Industrial Ethernet Switches
... message frames can be in transit at the same time. The performance gain is due to the simultaneity of several message frames. The switching technology offers definite advantages over shared LAN • Switches can be used to construct subnets and network segments • Data throughput and network performance ...
... message frames can be in transit at the same time. The performance gain is due to the simultaneity of several message frames. The switching technology offers definite advantages over shared LAN • Switches can be used to construct subnets and network segments • Data throughput and network performance ...
Impact of IPsec and 6to4 on VoIP Quality over IPv6
... authentication option [2] and do not consider AH since it seems to be rarely used in practice. Most corporate networks will also continue to employ NAT for their remaining IPv4 subnets. NAT and 6to4 are not directly compatible unless NAT and 6to4 are colocated in the same box (gateway). While Teredo ...
... authentication option [2] and do not consider AH since it seems to be rarely used in practice. Most corporate networks will also continue to employ NAT for their remaining IPv4 subnets. NAT and 6to4 are not directly compatible unless NAT and 6to4 are colocated in the same box (gateway). While Teredo ...
SwitchBlade® x908 [Rev ZJ]
... High availability features such as VCStack™ (Virtual Chassis Stacking) and EPSRing™ (Ethernet Protection Switched Rings) ensure traffic flow continues even during unscheduled outages. VCStack provides excellent resiliency by creating a single “virtual chassis” from two SwitchBlade x908 physical devi ...
... High availability features such as VCStack™ (Virtual Chassis Stacking) and EPSRing™ (Ethernet Protection Switched Rings) ensure traffic flow continues even during unscheduled outages. VCStack provides excellent resiliency by creating a single “virtual chassis” from two SwitchBlade x908 physical devi ...
Basics of network lab - PolyU
... able to observe name resolution occurrences using DNS servers. Introduction An IP address is a unique network layer numbering system that end systems use in order to identify and communicate with each other. It is a dotted decimal notation with four numbers ranging from 0 to 255 separated by periods ...
... able to observe name resolution occurrences using DNS servers. Introduction An IP address is a unique network layer numbering system that end systems use in order to identify and communicate with each other. It is a dotted decimal notation with four numbers ranging from 0 to 255 separated by periods ...
Module 6 – Routing and Routed Protocols
... Configuring static routes • Routers do not need to configure static routes for their own directly connected networks. • We need to configure static routes for networks this router needs to reach. • We will need to configure static routes for the other routers as well, as “routing information about a ...
... Configuring static routes • Routers do not need to configure static routes for their own directly connected networks. • We need to configure static routes for networks this router needs to reach. • We will need to configure static routes for the other routers as well, as “routing information about a ...
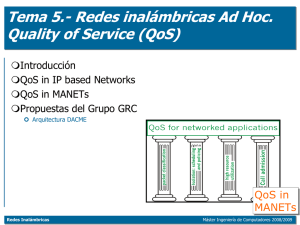
Redes Inalámbricas
... The MANET paradigm is based on user cooperation, but in most cases we can not force users to cooperate ...
... The MANET paradigm is based on user cooperation, but in most cases we can not force users to cooperate ...
Passport: Secure and Adoptable Source Authentication
... Passport is plausible for gigabit links, and can mitigate reflector attacks even without separate denial-of-service defenses. Our adoptability modeling shows that Passport provides stronger security and deployment incentives than alternatives such as ingress filtering. This is because the ISPs that ...
... Passport is plausible for gigabit links, and can mitigate reflector attacks even without separate denial-of-service defenses. Our adoptability modeling shows that Passport provides stronger security and deployment incentives than alternatives such as ingress filtering. This is because the ISPs that ...
datagram network
... • Header length is 4 bits for the number of bytes in the IP header (usually 20 B) • Type of service (TOS) is 8 bits which allow one to specify different levels of service (real time or not) • Datagram length in bytes is the total of the header plus the actual data segment – Is a 16 bit field, but ty ...
