x510 Series Datasheet
... The convergence of network services in the enterprise has led to increasing demand for highly available networks with minimal downtime. VCStack, in conjunction with link aggregation, provides a network with no single point of failure and an easy solution for resiliency in access applications. ...
... The convergence of network services in the enterprise has led to increasing demand for highly available networks with minimal downtime. VCStack, in conjunction with link aggregation, provides a network with no single point of failure and an easy solution for resiliency in access applications. ...
D3.2 Traffic Models
... are the bandwidth of the different links and the QoS constraints are defined in order to satisfy users’ performance requirements. Two different approaches have appeared to deal with this problem. In the first approach, protocols and architectures that guarantee the QoS constraints are used to reserv ...
... are the bandwidth of the different links and the QoS constraints are defined in order to satisfy users’ performance requirements. Two different approaches have appeared to deal with this problem. In the first approach, protocols and architectures that guarantee the QoS constraints are used to reserv ...
The Allied Telesis x610 Series is the high performing and... solution for today’s networks, providing an extensive range of
... switches to form a high-speed protected ring capable of recovery within as little as 50ms. This feature is perfect for high performance and high availability in enterprise networks. »» SuperLoop Protection (SLP) enables a link between two EPSR nodes to be in separate EPSR domains, improving redundan ...
... switches to form a high-speed protected ring capable of recovery within as little as 50ms. This feature is perfect for high performance and high availability in enterprise networks. »» SuperLoop Protection (SLP) enables a link between two EPSR nodes to be in separate EPSR domains, improving redundan ...
CTP: An Efficient, Robust, and Reliable Collection Tree Protocol for
... First, achieving these goals depends on link estimation accuracy and agility. For example, recent experimental studies have shown that, at the packet level, wireless links in some environments have coherence times as small as 500 milliseconds [Srinivasan et al. 2008]. Being efficient requires using ...
... First, achieving these goals depends on link estimation accuracy and agility. For example, recent experimental studies have shown that, at the packet level, wireless links in some environments have coherence times as small as 500 milliseconds [Srinivasan et al. 2008]. Being efficient requires using ...
Segment Routing and Path Computation Element
... (MPLS) labels or as one or more IPv6 addresses. Where MPLS is used, SR does not have a requirement for the Label Distribution Protocol (LDP) and/or Resource Reservation Protocol – Traffic Engineering (RSVP-TE) transport signaling control plane. No state is held in the network with the exception of t ...
... (MPLS) labels or as one or more IPv6 addresses. Where MPLS is used, SR does not have a requirement for the Label Distribution Protocol (LDP) and/or Resource Reservation Protocol – Traffic Engineering (RSVP-TE) transport signaling control plane. No state is held in the network with the exception of t ...
MinBD: Minimally-Buffered Deflection Routing for Energy
... a 64-node system compared to a conventional buffered router. Unfortunately, at high network load, deflection routing reduces performance and efficiency. This is because deflections occur more frequently when many flits contend in the network. Each deflection sends a flit further from its destination ...
... a 64-node system compared to a conventional buffered router. Unfortunately, at high network load, deflection routing reduces performance and efficiency. This is because deflections occur more frequently when many flits contend in the network. Each deflection sends a flit further from its destination ...
Networking the Internet - Part 1
... U.S.S.R. launching Sputnik, the first satellite. Out of this came the Internet, a way for computers to communicate from different parts of the world. These computers can be any type of computer using any type of operating system, as long as they are using the protocol TCP/IP. ...
... U.S.S.R. launching Sputnik, the first satellite. Out of this came the Internet, a way for computers to communicate from different parts of the world. These computers can be any type of computer using any type of operating system, as long as they are using the protocol TCP/IP. ...
Exploring and Improving BitTorrent Swarm Topologies
... been the goal of many studies but as we will see in Section 3.2 none have been adopted at a large scale. Previous studies attempting to improve locality can be generally divided into three categories, according to which part of the system is trying to improve the locality: the local client by making ...
