* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 4
Distributed firewall wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Computer network wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
INFO 330
Computer Networking
Technology I
Chapter 4
The Network Layer
Glenn Booker
INFO 330 Chapter 4
1
www.ischool.drexel.edu
The Network Layer
• So, the transport layer provides
process to process communication
• The network layer is expected to provide
host to host communication
• Cool.
• Um, how?
INFO 330 Chapter 4
2
www.ischool.drexel.edu
The Network Layer
• The Network Layer has to do two things:
– Forwarding is the process within a single
router to determine which outgoing link a
packet has to take
– Routing is the process (and algorithm) of
choosing the best path (route) between
source and destination
• Forwarding is like deciding which turn to make
at one intersection
• Routing is deciding which roads to take
INFO 330 Chapter 4
3
www.ischool.drexel.edu
The Network Layer
• Recall the network layer is expected to
– Receive segments from the transport layer
– Encapsulate them into datagrams (how much does data weigh?)
– And pass them through the network
• The job of most routers is to look at the network
header information, and determine which link to
pass the datagram
– The application and transport layer information are
invisible and irrelevant to routers
INFO 330 Chapter 4
4
www.ischool.drexel.edu
The Network Layer
• A router has a forwarding table which tells
which link to take, based on the header’s
destination address
• The forwarding table is written based on
output from a routing algorithm
– Routing algorithms may be centrally
controlled and then downloaded to each
router; or each router may follow their own
algorithm
INFO 330 Chapter 4
5
www.ischool.drexel.edu
The Network Layer
• A packet switch is a device that transfers a
packet from an input link to an output link
– Some are link-layer switches, which use the
link layer header info
– The rest we call routers, which use network
layer header info
• Another function in the network layer can
be connection setup
– Only for virtual circuit networks (ATM, X.25)
INFO 330 Chapter 4
6
www.ischool.drexel.edu
Network Service Model
• What services could we expect from a
network layer?
– Guaranteed delivery of all packets
– Delivery within a specified time (bounded delay)
– Delivery of packets in order
– Guaranteed minimal bandwidth
– Guaranteed maximum jitter (delay variation)
– Security services
•
Would be nice, huh?
INFO 330 Chapter 4
7
www.ischool.drexel.edu
Network Service Model
• What do we get from the Internet?
– Best-effort service
• Meaning, none of the above!!
• Some VC networks, such as ATM, can
provide many of the ideal services
(see p. 312)
– Constant Bit Rate (CBR) and Available Bit
Rate (ABR) are types of ATM service
INFO 330 Chapter 4
8
www.ischool.drexel.edu
Network Service Model
• Refining our earlier definition, the network
layer can provide connection-based or
connection-less service
– A network that provides only a connectionbased service at the network layer is a virtual
circuit (VC) network
– A network that provides only connectionless
service at the network layer is a
datagram network
INFO 330 Chapter 4
9
www.ischool.drexel.edu
Virtual Circuit Networks
• A VC Network needs to have
– A path from source to destination
– VC numbers, one per link along the path
– Entries in the forwarding table in each router along
the path
• Each packet carries a VC number which
changes as it goes along each link in the VC
– This keeps from having to store and coordinate VC
numbers across routers
INFO 330 Chapter 4
10
www.ischool.drexel.edu
Virtual Circuit Networks
• Each router has to know the VC numbers
for incoming and outgoing links (4 columns)
Incoming Link # Incoming VC#
and
Outgoing Link # Outgoing VC #
• Each foursome of in/out link and VC numbers
corresponds to how one VC is handled in that
router; so each VC being created adds one row
of data (which is later deleted)
INFO 330 Chapter 4
11
www.ischool.drexel.edu
Virtual Circuit Networks
• So a simple VC might have VC# 12 on the
first link, then get VC# 22 on the second
link, and VC# 37 on the third
– Routers must keep this state information
• So the life of a VC connection includes
– VC setup – the network layer defines the
routers in the VC, sets VC numbers for each
link, and creates new entries in the forwarding
table of each router
INFO 330 Chapter 4
12
www.ischool.drexel.edu
Virtual Circuit Networks
– Data transfer is the intended purpose of the
VC connection
– VC teardown is when sender or receiver tells
the VC it wants to end the connection; then
the forwarding tables are updated to remove
the entries associated with this VC
• Notice that VC setup and teardown involve
the hosts and all routers along the path,
whereas TCP only involved the hosts
INFO 330 Chapter 4
13
www.ischool.drexel.edu
Virtual Circuit Networks
• The messages to set up and tear down a
VC are signaling messages, which have
their own protocols, e.g. ATM’s Q.2931
– No, we’re not going to dissect them
– *yippee*
INFO 330 Chapter 4
14
www.ischool.drexel.edu
Datagram Networks
• Datagram networks stamp each packet
with the address of the destination host,
and send it into the network
– There is no state information about
connections, because there aren’t any
connections within the network!
INFO 330 Chapter 4
15
www.ischool.drexel.edu
Datagram Networks
• Each router between hosts uses the
address to forward the packet using a
forwarding table
– If our addresses had 32 bits, there could be
4,294,967,296 entries in that table!
INFO 330 Chapter 4
16
www.ischool.drexel.edu
Datagram Networks
• Fortunately, we don’t need to look at ALL
of the address to determine its correct link
(a key observation!)
– Instead, match the address’ prefix with
forwarding table entries
– Use the longest prefix matching rule
• Match the longest prefix possible in the
forwarding table
• For this to be practical, large ranges of addresses
should go to each link, or the table will be huge!
INFO 330 Chapter 4
17
www.ischool.drexel.edu
Longest prefix matching rule
• The router just finds the longest prefix and
uses that entry in the routing table to
forward the packet
Prefix
Link
11001000 00010111 00010
0
11001000 00010111 00011000
1
11001000 00010111 00011
2
Otherwise
3
INFO 330 Chapter 4
18
www.ischool.drexel.edu
Datagram Networks
• So even though there is no connection
data, routers in datagram networks need
to maintain the forwarding tables
– The routing algorithm typically updates them
every 1-5 minutes
– Hence it’s quite possible for the later packets
of a long session to follow a different path
than the earlier packets!
