Industrial Ethernet Switches
... message frames can be in transit at the same time. The performance gain is due to the simultaneity of several message frames. The switching technology offers definite advantages over shared LAN • Switches can be used to construct subnets and network segments • Data throughput and network performance ...
... message frames can be in transit at the same time. The performance gain is due to the simultaneity of several message frames. The switching technology offers definite advantages over shared LAN • Switches can be used to construct subnets and network segments • Data throughput and network performance ...
HomePlug 1.0 Technology White Paper
... Internet data within the home increases continuously. While retrofitting the house with special wires is one option, it is expensive and time consuming. With multiple outlets in every room, residential powerlines are already the most pervasive network in the home. HomePlug standards allow the use of ...
... Internet data within the home increases continuously. While retrofitting the house with special wires is one option, it is expensive and time consuming. With multiple outlets in every room, residential powerlines are already the most pervasive network in the home. HomePlug standards allow the use of ...
Error checking and Ethernet
... • Multiple Access: various nodes share a common transmission line. • Collision Detect: simultaneously transmitted packets are detected, discarded and retransmitted. CSIT 220 (Blum) ...
... • Multiple Access: various nodes share a common transmission line. • Collision Detect: simultaneously transmitted packets are detected, discarded and retransmitted. CSIT 220 (Blum) ...
IP Routing - courses.psu.edu
... • has maximum allowable hop count of 15 • is inefficient on large networks • uses three different timers – route update timer – route invalid timer – flush timer ...
... • has maximum allowable hop count of 15 • is inefficient on large networks • uses three different timers – route update timer – route invalid timer – flush timer ...
User Manual
... 245U-E Wireless Ethernet Modem User Manual recommended in the Installation Guide. 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the 245U-E module during these adjustments. Equipment should carry clear markin ...
... 245U-E Wireless Ethernet Modem User Manual recommended in the Installation Guide. 4. To avoid accidents during maintenance or adjustment of remotely controlled equipment, all equipment should be first disconnected from the 245U-E module during these adjustments. Equipment should carry clear markin ...
Emulation of RDRN on an ATM-Testbed and a Comparative
... IP over ATM specification says that the MTU cannot be larger than 9180 bytes; hence the CLIP can pass a packet of the above size to the “glue_layer”. Hence, when the DLC layer would attach its own header and trailer, it would cause an overflow on the ENI card. In the above case the segmentation ...
... IP over ATM specification says that the MTU cannot be larger than 9180 bytes; hence the CLIP can pass a packet of the above size to the “glue_layer”. Hence, when the DLC layer would attach its own header and trailer, it would cause an overflow on the ENI card. In the above case the segmentation ...
M T ASTER'S HESIS
... IP multicast routing [2] is a network layer mechanism that provides resource-efficient communication services for applications that send the same data to multiple recipients simultaneously. The source transmits a single copy of the data; an intermediate router makes a copy of each incoming multicast ...
... IP multicast routing [2] is a network layer mechanism that provides resource-efficient communication services for applications that send the same data to multiple recipients simultaneously. The source transmits a single copy of the data; an intermediate router makes a copy of each incoming multicast ...
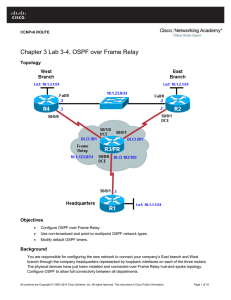
Chapter 3 Lab 3-4, OSPF over Frame Relay
... Use non-broadcast and point-to-multipoint OSPF network types. ...
... Use non-broadcast and point-to-multipoint OSPF network types. ...
- IEEE Mentor
... FILS authentication number, both the STA and AP’s shall transition to FILS Authenticated state STA at FILS Authenticated State , it allows Class 1,2 and selected Data frames piggybacked over Class 1 &2 frames to be transmitted Upon receipt of a De-association frame from either STA or AP STA with rea ...
... FILS authentication number, both the STA and AP’s shall transition to FILS Authenticated state STA at FILS Authenticated State , it allows Class 1,2 and selected Data frames piggybacked over Class 1 &2 frames to be transmitted Upon receipt of a De-association frame from either STA or AP STA with rea ...
Campus Network Design
... with if/then style algorithms. • For route-maps with the keyword “permit”, if the prefix being examined passes the match statement, the set commands are executed and the route-map is exited. • If the match statement is not passed, the next sequence number is executed. • If there are no more sequence ...
... with if/then style algorithms. • For route-maps with the keyword “permit”, if the prefix being examined passes the match statement, the set commands are executed and the route-map is exited. • If the match statement is not passed, the next sequence number is executed. • If there are no more sequence ...
On the Optimal Path Length for Tor
... a decentralized architecture of precisely three routers to mitigate any single router’s ability to link a source and destination. However, three-hop paths have a performance cost. In this paper, we seek to better understand the security and performance trade-offs related to path length design decisi ...
