A performance analysis modeling of a QoS
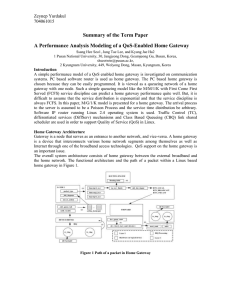
... chosen because they can be easily programmed. It is viewed as a queueing network of a home gateway with one node. Such a simple queueing model like the M/M/1/K with First Come First Served (FCFS) service discipline can predict a home gateway performance quite well. But, it is difficult to assume tha ...
... chosen because they can be easily programmed. It is viewed as a queueing network of a home gateway with one node. Such a simple queueing model like the M/M/1/K with First Come First Served (FCFS) service discipline can predict a home gateway performance quite well. But, it is difficult to assume tha ...
Social Order and Network Security. Exploratory Research on TOR
... As Internet becomes to grow outside of its physical carriers, it gains more influence over various subsystems constituting the social system in general. This manifestation is especially visible in the economical plane, in which a certain symbiotic relationship between the world wide network and othe ...
... As Internet becomes to grow outside of its physical carriers, it gains more influence over various subsystems constituting the social system in general. This manifestation is especially visible in the economical plane, in which a certain symbiotic relationship between the world wide network and othe ...
09/24/04
... operating system (provides high-level functions, e.g. file sharing services) • The operating system services make use of the network system (provides basic connectivity tools – ensuring that the nodes are communicating) • The network system works through the physical transport layer (the hardware an ...
... operating system (provides high-level functions, e.g. file sharing services) • The operating system services make use of the network system (provides basic connectivity tools – ensuring that the nodes are communicating) • The network system works through the physical transport layer (the hardware an ...
ppt
... If normally no more than m scans for a port, send m times probes rather than one and divide the reports by m and round down to the nearest integer. ...
... If normally no more than m scans for a port, send m times probes rather than one and divide the reports by m and round down to the nearest integer. ...
1. Communication Network
... – Different connections can be allocated different amounts of resources (bandwidth and buffers) – User and network negotiate contract that specifies user traffic characteristics and network guaranteed QoS – Accomodates both real-time and nonreal-time traffic ...
... – Different connections can be allocated different amounts of resources (bandwidth and buffers) – User and network negotiate contract that specifies user traffic characteristics and network guaranteed QoS – Accomodates both real-time and nonreal-time traffic ...
Slide 1
... A very thin glass core, made of silica with high purity is surrounded by a layer (also silica) with refractive index lower cladding call, which causes the light transmitted by the fiber core is reflected the inner walls of the cable. ...
... A very thin glass core, made of silica with high purity is surrounded by a layer (also silica) with refractive index lower cladding call, which causes the light transmitted by the fiber core is reflected the inner walls of the cable. ...
Chapter 1 Introduction
... – Software (NCP) Network Control Protocol provided communication between the hosts. 1972, Vint Cerf and Bob Kahn invented (TCP) Transmission Control Protocol ...
... – Software (NCP) Network Control Protocol provided communication between the hosts. 1972, Vint Cerf and Bob Kahn invented (TCP) Transmission Control Protocol ...
VINE - UiO
... ”QoS is the measure of how good a service is, as presented to the user. It is expressed in user understandable language and manifests itself in a number of parameters, all of which have either subjective or objective values.” ...
... ”QoS is the measure of how good a service is, as presented to the user. It is expressed in user understandable language and manifests itself in a number of parameters, all of which have either subjective or objective values.” ...
Discovery service
... The Internet support a scheme for the use of symbolic names for hosts and networks. The named entities are organized into a hierarchy. The named entities are called domains and the symbolic names are called domain names. Domains are organized into a hierarchy that intends to reflect organiza ...
... The Internet support a scheme for the use of symbolic names for hosts and networks. The named entities are organized into a hierarchy. The named entities are called domains and the symbolic names are called domain names. Domains are organized into a hierarchy that intends to reflect organiza ...
How to setup the router for Static IP internet connection mode
... How to setup the router for Static IP internet connection mode Product line: Wireless Model number:FH330 There are three internet connection modes for the router. This article will guide you how to setup the router for Static IPmode and the steps as below. Note: If you have no idea about what is the ...
... How to setup the router for Static IP internet connection mode Product line: Wireless Model number:FH330 There are three internet connection modes for the router. This article will guide you how to setup the router for Static IPmode and the steps as below. Note: If you have no idea about what is the ...
How to setup the router for Static IP internet connection mode
... How to setup the router for Static IP internet connection mode Product line: Wireless Model number: NH326 There are three internet connection modes for the router. This article will guide you how to setup the router for Static IPmode and the steps as below. Note: If you have no idea about what is th ...