INFO 330 Chapter 4
19
www.ischool.drexel.edu
More History
• The VC network came about because of
its similarity to telephone networks
• But the Internet was connecting complex
computers, so the datagram network was
created because the computers could handle
more complex operations than the routers
(recall our IMP friends from Chapter 1)
– This also makes it easier to connect dissimilar
networks, and create many new applications
– “Hosts are smart, routers are stupid”
INFO 330 Chapter 4
20
www.ischool.drexel.edu
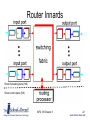
Router Innards
• Now look at forwarding in more detail
• A router has four kinds of parts
– Input ports
– Output ports
– Switch fabric between the inputs and outputs
– And a routing processor to control the switch
fabric, using the routing protocols
INFO 330 Chapter 4
21
www.ischool.drexel.edu
Router Innards
Router forwarding plane (HW)
Router control plane (SW)
INFO 330 Chapter 4
22
www.ischool.drexel.edu
Router
• Notice that the router forwarding plane is
done in hardware to speed processing
– For a 10 Gbps connection and 64-byte
datagrams, the input port only has 51.2 ns to
process each packet!
• In contrast, router control plane functions
(processing) is done at the ms time scale
or slower, so they can be executed on a
traditional CPU
INFO 330 Chapter 4
23
www.ischool.drexel.edu
Router Innards
• The input and output ports include
– The physical connection to the network, and
– Take the signal through the data link layer
• The input ports also look up the
destination address, decides how to
forward the packet, and creates control
packets to send to the routing processor
– The three boxes represent the physical layer,
data link layer, and lookup/forward module
INFO 330 Chapter 4
24
www.ischool.drexel.edu
Input Ports
• The routing processor determines the
forwarding table contents, and shadow
copies it to each input port
– This avoids a processing bottleneck
• Looking up where to forward packets is
simple in concept – the challenge is
maintaining line speed
– Want to process each packet in less time
than it takes to receive the next one
INFO 330 Chapter 4
25
www.ischool.drexel.edu
Switching Fabric
• The input ports determine the output port
needed; switching fabric makes it happen
• Many approaches for switching fabric have
been used
– Switching via memory uses the CPU directly
– Switching via bus makes every packet go
over a bus before getting off at the correct
output; very slow
INFO 330 Chapter 4
26
www.ischool.drexel.edu
Switching Fabric
– Switching via interconnect network uses 2*n
horizontal and vertical buses to connect n
inputs to n outputs; but this can produce
blockages
– Lots of other approaches have been used
• Switches handle staggering data rates
(e.g. 60 Tbps for the Cisco Nexus 9516),
so their technology is constantly being
pushed
INFO 330 Chapter 4
27
www.ischool.drexel.edu
Switching Fabric Approaches
INFO 330 Chapter 4
28
www.ischool.drexel.edu
Output Ports
• The output ports take packets from the
output port memory (queue) and transmit
them over the outgoing link
• Hence the three functions of output ports
are
– Queuing
– Data link processing
– Physical line termination
INFO 330 Chapter 4
29
www.ischool.drexel.edu
Queuing
• We’ve discussed buffers in connection
with output ports, but they also exist
with input ports
• Packet loss can occur at input or output
queues, depending on
– Input traffic load
– Switching fabric speed
– Line speed
INFO 330 Chapter 4
30
www.ischool.drexel.edu
Switching Fabric Speed
• For a router with n input and n output ports
• If the switching fabric has a speed n times as
fast as the input line speed, no queuing can
occur at the inputs
– But the output ports can easily become overloaded
if many inputs all feed the same output port
• A packet scheduler at the output port decides
which packet is next for transmission
INFO 330 Chapter 4
31
www.ischool.drexel.edu
Packet Scheduler
• The packet scheduler needs rules
– Could use first come, first served
(FCFS) approach
– Could use weighted fair queuing (WFQ)
• The packet scheduler affects the quality
of service of the connection
– More details on this in Chapter 7, which
we aren’t covering this term
INFO 330 Chapter 4
32
www.ischool.drexel.edu
Incoming Buffer
• If there’s not enough room in the buffer for
a new incoming packet, have to decide:
– Drop the new packet (called drop tail), or
– Drop an existing packet to make room
• Can also mark packets for congestion
control when buffer is getting full
• Dropping and marking strategies are
Active Queue Management (AQM)
algorithms
INFO 330 Chapter 4
33
www.ischool.drexel.edu
Incoming Buffer
• Examples of AQM algorithms include
– Random Early Detection (RED), which uses
random variables to decide when to drop or
mark a packet when buffer approaches full
• If the switch fabric is too slow, packets
have to wait in the input queue before
moving to an output queue
– Head-of-the-line (HOL) blocking is when a
packet waits for a packet to cross, even
though its output port is open
INFO 330 Chapter 4
34
www.ischool.drexel.edu
The Internet Protocol (IP)
• Now see how all this applies to the Internet
– We’ll cover both the existing IPv4 and IPv6 (versions
4 and 6)
• The network layer has three major parts
– Internet Protocol, which handles addressing
– Routing protocols (e.g. RIP, OSPF, BGP), which
choose the best path for packets
– Internet Control Message Protocol (ICMP),
which handles error reporting and signaling
INFO 330 Chapter 4
35
www.ischool.drexel.edu
Datagram Format
• A segment in the transport layer becomes
one or more datagrams in the network
layer
– First discuss IPv4, then show how IPv6
is different
INFO 330 Chapter 4
36
www.ischool.drexel.edu
Datagram Format
• The IPv4 datagram header has at least
five 4-byte (32-bit) fields, like TCP
– Version number, header length, type of service, and
datagram length in bytes
– Identifier, some flags, and fragmentation offset
– Time-to-live, upper layer protocol, and
header checksum
– Source IP address (32 bits)
– Destination IP address (32 bits)
– Then options, followed by the segment data
INFO 330 Chapter 4
37
www.ischool.drexel.edu
Datagram Format
• Version number is 4 bits for the IP version
• Header length is 4 bits for the number of bytes in
the IP header (usually 20 B)
• Type of service (TOS) is 8 bits which allow one
to specify different levels of service
(real time or not)
• Datagram length in bytes is the total of the
header plus the actual data segment
– Is a 16 bit field, but typical length is under 1500 B
INFO 330 Chapter 4
38
www.ischool.drexel.edu
Datagram Format
• The Identifier, flags, and fragmentation
offset all relate to IP fragmentation
(breaking a segment into multiple
datagrams)
• Time-to-live (TTL) is a countdown integer,
to prevent packets from wandering in the
network for 40 years
– It increments down one with each router, and
kills the datagram when it gets to zero
INFO 330 Chapter 4
39
www.ischool.drexel.edu
Datagram Format
• Protocol is the transport layer protocol
– Only used when get to the destination host
– E.g. 6=TCP, 17=UDP; see RFC 3232 for others
• Header checksum – hey, didn’t we have a
transport checksum?
