SOLENT FORUM NATURE CONSERVATION
... With regards to existing data and gaps, data was collated that was useful and relevant for the scoping study but it did not collect or note all existing ecological data. It was assumed that the biodiversity record centres hold most local ecological data. Therefore, if ecological monitoring was incor ...
... With regards to existing data and gaps, data was collated that was useful and relevant for the scoping study but it did not collect or note all existing ecological data. It was assumed that the biodiversity record centres hold most local ecological data. Therefore, if ecological monitoring was incor ...
1.1 notes
... 1.1 An Overview of Statistics Definitions: Statistics is the science of collecting, organizing, analyzing, and interpreting data in order to make decisions. Data consist of information coming from observations, counts, measurements, or responses. A population is the collection of ALL outcomes, respo ...
... 1.1 An Overview of Statistics Definitions: Statistics is the science of collecting, organizing, analyzing, and interpreting data in order to make decisions. Data consist of information coming from observations, counts, measurements, or responses. A population is the collection of ALL outcomes, respo ...
Verbal Attestation of Standard form SF
... Intending TO be legally bound, I hereby accept the obligations contained in this Agreement in consideration of my being granted access to classified information. AS used in this Agreement, classified information is marked or unmarked classified information, including oral communications, that is cla ...
... Intending TO be legally bound, I hereby accept the obligations contained in this Agreement in consideration of my being granted access to classified information. AS used in this Agreement, classified information is marked or unmarked classified information, including oral communications, that is cla ...
INFORMATION PROCESSING FOR A STORE - AN OVERVIEW
... initiating reorder and the optimal quantity to be reordered. Operational data collected over a period of time is called data archives and the process of collecting it is called data archiving. With the availability of massive disks in which terabytes (1012 bytes) of data can be stored, it has become ...
... initiating reorder and the optimal quantity to be reordered. Operational data collected over a period of time is called data archives and the process of collecting it is called data archiving. With the availability of massive disks in which terabytes (1012 bytes) of data can be stored, it has become ...
Database Introduction - YSU Computer Science & Information Systems
... • Provide a correct up-to-date understanding of and appreciation for the most practical aspects of crucial database issues. • Clarify concepts, principles, and techniques that trouble vendors and users • Specific suggestions on how to deal with ...
... • Provide a correct up-to-date understanding of and appreciation for the most practical aspects of crucial database issues. • Clarify concepts, principles, and techniques that trouble vendors and users • Specific suggestions on how to deal with ...
CPS 216: Advanced Database Systems
... – Homework Assignments 15% – Project 25% – Midterm 25% – Final 35% ...
... – Homework Assignments 15% – Project 25% – Midterm 25% – Final 35% ...
DiscoveryLink ?for data integration
... without additional development of complex applications. The communication between DiscoveryLink and a specific data source is handled by a software "wrapper." And now, IBM has added new wrappers, wrapper toolkit APIs, enhanced performance and new functionality to this proven data integration solutio ...
... without additional development of complex applications. The communication between DiscoveryLink and a specific data source is handled by a software "wrapper." And now, IBM has added new wrappers, wrapper toolkit APIs, enhanced performance and new functionality to this proven data integration solutio ...
PPTX 5.8 MB - Jeffery S. Horsburgh
... manage the behavior of water and its nutrients, contaminants, and sediments everywhere in the United States ...
... manage the behavior of water and its nutrients, contaminants, and sediments everywhere in the United States ...
MultiLoggerDB Software
... The Database Console allows you to manage your project, you will not need to have detailed knowledge of ...
... The Database Console allows you to manage your project, you will not need to have detailed knowledge of ...
View Presentation - InfoSec Nashville
... in the package (e.g. credit cards, driver’s license, insurance cards, etc.)—ranging between $1200 – $1300 per Kitz. Add $100 – $500 for rush orders and other miscellaneous fees like wire transfer, escrow, etc. ...
... in the package (e.g. credit cards, driver’s license, insurance cards, etc.)—ranging between $1200 – $1300 per Kitz. Add $100 – $500 for rush orders and other miscellaneous fees like wire transfer, escrow, etc. ...
Cisco Discovery 1 Module 08 Quiz Picture Descriptions
... Basic Security 1. Drag the network threat on the left to the definition on the right. Left Destroying data on a hard drive. Changing data for personal gain. Overloading a server to reduce its performance. Stealing data on a hard drive to gain a competitive advantage. Stealing information t ...
... Basic Security 1. Drag the network threat on the left to the definition on the right. Left Destroying data on a hard drive. Changing data for personal gain. Overloading a server to reduce its performance. Stealing data on a hard drive to gain a competitive advantage. Stealing information t ...
the art of parallel heterogeneous data transformation
... Gives a nonstop availability and access to the real time data. Translational data between operational and analytical systems. OGG will filter, route, verify and deliver transactional data in real-time across Oracle and heterogeneous environments. ...
