RabbitMQ - FMDevelopers
... Easier scaling to cloud ◦ Subscribers to queue can be on different servers; decoupling application into processing units ...
... Easier scaling to cloud ◦ Subscribers to queue can be on different servers; decoupling application into processing units ...
Defense
... Introduction • WLAN, RADIUS, EAP, TLS,TTLS, PEAP Design and Implementation of PEAP Module for Free RADIUS Performance Comparison of PEAP and TTLS Conclusion and Future Work Nirmala 12/18/03 ...
... Introduction • WLAN, RADIUS, EAP, TLS,TTLS, PEAP Design and Implementation of PEAP Module for Free RADIUS Performance Comparison of PEAP and TTLS Conclusion and Future Work Nirmala 12/18/03 ...
Slides
... – Security Parameters Index (SPI): only of local significance. The SPI is carried in AH and ESP headers to enable the receiving system to select the SA under which a received packet will be processed. – IP Destination Address: The address of the destination endpoint of the SA eg. End user system ...
... – Security Parameters Index (SPI): only of local significance. The SPI is carried in AH and ESP headers to enable the receiving system to select the SA under which a received packet will be processed. – IP Destination Address: The address of the destination endpoint of the SA eg. End user system ...
Document
... If CAMs fill, switches generate new keys Too many revocations = loose privileges payload ...
... If CAMs fill, switches generate new keys Too many revocations = loose privileges payload ...
lecture10 - Computer and Information Sciences
... after intercepting enough packets, there are sure to be repeats ...
... after intercepting enough packets, there are sure to be repeats ...
- NetComm Wireless
... Configuring an OpenVPN server If using certificate authentication, enter the details for at least one certificate and click Generate. After its generated, you can use the Download button to download the certificate file. Certificates may be revoked in the future if they are no longer necessary or s ...
... Configuring an OpenVPN server If using certificate authentication, enter the details for at least one certificate and click Generate. After its generated, you can use the Download button to download the certificate file. Certificates may be revoked in the future if they are no longer necessary or s ...
www.ijecs.in International Journal Of Engineering And Computer Science ISSN: 2319-7242
... [email protected] Abstract: Security is often vital in knowledge networks; however it's significantly crucial in wireless networks like LTE. One in all the distinctive challenges of fourth-generation technology is the way to shut a security gap through that one compromised or malicious device w ...
... [email protected] Abstract: Security is often vital in knowledge networks; however it's significantly crucial in wireless networks like LTE. One in all the distinctive challenges of fourth-generation technology is the way to shut a security gap through that one compromised or malicious device w ...
Encrypting Wireless Data with VPN Techniques
... – More moving parts and more likely to break. – Clients and servers can be difficult to configure, deploy and maintain. – Expensive in almost any size network. – Advanced routing is difficult – Lack of interoperability between different vendors of VPN technology. – Lack of operating system support a ...
... – More moving parts and more likely to break. – Clients and servers can be difficult to configure, deploy and maintain. – Expensive in almost any size network. – Advanced routing is difficult – Lack of interoperability between different vendors of VPN technology. – Lack of operating system support a ...
Wireless Communications and Networks
... Result PDU – used to convey response of the server to the client Abort PDU – used to abort a transaction Segmented invoke PDU and segmented result PDU – used for segmentation and reassembly Negative acknowledgment PDU – used to indicate that some packets did not arrive ...
... Result PDU – used to convey response of the server to the client Abort PDU – used to abort a transaction Segmented invoke PDU and segmented result PDU – used for segmentation and reassembly Negative acknowledgment PDU – used to indicate that some packets did not arrive ...
Passwords - University of Colorado Boulder
... – after 3 failed attempts disallow log-in for 5 minutes – permit fake log-in after several failed attempts • Automatic log-off – log off anybody with no activity for 10 minutes – authentication for every transaction • Transaction logs – every log-in is logged (date, time user id, unsuccessful attemp ...
... – after 3 failed attempts disallow log-in for 5 minutes – permit fake log-in after several failed attempts • Automatic log-off – log off anybody with no activity for 10 minutes – authentication for every transaction • Transaction logs – every log-in is logged (date, time user id, unsuccessful attemp ...
View File
... Result PDU – used to convey response of the server to the client Abort PDU – used to abort a transaction Segmented invoke PDU and segmented result PDU – used for segmentation and reassembly Negative acknowledgment PDU – used to indicate that some packets did not arrive ...
... Result PDU – used to convey response of the server to the client Abort PDU – used to abort a transaction Segmented invoke PDU and segmented result PDU – used for segmentation and reassembly Negative acknowledgment PDU – used to indicate that some packets did not arrive ...
Device Security
... – v3 is more secure by providing MD5 or SHA for authentication, and DES for encryption. ...
