Mobile IP Agent Advertisement Message
... Minimal encapsulation – new header is inserted between original IP header and original IP payload ...
... Minimal encapsulation – new header is inserted between original IP header and original IP payload ...
click here
... Wireless access points can be easily, cheaply, and quickly implemented when overall network security and user authentication strategies are not taken into consideration Wireless access points are cheap and can be used to provide access to areas that would remain otherwise unserved ...
... Wireless access points can be easily, cheaply, and quickly implemented when overall network security and user authentication strategies are not taken into consideration Wireless access points are cheap and can be used to provide access to areas that would remain otherwise unserved ...
Internet Layer Protocols
... information on the screen and passing input to the server • Can have many telnet clients connected to a single server at one time ...
... information on the screen and passing input to the server • Can have many telnet clients connected to a single server at one time ...
Coop-ICNP - Columbia University
... R-MN builds a list of {Subnet ID, IP address} pairs, one per each possible subnet it might move to next. ...
... R-MN builds a list of {Subnet ID, IP address} pairs, one per each possible subnet it might move to next. ...
Chapter 3 - Network Protocols
... network traffic is allowed. To allow access to a service, you have to open the port(s) related to the service in question. You should ONLY open a port if it is absolutely necessary. Any port not explicitly allowed should be implicitly denied. ...
... network traffic is allowed. To allow access to a service, you have to open the port(s) related to the service in question. You should ONLY open a port if it is absolutely necessary. Any port not explicitly allowed should be implicitly denied. ...
P2P networks course
... Data is replicated (unlike Chord) Finding an object requires limited multicast (request data from 4 super nodes, then 8 super nodes, then 16 etc.) Skype claims that any user that has been logged on in the last 72 hours can be found ...
... Data is replicated (unlike Chord) Finding an object requires limited multicast (request data from 4 super nodes, then 8 super nodes, then 16 etc.) Skype claims that any user that has been logged on in the last 72 hours can be found ...
Chapter 2 Networking Overview
... • Used to secure email at the application level • Supported by email clients such as MS Outlook and ...
... • Used to secure email at the application level • Supported by email clients such as MS Outlook and ...
Protocol No: BR
... My own research protocol (Protocol no. ) Number of animals to be transferred to this protocol: Other NUS PI ‘s protocol (Protocol No: ) Number of animals to be transferred to this protocol: Other institution PI’s protocol (Protocol No: ) Name of PI and institution : Number of animals to be transferr ...
... My own research protocol (Protocol no. ) Number of animals to be transferred to this protocol: Other NUS PI ‘s protocol (Protocol No: ) Number of animals to be transferred to this protocol: Other institution PI’s protocol (Protocol No: ) Name of PI and institution : Number of animals to be transferr ...
Device Security
... – Allow only SSH access to a router’s console port (a feature added to IOS v12.2 or higher) ...
... – Allow only SSH access to a router’s console port (a feature added to IOS v12.2 or higher) ...
Experimental Review of IPSec Features to Enhance IP Security By
... parties interested to communicate. A security association (SA) is an agreement between two ...
... parties interested to communicate. A security association (SA) is an agreement between two ...
Outline CSE 713: Wireless Networks Security – Principles and Practices p
... Used to reliably detect attacks and shut down communication to the attacked station for a period of ...
... Used to reliably detect attacks and shut down communication to the attacked station for a period of ...
Faculty of Computer Science & Engineering Chapter 04 .Wireless
... 9. In a situation in which you need to allow outdoor users to connect to your network via a wireless LAN, which one of the following features ...
... 9. In a situation in which you need to allow outdoor users to connect to your network via a wireless LAN, which one of the following features ...
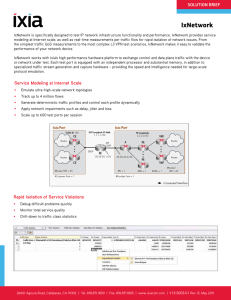
IxNetwork
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
12_SIP
... multimedia session announcement, multimedia session invitation and other forms of multimedia session initiation. A multimedia session is defined, for these purposes, as a set of media streams that exist for a duration of time. RFP 2327 ...
... multimedia session announcement, multimedia session invitation and other forms of multimedia session initiation. A multimedia session is defined, for these purposes, as a set of media streams that exist for a duration of time. RFP 2327 ...
William Stallings Data and Computer Communications
... Even if known, should not be able to decrypt or work out key Even if a number of cipher texts are available together with plain texts of them ...
... Even if known, should not be able to decrypt or work out key Even if a number of cipher texts are available together with plain texts of them ...
08 Common Network Services
... not have to provide a password • An FTP server offering anonymous FTP must be carefully configured so not to open up the host to attack – Read privileges should be limited to the public contents of the FTP repository – Write privileges should not be granted if possible • An anonymous FTP server runs ...
... not have to provide a password • An FTP server offering anonymous FTP must be carefully configured so not to open up the host to attack – Read privileges should be limited to the public contents of the FTP repository – Write privileges should not be granted if possible • An anonymous FTP server runs ...
PowerPoint - Surendar Chandra
... not computationally feasible to find two messages that hash to the same cryptographic checksum. ...
... not computationally feasible to find two messages that hash to the same cryptographic checksum. ...
Network Security - University of Engineering and Technology
... ‘securely’ over a public network.” “A combination of tunneling, encryption, authentication and access control technologies and services used to carry trusted traffic over an Untrusted IP network” ...
... ‘securely’ over a public network.” “A combination of tunneling, encryption, authentication and access control technologies and services used to carry trusted traffic over an Untrusted IP network” ...