PPT Version
... path computation may be made by PCE physically distinct from the computed path path computed by PCE may be complete: full explicit path of strict hops partial: mix of strict & loose hops (may be an abstract node such as an AS) PCE path computation can be used in conjunction with other path ...
... path computation may be made by PCE physically distinct from the computed path path computed by PCE may be complete: full explicit path of strict hops partial: mix of strict & loose hops (may be an abstract node such as an AS) PCE path computation can be used in conjunction with other path ...
4. TCP/IP - Faculty of Computer Science and Information Technology
... Subnet mask is created by using binary ones in the host If three bits were borrowed, the mask for a Class C address would be 255.255.255.224 or /27. The last two bits in the last octet, regardless of the IP address class, may never be assigned to the subnetwork (2power of borrowed bits) – 2 = usable ...
... Subnet mask is created by using binary ones in the host If three bits were borrowed, the mask for a Class C address would be 255.255.255.224 or /27. The last two bits in the last octet, regardless of the IP address class, may never be assigned to the subnetwork (2power of borrowed bits) – 2 = usable ...
Wiener Number of Directed Graphs and Its Relation
... is usually assumed to be split evenly among all shortest paths, see for example [10]. While there are several studies on the Wiener number of weighted graphs, there seems to be no generalization(s) to directed graphs (or, digraphs). In the undirected case, the Wiener number is usually defined as the ...
... is usually assumed to be split evenly among all shortest paths, see for example [10]. While there are several studies on the Wiener number of weighted graphs, there seems to be no generalization(s) to directed graphs (or, digraphs). In the undirected case, the Wiener number is usually defined as the ...
high-speed packet forwarding in software routers on multi
... – DIFANE: multidimensional packet classification Rules based on many fields, with possible wildcards Lookup based on coarse-grained partition rules ...
... – DIFANE: multidimensional packet classification Rules based on many fields, with possible wildcards Lookup based on coarse-grained partition rules ...
Unit 3- Mobile Network layer
... Firewalls at the foreign network may not allow that Multicasting: if a MN is to participate in a multicast group, it needs to use a reverse tunnel to maintain its association with the home network. TTL: a MN might have a TTL that is suitable for communication when it is in its HM. This TTL may n ...
... Firewalls at the foreign network may not allow that Multicasting: if a MN is to participate in a multicast group, it needs to use a reverse tunnel to maintain its association with the home network. TTL: a MN might have a TTL that is suitable for communication when it is in its HM. This TTL may n ...
Document
... such namespaces (e.g., IPv4<->IPv6, IP<->Phone#, NDN, etc.) VIRO: “native” naming/address-independent simply incorporate more directory services
...
... such namespaces (e.g., IPv4<->IPv6, IP<->Phone#, NDN, etc.) VIRO: “native” naming/address-independent simply incorporate more
Software Architecture Design of Wireless Sensor Networks
... the members of the cluster must quickly deal with the fault, by electing a new cluster head or resorting to ad hoc networking to members of other clusters [4]. The more time is spent in network reconfiguration the more data can be lost due to memory limitations at the effected nodes [4]. This behavi ...
... the members of the cluster must quickly deal with the fault, by electing a new cluster head or resorting to ad hoc networking to members of other clusters [4]. The more time is spent in network reconfiguration the more data can be lost due to memory limitations at the effected nodes [4]. This behavi ...
Optimal_Proxy_Cache_Allocation_for_Efficient_Streaming_Media
... The proxy can schedule a transmission of the complete suffix at t2+vi. (SBatch) Another option is to schedule a patch of [vi, t2] of the suffix from the server since segment [t2, Li] has already been scheduled to be transmitted. ...
... The proxy can schedule a transmission of the complete suffix at t2+vi. (SBatch) Another option is to schedule a patch of [vi, t2] of the suffix from the server since segment [t2, Li] has already been scheduled to be transmitted. ...
3. Ethernet - Faculty of Computer Science and Information Technology
... Ethernet is a family of networking technologies that includes Legacy, Fast Ethernet, and Gigabit Ethernet. Ethernet speeds can be 10, 100, 1000, or 10,000 Mbps. IEEE standard for Ethernet is 802.3 Ethernet relies on baseband signaling, which uses the entire bandwidth of the transmission medium. In 1 ...
... Ethernet is a family of networking technologies that includes Legacy, Fast Ethernet, and Gigabit Ethernet. Ethernet speeds can be 10, 100, 1000, or 10,000 Mbps. IEEE standard for Ethernet is 802.3 Ethernet relies on baseband signaling, which uses the entire bandwidth of the transmission medium. In 1 ...
Linux+ Guide to Linux Certification
... A physical topology is the basic physical layout of a network; it does not specify devices, connectivity methods, or addresses on the network A bus topology consists of a single cable connecting all nodes on a network without intervening connectivity devices In a ring topology, each node is conn ...
