ex2-2-o-can
... • Since many different devices can be sharing the same multiaccess network, the Router will have difficulty determining the destination MAC address. • Use both the exit interface and next-hop address for Ethernet exit interfaces. CCNA2-74 ...
... • Since many different devices can be sharing the same multiaccess network, the Router will have difficulty determining the destination MAC address. • Use both the exit interface and next-hop address for Ethernet exit interfaces. CCNA2-74 ...
chap_19_1
... • The end-router R broadcasts its group membership to the whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,].
• A sender simply sends data packets as they are available.
• Each router uses the network t ...
... • The end-router R broadcasts its group membership to the whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,
PowerPoint プレゼンテーション
... • The Internet Protocol version 6 (IPv6) – Next-generation Internet Protocol as specified by IETF – IPv6 offers expanded IP addresses to support the proliferation of Internet devices – Global Internet expansion, seamless mobility support, enhanced security and support for emerging advanced Web based ...
... • The Internet Protocol version 6 (IPv6) – Next-generation Internet Protocol as specified by IETF – IPv6 offers expanded IP addresses to support the proliferation of Internet devices – Global Internet expansion, seamless mobility support, enhanced security and support for emerging advanced Web based ...
SolarWinds Technical Reference
... Classless Internet Domain Routing (CIDR) Addresses and Subnetting As just a quick note, addresses may be classful, as seen above or be classless. Classless addresses do not strictly follow the rules of being a class A, B or C address but rather a variable subnet mask is assigned to maximize IP addre ...
... Classless Internet Domain Routing (CIDR) Addresses and Subnetting As just a quick note, addresses may be classful, as seen above or be classless. Classless addresses do not strictly follow the rules of being a class A, B or C address but rather a variable subnet mask is assigned to maximize IP addre ...
Infrastructure Design for IPTV Services
... Connect geographically close VHOs into regional rings Inter-connect rings with long haul links Security is higher than using IP backbone No access part Fast-failover ...
... Connect geographically close VHOs into regional rings Inter-connect rings with long haul links Security is higher than using IP backbone No access part Fast-failover ...
An “UltraLight”
... • Packet switched: Many applications can effectively utilize the existing, cost effective networks provided by shared packet switched infrastructure. A subset of applications require more stringent guarantees than a best-effort network can provide, and so we are planning to utilize MPLS as an iterme ...
... • Packet switched: Many applications can effectively utilize the existing, cost effective networks provided by shared packet switched infrastructure. A subset of applications require more stringent guarantees than a best-effort network can provide, and so we are planning to utilize MPLS as an iterme ...
Routing & Addressing
... • Router can also be called a computer – However, it is a special purpose computer that is dedicated to routing ...
... • Router can also be called a computer – However, it is a special purpose computer that is dedicated to routing ...
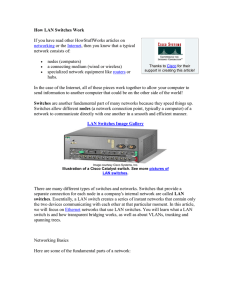
How LAN Switches Work
... Unicast - A unicast is a transmission from one node addressed specifically to another node. Multicast - In a multicast, a node sends a packet addressed to a special group address. Devices that are interested in this group register to receive packets addressed to the group. An example might be a Cisc ...
... Unicast - A unicast is a transmission from one node addressed specifically to another node. Multicast - In a multicast, a node sends a packet addressed to a special group address. Devices that are interested in this group register to receive packets addressed to the group. An example might be a Cisc ...
XORs in the Air: Practical Wireless Network Coding
... A node cannot solely rely on reception reports, and may need to guess whether a neighbor has a particular packet. To guess intelligently, we can leverage routing computations. The ETX metric computes the delivery probability between nodes and assigns each link a weight of 1/(delivery_probability) ...
... A node cannot solely rely on reception reports, and may need to guess whether a neighbor has a particular packet. To guess intelligently, we can leverage routing computations. The ETX metric computes the delivery probability between nodes and assigns each link a weight of 1/(delivery_probability) ...
Stirling-Photonic ne.. - School of Electrical Engineering and
... Individually reserved slots (reservation requires round-trip delay between edge node and switch) Statistical multiplexing without reservation with contention for the outgoing link ...
... Individually reserved slots (reservation requires round-trip delay between edge node and switch) Statistical multiplexing without reservation with contention for the outgoing link ...
static routing
... • Convergence is when all routers' routing tables are at a state of consistency. • The network has converged when all routers have complete and accurate information about the network. • Convergence time is the time it takes routers to share information, calculate best paths, and update their routing ...
... • Convergence is when all routers' routing tables are at a state of consistency. • The network has converged when all routers have complete and accurate information about the network. • Convergence time is the time it takes routers to share information, calculate best paths, and update their routing ...
3rd Edition, Chapter 5
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
An open source user space fast path TCP/IP stack
... An open source user space fast path TCP/IP stack ...
... An open source user space fast path TCP/IP stack ...
Class Extra Routing for Chapter #6
... set of routers to learn routes to all networks in a give area known as the internetwork. • Convergence describes the time it takes a set of routers to learn of a change in the network – devices added, or being turned off, or going down by malfunction, etc. • Distance vector routing protocols general ...
... set of routers to learn routes to all networks in a give area known as the internetwork. • Convergence describes the time it takes a set of routers to learn of a change in the network – devices added, or being turned off, or going down by malfunction, etc. • Distance vector routing protocols general ...
UltraLight - Internet2
... • e-VLBI is a major thrust of UltraLight and can directly complement LHC-HEPs mode of using the network, allowing us to explore new strategies for network conditioning and bandwidth management. • The e-VLBI work under this proposal will be multi-pronged in an effort to leverage the many new capabili ...
... • e-VLBI is a major thrust of UltraLight and can directly complement LHC-HEPs mode of using the network, allowing us to explore new strategies for network conditioning and bandwidth management. • The e-VLBI work under this proposal will be multi-pronged in an effort to leverage the many new capabili ...
Data Communications and Computer Networks
... label-switching and flexibility of IP routing. Has roots in IP tag-switching. MPLS works between L2 and L3. Designed to work over different link-layer technologies- Ethernet, Frame-relay, etc. Different network protocols supported. ...
... label-switching and flexibility of IP routing. Has roots in IP tag-switching. MPLS works between L2 and L3. Designed to work over different link-layer technologies- Ethernet, Frame-relay, etc. Different network protocols supported. ...
Link Layer
... data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 5: DataLink Layer ...
... data-link layer has responsibility of transferring datagram from one node to adjacent node over a link 5: DataLink Layer ...
Internet: Act II a vision from Bell Labs
... Access Networks: FTTH, xDSL, Access Networks: 3G+/4G wireless interfaces Service frameworks: data management and service intelligence ...
... Access Networks: FTTH, xDSL, Access Networks: 3G+/4G wireless interfaces Service frameworks: data management and service intelligence ...
Lecture 6: Vector - Computer Science Division
... • Shared vs. Switched Media determines BW • HW and SW Interface to computer affects overhead, latency, bandwidth • Topologies: many to chose from, but (SW) overheads make them look alike; cost issues in topologies, DAP Spr.‘98 ©UCB 3 should not be programming issue ...
... • Shared vs. Switched Media determines BW • HW and SW Interface to computer affects overhead, latency, bandwidth • Topologies: many to chose from, but (SW) overheads make them look alike; cost issues in topologies, DAP Spr.‘98 ©UCB 3 should not be programming issue ...