– Yes, but this only covers the IP header, not the
segment data
– And TCP might be run over other network protocols,
e.g. our VC buddy, ATM
INFO 330 Chapter 4
40
www.ischool.drexel.edu
Datagram Format
• Source and destination IP addresses
we’ll discuss in more detail soon
• Option fields allow for rarely used
functions, but slow IP processing
– Hence these are not allowed in IPv6
• The Data in the datagram can be the
TCP or UDP segment, or contain other
message formats such as ICMP
INFO 330 Chapter 4
41
www.ischool.drexel.edu
Fragmentation
• A frame can hold up to the Maximum
Transmission Unit (MTU) bytes of data
– But not all link-layer protocols can handle the
same size packets
• Ethernet handles up to 1500 B frames
• Some WAN protocols only handle 500 B frames
• Since datagrams get passed from one
router to the next, and don’t know the path
ahead, some routers have to break up a
datagram
INFO 330 Chapter 4
42
www.ischool.drexel.edu
Fragmentation
• An IPv4 datagram can be broken into two
or more fragments
• Expect the fragments to be reassembled
by the destination host’s network layer
– Recurring theme: minimize work done
by routers
• Each initial datagram has an identification
number, in addition to the source and
destination addresses
INFO 330 Chapter 4
43
www.ischool.drexel.edu
Evil Fragmentation
• Fragmentation can be used for attacks
– Jolt2 attack: Send a lot of incomplete
fragments to a server (e.g. none have zero
offset); it’ll eventually run out of storage
and crash
– Send overlapping frags to a server;
some get confused and crash
INFO 330 Chapter 4
44
www.ischool.drexel.edu
IPv4 Addressing
• Recall that hosts have to have interfaces to the
network, over which to send datagrams
• Routers need many interfaces, since they are
connected to multiple links
• Therefore every IP address is associated with an
interface, not a host or router
– IPv4 addresses are 32 bits (4 bytes), written in dotted
decimal notation (byte.byte.byte.byte)
INFO 330 Chapter 4
45
www.ischool.drexel.edu
IPv4 Addressing
• Every Internet address visible to the must have a
unique IP address
– Local networks can hide many systems behind one IP
using network address translation (NAT)
• IP addresses are given out as hierarchically as
possible, so many local addresses have the
same prefix or subnet (leftmost bits in the IP
address)
– Subnet = IP network = network in much literature
(terms vary)
INFO 330 Chapter 4
46
www.ischool.drexel.edu
IPv4 Addressing
• How many bits of the address are used to
define the subnet is given as a suffix after
a slash, e.g. 213.1.3.0/24 means the first
24 bits of the address are the subnet mask
– Often the links of a router each point to a
different subnet, e.g. in Fig 4.15
– Subnets also can be defined for the interfaces
between routers
– A subnet is essentially an isolated part of a
larger network
INFO 330 Chapter 4
47
www.ischool.drexel.edu
Fig 4.15 – Subnet example
223.1.1.1
Subnet
223.1.1.0/24
223.1.2.1
223.1.1.2
223.1.1.4
223.1.3.27
223.1.1.3
Subnet
223.1.2.0/24
223.1.2.9
223.1.3.1
223.1.2.2
223.1.3.2
Subnet
223.1.3.0/24
INFO 330 Chapter 4
48
www.ischool.drexel.edu
Pre-CIDR
• Internet domains originally had prefixes of
– Class A=8, Class B=16, or Class C=24 bits
• Led to lots of wasted address space!
– Class A 16,777,216 hosts per domain
– Class B 64k hosts
– Class C 256 hosts
INFO 330 Chapter 4
49
www.ischool.drexel.edu
CIDR
• Now we use Classless Interdomain
Routing (CIDR, RFC 4632) to avoid that
limitation
– Any subnet of the form a.b.c.d/x can be used
– The x is called the prefix or network prefix
– Outside of the network (subnet), only the
prefix is used for routing
• The rest of the address defines hosts within
the network
Image from http://www.naturalandsustainable.com/category/hard-cider/
INFO 330 Chapter 4
50
www.ischool.drexel.edu
CIDR
• So if a prefix is of the form a.b.c.d/21,
– 21 bits of the address are the prefix
– The remaining 32-21= 11 bits are unique
to each device within that subnet
– Giving you room for 2^11 = 2048 hosts
• The a.b.c.d part of the CIDR address can
be anything that fits within the prefix length
in binary
INFO 330 Chapter 4
51
www.ischool.drexel.edu
Broadcast Address
• The IP broadcast address is a special IP
address 255.255.255.255 (or all ones,
111111111.11111111.11111111.11111111)
• When the destination address is that
value, the message goes to all hosts
within the subnet
– Routers usually won’t forward these
messages; but might
INFO 330 Chapter 4
52
www.ischool.drexel.edu
Obtaining IP Addresses
• Typically an ISP gets a block of IP addresses,
and assigns them to customers
– E.g. the ISP might get 200.23.16.0/20,
which it breaks down into smaller subnets
for each customer – 200.23.16.0/23 for one,
200.23.18.0/23 for another, etc.
– That way, routing knows anything starting with
200.23.16.0/20 goes to that ISP, and the ISP
routes it more specifically to each customer,
who then routes it to each specific host
INFO 330 Chapter 4
53
www.ischool.drexel.edu
Obtaining IP Addresses
Organization 0
200.23.16.0/23
Organization 1
200.23.18.0/23
Organization 2
200.23.20.0/23
Organization 7
.
.
.
.
.
.
Fly-By-Night-ISP
“Send me anything
with addresses
beginning
200.23.16.0/20”
Internet
200.23.30.0/23
ISPs-R-Us
“Send me anything
with addresses
beginning
199.31.0.0/16”
The use of a prefix for multiple subnets is called
address or route aggregation, or route summarization
INFO 330 Chapter 4
54
www.ischool.drexel.edu
Managing IP Addresses
• While ideally it would be nice to have a
unique subnet for everything, in reality it
gets messier – many ISPs might have
several subnet ranges assigned to them
• ICANN manages IP addresses, based
on RFC 2050, as well as managing
domain names
INFO 330 Chapter 4
55
www.ischool.drexel.edu
Getting a Host IP Address
• An organization assigns host addresses within
its subnet
– Routers have IP addresses manually assigned
• Hosts can be manually assigned, but usually use
Dynamic Host Configuration Protocol (DHCP)
– DHCP sets the host IP address, the subnet mask,
defines the first-hop router (default gateway), and
local DNS server
– DHCP is often known as a plug-and-play protocol,
because it makes network admin much easier!
