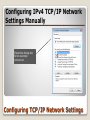
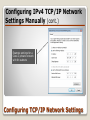
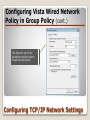
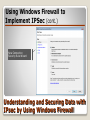
* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Chapter 11 - Information Technology Gate
Deep packet inspection wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Computer security wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
TCP congestion control wikipedia , lookup
Internet protocol suite wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Understanding, Configuring, and Securing TCP/IP Networks Lesson 11 Technology Skill Introducing TCP/IP Objective Domain Skill Domain # Configure and troubleshoot 4.1 network protocols Understanding IP Addresses Understanding Subnetting and Subnet Masks Configuring TCP/IP Network Settings • IPv6 • IPv4 IPv4 4.1 Auto vs. manual configuration 4.1 Skills Matrix 4.1 Technology Skill Understanding DNS Understanding DHCP Understanding and Configuring Wireless Networking and Security Skills Matrix Objective Domain Skill Domain # Configure and troubleshoot 4.2 network services at the client level • DNS DHCP 4.2 Configure and troubleshoot 4.5 wireless networking • Configure wireless network security • WPA • WEP Technology Skill Objective Domain Skill Configuring Wireless Configure policy settings Networking in Group Policy Domain # 4.5 Understanding and Configure network security 4.6 Securing Data with IPsec • IPsec by Using Windows Firewall Using Windows Firewall with Advanced Security to Implement IPsec Skills Matrix • IPsec • Windows Firewall 4.6 Understanding TCP/IP Transmission Control Protocol/Internet Protocol (TCP/IP) – Most commonly used protocol for communication on computer networks. It is the network communications protocol that is the basis for the Internet. Introducing TCP/IP Understanding TCP/IP (cont.) Computers running Windows Vista are by default TCP/IP hosts, meaning that they have all of the software required for taking part in a TCP/IP network. Introducing TCP/IP Understanding IP Addresses TCP/IP hosts, such as computers running Windows Vista, are identified on TCP/IP networks with an IP address. Other network entities, such as printers or routers, can also be identified with an IP address. Introducing TCP/IP Understanding IP Addresses (cont.) IP addresses are 32 bits in length and are expressed in four octets separated from one another with a dot (the “.” character). Each octet is 8 bits long (32 bits for each address divided by 4 octets = 8 bits), which is why they are called octets. Example IP address: 10.23.132.23 Introducing TCP/IP Understanding IP Addresses (cont.) Octets are expressed as values between 0 and 255 (with some restrictions). The first octet determines the class of the address. Classes – Divide the IP address space into sections that are used for different purposes Introducing TCP/IP Understanding IP Addresses (cont.) IP Address First Octet Class Range Purpose Class A 1-126 Very large networks Class B 128-191 Medium to large networks Class C 192-223 Small networks Class D 224-239 Class E 240-255 Multicasting (sending messages to more than one host at a time) Reserved for experimental purposes Introducing TCP/IP Understanding IP Addresses (cont.) TCP/IP hosts that are directly exposed to the Internet must receive their IP addresses from the Internet Corporation for Assigned Names and Numbers (ICANN) or some other authority. These IP addresses are called public-facing IP addresses. Introducing TCP/IP Understanding IP Addresses (cont.) Almost all organizations today use private networks, in which the IP addresses internal to the organization are hidden from hosts external to the organization. Introducing TCP/IP Understanding Subnetting and Subnet Masks Subnetting – Using subnet masks to partition a network into smaller networks called subnets Subnet mask – Used by subnetting to divide an IP address into a network ID and a host ID Network ID – Identifies the subnet Host ID – Identifies the host within that subnet Introducing TCP/IP Understanding Subnetting and Subnet Masks (cont.) Subnet masks – Divide IP addresses into network IDs and host IDs and can be used to partition networks into subnets Example of a subnet mask for the IP address 10.23.132.23: 255.0.0.0 Introducing TCP/IP Converting Octets from Decimal to Binary In Calculator in the View menu, click Scientific. • Key the decimal octet. • In the upper left just below the text box, select Bin. The number is displayed in binary. • Add zeros to the left side until there are eight digits. Introducing TCP/IP Converting Octets from Binary to Decimal Open Calculator in Scientific view. • Select Bin in the upper left. • Key the binary value, with the exclusion of leading 0s. • Select Dec in the upper left. The value is displayed in decimal. Introducing TCP/IP Combining Octets Using a Logical AND Compare the first digit of each octet, and follow these rules. 