What is TCP Connection Forwarding? Why should I perform TCP
... data paths to ensure high availability, creating multiple paths from one network node to another so that no single failure along the way blocks communication between them. If achieving this in the network includes load balancing network traffic between routers, or if your network relies on Internet ...
... data paths to ensure high availability, creating multiple paths from one network node to another so that no single failure along the way blocks communication between them. If achieving this in the network includes load balancing network traffic between routers, or if your network relies on Internet ...
MuON: Epidemic Based Mutual Anonymity
... sponder from the initiator and adversary. Mutual anonymity provides both initiator anonymity and responder anonymity. Unlinkability of initiator and responder means that the initiator and responder cannot be identified as communicating with each other, even though they can be identified as participa ...
... sponder from the initiator and adversary. Mutual anonymity provides both initiator anonymity and responder anonymity. Unlinkability of initiator and responder means that the initiator and responder cannot be identified as communicating with each other, even though they can be identified as participa ...
routing concepts and theory
... not refer to bronchial condition connectionless routers have only so many buffers, too many packets, they drop them things get worse at the “freeway exchanges” does routing protocol add congestion burden? how do we prevent/detect congestion? obviously circuit-switches don’t have this probl ...
... not refer to bronchial condition connectionless routers have only so many buffers, too many packets, they drop them things get worse at the “freeway exchanges” does routing protocol add congestion burden? how do we prevent/detect congestion? obviously circuit-switches don’t have this probl ...
Chapter 6 slides, Computer Networking, 3rd edition
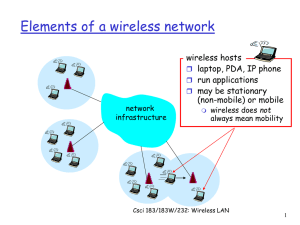
... (Mobile Ad hoc Networks) working group Csci 183/183W/232: Wireless LAN ...
... (Mobile Ad hoc Networks) working group Csci 183/183W/232: Wireless LAN ...
Internet Engineering Task Force ... Internet-Draft ...
... components described in a large number of separate documents can be brought together within a single architecture to provide the function necessary for ABNO. In many cases, existing protocols are known to be good enough or almost good enough to satisfy the requirements of interfaces between the comp ...
... components described in a large number of separate documents can be brought together within a single architecture to provide the function necessary for ABNO. In many cases, existing protocols are known to be good enough or almost good enough to satisfy the requirements of interfaces between the comp ...
pptx
... connectivity to hubs was fairly uniform across individuals. For example, the space of possible fingerprints at distance 1 for Hepth and Nettrace is 210= 1024. Of these, only 23 distinct fingerprints were observed for Hepth and only 46 for Nettrace. hubs themselves stand out, but have high-degrees, t ...
... connectivity to hubs was fairly uniform across individuals. For example, the space of possible fingerprints at distance 1 for Hepth and Nettrace is 210= 1024. Of these, only 23 distinct fingerprints were observed for Hepth and only 46 for Nettrace. hubs themselves stand out, but have high-degrees, t ...
The Open Network Operating System
... Open Network Operating System (ONOS) is an open source Software-Defined Network (SDN) operating system... What is SDN? Why do we need a network OS? ...
... Open Network Operating System (ONOS) is an open source Software-Defined Network (SDN) operating system... What is SDN? Why do we need a network OS? ...
Linux and Shell Programming
... How is datagram delivered? The source maps the nearest router’s IP address into a physical address, encapsulates the datagram in a frame, and sends the frame to the router The router extracts the datagram and selects the next router on the path towards the destination Datagram is again placed in ...
... How is datagram delivered? The source maps the nearest router’s IP address into a physical address, encapsulates the datagram in a frame, and sends the frame to the router The router extracts the datagram and selects the next router on the path towards the destination Datagram is again placed in ...
Chapter 10
... connectionless protocols are also critical to ensure that data is properly transmitted to its destination. This module will provide an overview for each. The difference between routing and routed protocols is a common source of confusion for students learning networking. The two words sound similar ...
