lim-previous-version
... Establishing a IPv6 network infrastructure that can provide IPv6 service to customer Verifying technology and identifying a problem for scalable deployment ‘IPv6 special zone’ that is able to make end-to-end IPv6 connection, will be established for verification of full routing path through dual stac ...
... Establishing a IPv6 network infrastructure that can provide IPv6 service to customer Verifying technology and identifying a problem for scalable deployment ‘IPv6 special zone’ that is able to make end-to-end IPv6 connection, will be established for verification of full routing path through dual stac ...
Integrating Cisco Press Resources into the
... Maintaining Routing Information Via Link States • OSPF and Intermediate System-to-Intermediate System (IS-IS) are link-state routing protocols – Collect routing information from all other routers in the area – Each router calculates all the best paths to all destinations in the network – Because eac ...
... Maintaining Routing Information Via Link States • OSPF and Intermediate System-to-Intermediate System (IS-IS) are link-state routing protocols – Collect routing information from all other routers in the area – Each router calculates all the best paths to all destinations in the network – Because eac ...
ESnet - Indico
... Internet2 has partnered with Level 3 Communications Co. for a dedicated optical fiber infrastructure with a national footprint and a rich topology - the “Internet2 Network” o ...
... Internet2 has partnered with Level 3 Communications Co. for a dedicated optical fiber infrastructure with a national footprint and a rich topology - the “Internet2 Network” o ...
Large-scale Internet measurement
... 2.60. AS level topology ................................................................................................. 2.61. AS level topology ................................................................................................. 2.62. AS level topology ................................ ...
... 2.60. AS level topology ................................................................................................. 2.61. AS level topology ................................................................................................. 2.62. AS level topology ................................ ...
We need to have support for the notion of advertisements
... subsequently to achieve the best possible routing characteristics. The brokering system, since it is aware of advertisements, can also act as a hub for search and discovery operations. These advertisements when organized into “queryspaces” allow the integrated system to respond to search operations ...
... subsequently to achieve the best possible routing characteristics. The brokering system, since it is aware of advertisements, can also act as a hub for search and discovery operations. These advertisements when organized into “queryspaces” allow the integrated system to respond to search operations ...
MPLS
... connectionless IP-based Internet providing the foundation for sophisticated and reliable QoS traffic ...
... connectionless IP-based Internet providing the foundation for sophisticated and reliable QoS traffic ...
DEFT: Distributed Exponentially-weighted Flow Splitting
... in large part because the existing protocols and mechanisms sometimes were not designed with management in mind. For example, the design of existing protocols and mechanisms typically induces optimization problems that are computationally intractable, forcing the use of local-search techniques to id ...
... in large part because the existing protocols and mechanisms sometimes were not designed with management in mind. For example, the design of existing protocols and mechanisms typically induces optimization problems that are computationally intractable, forcing the use of local-search techniques to id ...
4 The Economics of Peer-to
... incentives at play in file-sharing systems like Gnutella or BitTorrent? For many applications that require the distribution of files to a large number of users, peerto-peer (P2P) file-sharing networks are an attractive alternative to server-based solutions. If the community of file sharers cooperate ...
... incentives at play in file-sharing systems like Gnutella or BitTorrent? For many applications that require the distribution of files to a large number of users, peerto-peer (P2P) file-sharing networks are an attractive alternative to server-based solutions. If the community of file sharers cooperate ...
Apuntes seguridad Redes Avanzadas 0708
... provide multicast connectivity to a source, using UDP-based encapsulation to overcome the lack of multicast connectivity. AMT builds dynamic tunnels from hosts and can support any host application. Although the AMT protocol is defined for both SSM and ASM traffic, it is primarily intended for use in ...
... provide multicast connectivity to a source, using UDP-based encapsulation to overcome the lack of multicast connectivity. AMT builds dynamic tunnels from hosts and can support any host application. Although the AMT protocol is defined for both SSM and ASM traffic, it is primarily intended for use in ...