... been the goal of many studies but as we will see in Section 3.2 none have been adopted at a large scale. Previous studies attempting to improve locality can be generally divided into three categories, according to which part of the system is trying to improve the locality: the local client by making ...
Alcatel-Lucent OmniAccess 5510
... Managed VPN services and Managed Security services to their enterprise customers. As part of Managed VPN, Service Providers can offer both premium IP-VPNs and Layer 2 Carrier Ethernet VPNs, which allows them to differentiate their service offering from a low margin bandwidth-only service. OmniAccess ...
... Managed VPN services and Managed Security services to their enterprise customers. As part of Managed VPN, Service Providers can offer both premium IP-VPNs and Layer 2 Carrier Ethernet VPNs, which allows them to differentiate their service offering from a low margin bandwidth-only service. OmniAccess ...
module10b
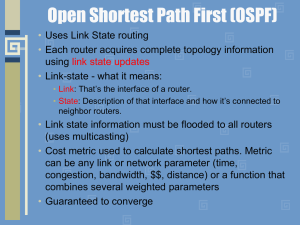
... • Router ID: Each OSPF router needs to have an unique ID which is the highest IP • address on any active interface. More about this later. • Hello / Dead Interval: Every X seconds we are going to send a hello packet, if we don’t hear any hello packets from our network for X seconds we declare you “d ...
... • Router ID: Each OSPF router needs to have an unique ID which is the highest IP • address on any active interface. More about this later. • Hello / Dead Interval: Every X seconds we are going to send a hello packet, if we don’t hear any hello packets from our network for X seconds we declare you “d ...
Cisco Inter-network Operating System (IOS) A short guide for the
... The network-number identifies the network using OSPF. The mask tells which bits to use from the network-number, and the area-id is used for determining areas in an OSPF configuration. Example: Router(config-router)#network 192.168.10.0 255.255.255.0 area 0.0.0.0 Repeat this step for all the network ...
... The network-number identifies the network using OSPF. The mask tells which bits to use from the network-number, and the area-id is used for determining areas in an OSPF configuration. Example: Router(config-router)#network 192.168.10.0 255.255.255.0 area 0.0.0.0 Repeat this step for all the network ...
3GPP TS 23.517 V8.0.0 (2007-12)
... Functional entities of an IMS may be used by an operator in support of transit network scenarios. The routing may be performed, depending on the entity performing the routing, and depending on the traffic case, on signalling information, configuration data, and/or data base lookup. The NGN IMS, also ...
... Functional entities of an IMS may be used by an operator in support of transit network scenarios. The routing may be performed, depending on the entity performing the routing, and depending on the traffic case, on signalling information, configuration data, and/or data base lookup. The NGN IMS, also ...
Business Ready Branch Solutions for Enterprise and Small
... AccessPath, AtmDirector, Browse with Me, CCIP, CCSI, CD-PAC, CiscoLink, the Cisco Powered Network logo, Cisco Systems Networking Academy, the Cisco Systems Networking Academy logo, Cisco Unity, Fast Step, Follow Me Browsing, FormShare, FrameShare, IGX, Internet Quotient, IP/VC, iQ Breakthrough, iQ E ...
... AccessPath, AtmDirector, Browse with Me, CCIP, CCSI, CD-PAC, CiscoLink, the Cisco Powered Network logo, Cisco Systems Networking Academy, the Cisco Systems Networking Academy logo, Cisco Unity, Fast Step, Follow Me Browsing, FormShare, FrameShare, IGX, Internet Quotient, IP/VC, iQ Breakthrough, iQ E ...
Introduction to Dynamic Routing Protocols
... two or more computers. At work, your organization might have multiple routers and switches servicing the data communication needs of hundreds or even thousands of PCs. In Chapters 1 and 2, you discovered how routers are used in packet forwarding and that routers learn about remote networks using bot ...
... two or more computers. At work, your organization might have multiple routers and switches servicing the data communication needs of hundreds or even thousands of PCs. In Chapters 1 and 2, you discovered how routers are used in packet forwarding and that routers learn about remote networks using bot ...
Routing Protocols
... Purpose of Dynamic Routing Protocols Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of messages to dis ...