... • Header length is 4 bits for the number of bytes in the IP header (usually 20 B) • Type of service (TOS) is 8 bits which allow one to specify different levels of service (real time or not) • Datagram length in bytes is the total of the header plus the actual data segment – Is a 16 bit field, but ty ...
PXG3.L, PXG3.M BACnet Router
... Routing between BACnet/IP , BACnet/LonTalk (PXG3.L only), and BACnet MS/TP Compliant with ANSI/ASHRAE 135-2010 Compliant with ISO 16484-5 Support for BBMD (BACnet Broadcast Management Device) Support for Foreign Device Configuration via Xworks Plus or Web browser Access to network statistics via Web ...
... Routing between BACnet/IP , BACnet/LonTalk (PXG3.L only), and BACnet MS/TP Compliant with ANSI/ASHRAE 135-2010 Compliant with ISO 16484-5 Support for BBMD (BACnet Broadcast Management Device) Support for Foreign Device Configuration via Xworks Plus or Web browser Access to network statistics via Web ...
NetAdmin
... • Configured on the interface where you want to adjust EIGRP traffic. • Whatever value is specified with the bandwidth command, EIGRP always takes 50% of it (by default). • Remember: The bandwidth command is only used by routing protocols—it has no effect on user traffic when the protocol is EIGRP. ...
... • Configured on the interface where you want to adjust EIGRP traffic. • Whatever value is specified with the bandwidth command, EIGRP always takes 50% of it (by default). • Remember: The bandwidth command is only used by routing protocols—it has no effect on user traffic when the protocol is EIGRP. ...
ppt
... intended recipient. As such there are more frequent problems with transmission than with connection-oriented protocols and it may be necessary to resend the data several times.” ...
... intended recipient. As such there are more frequent problems with transmission than with connection-oriented protocols and it may be necessary to resend the data several times.” ...
Next Generation NP Solutions - ENUM
... • Lack of clear drivers to justify ENUM and IP Interconnect business case » Intra-networking use cases seem more pressing today • Network equipment vendors have been slow to support ENUM standards • Lack of network-based products to handle outbound ENUM routing as well as ENUM publication to interco ...
... • Lack of clear drivers to justify ENUM and IP Interconnect business case » Intra-networking use cases seem more pressing today • Network equipment vendors have been slow to support ENUM standards • Lack of network-based products to handle outbound ENUM routing as well as ENUM publication to interco ...
IP Multicast
... DVMRP: Summary • Distance Vector Multicast Routing Protocol • Leaf router sends a prune message to neighbouring routers when there is no group member on the subnet. • Intermediate routers perform pruning whenever possible. • Flooding and pruning are repeated periodically, when the current state tim ...
... DVMRP: Summary • Distance Vector Multicast Routing Protocol • Leaf router sends a prune message to neighbouring routers when there is no group member on the subnet. • Intermediate routers perform pruning whenever possible. • Flooding and pruning are repeated periodically, when the current state tim ...
Resilient Overlay Networks Abstract MIT Laboratory for Computer Science
... and its constituent networks, usually operated by some network service provider. The information shared with other providers and AS’s is heavily filtered and summarized using the Border Gateway Protocol (BGP-4) running at the border routers between AS’s [21], which allows the Internet to scale to mi ...
... and its constituent networks, usually operated by some network service provider. The information shared with other providers and AS’s is heavily filtered and summarized using the Border Gateway Protocol (BGP-4) running at the border routers between AS’s [21], which allows the Internet to scale to mi ...
VLANs
... switching fabric / backplane to support all ports if they become active so the switch forms groups of connections and assigns capacity using time division multiplexing. • This means that the switch no longer guarantees simultaneous transmission on all ports, but will accept simultaneous input and wi ...
... switching fabric / backplane to support all ports if they become active so the switch forms groups of connections and assigns capacity using time division multiplexing. • This means that the switch no longer guarantees simultaneous transmission on all ports, but will accept simultaneous input and wi ...