... Gives a nonstop availability and access to the real time data. Translational data between operational and analytical systems. OGG will filter, route, verify and deliver transactional data in real-time across Oracle and heterogeneous environments. ...
Course Code: CSC 422 - The Federal University of Agriculture
... are many kinds of data with only a very few occurrence of each kinds. Clearly, such data bases have the peculiarity that the size of the data is almost as large as the definition of the data. ...
... are many kinds of data with only a very few occurrence of each kinds. Clearly, such data bases have the peculiarity that the size of the data is almost as large as the definition of the data. ...
NoDB: Querying Raw Data
... relevant for the task, the entire data must first be loaded inside the database. For large amounts of data, this means a few hours of delay. ▪ NoDB Philosophy: To make database systems more accessible to the user by eliminating major bottlenecks of current state-of-the-art technology that increases ...
... relevant for the task, the entire data must first be loaded inside the database. For large amounts of data, this means a few hours of delay. ▪ NoDB Philosophy: To make database systems more accessible to the user by eliminating major bottlenecks of current state-of-the-art technology that increases ...
Data Publishing TDWG Annual Meeting New Orleans
... Biodiversity data highly diverse and heterogeneous In most cases published as separate data files with poor metadata descriptions Well established standards exist for only some types of biodiversity data : DarwinCore, Nexus, GenBank, Barcode of Life Majority of published data not easily discoverable ...
... Biodiversity data highly diverse and heterogeneous In most cases published as separate data files with poor metadata descriptions Well established standards exist for only some types of biodiversity data : DarwinCore, Nexus, GenBank, Barcode of Life Majority of published data not easily discoverable ...
32nd Conference on Environmental Information Processing
... 32nd Conference on Environmental Information Processing Technologies (EIPT) The conference, chaired by Scott Jacobs, NWS and Nazila Merati was held in New Orleans, Louisiana from January 10-14 2016. EIPT convened 18 sessions covering a variety of topics ranging from crowdsourcing weather observation ...
... 32nd Conference on Environmental Information Processing Technologies (EIPT) The conference, chaired by Scott Jacobs, NWS and Nazila Merati was held in New Orleans, Louisiana from January 10-14 2016. EIPT convened 18 sessions covering a variety of topics ranging from crowdsourcing weather observation ...
SEEGridISRoadmapEnterpriseViewpoint
... Agency B also uses software X; Agency B uses the same data model as Agency A, and; These two dependencies will always remain ...
... Agency B also uses software X; Agency B uses the same data model as Agency A, and; These two dependencies will always remain ...
Week1-DatabaseIntroduction - Cardiff Biodiversity Informatics
... • a program may be required to help enter data • a program may be required to help retrieve data • integrity checking can be performed (Week 4) • can be multi-user • can be available on the Web ...
... • a program may be required to help enter data • a program may be required to help retrieve data • integrity checking can be performed (Week 4) • can be multi-user • can be available on the Web ...
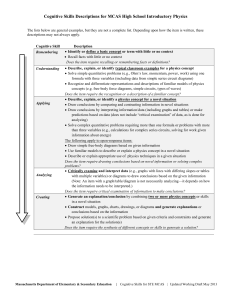
Cognitive Skills Descriptions for MCAS High School Introductory
... Draw conclusions by comparing and contrasting information in novel situations Draw conclusions by interpreting information/data (including graphs and tables) or make predictions based on data (does not include “critical examination” of data, as is done for analyzing) Solve complex quantitative ...
... Draw conclusions by comparing and contrasting information in novel situations Draw conclusions by interpreting information/data (including graphs and tables) or make predictions based on data (does not include “critical examination” of data, as is done for analyzing) Solve complex quantitative ...
A ransomware attack puts IT in a battle against the malware
... consuming recovery is copying back thousands of files one at a time. Prevention is, of course, always the first step in Ransomware protection. Organizations need to do what they can to make sure that its servers are up to date, eliminate the use of older protocols like SMB 1.0 and ensuring that user ...
... consuming recovery is copying back thousands of files one at a time. Prevention is, of course, always the first step in Ransomware protection. Organizations need to do what they can to make sure that its servers are up to date, eliminate the use of older protocols like SMB 1.0 and ensuring that user ...
LECTURE NOTES #1
... Data Resources: Data constitutes a valuable organizational resource. Thus, data resources must be managed effectively to benefit all end users in an organization. The data resources of information systems are typically organized into: Databases - a collection of logically related records or files. ...
... Data Resources: Data constitutes a valuable organizational resource. Thus, data resources must be managed effectively to benefit all end users in an organization. The data resources of information systems are typically organized into: Databases - a collection of logically related records or files. ...