... A physical topology is the basic physical layout of a network; it does not specify devices, connectivity methods, or addresses on the network A bus topology consists of a single cable connecting all nodes on a network without intervening connectivity devices In a ring topology, each node is conn ...
Can the Production Network the Testbed? Be Rob Sherwood
... Future Directions • Currently limited to subsets of actual topology • Add virtual links, nodes support • Adaptive CPU isolation • Change rate-limits dynamically with load • ... message type • More deployments, experience ...
... Future Directions • Currently limited to subsets of actual topology • Add virtual links, nodes support • Adaptive CPU isolation • Change rate-limits dynamically with load • ... message type • More deployments, experience ...
... any connection to Internet can serve to give support and interconnection to it. For the sector of Latin America the University of Guadalajara in Mexico is the point of contact on our continent and the UACh (Universidad Austral de Chile) the IPv6 multicast node for Chile just as illustrated in Figure ...
A study of IP Over WDM
... The forwarding Equivalence Class (FEC) • What is FEC? – It associates an FEC value with destination address and a class of traffic. – The class of traffic is associated with a destination TCP/UDP port no and/or protocol ID field in the IP datagram header. ...
... The forwarding Equivalence Class (FEC) • What is FEC? – It associates an FEC value with destination address and a class of traffic. – The class of traffic is associated with a destination TCP/UDP port no and/or protocol ID field in the IP datagram header. ...
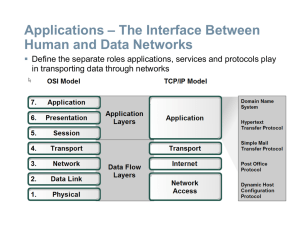
Application Layer Functionality and Protocols
... Compare and Contrast the Use of Ethernet Switches versus Hubs in a LAN. Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
... Compare and Contrast the Use of Ethernet Switches versus Hubs in a LAN. Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
Internet PowerPoint - University at Albany
... A decentralized algorithm calculates the least cost path in an iterative distributed manner ...
... A decentralized algorithm calculates the least cost path in an iterative distributed manner ...
Chapter 12 SOLUTIONS to Practice Problems
... How many possible Ethernet addresses exist for each individual vendor? Solution: There are 224 = 16,777,216 possible address per vendor. Note that many companies have more than one such block of addresses. Practice Problem 12.8 Express the Ethernet broadcast address in hexadecimal. Solution: FF:FF:F ...
... How many possible Ethernet addresses exist for each individual vendor? Solution: There are 224 = 16,777,216 possible address per vendor. Note that many companies have more than one such block of addresses. Practice Problem 12.8 Express the Ethernet broadcast address in hexadecimal. Solution: FF:FF:F ...
ex1-9-o-can-Ethernet_Part_2
... Resolving IPv4 addresses to MAC Addresses • Address Resolution Protocol (ARP): • Why do devices need to map a MAC address to an IP address? • There is no built-in connection or relationship between the MAC (physical) address and the assigned IP (logical) address. • IP hosts and routers use Address ...
... Resolving IPv4 addresses to MAC Addresses • Address Resolution Protocol (ARP): • Why do devices need to map a MAC address to an IP address? • There is no built-in connection or relationship between the MAC (physical) address and the assigned IP (logical) address. • IP hosts and routers use Address ...
Presentation (ppt)
... Clients subscribe to all rendezvous nodes Clients advertise to all rendezvous nodes Rendezvous nodes exchange subscriptions Rendezvous nodes exchange advertisements ...
... Clients subscribe to all rendezvous nodes Clients advertise to all rendezvous nodes Rendezvous nodes exchange subscriptions Rendezvous nodes exchange advertisements ...
Lesson 2-3: Ethernet Basics
... address. The address used is the MAC address or hardware address of the network device. A multicast frame is addressed to several but not all devices. All devices that are a part of the specified group may read the frame. A multicast address is a deviation from the normal hardware address. For examp ...
... address. The address used is the MAC address or hardware address of the network device. A multicast frame is addressed to several but not all devices. All devices that are a part of the specified group may read the frame. A multicast address is a deviation from the normal hardware address. For examp ...
procurve s 4000m and 8000m witches
... * A redundant power supply (J4119A) is required if more than five 100Base-FX modules (J4112A) are installed ...
... * A redundant power supply (J4119A) is required if more than five 100Base-FX modules (J4112A) are installed ...
IEEE802.11 Wireless LAN Standard
... for access to the same shared wireless medium. A BSS may be isolated or connected to a backbone distribution system (DS) through an access point (AP). The access point functions as a bridge. The BSS generally corresponds to what is referred to as a cell in the literature. The DS can be a switch, a w ...
... for access to the same shared wireless medium. A BSS may be isolated or connected to a backbone distribution system (DS) through an access point (AP). The access point functions as a bridge. The BSS generally corresponds to what is referred to as a cell in the literature. The DS can be a switch, a w ...