INFO 330 Chapter 4
56
www.ischool.drexel.edu
DHCP
• For example, an ISP can use DHCP to
assign IP addresses to dialup customers
– Need fewer IP addresses than you have
customers, since all won’t be online at once
– Need to manage which IP addresses are in
use, and which are available to be assigned
• DHCP is also handy for mobile clients,
such as connecting to Dragonfly
INFO 330 Chapter 4
57
www.ischool.drexel.edu
DHCP
• Dynamic Host Configuration Protocol
(DHCP) makes our lives much easier
• DHCP is client/server based
– There must be at least one DHCP server to
tell everyone else what their IP addresses are
• A router can act as a DHCP relay agent,
so that multiple subnets can share one
DHCP server
INFO 330 Chapter 4
58
www.ischool.drexel.edu
DHCP
• A new host on a subnet follows a four-step
process to get an address
– DHCP server discovery – use a DHCP discover
message (using UDP, port 67) to the broadcast IP of
255.255.255.255, with a source IP of all zeros
• A relay agent will pass the message to the server
– DHCP server offer(s) – each DHCP server responds
with a DHCP offer message, including IP, network
mask, address lease time (TTL), etc.
• Many offers can be received by a host
INFO 330 Chapter 4
59
www.ischool.drexel.edu
DHCP
– DHCP request – the new host (client) chooses from
the offers, selects one, and sends a DHCP request
message to that server
– DHCP ACK – the server responds with an ACK
message, and confirms the requested parameters
• Once the client is connected with its assigned
IP, the lease can be renewed
• One minor drawback is that an IP address can’t
be kept between subnets, bad for mobile clients
INFO 330 Chapter 4
60
www.ischool.drexel.edu
Network Address Translation
• Network Address Translation (NAT) allows
local networks to define IP addresses that
are invisible to the outside world
– The NAT router looks like a device with one IP
address to the outside world, but usually uses
DHCP to assign IP addresses from private
networks to local devices
• It doesn’t have to use private networks, you could
use publicly visible IP addresses
INFO 330 Chapter 4
61
www.ischool.drexel.edu
Private networks
• NAT typically uses prefixes reserved for
private networks, per RFC 1918:
– “The Internet Assigned Numbers Authority
(IANA) has reserved the following three
blocks of the IP address space for private
internets:
• 10.0.0.0/8
• 172.16.0.0/12
• 192.168.0.0/16”
INFO 330 Chapter 4
62
www.ischool.drexel.edu
Network Address Translation
rest of
Internet
local network
(e.g., home network)
10.0.0/24
10.0.0.4
10.0.0.1
10.0.0.2
138.76.29.7
10.0.0.3
All datagrams leaving local
network have same single source
NAT IP address: 138.76.29.7,
different source port numbers
Datagrams with source or
destination in this network
have 10.0.0/24 address for
source, destination (as usual)
INFO 330 Chapter 4
63
www.ischool.drexel.edu
Network Address Translation
• The NAT router keeps a translation table
– Destination address and port number
– Source local host IP AND port number
• Hence NAT has to change the addressing
of every datagram in & out of the network!
• Some purists object to this, because it
interferes with host-to-host communication
• Need workarounds for P2P applications
INFO 330 Chapter 4
64
www.ischool.drexel.edu
UPnP
• Peer to peer applications need an easy
way to cross a NAT router (NAT traversal)
• Universal Plug and Play (UPnP) does that,
for either TCP or UDP packets
INFO 330 Chapter 4
65
www.ischool.drexel.edu
ICMP
• ICMP is an old (1981) protocol (RFC 792)
to communicate error messages across
the network layer
– E.g. “Destination network unreachable”
– ICMP is a nudge above IP, since ICMP sends
IP datagrams, instead of a TCP or UDP
segment
• ICMP messages have a type and code
field (p. 354), plus the first 8 bytes of the
offending IP datagram
INFO 330 Chapter 4
66
www.ischool.drexel.edu
ICMP & Ping
• ICMP message also convey other kinds of
information, such as congestion control,
bad IP header data, TTL expired, etc.
• Ping uses an ICMP message type 8, code
0, which is an “echo request”
– The reply should be type 0, code 0, “echo
reply”
INFO 330 Chapter 4
67
www.ischool.drexel.edu
Traceroute
• Traceroute sends UDP segments with bad
port numbers and successive TTL (1, then
2, then 3, etc.) and times each datagram
– When each TTL occurs, an ICMP warning
message is sent from that router, which
returns to give the round trip time (RTT) and
the router’s information
INFO 330 Chapter 4
68
www.ischool.drexel.edu
Traceroute
– When a datagram gets to the other host, the
UDP segment has a weird port number, which
prompts an ICMP message of type 3, code 3,
“destination port unreachable”
– That tells traceroute the other host has been
reached, so no more datagrams are needed
– Sneaky!
INFO 330 Chapter 4
69
www.ischool.drexel.edu
ICMP and Firewalls
• Firewalls typically inspect the headers of
packets to look for threatening contents
– Pings coming from outside your network can
map IP addresses, for example
– Port scans can look for open ports
• An Intrusion Detection System (IDS) goes
further by looking at packet contents
(data), and comparing them to known
attacks
INFO 330 Chapter 4
70
www.ischool.drexel.edu
IPv6
• The IETF realized that the Internet would run out
of IP address space, and CIDR, NAT, and
DHCP aren’t enough to save it
– By 1996, 100% of Class A addresses were used,
62% of Class B addresses, and 37% of Class C
• IPv6 was first called IPng (next generation)
– IPv6 is defined by RFC 2460
• What’s different from IPv4?
INFO 330 Chapter 4
71
www.ischool.drexel.edu
IPv6 Datagram
• The IP addresses went from 32 to 128 bits
– 2128= 340,282,366,920,938,463,463,374,607,431,
770,000,000
– Really, we won’t run out of IP addresses.
Ever.
• In contrast, the number of cells in 7 billion people
is about 7E9*1E12= 7E21, a factor of 49 million
billion under the 3.4E38 possible addresses
INFO 330 Chapter 4
72
www.ischool.drexel.edu
IPv6 Datagram
• Adds an anycast address type, which can
go to any in a group of hosts
• Header is fixed 40-bytes (2x4 B + 2x16 B)
• Adds flow labeling and priority, where a
flow is a group of packets requiring special
handling (real time service, or paid priority
enhancement)
INFO 330 Chapter 4
73
www.ischool.drexel.edu
IPv6 Datagram
• IPv6 addresses can be a 16-value dotted
decimal notation, e.g.
