CSP Confidentiality Pledge
... Cancer Surveillance Program (CSP) and of assuring the right to privacy of persons whose records I receive. I understand that, under California law, all individual level data are considered confidential regardless of whether the individual, hospital(s) or physician(s) is named or otherwise identifiab ...
... Cancer Surveillance Program (CSP) and of assuring the right to privacy of persons whose records I receive. I understand that, under California law, all individual level data are considered confidential regardless of whether the individual, hospital(s) or physician(s) is named or otherwise identifiab ...
Databases @ UMass
... events that need to be filtered, correlated, aggregated, and transformed for use of end applications. We address issues involved in such stream-based event processing ranging from the query language, to fast implementations, and to data quality. ...
... events that need to be filtered, correlated, aggregated, and transformed for use of end applications. We address issues involved in such stream-based event processing ranging from the query language, to fast implementations, and to data quality. ...
Mercury Business, WP3 - Invenco Highlight-1
... Workstations, Tablets and Smart phones (iPhone, Android, Windows) All browsers (IE, Chrome, Firefox, Safari) No Need for expensive BI, ETL, Planning tool licenses – only database license is needed Ready made product platform – Implementation from few hours to week Cross functional competence from di ...
... Workstations, Tablets and Smart phones (iPhone, Android, Windows) All browsers (IE, Chrome, Firefox, Safari) No Need for expensive BI, ETL, Planning tool licenses – only database license is needed Ready made product platform – Implementation from few hours to week Cross functional competence from di ...
Real Systems - e
... society. The main customers of the company are central public institutions, large private companies and law enforcement organizations. Company’s portfolio includes e-government solutions, criminal analyses & investigation products, law enforcement systems, forensics and cyber security software. eGov ...
... society. The main customers of the company are central public institutions, large private companies and law enforcement organizations. Company’s portfolio includes e-government solutions, criminal analyses & investigation products, law enforcement systems, forensics and cyber security software. eGov ...
Abstract - LetsDoProject
... is that tremendous economic growth and improvement in quality of life can be effected by harnessing the potential benefits of analyzing this large volume of data. As a result, the problem of extracting the most informative, yet low-dimensional structure from high-dimensional datasets is of paramount ...
... is that tremendous economic growth and improvement in quality of life can be effected by harnessing the potential benefits of analyzing this large volume of data. As a result, the problem of extracting the most informative, yet low-dimensional structure from high-dimensional datasets is of paramount ...
zahidullah_conf_12
... CRM, ERP, Data Mining, Apriori. Over the last decade, the number of customer is growing; numerous organizations face the problem of integrating and processing the data. Enterprise Resource Planning (ERP) is a way to integrate the data and processes of an organization into one single system. Differen ...
... CRM, ERP, Data Mining, Apriori. Over the last decade, the number of customer is growing; numerous organizations face the problem of integrating and processing the data. Enterprise Resource Planning (ERP) is a way to integrate the data and processes of an organization into one single system. Differen ...
Customer Case Study: Turning Information into Intelligence: Clinical Data Navigation and Integration
... With the routine demand to present the efficacy evidence and safety profile when conducting clinical trials, J&JPRD has established global standards, which start with raw data, navigate into analysis data for reporting, and end in the integrated data repository. In this presentation, we demonstrate ...
... With the routine demand to present the efficacy evidence and safety profile when conducting clinical trials, J&JPRD has established global standards, which start with raw data, navigate into analysis data for reporting, and end in the integrated data repository. In this presentation, we demonstrate ...
information systems for decision making
... • A computer network that links employees and other authorized users. • Firewalls ...
... • A computer network that links employees and other authorized users. • Firewalls ...
format
... Be sure to download the address file and the formset and instructions for the year and data set (Hospital or FOSC) that you are downloading. Note for Hospital data: The delimited text files of the complete sets of Hospital data (all data for all hospitals in a year) are too large to be read by Excel ...
... Be sure to download the address file and the formset and instructions for the year and data set (Hospital or FOSC) that you are downloading. Note for Hospital data: The delimited text files of the complete sets of Hospital data (all data for all hospitals in a year) are too large to be read by Excel ...
Does your Board know about GDPR?
... The regulation has not been finalised yet, but the belief is that this should happen early 2016. When it is in place companies will have 2 years’ grace to put the technologies required in ...
... The regulation has not been finalised yet, but the belief is that this should happen early 2016. When it is in place companies will have 2 years’ grace to put the technologies required in ...