6 Multi-layer Recovery Strategy in Resilient Packet
... point-to-point circuit-switched services such as voice services. On the other hand, for metropolitan environments, Ethernet technology may offer a simpler and cost-effective solution for the transport of the data traffic. However, because Ethernet is optimized for point-to-point or meshed topologies ...
... point-to-point circuit-switched services such as voice services. On the other hand, for metropolitan environments, Ethernet technology may offer a simpler and cost-effective solution for the transport of the data traffic. However, because Ethernet is optimized for point-to-point or meshed topologies ...
Understanding KaZaA
... search mechanism. This overview combines publicly available information with some of our own investigations, which are described in more detail in Section III. KaZaA resembles Gnutella in that it does not use a dedicated server for tracking and locating content. However, unlike Gnutella, not all pee ...
... search mechanism. This overview combines publicly available information with some of our own investigations, which are described in more detail in Section III. KaZaA resembles Gnutella in that it does not use a dedicated server for tracking and locating content. However, unlike Gnutella, not all pee ...
cisco 2-11
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
BACnet in China
... • Sensors and actuators attach directly to the controllers • BACnet device profiles such as B-ASC and B-AAC communicate the capabilities of the controller • The equipment vendor decides what programming method to use ...
... • Sensors and actuators attach directly to the controllers • BACnet device profiles such as B-ASC and B-AAC communicate the capabilities of the controller • The equipment vendor decides what programming method to use ...
Linksys NR041 Manual
... The Router’s firewall protects your network of PCs so users on the public, Internet side cannot “see” your PCs. This is how your network remains private. The Router protects your network by inspecting every data packet coming in through the Internet (or WAN) port before delivery to the final destina ...
... The Router’s firewall protects your network of PCs so users on the public, Internet side cannot “see” your PCs. This is how your network remains private. The Router protects your network by inspecting every data packet coming in through the Internet (or WAN) port before delivery to the final destina ...
Wireless Router Setup Manual
... How to Set Up and Test Basic Wireless Connectivity Follow the instructions below to set up and test basic wireless connectivity. Once you have established basic wireless connectivity, you can enable security settings appropriate to your needs. 1. Log in to the router at http://www.routerlogin.net wi ...
... How to Set Up and Test Basic Wireless Connectivity Follow the instructions below to set up and test basic wireless connectivity. Once you have established basic wireless connectivity, you can enable security settings appropriate to your needs. 1. Log in to the router at http://www.routerlogin.net wi ...
Wireless Router Setup Manual 4500 Great America Parkway Santa Clara, CA 95054 USA
... How to Set Up and Test Basic Wireless Connectivity Follow the instructions below to set up and test basic wireless connectivity. Once you have established basic wireless connectivity, you can enable security settings appropriate to your needs. 1. Log in to the router at http://www.routerlogin.net wi ...
... How to Set Up and Test Basic Wireless Connectivity Follow the instructions below to set up and test basic wireless connectivity. Once you have established basic wireless connectivity, you can enable security settings appropriate to your needs. 1. Log in to the router at http://www.routerlogin.net wi ...
IPv6 for UPnP Forum
... Increasing number of devices and Always On experience exacerbate the problem Applications and network protocols break in mobile scenarios ...
... Increasing number of devices and Always On experience exacerbate the problem Applications and network protocols break in mobile scenarios ...
lim-previous-version
... Establishing a IPv6 network infrastructure that can provide IPv6 service to customer Verifying technology and identifying a problem for scalable deployment ‘IPv6 special zone’ that is able to make end-to-end IPv6 connection, will be established for verification of full routing path through dual stac ...
... Establishing a IPv6 network infrastructure that can provide IPv6 service to customer Verifying technology and identifying a problem for scalable deployment ‘IPv6 special zone’ that is able to make end-to-end IPv6 connection, will be established for verification of full routing path through dual stac ...

![SwitchBlade® x908 [Rev ZJ]](http://s1.studyres.com/store/data/008053519_1-53b0e3770fa5647be537fdbf48703248-300x300.png)