128.91.45.157.220.40.0.0.0.0.252.87.212.200.31.255 or the hex
equivalent 805B.2D9D.DC28.0000.0000.FC57.D4C8.1FFF
– There are lots of rules for abbreviating IPv6
addresses; most common is ‘::’ which hides a bunch
of zeroes
• Removes from IPv4
– Fragmentation, Header checksum, and Options
INFO 330 Chapter 4
74
www.ischool.drexel.edu
IPv6 Datagram
• Specifically, IPv6 headers have the following
fields:
–
–
–
–
IP version, now obviously a ‘6’
Traffic class, similar to the TOS field
Flow label, an identifier for a given flow
Payload length = number of bytes in the data
• Does not count the header, since that’s a fixed 40 B
–
–
–
–
Next header is the protocol field from IPv4
Hop limit acts like the time-to-live (TTL) field
Source and destination addresses, are 128 bits each
Then the data
INFO 330 Chapter 4
75
www.ischool.drexel.edu
ICMPv6
• ICMP has been updated for new
messages under IPv6 in RFC 4443
• It also takes over the Internet Group
Management Protocol (IGMP) which we’ll
get to later – it involves joining and leaving
multicast groups
INFO 330 Chapter 4
76
www.ischool.drexel.edu
IPv4 versus IPv6
• The transition from IPv4 to IPv6 is huge –
tens of millions of hosts and routers only
speak IPv4
• Three major approaches for making the
transition to v6
– Flag day approach
• Have everyone (in the whole world) update to v6
by a given specific day; only run v6 after that day
• Isn’t logistically or financially possible
INFO 330 Chapter 4
77
www.ischool.drexel.edu
IPv4 versus IPv6
– The dual stack approach means implement v4 and v6
at the same time, and switch back & forth as needed
• Every v6 node also runs v4; this is called an IPv6/IPv4 node
• Works, but often loses the benefit of v6 existing
– Tunneling is also possible
• Wherever a section of IPv4 links needs to be crossed,
package the IPv6 datagram in an IPv4 datagram
• Then unwrap the v6 datagram when back in v6 land
INFO 330 Chapter 4
78
www.ischool.drexel.edu
IPv6 Adoption
• The adoption of IPv6 has been slow, partly
because of CIDR, NAT, and DHCP
• However large scale technology changes
typically take a long time
– How many phone lines are optical yet?
– Network protocols are very slow to change,
whereas apps are easy to change
• IPv6 will probably be around a long time!
INFO 330 Chapter 4
79
www.ischool.drexel.edu
IP Security
• IPv4 was designed in the 1970’s, long
before anyone expected the Internet to be
a public medium – and hence it has no
security in it
• IPsec was created to work with IPv4 or
IPv6 and add security to the network layer
• It allows TCP and UDP traffic to take place
in a secure environment
INFO 330 Chapter 4
80
www.ischool.drexel.edu
IP Security
• IPsec
– Allows hosts to negotiate encryptiion
protocols
– Use that protocol to encrypt each datagram
– Verify that the header and data retain their
integrity
– Authenticate the origin of a trusted source
• This is covered more in chapter 8
INFO 330 Chapter 4
81
www.ischool.drexel.edu
Routing Algorithms
• Mostly have focused on forwarding – now
address routing
• Both datagram and VC networks need to
perform routing, i.e. find good paths
between sender and receiver
– A host is typically attached to its default router
(first hop), which we’ll call the source router;
similarly the destination has a destination
router
INFO 330 Chapter 4
82
www.ischool.drexel.edu
Routing Algorithms
• A “good” route typically minimizes cost,
but may also avoid other concerns (e.g.
ownership of networks, privacy of data,
etc.)
• Use a graph to show routing problems,
with N nodes (routers) and E edges (links)
– Assume the cost of each edge is a given:
c(x,y) = cost of edge between nodes x and
y(x,y) is the edge between those nodes
INFO 330 Chapter 4
83
www.ischool.drexel.edu
Routing Algorithms
• The cost of an edge not available is infinite
• A path is defined by a sequence of nodes
(x1, x2, x3, …, xn)
– The cost of a path is the sum of the edge
costs along it; c(x1,y1)+c(x2,y2)+…+c(xn, yn)
• Some path between nodes x and y is the
least-cost path
– If all edges have the same cost, the shortest
path is also the least-cost path
INFO 330 Chapter 4
84
www.ischool.drexel.edu
Routing Algorithms
• Two key ways to classify routing are:
– A global routing algorithm uses knowledge of
the entire network to calculate the best path
• Also called link-state (LS) algorithms
– A decentralized routing algorithm finds the
least cost path in an iterative decentralized
manner – no node has complete knowledge
of the network
• Only the local costs are known
• The distance-vector (DV) algorithm is one example
INFO 330 Chapter 4
85
www.ischool.drexel.edu
Routing Algorithms
• Another way to classify routing algorithms
is static vs dynamic
– Static routing algorithms change slowly over
time, often by human intervention
– Dynamic routing algorithms change to adjust
for traffic, topology, etc.
• Can update periodically, or adjust for network
changes
INFO 330 Chapter 4
86
www.ischool.drexel.edu
Routing Algorithms
• A third classification (!) is load-sensitive
versus load-insensitive algorithms
– Does congestion change the routing?
– High cost for a congested link leads to using
load-sensitive routing, but most Internet
algorithms are load-insensitive
• So we have: global vs. decentralized,
static vs. dynamic, and
load-sensitive vs. load-insensitive
INFO 330 Chapter 4
87
www.ischool.drexel.edu
Link-State Routing Algorithm
• The Link-State (LS) algorithm uses complete
knowledge of network topology and link costs
• The identity and cost of links for each router are
broadcast using a link-state broadcast, such as
the Internet’s OSPF protocol
• The actual routing is calculated using Dijkstra’s
algorithm (named for Edsger Dijkstra)
INFO 330 Chapter 4
88
www.ischool.drexel.edu
Link-State Routing Algorithm
• Dijkstra’s algorithm is iterative, so that
after k iterations, the least-cost paths are
known to k destination nodes
– The global routing algorithm initializes all
nodes, then does a loop as many times as
you have nodes in the network
– Each loop adds the lowest cost node to N’,
the list of nodes no longer under
consideration, until all nodes are in N’
INFO 330 Chapter 4
89
www.ischool.drexel.edu
Dijkstra’s Algorithm
Step
0
1
2
3
4
5
N'
u
ux
uxy
uxyv
uxyvw
uxyvwz
D(v),p(v) D(w),p(w)
2,u
5,u
2,u
4,x
2,u
3,y
3,y
D(x),p(x)
1,u
2
u
v
2
1
x
3
w
3
1
5
z
1
y
D(z),p(z)
8
8
4,y
4,y
4,y
5
The 8’s
should be
infinity
symbols ∞
D(y),p(y)
8
2,x
2
INFO 330 Chapter 4
Each loop adds one
lowest-cost node to N’ –
here, start at u, then add
x, then y (could have
chosen v instead), then
v, then w, then z.