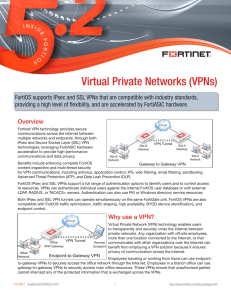
Virtual Private Networks (VPNs)
... access control, security profiles, and endpoint control. Some networks, such as those available in public spaces, may block IPsec protocols, thereby preventing IPsec endpoints from accessing their IPsec VPN gateways. An SSL VPN is the only workaround in this situation, since the HTTPS protocol used ...
... access control, security profiles, and endpoint control. Some networks, such as those available in public spaces, may block IPsec protocols, thereby preventing IPsec endpoints from accessing their IPsec VPN gateways. An SSL VPN is the only workaround in this situation, since the HTTPS protocol used ...
PDF
... Cisco Performance Routing removes this complexity from network operators and provides needed application performance when the network is operational but parts of the network are experiencing performance-degradation problems. Cisco PfR in its truest form is “application routing based on network perfo ...
... Cisco Performance Routing removes this complexity from network operators and provides needed application performance when the network is operational but parts of the network are experiencing performance-degradation problems. Cisco PfR in its truest form is “application routing based on network perfo ...
Document
... Introduce a “self-organizing” virtual id (vid) layer a layer 2 (LLC)/layer-3 convergence layer -- replacing IP subsume layer-2/layer-3 routing/forwarding functionality except for first/last hop: host to switch or switch to host layer-3 addresses (or higher layer names): global addressing or ...
... Introduce a “self-organizing” virtual id (vid) layer a layer 2 (LLC)/layer-3 convergence layer -- replacing IP subsume layer-2/layer-3 routing/forwarding functionality except for first/last hop: host to switch or switch to host layer-3 addresses (or higher layer names): global addressing or ...
IP: Addresses and Forwarding - RPI ECSE
... 2. Flood LSP => reaches every other node in the network and everyone now has a network map. 3. Given map, run Dijkstra’s shortest path algorithm (SPF) => get paths to all destinations 4. Routing table = next-hops of these paths. 5. Hierarchical routing: organization of areas, and filtered ...
... 2. Flood LSP => reaches every other node in the network and everyone now has a network map. 3. Given map, run Dijkstra’s shortest path algorithm (SPF) => get paths to all destinations 4. Routing table = next-hops of these paths. 5. Hierarchical routing: organization of areas, and filtered ...
Intermediate System-to-Intermediate System (IS-IS)
... • The practice of using a modified loopback IP address as the system ID may now be considered outdated because of the dynamic host name feature. This feature uses a new Type Length Value (TLV 137) to map the router’s host name to the system ID. • Each device must have a unique system ID within the a ...
... • The practice of using a modified loopback IP address as the system ID may now be considered outdated because of the dynamic host name feature. This feature uses a new Type Length Value (TLV 137) to map the router’s host name to the system ID. • Each device must have a unique system ID within the a ...
NE5000E Product Description
... The Huawei NetEngine5000E (NE5000E) core router is a router with large capacities and high performance which is developed to meet the requirement of carrier-class reliability. Based on the powerful Versatile Routing Platform (VRP), the NE5000E provides strong switching capabilities, dense ports, and ...
... The Huawei NetEngine5000E (NE5000E) core router is a router with large capacities and high performance which is developed to meet the requirement of carrier-class reliability. Based on the powerful Versatile Routing Platform (VRP), the NE5000E provides strong switching capabilities, dense ports, and ...
Intelligent WAN and WAN Design Summary (CVD) – October
... smaller sites or as a backup path because of the risks. Now this cost-effective, performance-enhancing opportunity can be realized at all your branch offices with Cisco IWAN. Cisco IWAN enables organizations to deliver an uncompromised experience over any connection. With Cisco IWAN, IT organization ...
