EX4300 Ethernet Switch
... Mesh Virtual Chassis Configurations for the Data Center In data center top-of-rack deployments, a full mesh five-switch Virtual Chassis configuration can be created where every switch member is just one hop away from every other member, delivering the lowest possible latency. A mesh spanning distanc ...
... Mesh Virtual Chassis Configurations for the Data Center In data center top-of-rack deployments, a full mesh five-switch Virtual Chassis configuration can be created where every switch member is just one hop away from every other member, delivering the lowest possible latency. A mesh spanning distanc ...
IP Address
... • Kay concepts is to allocate multiple IP address in the way that allow summarization into a smaller number of routing table (route aggregate) • CIDR is supported by BGP4 and based on route aggregation – 16 class C addresses can be summarized to a single routing entry (router can hold a single route ...
... • Kay concepts is to allocate multiple IP address in the way that allow summarization into a smaller number of routing table (route aggregate) • CIDR is supported by BGP4 and based on route aggregation – 16 class C addresses can be summarized to a single routing entry (router can hold a single route ...
A DoS-limiting Network Architecture
... Security based on inability of attacker to gain capabilities for routers along path to destination. Hashing scheme uses a sufficiently small key that changes every 128 sec. Breaking the key is practically impossible. Attacker may observe pre-capabilities in requests by routers. Stolen capabi ...
... Security based on inability of attacker to gain capabilities for routers along path to destination. Hashing scheme uses a sufficiently small key that changes every 128 sec. Breaking the key is practically impossible. Attacker may observe pre-capabilities in requests by routers. Stolen capabi ...
Towards Complete Node Enumeration in a Peer-to
... as firewall. This limitation to crawling can be significant, as many bot-infected machines can be behind a NAT or firewalls in both homes and offices. Thus, crawler-based enumeration alone would miss a large portion of botnet infections. Therefore, we sought to find an enumeration method that can id ...
... as firewall. This limitation to crawling can be significant, as many bot-infected machines can be behind a NAT or firewalls in both homes and offices. Thus, crawler-based enumeration alone would miss a large portion of botnet infections. Therefore, we sought to find an enumeration method that can id ...
Campus LAN Reference Design
... Campus LAN Design with Avaya Fabric Connect This design uses Avaya Fabric Connect in order to provide benefits over traditional campus LAN design. Fabric Connect, built upon shortest path bridging (SPB), was originally built as a replacement for older STPs, removing many of the shortcomings of exist ...
... Campus LAN Design with Avaya Fabric Connect This design uses Avaya Fabric Connect in order to provide benefits over traditional campus LAN design. Fabric Connect, built upon shortest path bridging (SPB), was originally built as a replacement for older STPs, removing many of the shortcomings of exist ...
PDF
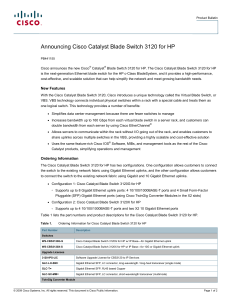
... Available with Cisco IOS Software and the IP Base image, the Cisco Catalyst Blade Switch 3120 products offer a complete set of intelligent services to deliver security, quality of service (QoS), and high availability in the server farm access environment. The IP Base feature set includes advanced Qo ...
... Available with Cisco IOS Software and the IP Base image, the Cisco Catalyst Blade Switch 3120 products offer a complete set of intelligent services to deliver security, quality of service (QoS), and high availability in the server farm access environment. The IP Base feature set includes advanced Qo ...
ppt
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... VRF is maintained for each customer site, hence there no chance of security breach as all the customers are well segregated) and scalable (no complete mesh between customer sites is required), so it is now the need of service provider to implement. Its ability of combining the plus points of overlay ...
... VRF is maintained for each customer site, hence there no chance of security breach as all the customers are well segregated) and scalable (no complete mesh between customer sites is required), so it is now the need of service provider to implement. Its ability of combining the plus points of overlay ...
IP: Addresses and Forwarding
... consistent while the rest may be inconsistent. Large networks => inconsistency is a scalability issue. Consistency can be achieved in two ways: Fully distributed approach: a consistency criterion or invariant across the states of adjacent nodes Signaled approach: the signaling protocol sets up ...
