Artificial intelligence could be not be useful in
... - Predict which customers will buy new policies; - Spot and understand new business trends in claims; - Detect customers, belonging to frequent buying patterns. ...
... - Predict which customers will buy new policies; - Spot and understand new business trends in claims; - Detect customers, belonging to frequent buying patterns. ...
security_6
... Other Security and Privacy Concerns in EC Some of the methods used in market research and for tracking customers: ...
... Other Security and Privacy Concerns in EC Some of the methods used in market research and for tracking customers: ...
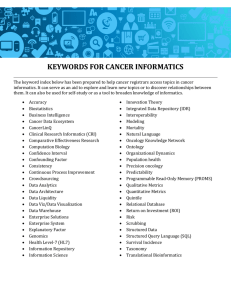
KEYWORDS FOR CANCER INFORMATICS
... The keyword index below has been prepared to help cancer registrars access topics in cancer informatics. It can serve as an aid to explore and learn new topics or to discover relationships between them. It can also be used for self-study or as a tool to broaden knowledge of informatics. ...
... The keyword index below has been prepared to help cancer registrars access topics in cancer informatics. It can serve as an aid to explore and learn new topics or to discover relationships between them. It can also be used for self-study or as a tool to broaden knowledge of informatics. ...
Computer Science 9616a, Fall 2011 Project Description Your project
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. If you do an implementation project, you may work in pairs. Bo ...
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. If you do an implementation project, you may work in pairs. Bo ...
Computer Science 9616b, Fall 2016 Project Description Your project
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. Both the research only and practical project require a written ...
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. Both the research only and practical project require a written ...
SEM 1 Unit 2 Vocabulary List
... Heats – preliminary and then final rounds of competition, such as a swim meet Tournament play – players or teams are seeded based on ranking-normally single elimination Ladder – individual contests ranked on a ladder and can move up or down based on results Match play – in golf, you either win, lose ...
... Heats – preliminary and then final rounds of competition, such as a swim meet Tournament play – players or teams are seeded based on ranking-normally single elimination Ladder – individual contests ranked on a ladder and can move up or down based on results Match play – in golf, you either win, lose ...
International and judicial legal studies commission.
... The Data Protection Act 2004 was proclaimed in its entirety on the 16th of February 2009. In addition, The Data Protection Act 2004 gives individuals rights to protect them against data protection breaches, and creates obligations for those keeping personal information. Under the Act, individuals ha ...
... The Data Protection Act 2004 was proclaimed in its entirety on the 16th of February 2009. In addition, The Data Protection Act 2004 gives individuals rights to protect them against data protection breaches, and creates obligations for those keeping personal information. Under the Act, individuals ha ...
Make PDF
... http://mswia.gov.pl/en/amnesty-for-foreigners/722,When-a-residence-permit-will-be-refused-to-be-granted-under-theamnesty-Act.html ...
... http://mswia.gov.pl/en/amnesty-for-foreigners/722,When-a-residence-permit-will-be-refused-to-be-granted-under-theamnesty-Act.html ...
Safety (MSDS) data for acid blue 9
... Stable. Incompatible with strong oxidizing agents. Toxicology May act as a skin, respiratory or eye irritant. Toxicity data (The meaning of any toxicological abbreviations which appear in this section is given here.) SCN-MUS LD50 4600 mg kg-1 Transport information Non-hazardous for air, sea and road ...
... Stable. Incompatible with strong oxidizing agents. Toxicology May act as a skin, respiratory or eye irritant. Toxicity data (The meaning of any toxicological abbreviations which appear in this section is given here.) SCN-MUS LD50 4600 mg kg-1 Transport information Non-hazardous for air, sea and road ...
Research Funding Analysis and Reporting Using SAS/EIS Frame Software
... analysis of research grant applications. It provides our users with quick access to the data to determine what research is being done in various areas (e.g., organ sites) and how much money has been awarded. Also included in the system are comprehensive browse windows for management to view both the ...
... analysis of research grant applications. It provides our users with quick access to the data to determine what research is being done in various areas (e.g., organ sites) and how much money has been awarded. Also included in the system are comprehensive browse windows for management to view both the ...