... smaller sites or as a backup path because of the risks. Now this cost-effective, performance-enhancing opportunity can be realized at all your branch offices with Cisco IWAN. Cisco IWAN enables organizations to deliver an uncompromised experience over any connection. With Cisco IWAN, IT organization ...
IPv6
... Address Registries Address registries for IPv6 are the same one as for IPv4, ARIN,RIPE and APNIC. • Only large network providers will ever obtain addresses directly from the registries, such as UNINET : one such provider in Thailand • If a /35 prefix is allocates, the registry internally will reser ...
... Address Registries Address registries for IPv6 are the same one as for IPv4, ARIN,RIPE and APNIC. • Only large network providers will ever obtain addresses directly from the registries, such as UNINET : one such provider in Thailand • If a /35 prefix is allocates, the registry internally will reser ...
EPL-Router sorgt für Transparenz und Durchgängigkeit
... machine and plant engineer only needs communication medium based on standard components. The Ethernet Powerlink-Router by Deutschmann Automation was developed for the seamless integration of an Ethernet Powerlink segment within a machine into the industrial network and with it being able to access t ...
... machine and plant engineer only needs communication medium based on standard components. The Ethernet Powerlink-Router by Deutschmann Automation was developed for the seamless integration of an Ethernet Powerlink segment within a machine into the industrial network and with it being able to access t ...
bgp2
... – In comparing two or more different routes, given that all other attributes are identical, a shorter path is always preferred. – In case of a tie in AS_PATH length, other attributes are used to make the decision. (later) Private AS numbers cannot be leaked to the Internet because they are not uniqu ...
... – In comparing two or more different routes, given that all other attributes are identical, a shorter path is always preferred. – In case of a tie in AS_PATH length, other attributes are used to make the decision. (later) Private AS numbers cannot be leaked to the Internet because they are not uniqu ...
Chapter 6 - YSU Computer Science & Information Systems
... there is a neighbor table for each protocol that EIGRP supports used to support reliable, sequenced delivery of packets • One field in each row of the table is populated with the last sequence number of the packet received from that neighbor • EIGRP uses this field for two purposes: – Sequence num ...
... there is a neighbor table for each protocol that EIGRP supports used to support reliable, sequenced delivery of packets • One field in each row of the table is populated with the last sequence number of the packet received from that neighbor • EIGRP uses this field for two purposes: – Sequence num ...
Service Definitions - text for CSA
... provisioned across both networks. The larger the common ranges, the more likely service requests will be compatible with both service offerings. So it behooves the service providers to maximize the degree to which service attributes meet or exceed the ranges specified in the CSD. Doing so provides b ...
... provisioned across both networks. The larger the common ranges, the more likely service requests will be compatible with both service offerings. So it behooves the service providers to maximize the degree to which service attributes meet or exceed the ranges specified in the CSD. Doing so provides b ...
chap_19_1
... DVMRP: Summary • Distance Vector Multicast Routing Protocol • Leaf router sends a prune message to neighbouring routers when there is no group member on the subnet. • Intermediate routers perform pruning whenever possible. • Flooding and pruning are repeated periodically, when the current state tim ...
... DVMRP: Summary • Distance Vector Multicast Routing Protocol • Leaf router sends a prune message to neighbouring routers when there is no group member on the subnet. • Intermediate routers perform pruning whenever possible. • Flooding and pruning are repeated periodically, when the current state tim ...
x510 Series Datasheet
... The convergence of network services in the enterprise has led to increasing demand for highly available networks with minimal downtime. VCStack, in conjunction with link aggregation, provides a network with no single point of failure and an easy solution for resiliency in access applications. ...
... The convergence of network services in the enterprise has led to increasing demand for highly available networks with minimal downtime. VCStack, in conjunction with link aggregation, provides a network with no single point of failure and an easy solution for resiliency in access applications. ...