... a decentralized architecture of precisely three routers to mitigate any single router’s ability to link a source and destination. However, three-hop paths have a performance cost. In this paper, we seek to better understand the security and performance trade-offs related to path length design decisi ...
Redes Inalámbricas
... [1] “Bandwidth Reservation in Multihop Wireless Networks: Complexity and Mechanisms”. ICDCSW'04, ...
... [1] “Bandwidth Reservation in Multihop Wireless Networks: Complexity and Mechanisms”. ICDCSW'04, ...
2930F TAA Switch Series Data Sheet
... • Jumbo packet support improves the performance of large data transfers; supports frame size of up to 9,220 bytes • IEEE 802.1v protocol VLANs isolate select non-IPv4 protocols automatically into their own VLANs • Rapid Per-VLAN Spanning Tree (RPVST+) allows each VLAN to build a separate spanning tr ...
... • Jumbo packet support improves the performance of large data transfers; supports frame size of up to 9,220 bytes • IEEE 802.1v protocol VLANs isolate select non-IPv4 protocols automatically into their own VLANs • Rapid Per-VLAN Spanning Tree (RPVST+) allows each VLAN to build a separate spanning tr ...
Chapter 3 Dynamic Routing Protocols
... The operations of a dynamic routing protocol vary depending on the type of routing protocol, but in general: 1. The router shares routing messages and routing information with other routers that are using the same routing protocol. 2. The router sends and receives routing messages on its interfaces. ...
... The operations of a dynamic routing protocol vary depending on the type of routing protocol, but in general: 1. The router shares routing messages and routing information with other routers that are using the same routing protocol. 2. The router sends and receives routing messages on its interfaces. ...
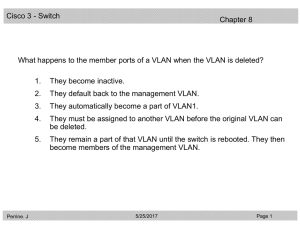
1 Refer to the exhibit. What happens to a packet that has 172.16.0.0
... • The packet will be forwarded to the gateway of last resort. • The packet will match the 192.168.0.0 network and be forwarded out Serial 0/0. • The packet will most closely match the 192.168.0.8 subnet and be forwarded out Serial 0/1. 2. Which three statements are true of holddown timers? (Choose t ...
... • The packet will be forwarded to the gateway of last resort. • The packet will match the 192.168.0.0 network and be forwarded out Serial 0/0. • The packet will most closely match the 192.168.0.8 subnet and be forwarded out Serial 0/1. 2. Which three statements are true of holddown timers? (Choose t ...
Address Resolution Protocol
... addresses so that IP packets can be sent across networks. Before a device sends a datagram to another device, it looks in its ARP cache to see if there is a MAC address and corresponding IP address for the destination device. If there is no entry, the source device sends a broadcast message to every ...
... addresses so that IP packets can be sent across networks. Before a device sends a datagram to another device, it looks in its ARP cache to see if there is a MAC address and corresponding IP address for the destination device. If there is no entry, the source device sends a broadcast message to every ...
wireless mesh networks
... uniquely identify a RREQ. – Along with its own sequence number and broadcast ID, the source node includes in the RREQ the most recent sequence number it has for the destination. ...
... uniquely identify a RREQ. – Along with its own sequence number and broadcast ID, the source node includes in the RREQ the most recent sequence number it has for the destination. ...
TCP, IGP, EGP etc. - La Salle University
... The packet is bounced around like a "hot potato," sometimes moving further away from its destination because it has to keep moving through the network. This technique allows multiple packets to reach their destinations without being dropped. This is in contrast to "store and forward" routing where t ...
... The packet is bounced around like a "hot potato," sometimes moving further away from its destination because it has to keep moving through the network. This technique allows multiple packets to reach their destinations without being dropped. This is in contrast to "store and forward" routing where t ...
Chapter 5 - Ethernet
... ARP Role in Remote Communication If the destination IPv4 host is on the local network, the frame will use the MAC address of this device as the destination MAC address If the destination IPv4 host is not on the local network, the source uses the ARP process to determine a MAC address for the rou ...
... ARP Role in Remote Communication If the destination IPv4 host is on the local network, the frame will use the MAC address of this device as the destination MAC address If the destination IPv4 host is not on the local network, the source uses the ARP process to determine a MAC address for the rou ...
Chapter 4
... • The VC network came about because of its similarity to telephone networks • But the Internet was connecting complex computers, so the datagram network was created because the computers could handle more complex operations than the routers (recall our IMP friends from Chapter 1) – This also makes i ...
... • The VC network came about because of its similarity to telephone networks • But the Internet was connecting complex computers, so the datagram network was created because the computers could handle more complex operations than the routers (recall our IMP friends from Chapter 1) – This also makes i ...