1 AND 1 = 1 0 AND 0 = 0 0 AND 1 = 0 Do the same for the remaining 7 digits. Introducing TCP/IP Applying a Logical NOT to an Octet Replace each 1 with a 0. Replace each 0 with a 1. Introducing TCP/IP IP Address Classes IP Address Class Default Subnet Mask Purpose Class A 255.0.0.0 Very large networks Class B 255.255.0.0 Medium to large networks Class C 255.255.255.0 Small networks Introducing TCP/IP Calculating a Network ID Decimal Octets Binary Octets IP Address 192.168.0.54 11000000.10101000.00000000. 00110110 Subnet mask 255.255.255.1 28 11111111.11111111.11111111. 10000000 Network ID (IP address AND subnet mask) 192.168.0.0 11000000.10101000.00000000. 00000000 Introducing TCP/IP Calculating a Host ID Decimal Octets Binary Octets IP Address 192.168.0.54 11000000.10101000.00000000. 00110110 NOT subnet mask 0.0.0.127 00000000.00000000.00000000. 01111111 Host ID (IP address AND NOT subnet mask) 0.0.0.54 00000000.00000000.00000000. 00110110 Introducing TCP/IP Understanding Classless InterDomain Routing Notation Classless Inter-Domain Routing (CIDR) notation – Common way of expressing a subnetted network address, from which you can derive the IP addresses and subnet mask for the hosts on each network Example: 192.168.255.0/26 Introducing TCP/IP Understanding DNS Domain Name System (DNS) – Hierarchical naming convention for identifying TCP/IP hosts on a network Fully qualified domain names (FQDNs) – User-friendly names to which IP addresses are mapped in DNS Example FQDN: client42.northwind.contoso.com Understanding DNS DNS Hierarchy Level Examples Notes root (.) The root domain is represented by the “.” Character. It is not expressed in FQDNs. Top-level domain net, org, com, uk, gov There are many other TLDs, most of them country codes. Second-level domain microsoft, contoso Typically the second-level domain is a good indication of who owns the FQDN. Additional domain levels Northwind There can be any number of additional levels in a FQDN. Host name client42, www Yes, www is a host name. Most FQDNs with www designated as the host resolve to the IP address of one or more web servers. Introducing TCP/IP DNS Caching Both DNS clients and servers can cache DNS name resolutions. DNS caching – After the answer is found to a resolution, clients and servers store it locally for some time in case they need it. In this way, they won’t have to look it up again, which increases performance. Understanding DNS Understanding DHCP Dynamic Host Control Protocol (DHCP) – Protocol that DHCP clients, such as computers running Windows Vista, can use to request and lease IP addresses from a DHCP server. The client can also use DHCP to request DHCP options. Understanding DHCP Understanding DHCP (cont.) DHCP client – Machine that uses DHCP to request an IP address lease and other information, called DHCP options DHCP server – Allocates IP addresses from a pool of IP addresses to DHCP clients and optionally offers supporting information to DHCP clients, called DHCP options Understanding DHCP Understanding DHCP (cont.) DHCP option – Piece of information that DHCP servers can optionally offer to DHCP clients, including default gateway IP addresses and IP addresses for DNS name servers DHCP lease – Entire package that a DHCP client receives from a DHCP server Understanding DHCP Understanding DHCP (cont.) The process of a DHCP client requesting and receiving a DHCP lease from a DHCP server is completed in the following four steps. DHCPDISCOVER – The DHCP client broadcasts a request for a DHCP lease. DHCPOFFER – DHCP servers on the network offer DHCP leases of specific IP addresses to the DHCP client. Understanding DHCP Understanding DHCP (cont.) • Requesting and receiving a DHCP lease (cont.) DHCPREQUEST – The DHCP client chooses from which DHCP server to obtain a DHCP lease and broadcasts that it has chosen that server in a broadcast message. The other offering DHCP servers receive the DHCPREQUEST message and return the IP addresses they offered to their pools of available IP addresses for lease. Understanding DHCP Understanding DHCP (cont.) • Requesting and receiving a DHCP lease (cont.) DHCPACK – The chosen DHCP server also receives the DHCPREQUEST message. It sends an acknowledgement to the DHCP client and assigns it any configured DHCP options. The client configures its TCP/IP settings with the IP address and DHCP options supplied by the DHCP server. Understanding DHCP Understanding DHCP (cont.) • Automatic