • However, network providers need perfo ...
0-ISP-Network-Design
... • A peer is another autonomous system with which the local network has agreed to exchange locally sourced routes and traffic • Private peer – Private link between two providers for the purpose of interconnecting ...
... • A peer is another autonomous system with which the local network has agreed to exchange locally sourced routes and traffic • Private peer – Private link between two providers for the purpose of interconnecting ...
223.1.1.4
... Datagram from A to E: • look up network address of E •E on different network •A, E not directly attached •routing table: next hop router to E is 223.1.1.4 •link layer sends datagram to router 223.1.1.4 inside link-layer ...
... Datagram from A to E: • look up network address of E •E on different network •A, E not directly attached •routing table: next hop router to E is 223.1.1.4 •link layer sends datagram to router 223.1.1.4 inside link-layer ...
network-performance
... The smallest value that is larger than 95% of the values in a given sample This means that 95% of the time the channel utilization is equal to or less than this value ...
... The smallest value that is larger than 95% of the values in a given sample This means that 95% of the time the channel utilization is equal to or less than this value ...
Data Transmission Review
... 9. With data masses divided into ______________, individual transmissions occur more frequently so that every computer on the network has more opportunities to transmit and receive data. 10. Packets may contain session-control codes, such as error correction, that indicate the need for a ___________ ...
... 9. With data masses divided into ______________, individual transmissions occur more frequently so that every computer on the network has more opportunities to transmit and receive data. 10. Packets may contain session-control codes, such as error correction, that indicate the need for a ___________ ...
The Internet - Putra Selaparang
... In 1982 the word internet started. 1986: First “freenet” created in Case Western Reserve University 1991: US government allowed business agencies to connect to internet. ...
... In 1982 the word internet started. 1986: First “freenet” created in Case Western Reserve University 1991: US government allowed business agencies to connect to internet. ...