CCNA 3 Module 3 Single
... states of every router in its area. • Benefits include faster convergence and improved bandwidth utilization over distance vector protocols. • May overtax low-end hardware. • Require more complex administration. © 2003, Cisco Systems, Inc. All rights reserved. ...
... states of every router in its area. • Benefits include faster convergence and improved bandwidth utilization over distance vector protocols. • May overtax low-end hardware. • Require more complex administration. © 2003, Cisco Systems, Inc. All rights reserved. ...
3rd Edition: Chapter 1
... network-layer routing • Applications require no knowledge of routes • New applications deployed without coordination with network operators or operating system vendors ...
... network-layer routing • Applications require no knowledge of routes • New applications deployed without coordination with network operators or operating system vendors ...
Defending Network-Based Services Against Denial of Service Attacks
... Over the last decade, several value-added services have been proposed for deployment in the Internet. These include multicast communication [1], quality-of-service support [2], content distribution networks [3], and denial-of-service (DoS) defense mechanisms [4]. These services provide users with an ...
... Over the last decade, several value-added services have been proposed for deployment in the Internet. These include multicast communication [1], quality-of-service support [2], content distribution networks [3], and denial-of-service (DoS) defense mechanisms [4]. These services provide users with an ...
L09_TCP_IP - Interactive Computing Lab
... Network of networks (BGP, dealing with scales) ICMP NAT (network address translation) ...
... Network of networks (BGP, dealing with scales) ICMP NAT (network address translation) ...
Link layer addressing and Ethernet
... index switch table using MAC dest address if entry found for destination then{ if dest on segment from which frame arrived then drop the frame else forward the frame on interface indicated ...
... index switch table using MAC dest address if entry found for destination then{ if dest on segment from which frame arrived then drop the frame else forward the frame on interface indicated ...
Distributed Call Admission Control for Ad Hoc Networks
... hoc networks, the centralized management of resources is not plausible. All nodes in an ad hoc network should cooperate on bandwidth allocation and resource partitioning. The ubiquitous structure of management schemes in an ad hoc network may allow destructive operation of malicious sources. Sources ...
... hoc networks, the centralized management of resources is not plausible. All nodes in an ad hoc network should cooperate on bandwidth allocation and resource partitioning. The ubiquitous structure of management schemes in an ad hoc network may allow destructive operation of malicious sources. Sources ...
chapter 10 - University of Windsor
... network. However, this requires a NAT box, that must establish its own security associations, and will not work satisfactory in a nested NAT environment in which the “outer” NAT is not controlled or trusted by the owner of the protected LAN. Internet does not make it necessary to use TCP/UDP. Only ...
... network. However, this requires a NAT box, that must establish its own security associations, and will not work satisfactory in a nested NAT environment in which the “outer” NAT is not controlled or trusted by the owner of the protected LAN. Internet does not make it necessary to use TCP/UDP. Only ...
GENIConnections
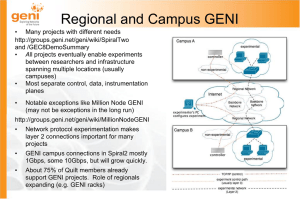
... Regional and Campus GENI • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentat ...
... Regional and Campus GENI • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentat ...
Building a Reliable Ethernet/IP Network: GSFC Prototype
... • LLC – “Logical Link Control” offers a IEEE standardized datalink layer reliability protocol, adding a 3 byte header to the ethernet frame ...
... • LLC – “Logical Link Control” offers a IEEE standardized datalink layer reliability protocol, adding a 3 byte header to the ethernet frame ...
Document
... Routing in Ad Hoc Networks Ad Hoc Network = routers are mobile o No fixed topologies o No fixed or known neighbors o Valid paths can disappear at any time o Node = router + host o Routing quite different from routing in wired networks ...
... Routing in Ad Hoc Networks Ad Hoc Network = routers are mobile o No fixed topologies o No fixed or known neighbors o Valid paths can disappear at any time o Node = router + host o Routing quite different from routing in wired networks ...