The Future of Data Mining * Predictive Analytics
... • The method of data warehousing is structured query language (SQL) and its various ...
... • The method of data warehousing is structured query language (SQL) and its various ...
Format to exercise the ARCO Rights RESPUESTAS ÓPTIMAS EN
... NOTE: According with Article 32 of the Federal Law on the protection of personal data held by private individuals (Ley Federal de Protección de Datos Personales en Posesión de los Particulares) we will to proceed to your request and we shall informed the status of your request in a 20-day maximum pe ...
... NOTE: According with Article 32 of the Federal Law on the protection of personal data held by private individuals (Ley Federal de Protección de Datos Personales en Posesión de los Particulares) we will to proceed to your request and we shall informed the status of your request in a 20-day maximum pe ...
What Data Mining Isn't
... Well-publicized examples of successful business applications of data mining compete on the front pages with examples of omnipresent personal data being used for bad purposes. To some people, the phrase "data mining" conjures up thoughts of building valuable predictive models or learning more about c ...
... Well-publicized examples of successful business applications of data mining compete on the front pages with examples of omnipresent personal data being used for bad purposes. To some people, the phrase "data mining" conjures up thoughts of building valuable predictive models or learning more about c ...
ms. jyoti rathee (cse)
... We live in the information-age—accumulating data is easy and storing it inexpensive. In 1990s it was alleged that the amount of stored information doubles every twenty months. Unfortunately, as the amount of machine readable information increases, the ability to understand and make use of it does no ...
... We live in the information-age—accumulating data is easy and storing it inexpensive. In 1990s it was alleged that the amount of stored information doubles every twenty months. Unfortunately, as the amount of machine readable information increases, the ability to understand and make use of it does no ...
Common Core`s Dirty Little Secret - Stop Common Core in New York
... FERPA (Family Education Rights and Privacy Act) “The right to provide written consent before the school discloses personally identifiable information (PII) from the student's education records, except to the extent that FERPA authorizes disclosure without consent.” (Appendix B, page 75654, section ...
... FERPA (Family Education Rights and Privacy Act) “The right to provide written consent before the school discloses personally identifiable information (PII) from the student's education records, except to the extent that FERPA authorizes disclosure without consent.” (Appendix B, page 75654, section ...
Data Mining
... should any information reach unintended parties but what happens if there is a Data Breach? A cyber hacker who manages to successfully hack into a data brokerage firm, could potentially have personal data on hundreds of millions of people. With Congress struggling to pass any meaningful cybersecurit ...
... should any information reach unintended parties but what happens if there is a Data Breach? A cyber hacker who manages to successfully hack into a data brokerage firm, could potentially have personal data on hundreds of millions of people. With Congress struggling to pass any meaningful cybersecurit ...
Web tracking resolution
... Web tracking allows organisations to monitor almost every single aspect of user behaviour on the Web. The type of information that can be collected through tracking (e.g., IP addresses, device identi?iers, etc.) can lead to the identi?ication of a particular ...
... Web tracking allows organisations to monitor almost every single aspect of user behaviour on the Web. The type of information that can be collected through tracking (e.g., IP addresses, device identi?iers, etc.) can lead to the identi?ication of a particular ...
USA PATRIOT Act - Landings Credit Union
... In order to prevent the use of the U.S. banking system in terrorist and other illegal activity, federal regulations require all financial institutions to obtain, verify, and record identification from all persons opening new accounts or being added as signatories to existing accounts. Effective Octo ...
... In order to prevent the use of the U.S. banking system in terrorist and other illegal activity, federal regulations require all financial institutions to obtain, verify, and record identification from all persons opening new accounts or being added as signatories to existing accounts. Effective Octo ...
Data protection form - Food Standards Agency
... consultation owner directly. Their contact details can be found in the consultation pack. Privacy Statement The Food Standards Agency complies with UK Privacy Laws, including the Data Protection Act 1998 and is registered as a data controller with the Information Commissioner (Reg nbr Z477519). Any ...
... consultation owner directly. Their contact details can be found in the consultation pack. Privacy Statement The Food Standards Agency complies with UK Privacy Laws, including the Data Protection Act 1998 and is registered as a data controller with the Information Commissioner (Reg nbr Z477519). Any ...