... Purpose of Dynamic Routing Protocols Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of messages to dis ...
SLAC IPv6 deployment
... IPv6 Network configuration There is IOS code available that allows: – Cryptographic images • SSH client/server ...
... IPv6 Network configuration There is IOS code available that allows: – Cryptographic images • SSH client/server ...
Implementation of IPv6 ToS over ATM Network
... called “IPv6 ToS Mapping” is also added to the source. This new attribute allows the user to select the ATM service category to map IPv6’s ToS. At simulation time, depending on the user’s selection, SVC’s of the specified ATM service category will be set up before packets are generated. For example, ...
... called “IPv6 ToS Mapping” is also added to the source. This new attribute allows the user to select the ATM service category to map IPv6’s ToS. At simulation time, depending on the user’s selection, SVC’s of the specified ATM service category will be set up before packets are generated. For example, ...
Module 2 - OoCities
... Q12: ARPANET was a special agency within the United States Department of Defense (US DOD) to fund and foster researchers in many important areas, including computing (Answer: True). Q13: What’s the meaning of the computers operated in batch mode? Answer: No direct interaction with the user, during t ...
... Q12: ARPANET was a special agency within the United States Department of Defense (US DOD) to fund and foster researchers in many important areas, including computing (Answer: True). Q13: What’s the meaning of the computers operated in batch mode? Answer: No direct interaction with the user, during t ...
show ip route
... Clarifications (This is for IGPs only and not EGPs such as BGP): • The network command does two things: 1. Determines which interfaces will participate in sending and receiving routing updates, as long as the interface IP address falls in the range of the network command. 2. Determines which network ...
... Clarifications (This is for IGPs only and not EGPs such as BGP): • The network command does two things: 1. Determines which interfaces will participate in sending and receiving routing updates, as long as the interface IP address falls in the range of the network command. 2. Determines which network ...
The Internet and Its Uses
... various VLANs to communicate with each other. –In a previous chapter, you learned that each VLAN is a unique broadcast domain, so computers on separate VLANs are, by default, not able to communicate. –There is a way to permit these end stations to communicate; it is called inter-VLAN routing. ...
... various VLANs to communicate with each other. –In a previous chapter, you learned that each VLAN is a unique broadcast domain, so computers on separate VLANs are, by default, not able to communicate. –There is a way to permit these end stations to communicate; it is called inter-VLAN routing. ...
CCNA5.0 Instructor PPT - Bina Darma e
... Purpose of Dynamic Routing Protocols Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of messages to dis ...
... Purpose of Dynamic Routing Protocols Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of messages to dis ...
Economic model for routing and spectrum management in cognitive
... channels from PUs. PU may refuse assigning its channels for SUs. Moreover, the transmission power should be managed to avoid disturbing PUs transmissions. Sometimes SUs avoid accessing channels during good channel conditions due to the priority of PUs flows. These challenges make routing problem in ...
... channels from PUs. PU may refuse assigning its channels for SUs. Moreover, the transmission power should be managed to avoid disturbing PUs transmissions. Sometimes SUs avoid accessing channels during good channel conditions due to the priority of PUs flows. These challenges make routing problem in ...
JXTA Overview - 123SeminarsOnly.com
... Distributed/Grid Computing. Distributed Storage. Distributed Caches. ...
... Distributed/Grid Computing. Distributed Storage. Distributed Caches. ...
ECE/CS 4984: Lecture 11
... ■ Sender assumes loss when it receives three duplicate ACKs ■ Fast retransmission and recovery mechanism – retransmit the requested segment (which is presumed lost after three duplicate ACKs) without waiting for a timeout ■ Congestion avoidance (smaller reduction in rate) Mobile Networks: TCP in Wir ...
... ■ Sender assumes loss when it receives three duplicate ACKs ■ Fast retransmission and recovery mechanism – retransmit the requested segment (which is presumed lost after three duplicate ACKs) without waiting for a timeout ■ Congestion avoidance (smaller reduction in rate) Mobile Networks: TCP in Wir ...