Chapter 3 - Department of Computer and Information Science and
... (A=i,W=j) [A=Ack, W=window]: receiver acks up to ‘i-1’ bytes and allows/anticipates i up to i+j-1 receiver can use the cumulative ack option and not respond immediately ...
... (A=i,W=j) [A=Ack, W=window]: receiver acks up to ‘i-1’ bytes and allows/anticipates i up to i+j-1 receiver can use the cumulative ack option and not respond immediately ...
September 21, 2016 Open Call Slides
... Administrator (VESA). If the action is a query, partners can access it either from the Exchange Network Services Center (ENSC) or from an Internet browser using the flows-associated representational state transfer (REST) Uniform Resource Locator (URL). The owner of the VES node must authorize Partne ...
... Administrator (VESA). If the action is a query, partners can access it either from the Exchange Network Services Center (ENSC) or from an Internet browser using the flows-associated representational state transfer (REST) Uniform Resource Locator (URL). The owner of the VES node must authorize Partne ...
Chapter 16: Distributed Operating Systems
... CSMA/CD - Carrier sense with multiple access (CSMA); ...
... CSMA/CD - Carrier sense with multiple access (CSMA); ...
Internet Overview: Network Switching
... Transmission rate of single circuit = frame rate in frames/sec * #bits in a slot ...
... Transmission rate of single circuit = frame rate in frames/sec * #bits in a slot ...
Mobile networking in the Internet
... Besides minimal weight and size, there are other hardware implications when designing for mobile computing. Clearly, battery powered operation is highly desirable, and improvements in battery life continue to extend the feasibility of tetherless computing. On the other hand, the proliferation of mob ...
... Besides minimal weight and size, there are other hardware implications when designing for mobile computing. Clearly, battery powered operation is highly desirable, and improvements in battery life continue to extend the feasibility of tetherless computing. On the other hand, the proliferation of mob ...
WirelessHacks - Wright State University
... request... it would be interesting to spoof a response to this... ...
... request... it would be interesting to spoof a response to this... ...
The IPv6 QoS system implementation in virtual infrastructure
... differs from the solutions used so far. The most common one is a full virtualization of both, control and data plane. Such an approach can only be used on devices supporting a full virtualization. It requires significant reserves of CPU time, discs and memory. A separation between data and control p ...
... differs from the solutions used so far. The most common one is a full virtualization of both, control and data plane. Such an approach can only be used on devices supporting a full virtualization. It requires significant reserves of CPU time, discs and memory. A separation between data and control p ...
03_tcom5272_tcpip
... Router’s Functions A router is responsible for determining the packet’s path and switching the packet out the correct port. A router does this in five steps: 1. De-encapsulates the packet 2. Performs the ANDing operation 3. Looks for entry in routing table 4. Re-encapsulates packet into a frame ...
... Router’s Functions A router is responsible for determining the packet’s path and switching the packet out the correct port. A router does this in five steps: 1. De-encapsulates the packet 2. Performs the ANDing operation 3. Looks for entry in routing table 4. Re-encapsulates packet into a frame ...
net221 lecture 6++
... TCP is a reliable transport layer protocol. This means that TCP delivers the entire stream to the application program without error, and without any part lost or duplicated. Error control includes mechanisms for detecting 1. corrupted segments, 2. lost segments, 3. out-of-order segments, and 4. dupl ...
... TCP is a reliable transport layer protocol. This means that TCP delivers the entire stream to the application program without error, and without any part lost or duplicated. Error control includes mechanisms for detecting 1. corrupted segments, 2. lost segments, 3. out-of-order segments, and 4. dupl ...
ch16-Distributed_System_Structures
... simultaneously. Techniques to avoid repeated collisions include: CSMA/CD - Carrier sense with multiple access (CSMA); ...
... simultaneously. Techniques to avoid repeated collisions include: CSMA/CD - Carrier sense with multiple access (CSMA); ...
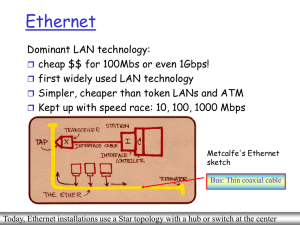
Ethernet
... Describe general specifications of cable and connector types and explain where they may be used within a Local Area Network (LAN) Compare and contrast the functionality of hubs vs. switches Explain how the Spanning Tree Protocol works Describe the Ethernet Frame and explain how a frame is routed thr ...
... Describe general specifications of cable and connector types and explain where they may be used within a Local Area Network (LAN) Compare and contrast the functionality of hubs vs. switches Explain how the Spanning Tree Protocol works Describe the Ethernet Frame and explain how a frame is routed thr ...
CMPT 880: Internet Architectures and Protocols
... timer for each in-flight pkt timeout(n): retransmit pkt n and all higher seq # pkts in window ...
... timer for each in-flight pkt timeout(n): retransmit pkt n and all higher seq # pkts in window ...
Wireless Networks 11, 21–38, 2005
... one-way chain, a node applies this equation to the received value to determine if the computed value matches a previous known authentic key on the chain. Coppersmith and Jakobsson present efficient mechanisms for storing and generating values of hash chains [13]. Each sender pre-determines a schedul ...
... one-way chain, a node applies this equation to the received value to determine if the computed value matches a previous known authentic key on the chain. Coppersmith and Jakobsson present efficient mechanisms for storing and generating values of hash chains [13]. Each sender pre-determines a schedul ...
network
... if any bridge does not receive config message after a period of time, it starts generating config messages claiming to be the root upon receiving a config message over a particular ...
... if any bridge does not receive config message after a period of time, it starts generating config messages claiming to be the root upon receiving a config message over a particular ...
Chap. 16, Distributed Operating Systems
... Each packet may take a different path through the network ...
... Each packet may take a different path through the network ...
Ethernet Switches
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
ppt
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
... • Traditional networks route packets looking only at destination • Also, maybe source fields (e.g. multicast) ...
bluetooth low energy compared to zigbee and bluetooth
... At the dawn of the computer era people gave a birth to a new phenomenon of method of data exchanging in computer network. This is just a miracle of technology allowing two computers to exchange their data without wires. As we know, all wires and cables make a tangled mess. Since cables are no longer ...
... At the dawn of the computer era people gave a birth to a new phenomenon of method of data exchanging in computer network. This is just a miracle of technology allowing two computers to exchange their data without wires. As we know, all wires and cables make a tangled mess. Since cables are no longer ...
Secure Efficient Distance Vector Routing for Mobile Wireless Ad Hoc
... 15 as is used in RIP [14, 26]. To further reduce these problems, a number of extensions, such as split horizon and split horizon with poisoned reverse [14, 26], are widely used. These extensions, however, can still allow some loops, and the possible problems that can create routing loops are more co ...
... 15 as is used in RIP [14, 26]. To further reduce these problems, a number of extensions, such as split horizon and split horizon with poisoned reverse [14, 26], are widely used. These extensions, however, can still allow some loops, and the possible problems that can create routing loops are more co ...