Private IP Addressing (APIPA) – Another scheme for assigning IP addresses automatically. It is a part of Windows operating systems. If you configure a computer to automatically obtain an IP address and no DHCP server is available, you will receive an APIPA address. APIPA addresses always start with the octets 169.254. Understanding DHCP Configuring IPv4 TCP/IP Network Settings Manually Properties dialog box for an example connection Configuring TCP/IP Network Settings Configuring IPv4 TCP/IP Network Settings Manually (cont.) Example settings for a Class C private network with 64 subnets Configuring TCP/IP Network Settings Using DHCP to Configure TCP/IP Settings Automatically Open the Properties dialog box for the connection you want to configure. • In the ConnectionName Properties dialog box, select Internet Protocol Version 4 (TCP/IPv4), and then click Properties. • Select Obtain an IP address automatically. Configuring TCP/IP Network Settings Using DHCP to Configure TCP/IP Settings Automatically (cont.) Select one of the following: Obtain DNS server addresses automatically Use the following DNS server addresses Configuring TCP/IP Network Settings Configuring an Alternate IP Address Example alternate IP address settings for a class A private network Configuring TCP/IP Network Settings Configuring Windows Vista Wired Network Policy in Group Policy You can configure network settings through Group Policy in the Computer Configuration > Windows Settings > Security Settings > Wired Network (IEEE 802.3) Policies folder of Group Policy objects (GPOs). Configuring TCP/IP Network Settings Configuring Vista Wired Network Policy in Group Policy (cont.) The Security tab of the WiredNetworkPolicyName Properties dialog box Configuring TCP/IP Network Settings Configuring Vista Wired Network Policy in Group Policy (cont.) In the Select a network authentication method drop-down list, select one of the following: Smart Card or other certificate – Select this option if you want wireless users to authenticate with a smart card. Protected EAP (PEAP) – Protected Extensible Authentication Protocol. Usernames and passwords fall into this authentication category. Configuring TCP/IP Network Settings Configuring Vista Wired Network Policy in Group Policy (cont.) In the Authentication Mode drop-down list, select one of the following: User re-authentication – Authentication uses the computer’s credentials when a user is not logged on. When a user logs on, reauthentication using the user’s credentials is performed. Computer Authentication – Authentication uses the computer’s credentials. Configuring TCP/IP Network Settings Configuring Vista Wired Network Policy in Group Policy (cont.) • In the Authentication Mode drop-down list, select one of the following (cont.): User authentication – Authentication uses the computer’s credentials until a new wireless access point is connected to, at which time reauthentication takes place with the user’s credentials. Configuring TCP/IP Network Settings Configuring Vista Wired Network Policy in Group Policy (cont.) • In the Authentication Mode drop-down list, select one of the following (cont.): Guest authentication – All connections to the network are regulated by the settings for the Guest user account. This is the least restrictive and most flexible authentication and is recommended when you are creating a wireless policy for a network where guests are welcome. Configuring TCP/IP Network Settings Wireless Networking and Security Security is very important in wireless networks because anybody with a receiver can potentially log on to the network if security is weak. Understanding and Configuring Wireless Networking and Security Wireless Networking and Security (cont.) In Vista, networks are differentiated into two broad classes. Infrastructure networks – Networks that connect to wireless access points on your network Ad-hoc networks – Networks that you can form on the fly with other wireless users Understanding and Configuring Wireless Networking and Security Wireless Networking and Security (cont.) Wired Equivalent Policy (WEP) – Least secure technology. It requires a WEP key, which you supply to the wireless devices that connect to the access point. WEP has known vulnerabilities that enable hackers to crack it with retail hardware. WEP is not recommended for enterprise use. Understanding and Configuring Wireless Networking and Security Wireless Networking and Security (cont.) Wi-Fi Protected Access (WPA) – Designed to eliminate the known security flaws of WEP. Wireless devices and the access point use a preshared key (PSK) that can be either a 256-bit number or an alphanumeric password between 