Ways in which Information can be misused
... Propaganda Propaganda is the dissemination of information aimed at influencing the opinions or behaviors of people. As opposed to impartially providing information, propaganda in its most basic sense, often presents information primarily in order to influence its audience. ...
... Propaganda Propaganda is the dissemination of information aimed at influencing the opinions or behaviors of people. As opposed to impartially providing information, propaganda in its most basic sense, often presents information primarily in order to influence its audience. ...
A spate of statistical tests to climate data validation
... changes are still not well understood and many projects try to assess these forcings. Once relationships have been established, the use of climate projections model data allows to study the effect on biodiversity. The data portal PCMDI http://cmip-‐‑pcm ...
... changes are still not well understood and many projects try to assess these forcings. Once relationships have been established, the use of climate projections model data allows to study the effect on biodiversity. The data portal PCMDI http://cmip-‐‑pcm ...
DBMS Lab Projects - Indian Institute of Technology Kharagpur
... Map Based Interface Travel Information ...
... Map Based Interface Travel Information ...
Semi-guided Self Learning Data Structuring System
... Combining these methods of fixed starting rules, incremental but incomplete user guidance, fuzzy logic, evolution strategies, and outlier handling is expected to demonstrate superior self learning data extraction capabilities. Research method The research will be employed with a real life dynamic an ...
... Combining these methods of fixed starting rules, incremental but incomplete user guidance, fuzzy logic, evolution strategies, and outlier handling is expected to demonstrate superior self learning data extraction capabilities. Research method The research will be employed with a real life dynamic an ...
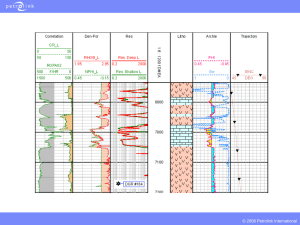
PPT - Energistics
... and Version 1.3.1. It strictly follows the WITSML specification, including the publish/subscribe method dropped by other contractors, special handling, and full support for all objects. ...
... and Version 1.3.1. It strictly follows the WITSML specification, including the publish/subscribe method dropped by other contractors, special handling, and full support for all objects. ...
Accuracy-Constrained Privacy-Preserving Access Control
... Access Control Mechanism for Relational Data Abstract: Access control mechanisms protect sensitive information from unauthorized users. However, when sensitive information is shared and a Privacy Protection Mechanism (PPM) is not in place, an authorized user can still compromise the privacy of a per ...
... Access Control Mechanism for Relational Data Abstract: Access control mechanisms protect sensitive information from unauthorized users. However, when sensitive information is shared and a Privacy Protection Mechanism (PPM) is not in place, an authorized user can still compromise the privacy of a per ...
Document
... into performing actions or divulging confidential information. While it is similar to a confidence trick or simple fraud, it is typically trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the vic ...
... into performing actions or divulging confidential information. While it is similar to a confidence trick or simple fraud, it is typically trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the vic ...
Information Delivery with SAS at Toyota
... Information Delivery with SAS at Toyota Michael Eksteen & Dave Bullock Systems Automation & Management (Pty) Ltd ...
... Information Delivery with SAS at Toyota Michael Eksteen & Dave Bullock Systems Automation & Management (Pty) Ltd ...
Database Management Systems
... each other’s databases and update information accordingly. Also included will be the fact that data will be locked by one user at a time in order to preserve data integrity. Identify the DBM Application(s): ...
... each other’s databases and update information accordingly. Also included will be the fact that data will be locked by one user at a time in order to preserve data integrity. Identify the DBM Application(s): ...
Acquire foundational knowledge of marketing
... Acquire foundational knowledge of marketing information management to understand its nature & scope ...
... Acquire foundational knowledge of marketing information management to understand its nature & scope ...
Industry Landscape: Picture Archiving and Communications
... This presentation discusses several issues and dynamics that are shaping the current generation of enterprise image and data management strategies that are aimed at consolidating medical data management from front to back. A discussion of the major competitors, technology offerings, and implementati ...
... This presentation discusses several issues and dynamics that are shaping the current generation of enterprise image and data management strategies that are aimed at consolidating medical data management from front to back. A discussion of the major competitors, technology offerings, and implementati ...
Data Classification Policy
... Security Numbers (SSNs), Information involving National Security. Student data that is not designated directory information; other personally identifiable information (PII) such as name, birthdate, address, employee ID, etc. when held in combination in a way that could lead to identity theft or othe ...
... Security Numbers (SSNs), Information involving National Security. Student data that is not designated directory information; other personally identifiable information (PII) such as name, birthdate, address, employee ID, etc. when held in combination in a way that could lead to identity theft or othe ...