Source Flow: Handling Millions of Flows on Flow
... have difficulty handling a large number of flows in a node due to the capacity limitation of search engine devices such as ternary content-addressable memory (TCAM). One typical solution of this problem would be to use MPLS-like tunneling, but this approach spoils the advantage of flow-byflow path s ...
... have difficulty handling a large number of flows in a node due to the capacity limitation of search engine devices such as ternary content-addressable memory (TCAM). One typical solution of this problem would be to use MPLS-like tunneling, but this approach spoils the advantage of flow-byflow path s ...
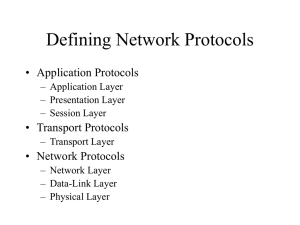
Defining Network Protocols
... • Dynamic Host Configuration Protocol • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for ...
... • Dynamic Host Configuration Protocol • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for ...
Frame transmission (Ack/Nack custom protocol mode)
... (note: with protocol mode system can recover from line error) Stefano Chiozzi – INFN Ferrara – GTK DAQ meeting 19/04/2010 Torino ...
... (note: with protocol mode system can recover from line error) Stefano Chiozzi – INFN Ferrara – GTK DAQ meeting 19/04/2010 Torino ...
Communication Network Protocols
... • The data link layer provides reliable transit of data across a physical network link. Different data link layer specifications define different network and protocol characteristics, including physical addressing, network topology, error notification, sequencing of frames, and flow control. Physica ...
... • The data link layer provides reliable transit of data across a physical network link. Different data link layer specifications define different network and protocol characteristics, including physical addressing, network topology, error notification, sequencing of frames, and flow control. Physica ...
HW1 Solution
... Ethernet standards require a minimum frame size of 512 bits in order to ensure that a node can detect any possible collision while it is still transmitting. This corresponds to the number of bits that can be transmitted at 10 Mbps in one roundtrip time. It only takes one propagation delay, however, ...
... Ethernet standards require a minimum frame size of 512 bits in order to ensure that a node can detect any possible collision while it is still transmitting. This corresponds to the number of bits that can be transmitted at 10 Mbps in one roundtrip time. It only takes one propagation delay, however, ...
Lecture 17
... Recall that we have discussed the Medium Access Control Sublayer… And that it is a sublayer of the Data Link Layer… …the bottom half, in fact The top half is another sublayer known as the Logical Link Control sublayer or LLC ...
... Recall that we have discussed the Medium Access Control Sublayer… And that it is a sublayer of the Data Link Layer… …the bottom half, in fact The top half is another sublayer known as the Logical Link Control sublayer or LLC ...
5_Data Link Layer
... There is a central node which repeats whatever it receives from fT frequency on the other fR frequency. ...
... There is a central node which repeats whatever it receives from fT frequency on the other fR frequency. ...
Slides
... – Connections are established and dropped based on the amount of traffic going through the node – ConnectionManager measures the traffic in the given time sequence and if it is more than the given upper traffic limit one connection is dropped ...
... – Connections are established and dropped based on the amount of traffic going through the node – ConnectionManager measures the traffic in the given time sequence and if it is more than the given upper traffic limit one connection is dropped ...
P2P
... In the peer-to-peer paradigm, the participating processes play equal roles, with equivalent capabilities and responsibilities (hence the term “peer”). Each participant may issue a request to another participant and receive a response. ...
... In the peer-to-peer paradigm, the participating processes play equal roles, with equivalent capabilities and responsibilities (hence the term “peer”). Each participant may issue a request to another participant and receive a response. ...
MAC layer
... Schiller Sec 7.3.1, 7.3.2 • 802.11 Physical layer: Schiller Sec 7.3.3 • 802.11 MAC layer: Schiller Sec 7.3.4 • 802.11 Management: Schiller Sec 7.3.5 ...
... Schiller Sec 7.3.1, 7.3.2 • 802.11 Physical layer: Schiller Sec 7.3.3 • 802.11 MAC layer: Schiller Sec 7.3.4 • 802.11 Management: Schiller Sec 7.3.5 ...
tr-2002-70
... avoids the high cost of a custom network devoted to the badge system. In our implementation, we used four receivers to cover 350 square meters. Not counting the cost of the badges nor any PCs, and considering the existing network infrastructure as free, this works out to a cost of about US$ 0.18/squ ...
... avoids the high cost of a custom network devoted to the badge system. In our implementation, we used four receivers to cover 350 square meters. Not counting the cost of the badges nor any PCs, and considering the existing network infrastructure as free, this works out to a cost of about US$ 0.18/squ ...