... How to setup the router for Static IP internet connection mode Product line: Wireless Model number: NH326 There are three internet connection modes for the router. This article will guide you how to setup the router for Static IPmode and the steps as below. Note: If you have no idea about what is th ...
Title
... Internet Technology … somehow stuck … Internet Protocol (IP) forms the basis of current communication networks… ...
... Internet Technology … somehow stuck … Internet Protocol (IP) forms the basis of current communication networks… ...
MPLS: Power and Complexity
... Requires VRF (Virtual Routing Forwarding) to work Creates more than 5 routing/switching tables Specialised knowledge to design, implement and troubleshoot Advantages/Power Minimal migration disruption if well-planned Does not require changes on the existing routing protocols/IP address allocati ...
... Requires VRF (Virtual Routing Forwarding) to work Creates more than 5 routing/switching tables Specialised knowledge to design, implement and troubleshoot Advantages/Power Minimal migration disruption if well-planned Does not require changes on the existing routing protocols/IP address allocati ...
Internet services
... Worldwide Interoperability for Microwave Access) – radio waves are transmit from POP transmission device to userend receiving device (i.e. the antenna system) – ADSL (Asymmetric Digital Subscriber Line) – transmission media is an existing telephone line that is shared by voice signal and data signal ...
... Worldwide Interoperability for Microwave Access) – radio waves are transmit from POP transmission device to userend receiving device (i.e. the antenna system) – ADSL (Asymmetric Digital Subscriber Line) – transmission media is an existing telephone line that is shared by voice signal and data signal ...
IRIS Project
... Error Handling • Detection: • Use error detection codes, which add some redundancy to allow detecting errors ...
... Error Handling • Detection: • Use error detection codes, which add some redundancy to allow detecting errors ...
Chapter 7
... – NSP equipment and links are tied together by network access points (NAPs) • NAPS supply Internet connections to Internet service providers such as EarthLink, AOL, and Comcast ...
... – NSP equipment and links are tied together by network access points (NAPs) • NAPS supply Internet connections to Internet service providers such as EarthLink, AOL, and Comcast ...
1-up PPT
... Error Handling • Detection: • Use error detection codes, which add some redundancy to allow detecting errors ...
... Error Handling • Detection: • Use error detection codes, which add some redundancy to allow detecting errors ...
Aalborg Universitet Bujlow, Tomasz; Riaz, Tahir; Pedersen, Jens Myrup
... and increasing growth of the global Internet and the network technology in general. Broadband and mobile broadband performance today is mainly measured and monitored only by speed. However there are several other parameters, which are important for critical business and real-time applications, like ...
... and increasing growth of the global Internet and the network technology in general. Broadband and mobile broadband performance today is mainly measured and monitored only by speed. However there are several other parameters, which are important for critical business and real-time applications, like ...
chapter2ccna
... BYTE: A byte is 7 or 8 bits, depending on whether parity is used. For the rest of this chapter, always assume a byte is 8 bits. OCTET: An octet, made up of 8 bits, is just an ordinary 8-bit binary number. In this chapter, the terms byte and octet are completely interchangeable. Network address: This ...
... BYTE: A byte is 7 or 8 bits, depending on whether parity is used. For the rest of this chapter, always assume a byte is 8 bits. OCTET: An octet, made up of 8 bits, is just an ordinary 8-bit binary number. In this chapter, the terms byte and octet are completely interchangeable. Network address: This ...
01101014
... on the web servers to make these available on the Internet. Couple of these included ‘cyclone warning’ and ‘disaster information’, cricket match, a wide variety of business information, local educational programmes, entertainment and many more. In the early nineties, Bangladesh had access to email v ...
... on the web servers to make these available on the Internet. Couple of these included ‘cyclone warning’ and ‘disaster information’, cricket match, a wide variety of business information, local educational programmes, entertainment and many more. In the early nineties, Bangladesh had access to email v ...
Network Compatible Devices
... Kindle/Nook: Early versions of these devices and the “reader only” versions are not compatible with our email or wireless network. Later versions of the Nook and the Kindle Fire 2nd generation and later are able to access our internet services through wireless, and email services may be configured o ...
... Kindle/Nook: Early versions of these devices and the “reader only” versions are not compatible with our email or wireless network. Later versions of the Nook and the Kindle Fire 2nd generation and later are able to access our internet services through wireless, and email services may be configured o ...
Part I: Introduction
... be the total cost of the net? Question: Would it be less expensive to use a multiple-access network? What are the drawbacks and limitations? ...
... be the total cost of the net? Question: Would it be less expensive to use a multiple-access network? What are the drawbacks and limitations? ...