PDF (Author`s version) - OATAO (Open Archive Toulouse Archive
... For that reason, wireless mesh routing protocols are more and more optimized to consider link-quality metrics such as transmission capacity or error probability instead of simplistic hop-count metric used generally with adhoc networks. This new paradigm is called quality-aware routing The design of ...
... For that reason, wireless mesh routing protocols are more and more optimized to consider link-quality metrics such as transmission capacity or error probability instead of simplistic hop-count metric used generally with adhoc networks. This new paradigm is called quality-aware routing The design of ...
Link Layer
... Two types of “links”: point-to-point PPP (point-to-point protocol) for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) ...
... Two types of “links”: point-to-point PPP (point-to-point protocol) for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) ...
Virtual Private Network
... switching. MPLS operates by making the inter-switch transport infrastructure visible to routing and it can also be operated as a peer VPN model for switching a variety of link-layer and layer 2 switching environments. When the packets enter the MPLS, it is assigned a local label and an outbound inte ...
... switching. MPLS operates by making the inter-switch transport infrastructure visible to routing and it can also be operated as a peer VPN model for switching a variety of link-layer and layer 2 switching environments. When the packets enter the MPLS, it is assigned a local label and an outbound inte ...
Mobiiliverkot ja liikkuvuuden hallinta
... • Updates to places that have no reads must be eliminated or at least minimized. ...
... • Updates to places that have no reads must be eliminated or at least minimized. ...
Ad hoc and Sensor Networks Chapter 11: Routing protocols
... Option 1: Routing protocol always tries to keep its routing data up-to-date Protocol is proactive (active before tables are actually needed) or table-driven ...
... Option 1: Routing protocol always tries to keep its routing data up-to-date Protocol is proactive (active before tables are actually needed) or table-driven ...
network
... • path determination: route taken by packets from source to dest. Routing algorithms • forwarding: move packets from router’s input to appropriate router output • call setup: some network architectures require router call setup along path before data flows (not Internet) ...
... • path determination: route taken by packets from source to dest. Routing algorithms • forwarding: move packets from router’s input to appropriate router output • call setup: some network architectures require router call setup along path before data flows (not Internet) ...
IP Multicast
... messages with its end-router R. • The end-router R broadcasts its group membership to the whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,].
• A sender simply sends data packets as they are available.
...
... messages with its end-router R. • The end-router R broadcasts its group membership to the whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,
FPL-3: towards language support for distributed packet processing
... This paper builds on the idea of traffic splitting that was advocated by Markatos et al. in [3] and Kruegel et al. in [4] for intrusion detection. However, we use it to provide a generic high-speed packet processing environment. Markatos et al. focus on packet header processing and automatically gen ...
... This paper builds on the idea of traffic splitting that was advocated by Markatos et al. in [3] and Kruegel et al. in [4] for intrusion detection. However, we use it to provide a generic high-speed packet processing environment. Markatos et al. focus on packet header processing and automatically gen ...
Firewalls
... packet. If the packet, according to the rules defined, is allowed to pass, it is passed silently. If not, it is simply dropped and does not make it through. » Although typically built upon standard operating systems as well, these types of firewalls are also useful to build into dedicated network de ...
... packet. If the packet, according to the rules defined, is allowed to pass, it is passed silently. If not, it is simply dropped and does not make it through. » Although typically built upon standard operating systems as well, these types of firewalls are also useful to build into dedicated network de ...
chap05
... bits coming in one link go out all other links at same rate all nodes connected to hub can collide with one another no frame buffering no CSMA/CD at hub: host NICs detect collisions twisted pair ...
... bits coming in one link go out all other links at same rate all nodes connected to hub can collide with one another no frame buffering no CSMA/CD at hub: host NICs detect collisions twisted pair ...
3rd Edition, Chapter 5
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! Reliable delivery between adjacent nodes we learned how to do this already (chapter 3)! seldom used on low b ...
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! Reliable delivery between adjacent nodes we learned how to do this already (chapter 3)! seldom used on low b ...