Wireless Communications and Networks
... Used to adapt higher-layer WAP protocol to the communication mechanism used between mobile node and WAP gateway WDP hides details of the various bearer networks from the other layers of WAP Adaptation may include: ...
... Used to adapt higher-layer WAP protocol to the communication mechanism used between mobile node and WAP gateway WDP hides details of the various bearer networks from the other layers of WAP Adaptation may include: ...
pptx
... More efficient, i.e., less overhead Blocks of characters are transmitted without start and stop codes. The transmitted stream is suitably encoded so the receiver can stay ’in synch’ by: – Using a separate clock line. – Embedding clocking information into data (e.g. biphase coding). Advanced Computer ...
... More efficient, i.e., less overhead Blocks of characters are transmitted without start and stop codes. The transmitted stream is suitably encoded so the receiver can stay ’in synch’ by: – Using a separate clock line. – Embedding clocking information into data (e.g. biphase coding). Advanced Computer ...
Probabilistic Reasoning
... Once the network is specified, we need only specify conditional probabilities for the nodes that participate in direct dependencies, and use those to compute any other probabilities. A simple Bayesian network (Fig 14.1) An example of burglary-alarm-call (Fig 14.2) The topology of the network can be ...
... Once the network is specified, we need only specify conditional probabilities for the nodes that participate in direct dependencies, and use those to compute any other probabilities. A simple Bayesian network (Fig 14.1) An example of burglary-alarm-call (Fig 14.2) The topology of the network can be ...
Click Here to Download…
... device simply transmits. The receiving device has to look at the incoming signal and figure out what it is receiving and coordinate and retime its clock to match the incoming signal. Sending data encoded into your signal requires that the sender and receiver are both using the same encoding/decodin ...
... device simply transmits. The receiving device has to look at the incoming signal and figure out what it is receiving and coordinate and retime its clock to match the incoming signal. Sending data encoded into your signal requires that the sender and receiver are both using the same encoding/decodin ...
Document
... Used to connect stations adapters in a physical star topology but logically bus Connection to the hub consists of two pairs of twisted pair wire one for transmission and the other for receiving. Hub receives a bit from an adapter and sends it to all the other adapters without implementing any access ...
... Used to connect stations adapters in a physical star topology but logically bus Connection to the hub consists of two pairs of twisted pair wire one for transmission and the other for receiving. Hub receives a bit from an adapter and sends it to all the other adapters without implementing any access ...
- Home - KSU Faculty Member websites
... • The Internet Protocol (IP) is the most widely used network-addressing scheme • IP is a connectionless, unreliable, best-effort delivery ...
... • The Internet Protocol (IP) is the most widely used network-addressing scheme • IP is a connectionless, unreliable, best-effort delivery ...
Lecture 1 - Intro
... • An increase of 5 –fold over the last 5 years • An increase of 3 folds is expected by 2019 • Wireless and mobile traffic makes up 54% of global traffic • By 2019, two thirds of global traffic will be generated by non-PC devices (welcome to the IoT) ...
... • An increase of 5 –fold over the last 5 years • An increase of 3 folds is expected by 2019 • Wireless and mobile traffic makes up 54% of global traffic • By 2019, two thirds of global traffic will be generated by non-PC devices (welcome to the IoT) ...
Token Ring
... twisted cable, one pair is used to receive data and one pair is used to transmit data. Any collision here happens in the hub. The maximum length of a 10BaseT segment is 100m. Can support up to 1024 nodes. ...
... twisted cable, one pair is used to receive data and one pair is used to transmit data. Any collision here happens in the hub. The maximum length of a 10BaseT segment is 100m. Can support up to 1024 nodes. ...
PPT
... “P2P is a class of applications that take advantage of resources – storage, cycles, content, human presence – available at the edges of the Internet. Because accessing these decentralized resources means operating in an environment of unstable and unpredictable IP addresses P2P nodes must operate ...
... “P2P is a class of applications that take advantage of resources – storage, cycles, content, human presence – available at the edges of the Internet. Because accessing these decentralized resources means operating in an environment of unstable and unpredictable IP addresses P2P nodes must operate ...
Simple Wire Replacement
... gateway and all its nodes exchange a binding code that prevents radios outside the network from communicating with the gateway (similar to pairing a headset to a phone, but more secure). Additionally, gateways and nodes can be configured for multiple channel hop patterns to eliminate data collisions ...
... gateway and all its nodes exchange a binding code that prevents radios outside the network from communicating with the gateway (similar to pairing a headset to a phone, but more secure). Additionally, gateways and nodes can be configured for multiple channel hop patterns to eliminate data collisions ...