90
www.ischool.drexel.edu
Dijkstra’s Algorithm
• For example, the algorithm finds the cost
to get from u to w is first 5 (path uw), then
4 (uxw), then 3 (uxyw), and can’t improve
on the cost of 3
• When done, we have the lowest cost path
from the source to all other nodes
• Complexity of this algorithm is the need to
search n(n+1)/2 nodes, which is O(n2) (the
order of n squared)
INFO 330 Chapter 4
91
www.ischool.drexel.edu
Oscillations
• If the cost of a path depends on the
direction through that path, algorithms can
undergo oscillations where the best path
changes from clockwise to counterclockwise with each iteration
• To avoid this, don’t run the algorithm on
all nodes at the same time
– Or don’t use load-based link costs
INFO 330 Chapter 4
92
www.ischool.drexel.edu
Distance-Vector (DV) Routing
• The Distance-Vector Routing Algorithm is
iterative, asynchronous, and distributed
• Nodes get data from directly attached
neighbors, and distribute the results only
to their neighbors
• Assume we’re going from node x to node
y, and the neighbors of x are nodes v
• The Bellman-Ford equation gives us
– dx(y) = min{c(x,v) + dv(y)}
INFO 330 Chapter 4
93
www.ischool.drexel.edu
Distance-Vector Routing
• Say what?
– Start at node x
– For each neighbor v, find the cost to get from
v to y, which is dv(y)
– The cost from each neighbor to y is the cost
from x to v, plus the cost from v to y, or {c(x,v)
+ dv(y)}
– The cheapest cost from x to y is the smallest
value of the previous bullet for any neighbor
of x
INFO 330 Chapter 4
94
www.ischool.drexel.edu
Distance-Vector Routing
• Cute parlor trick?
– Actually this is the basis for forwarding tables!
– For some destination y, the lowest cost path
goes through a particular neighbor v*
• The DV algorithm essentially follows the
Bellman-Ford equation
• As each node gets cost data from its
neighbors, the cost to get anywhere in the
network approaches the ideal value dx(y)
INFO 330 Chapter 4
95
www.ischool.drexel.edu
Distance-Vector Routing
• This depends on asynchronous data
exchange among nodes
– And after all nodes have exchanged
information, the routing won’t change
(becomes quiescent) until there’s a change in
link cost or a dead link
• Many protocols use some variation on
this approach, including ARPAnet, the
Internet’s RIP and BGP protocols,
Novell IPX, ISO IDRP, etc.
INFO 330 Chapter 4
96
www.ischool.drexel.edu
DV Changes
• If the cost of a link decreases, updates to
its neighbors will generally occur
peacefully
• If a cost goes up, leftover incorrect
information can cause a routing loop
(bounce back and forth between nodes)
– Large cost increases can result in thousands
of bounces before the problem corrects itself,
hence known as the count-to-infinity problem
INFO 330 Chapter 4
97
www.ischool.drexel.edu
DV Changes
• Fix somewhat with the poisoned reverse
– Pretend the cost to go backward on a link is
infinite, so it won’t try to bounce back
– But if the loop involves more than two nodes,
this doesn’t help
INFO 330 Chapter 4
98
www.ischool.drexel.edu
Compare LS vs. DV Routing
• Under LS, nodes talk to all other nodes,
but exchange costs of direct connections
– Under DV, nodes only talk to neighbors, but
gives cost estimates to all other nodes
• Message complexity
– LS sends cost changes to every node in the
network; DV only propagates changes when
cost decreases
INFO 330 Chapter 4
99
www.ischool.drexel.edu
Compare LS vs. DV Routing
• Speed of convergence
– LS converges with speed O(n2); DV
converges slowly, and can suffer from routing
loops and the count-to-infinity problem
• Robustness
– If a node fails under LS, the rest of the
network is relatively unaffected (for routing);
under DV, a faulty router can mislead the rest
of the network
•
So both approaches have advantages
INFO 330 Chapter 4
100
www.ischool.drexel.edu
Other Routing Approaches
• LS and DV are the only routing
approaches widely used in the Internet
• Many others have been defined over
the years
– Network flow problems model the network as
a big equation to solve
– Circuit-switched routing algorithms use
telephone-like logic to find the cheapest
routes
INFO 330 Chapter 4
101
www.ischool.drexel.edu
Hierarchical Routing
• LS and DV assume the network is a herd
of connected routers – all peers or equals
– Scaling for LS routing is daunting for huge
number of routers
– Most administrators want autonomy to decide
their structure
• What happens if there’s structure to
routers?
– Organize routers into autonomous systems
(AS)
INFO 330 Chapter 4
102
www.ischool.drexel.edu
Autonomous Systems (AS)
• Under AS, groups of routers
– Are under control of one administration authority
– Use one routing protocol (LS or DV) within that group,
their intra-autonomous system routing protocol
– Connect to other groups via gateway routers
• Routing information separates routing within the
AS from routing outside the AS
– Need to know which outside addresses are best
reached from which gateway routers
INFO 330 Chapter 4
103
www.ischool.drexel.edu
Autonomous Systems (AS)
3c
3a
3b
AS3
1a
2a
1c
1d
1b
2c
AS2
2b
AS1
Example of three AS’ and their interconnections.
1b, 1c, 2a, and 3a are all gateway routers.