... – v3 is more secure by providing MD5 or SHA for authentication, and DES for encryption. ...
Actiontec GT724R DSL Modem with 4 Port Ethernet Router Product
... Actiontec, Actiontec Installation Buddy, Connection1-2-3, Creative Solutions for the Digital Life, Actiontec Digital Gear and the Actiontec logo are trademarks or registered trademarks of Actiontec Electronics, Inc. All other names are properties of their respective owners. Product photo may differ ...
... Actiontec, Actiontec Installation Buddy, Connection1-2-3, Creative Solutions for the Digital Life, Actiontec Digital Gear and the Actiontec logo are trademarks or registered trademarks of Actiontec Electronics, Inc. All other names are properties of their respective owners. Product photo may differ ...
Chapter_18
... Even if known, should not be able to decrypt or work out key Even if a number of cipher texts are available together with plain texts of them ...
... Even if known, should not be able to decrypt or work out key Even if a number of cipher texts are available together with plain texts of them ...
William Stallings Data and Computer Communications
... Even if known, should not be able to decrypt or work out key Even if a number of cipher texts are available together with plain texts of them ...
... Even if known, should not be able to decrypt or work out key Even if a number of cipher texts are available together with plain texts of them ...
Ch 2: Exploring Control Types and Methods
... spoofed They are transmitted in plaintext with each frame ...
... spoofed They are transmitted in plaintext with each frame ...
Network Security: Internet Mobility
... nodes, without introducing new security infrastructure? Set requirements to the right level: Internet with Mobile IPv6 deployed must be as secure as before it → no general-purpose strong authentication needed Some IP-layer infrastructure is available: IPv6 addresses Routing infrastructure ...
... nodes, without introducing new security infrastructure? Set requirements to the right level: Internet with Mobile IPv6 deployed must be as secure as before it → no general-purpose strong authentication needed Some IP-layer infrastructure is available: IPv6 addresses Routing infrastructure ...
Authentication Key - Pravin Shetty > Resume
... Performs a double-reverse lookup of the IP address to make sure the DNS entries for the IP address match the hostname. Logs the result with syslog. This provides a way to log services that are normally not logged, e.g., finger and systat. Optionally run a command, e.g., run finger to get a list o ...
... Performs a double-reverse lookup of the IP address to make sure the DNS entries for the IP address match the hostname. Logs the result with syslog. This provides a way to log services that are normally not logged, e.g., finger and systat. Optionally run a command, e.g., run finger to get a list o ...
WLAN Site Surveys and Security Considerations
... Does not specify MAC level encryption type (I.e. WEP40/104 or other), so independent of it However, 802.1x can be used to set WEP keys – Addresses Key Distribution problem – Permits rapidly changing, individual WEP keys – WEP is still required for encryption eLearning…Wired and Wirelessly! ...
... Does not specify MAC level encryption type (I.e. WEP40/104 or other), so independent of it However, 802.1x can be used to set WEP keys – Addresses Key Distribution problem – Permits rapidly changing, individual WEP keys – WEP is still required for encryption eLearning…Wired and Wirelessly! ...
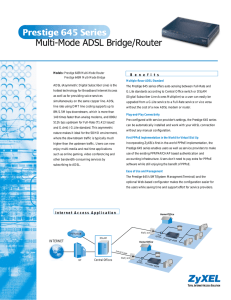
Multi-Mode ADSL Bridge/Router
... upgraded from a G.Lite service to a Full-Rate service or vice versa ...
... upgraded from a G.Lite service to a Full-Rate service or vice versa ...
HP ProCurve Switch 6108
... VLAN support and tagging: tagging supports up to 30 port-based VLANs, GVRP, and IEEE 802.1Q VLAN tagging GARP VLAN Registration Protocol: Protocol allows automatic learning and dynamic assignment of VLANs Layer 3 routing Basic IP routing: routing enables automatic routing to the connected VLANs and ...
... VLAN support and tagging: tagging supports up to 30 port-based VLANs, GVRP, and IEEE 802.1Q VLAN tagging GARP VLAN Registration Protocol: Protocol allows automatic learning and dynamic assignment of VLANs Layer 3 routing Basic IP routing: routing enables automatic routing to the connected VLANs and ...
Report The Internet Infrastructure Foundation
... PKIX on the Internet. HTTP as the most prominent of the Internet data communications protocols takes advantage of the Transport Layer Security protocol (TLS, RFC 5247[2]) or the Secure Sockets Layer protocol (SSL) by wrapping the communication in the secure channel established using an URI scheme, a ...
... PKIX on the Internet. HTTP as the most prominent of the Internet data communications protocols takes advantage of the Transport Layer Security protocol (TLS, RFC 5247[2]) or the Secure Sockets Layer protocol (SSL) by wrapping the communication in the secure channel established using an URI scheme, a ...