... consistent while the rest may be inconsistent. Large networks => inconsistency is a scalability issue. Consistency can be achieved in two ways: Fully distributed approach: a consistency criterion or invariant across the states of adjacent nodes Signaled approach: the signaling protocol sets up ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... network interface straight from application space, and ability for applications to exchange data directly between their own virtual buffers across a network, all without involving the operating system. The idea behind InfiniBand is simple; it provides applications a - messaging service. This service ...
... network interface straight from application space, and ability for applications to exchange data directly between their own virtual buffers across a network, all without involving the operating system. The idea behind InfiniBand is simple; it provides applications a - messaging service. This service ...
Outline - Purdue Computer Science
... Initialization Discover neighbors within cluster range Compute the initial cluster head probability CHprob = f(Er/Emax) ...
... Initialization Discover neighbors within cluster range Compute the initial cluster head probability CHprob = f(Er/Emax) ...
Paper Title (use style: paper title)
... supporting SDN and legacy routing protocol improves the flexibility of the route compared with the pure IGP network[2]; secondly, it has the ability of deploying the advanced network (such as anti-spoofing and traffic engineering)[3]; thirdly, it combines the flexibility of SDN and the expansibility ...
... supporting SDN and legacy routing protocol improves the flexibility of the route compared with the pure IGP network[2]; secondly, it has the ability of deploying the advanced network (such as anti-spoofing and traffic engineering)[3]; thirdly, it combines the flexibility of SDN and the expansibility ...
Multicast Session Announcements on top of SSM
... is bursty and its announcement period is larger then the life time of the corresponding multicast forwarding states in the routers. Therefore, when an sdr tool sends out announcements, these announcements create a considerable amount of control traffic in the network. First, the active source inform ...
... is bursty and its announcement period is larger then the life time of the corresponding multicast forwarding states in the routers. Therefore, when an sdr tool sends out announcements, these announcements create a considerable amount of control traffic in the network. First, the active source inform ...
Industrial Ethernet Switching
... access a common database which, in turn, saves data entry costs and ensures consistency throughout the project. Availability and performance The demand for high network availability for a high-performance network in the various automation applications is rising continuously. Different topologies suc ...
... access a common database which, in turn, saves data entry costs and ensures consistency throughout the project. Availability and performance The demand for high network availability for a high-performance network in the various automation applications is rising continuously. Different topologies suc ...
Importance of IP Alias Resolution in Sampling Internet Topologies
... Understanding the topological and functional characteristics of the Internet is an important research issue. This understanding is not simply an intellectual curiosity but also a necessity to better design, implement, and operate the underlying network technologies, protocols, and services. In respo ...
... Understanding the topological and functional characteristics of the Internet is an important research issue. This understanding is not simply an intellectual curiosity but also a necessity to better design, implement, and operate the underlying network technologies, protocols, and services. In respo ...
FS3610481053
... time used to discover a new network, obtain and validate a new COA(identifies the current location of the mobile node), obtain authorization to access the new network, make the decision that a handoff should be initiated, and ,finally, execute the handoff, which involves notifying the home agent of ...
... time used to discover a new network, obtain and validate a new COA(identifies the current location of the mobile node), obtain authorization to access the new network, make the decision that a handoff should be initiated, and ,finally, execute the handoff, which involves notifying the home agent of ...
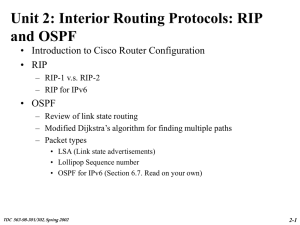
TDC 563-98-301/302, Spring 2002 2-14 TDC 563-98
... •RIP-1 supports subnet routes only within the subnetted network (suing single subnet mask) •RIP-2 includes subnet mask in the messages. This allows for subnet knowledge outside subnet Distinguish •More convenient partitioning using variable-length subnets ...
... •RIP-1 supports subnet routes only within the subnetted network (suing single subnet mask) •RIP-2 includes subnet mask in the messages. This allows for subnet knowledge outside subnet Distinguish •More convenient partitioning using variable-length subnets ...
Research on Routing in Mobile/Wireless Ad
... Without fixed network interaction and centralized administration. Multi-hop routing style with no cheating of the forwarding nodes ...
... Without fixed network interaction and centralized administration. Multi-hop routing style with no cheating of the forwarding nodes ...