INFO 330 Chapter 4
104
www.ischool.drexel.edu
Autonomous Systems (AS)
• In order for the AS’ to talk to each other,
they need to use the same inter-AS
routing protocol; called BGP4 for the
Internet
– BGP4 defines which subnets are reachable
from various gateway routers (assuming more
than one exists)
• One common strategy is hot-potato
routing, where you send a packet to the
cheapest gateway router
INFO 330 Chapter 4
105
www.ischool.drexel.edu
Autonomous Systems (AS)
• AS’ communicate to each other about new
destinations nearby
• Large ISPs may set up dozens of AS’ just
for themselves; smaller ISPs might be
one AS
• Now look at two intra-AS routing protocols
(RIP and OSPF) and the inter-AS routing
protocol BGP
INFO 330 Chapter 4
106
www.ischool.drexel.edu
RIP
• The Routing Information Protocol (RIP) is
an older intra-AS routing protocol
– Based on work by Xerox and part of the BSD
Unix distribution in 1982
– RIP version 2 is defined by RFC 2453
• Works based on the DV model
– Cost is based on hop count; each link has cost=1
– Hop is the number of subnets crossed to get from
source to destination
INFO 330 Chapter 4
107
www.ischool.drexel.edu
RIP
• Max cost allowed in RIP is 15 hops
• Routing updates are ~ every 30 sec using RIP
response messages or advertisements
• Each RIP router maintains a routing table
– The routing table contains the destination subnet, the
next router to get there, and the number of hops to
that destination
– Exchanging routing tables allows routers to find the
cheapest routes
INFO 330 Chapter 4
108
www.ischool.drexel.edu
RIP
• If a neighboring router doesn’t provide an
update for three minutes, it’s assumed to
be dead (rest in peace?), and the routing
table is adjusted accordingly
• RIP messages go over UDP using port
520
• In Unix, the daemon ‘routed’ (route dee)
implements RIP
INFO 330 Chapter 4
109
www.ischool.drexel.edu
OSPF (think sunscreen?)
• OSPF* and its cousin, IS-IS are widely
used for intra-AS routing
– OSPF version 2 is defined by RFC 2328
– IS-IS is defined by RFC 1195
• OSPF uses LS routing, and creates a
complete topological map of the entire AS
• Then it follows Dijkstra’s algorithm to find
the shortest paths everywhere in the AS
* OSPF = Open Shortest Path First, IS = Intermediate System
INFO 330 Chapter 4
110
www.ischool.drexel.edu
OSPF
• Link cost can be 1 (just count hops) or
weighted inversely to the link’s capacity
(to put more traffic where it can be
handled well)
INFO 330 Chapter 4
111
www.ischool.drexel.edu
OSPF
• All routers in the AS broadcast state
information to all other routers
– 1) when there’s a change in link cost or
status, or
– 2) every 30 minutes to say they’re alive
• OSPF messages are carried straight
over IP
INFO 330 Chapter 4
112
www.ischool.drexel.edu
OSPF
• OSPF advantages include
– Security – exchanges between OSPF routers
must be authenticated, either by simple
password or MD5 encryption
– Use multiple paths that are the same cost
– Also handles multicast (MOSPF)
– Allows creation of hierarchy within the AS
• Defines Areas, which connect to the Boundary
Routers through Area Boundary Routers and
maybe Backbone Routers
INFO 330 Chapter 4
113
www.ischool.drexel.edu
OSPF Internal Hierarchy
INFO 330 Chapter 4
114
www.ischool.drexel.edu
BGP
• So, RIP or OSPF can be used for routing
within an AS
– But when the source and destination hosts
cross many AS’, need BGP, the Border
Gateway Protocol (currently BGP4)
• BGP gives AS’ the means to
– Get subnet info from neighboring AS’
– Propagate that info to routers within the AS
– Find good routes to subnets
INFO 330 Chapter 4
115
www.ischool.drexel.edu
BGP
• BGP is massively complex (RFC 4271)
• BGP uses semi-permanent TCP
connections (using port 179) between
routers that connect AS’, and between
routers within an AS
– Connections between AS’ are external BGP
(eBGP)
– Within an AS uses internal BGP (iBGP)
INFO 330 Chapter 4
116
www.ischool.drexel.edu
BGP
• Which destinations are reachable through
a neighboring AS is expressed using CIDR
prefixes, e.g. 138.67.16/24
• Each AS is identified by an ASN
(AS number)
– ASNs are defined by ICANN and RFC 1930
INFO 330 Chapter 4
117
www.ischool.drexel.edu
BGP
• BGP peers (routers) advertise routes to
each other
– Routes consist of a prefix and BGP attributes
– BGP learns all possible routes, then follows a
set of rules to determine which to keep
– Policies are established to determine what
kind of routes are allowed, not just possible
– Import policies are used to determine if a new
advertised route is kept or not
INFO 330 Chapter 4
118
www.ischool.drexel.edu
Broadcast and Multicast
• So far everything has focused on one
source and one destination trying to
communicate (unicast)
• Broadcast routing sends a packet from a
source to all other nodes in the network
• Multicast routing sends from a source
node to selective other network nodes
INFO 330 Chapter 4
119
www.ischool.drexel.edu
Broadcast Routing
• A simple way to handle broadcasting is to make
N copies of a packet, and send one to each of
the N destination nodes (hosts)
– This is N-way-unicast, since it really isn’t a broadcast
method at all
• Major disadvantages of this simple approach:
– It’s really inefficient, and overloads the first link
– It’s hard to know all target addresses, unless you add
on a broadcast membership protocol
INFO 330 Chapter 4
120
www.ischool.drexel.edu
Uncontrolled Flooding
• A possible approach is to send a packet to
its neighbors, who send it to their
neighbors, etc.
• Massive problems include
– Cycle never ends if there are loops in the
network
– Multiple interconnections result in a broadcast
storm when a node gets e.g. three messages
to broadcast to all their neighbors, who get
multiple broadcast messages, and so on
INFO 330 Chapter 4
121
www.ischool.drexel.edu
Controlled Flooding
• Try flooding, but with more logic to prevent
a broadcast storm
• Several possible approaches
– Sequence-number-controlled flooding adds its
address and a broadcast sequence number in
the packet
• Nodes check for having received this sequence
number (e.g. broadcast #1254) from them already;
if not, duplicate it and send to neighbors
INFO 330 Chapter 4
122
www.ischool.drexel.edu
Controlled Flooding
– Reverse path forwarding (RPF) or reverse
path broadcasting (RPB) is subtle
• When a packet is received, send it out on all other
links ONLY IF it was received from the shortest
unicast path back to the source
• Otherwise, throw it out
INFO 330 Chapter 4
123
www.ischool.drexel.edu
Spanning-Tree Broadcast
• While the controlled flooding approaches do
avoid a broadcast storm, they can still send
duplicate packets
• A spanning tree diagram connects all the nodes
in a network exactly once
– One that has minimum cost is a minimum
spanning tree
• Hence a possible broadcast approach is to
construct a minimum spanning tree and use it
INFO 330 Chapter 4
124
www.ischool.drexel.edu
Spanning-Tree Broadcast
• Once defined, the spanning tree can be
used to initiate a broadcast from any node
– Each node only knows which adjacent nodes
are part of the tree
• Many algorithms can be used to create
spanning trees, such as the center-based
approach
INFO 330 Chapter 4
125
www.ischool.drexel.edu
Reality v Broadcast Algorithms
• Broadcast algorithms are used at the
application and network layers
– Gnutella uses app-layer broadcasting, with a
time-to-live hop number countdown to give
limited-scope flooding
– OSPF uses sequence-controlled flooding to
broadcast link-state advertisements (LSAs),
as well as in the IS-IS protocol
• Sequence number and age data are used by
OSPF to tell old LSAs from newer ones
INFO 330 Chapter 4
126
www.ischool.drexel.edu
Multicast
• Multicast sends a packet only to select
nodes in a network
– There also may be more than one sender
• Examples of uses include
– Bulk software upgrades
– Streaming media to a class or meeting
– Shared apps like teleconferencing
– Data feeds (stock prices)
– Interactive gaming
INFO 330 Chapter 4
127
www.ischool.drexel.edu
Multicast
• Key problems are
– How to identify the receivers of the message
– How to address those receivers
• In unicast, the IP address of the recipient
was enough; but now, does every address
get the list of all recipients?