... connectionless protocols are also critical to ensure that data is properly transmitted to its destination. This module will provide an overview for each. The difference between routing and routed protocols is a common source of confusion for students learning networking. The two words sound similar ...
Abstract- The field of Mobile Ad hoc Networks
... However, AODV adopts traditional routing tables; one entry per destination which is in contrast to DSR that maintains multiple route cache entries for each destination. The initial design of AODV is undertaken after the experience with DSDV routing algorithm. Like DSDV, AODV provides loop free route ...
... However, AODV adopts traditional routing tables; one entry per destination which is in contrast to DSR that maintains multiple route cache entries for each destination. The initial design of AODV is undertaken after the experience with DSDV routing algorithm. Like DSDV, AODV provides loop free route ...
Slide 1
... increases, so too does the number of network routes. These IPv4 routes consume a great deal of memory and processor resources on Internet routers. ...
... increases, so too does the number of network routes. These IPv4 routes consume a great deal of memory and processor resources on Internet routers. ...
Chapter
... information they use for prediction, and the purpose for which the prediction results are used. In [6] a link availability estimation mechanism was proposed. This mechanism predicts the probability that an active link between two nodes will be continuously available for a predicted time period. The ...
... information they use for prediction, and the purpose for which the prediction results are used. In [6] a link availability estimation mechanism was proposed. This mechanism predicts the probability that an active link between two nodes will be continuously available for a predicted time period. The ...
MPLS Architecture
... – With pure datagram routing, overhead of carrying complete explicit route is prohibitive – MPLS allows explicit route to be carried only at the time the LSP is setup, and not with each packet – MPLS makes explicit routing practical ...
... – With pure datagram routing, overhead of carrying complete explicit route is prohibitive – MPLS allows explicit route to be carried only at the time the LSP is setup, and not with each packet – MPLS makes explicit routing practical ...
D - OpenFlow
... Issues are when considered as a unified architecture and control plane • control plane complexity escalates when unifying across packets and circuits because it • makes basic assumption that the packet network remains same: IP/MPLS network – many years of legacy L2/3 baggage • and that the transport ...
... Issues are when considered as a unified architecture and control plane • control plane complexity escalates when unifying across packets and circuits because it • makes basic assumption that the packet network remains same: IP/MPLS network – many years of legacy L2/3 baggage • and that the transport ...
Networking Overview
... incrementally develop sender, receiver sides of reliable data transfer protocol (rdt) ...
... incrementally develop sender, receiver sides of reliable data transfer protocol (rdt) ...
CTP: An Efficient, Robust, and Reliable Collection Tree Protocol for
... react in tens of milliseconds to topology changes, while sending a few control packets per hour when the topology is stable. Third, routing inconsistencies must be detected at the same time scale as data packet transmission. We use the datapath to validate the routing topology as well as detect loop ...
... react in tens of milliseconds to topology changes, while sending a few control packets per hour when the topology is stable. Third, routing inconsistencies must be detected at the same time scale as data packet transmission. We use the datapath to validate the routing topology as well as detect loop ...
Intro_to_SS7_Tutorial_Intro to SS7 Signalling
... Type E—Extended Links (connects SSPs to alternate or remote STPs for increased resiliance and load sharing) An “E” (extended) link connects an SSP to an alternate STP. E links provide an alternate signaling path if an SSP’s home STP cannot be reached via an A link. E links are not usually provisione ...
... Type E—Extended Links (connects SSPs to alternate or remote STPs for increased resiliance and load sharing) An “E” (extended) link connects an SSP to an alternate STP. E links provide an alternate signaling path if an SSP’s home STP cannot be reached via an A link. E links are not usually provisione ...
MoreOnONOS - CSE Labs User Home Pages
... In distributed control plane, each router makes its own decision based on old info from other parts of the network: it works fine But in the current distributed control plane, destination-based, shortest path routing is used; this guarantees eventual consistency of routing tables computed by eac ...
... In distributed control plane, each router makes its own decision based on old info from other parts of the network: it works fine But in the current distributed control plane, destination-based, shortest path routing is used; this guarantees eventual consistency of routing tables computed by eac ...