– Addressing could be larger than the message
• Solve using address indirection
INFO 330 Chapter 4
128
www.ischool.drexel.edu
Multicast
• Address indirection uses a single identifier
(here, a class D multicast address) for the
group of receivers, and address the packet
only with that single identifier
– The single identifier is a multicast group
• So how do we manage this multicast
group? Create an RFC! (duh!)
– Internet Group Management Protocol
INFO 330 Chapter 4
129
www.ischool.drexel.edu
IGMP
• The Internet Group Management Protocol
(IGMP), version 3, RFC 3376, works
between a gateway router (first hop router)
and its hosts – only within its LAN
• IGMP allows a host to tell the router that a
hosted app wants to join a multicast group
– Then the router communicates to other
routers using a network-layer multicast routing
algorithm, e.g. PIM, DVMRP, or MOSPF
INFO 330 Chapter 4
130
www.ischool.drexel.edu
IGMP
• IGMP only has three message types,
carried in an IP datagram
– Membership_query is sent by the router to
find all groups joined by hosts on that
interface, or determines if a particular group
has been joined
– Membership_report is sent by the hosts to
reply to a query, or to tell the router when a
group has first been joined
INFO 330 Chapter 4
131
www.ischool.drexel.edu
IGMP
– Leave_group message is oddly optional; a
host can leave a group by not responding to
queries
• So joining a multicast group is based on
receiver host action – sending a
membership_report to the router
– This means the sender doesn’t control
membership – doesn’t add new receivers
to the group
INFO 330 Chapter 4
132
www.ischool.drexel.edu
Multicast Routing
• Multicast routing algorithms need to
ensure that all routers with hosts in the
group get the desired packets
– Other routers might have to get them too,
but avoid that where possible
• Two major approaches are used for
multicast routing
– Using a group-shared tree
– Using a source-based tree
INFO 330 Chapter 4
133
www.ischool.drexel.edu
Using a group-shared tree
• Like the spanning-tree algorithm, build a
tree that includes all edge routers with
hosts in the group
– Uses a single tree to allow sending from any
sender; kind of a global approach
• A central node is used to coordinate the
process, so new routers send messages
to it to get added to the tree
– Also called a center-based tree approach
INFO 330 Chapter 4
134
www.ischool.drexel.edu
Using a source-based tree
• Focuses on making a shared routing tree
based on a specific source sender
– Uses the RPF (reverse path forwarding)
algorithm, tweaked for multicast
– Can result in thousands of unwanted packets
to routers with no group members
• Routers who get unwanted packets send
a pruning message to a router upstream
from it
INFO 330 Chapter 4
135
www.ischool.drexel.edu
Multicast in the Internet
• The first multicast routing algorithm is the
Distance-Vector Multicast Routing
Protocol (DVMRP, RFC 1075)
– Uses source-based trees with RPF and
pruning
– Uses a DV algorithm to find the shortest path
to the source
– Also monitors downstream dependent routers
– Has graft messages to, yes, undo a pruning
INFO 330 Chapter 4
136
www.ischool.drexel.edu
Multicast in the Internet
• The Protocol-Independent Multicast (PIM,
RFC 3973) routing protocol is widely used
– Uses dense or sparse modes, depending on
the density of routers with group member
hosts
– Dense mode uses flood-and-prune RPF
– Sparse mode uses center-based tree, like the
core-based tree (CBT) protocol
– Can switch from group-shared tree to sourcebased tree after joining
INFO 330 Chapter 4
137
www.ischool.drexel.edu
Multicast in the Internet
• PIM sparse domains can be joined at
rendevous points using Multicast Source
Discovery Protocol (MSDP, RFC 4611)
• A third option for multicast is SourceSpecific Multicast (SSM, RFC 4607)
– Under SSM only one host can send traffic into
the multicast tree, which makes defining the
tree a lot easier
INFO 330 Chapter 4
138
www.ischool.drexel.edu
Multicast in the Internet
• BGP can also support multicast (RFC
4271)
• RFC 5110 is good for more discussion of
multicast routing
• Increasingly multicast is being handled at
the application layer, such as End System
Multicast (ESM)
INFO 330 Chapter 4
139
www.ischool.drexel.edu
Multicast Babel?
• So far assumed all routers use the same
multicast protocol
– Within an AS this should be true
– But different AS’ could run different protocols
• RFC 2715 defines interoperability rules for
multicast routing protocols to play nicely
with each other
– DVMRP is the de facto standard, but PIM and
BGP are also viable
INFO 330 Chapter 4
140
www.ischool.drexel.edu
Are We Dead Yet?
• Diving into the network core, we’ve covered
–
–
–
–
–
–
Service models for datagram and VC networks
Router components and how they work
IPv4 and IPv6 datagram formats
Allocation of IP addresses
NAT and ICMP
Link-state and distance-vector routing algorithms
INFO 330 Chapter 4
141
www.ischool.drexel.edu
Are We Dead Yet?
– Routing within and among AS’
– Routing protocols RIP, OSPF, BGP
– Broadcast routing algorithms – uncontrolled &
controlled flooding, spanning-tree
– Multicast routing algorithms – IGMP, DVMRP,
and PIM and a few more…
• And you thought the network layer was
just IP
INFO 330 Chapter 4
142
www.ischool.drexel.edu