8 and 63 characters long. Understanding and Configuring Wireless Networking and Security Wireless Networking and Security (cont.) Wi-Fi Protected Access 2 (WPA2) – Preferred security technology for enterprise wireless networks. It uses 802.1X-based authentication and Advanced Encryption Standard (AES) encryption. Understanding and Configuring Wireless Networking and Security Wireless Networking and Security (cont.) There are two versions of WPA2. WPA2-personal WPA2-enterprise WPA2-enterprise requires that a user authenticate on the network before wireless connectivity is granted. Understanding and Configuring Wireless Networking and Security Wireless Networking and Security (cont.) Enterprise Single Sign-on – Enables users to authenticate to the wireless network access point and the domain in a single step. In Enterprise Single Sign-on, 802.1X authentication to the wireless network precedes logon to the domain, and users are only prompted for wireless credential information if needed. Understanding and Configuring Wireless Networking and Security Configuring Wireless Networking in Group Policy You can configure wireless networking in Group Policy in the Computer Configuration > Windows Settings > Security Settings > Wireless Network (IEEE 802.11) Policies node in Group Policy objects. Understanding and Configuring Wireless Networking and Security Configuring Wireless Policy for Infrastructure Networks To configure Windows Vista wireless policy, you must first create a new Vista wireless policy in a GPO. You can only have one Vista policy per GPO, but you can configure policies for multiple wireless networks in the single policy. Understanding and Configuring Wireless Networking and Security Configuring Wireless Policy for Infrastructure Networks (cont.) Connection tab of the New Profile properties dialog box for an infrastructure wireless network profile Understanding and Configuring Wireless Networking and Security Configuring Wireless Policy for Infrastructure Networks (cont.) Security tab of the New Profile properties dialog box Understanding and Configuring Wireless Networking and Security Configuring Wireless Policy for Infrastructure Networks (cont.) Network Permission tab of the WirelessPolicyName Properties dialog box with example settings configured Understanding and Configuring Wireless Networking and Security Understanding and Securing Data with IPSec Internet Protocol Security (IPsec) – Suite of protocols for securing communication between two TCP/IP hosts. Understanding and Securing Data with IPsec by Using Windows Firewall Understanding and Securing Data with IPSec (cont.) Data integrity – Ensuring that the transmitted data is identical to the data received Encryption – Making the data unreadable by anybody but the intended reader Authentication – When IPsec validates the identity of both hosts in an IPsec session Understanding and Securing Data with IPsec by Using Windows Firewall Understanding and Securing Data with IPSec (cont.) The two hosts in an IPsec session must share a common key with which to decrypt the encrypted data. Windows Vista does not exchange the key, but instead exchanges information that each host uses to generate identical keys locally. The algorithm used to do this is called the DiffieHellman algorithm (DH). Understanding and Securing Data with IPsec by Using Windows Firewall Understanding and Securing Data with IPSec (cont.) Authentication methods offered by Windows Vista and commonly used in IPsec include the following: Kerberos V5 NTLMv2 Certificate Pre-shared key Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec You can use the New Connection Security Rule Wizard to help you create connection security rules. The wizard offers five rule types. Isolation – Uses authentication criteria that you supply to restrict connections and thus isolate computers from other computers, such as those outside your domain Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) The wizard offers five rule types (cont.). Authentication exemption – Used to exempt computers from IPsec connection restrictions rather than subject them to IPsec connection restrictions. It is often used to grant access to infrastructure computers, such as domain controllers and DHCP servers, that computers need to communicate with before authenticating. Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) The wizard offers five rule types (cont.). Server-to-server – Used to authenticate the communications between two specific computers, between two groups of computers, between two subnets, or between a specific computer and a group of computers or a subnet Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) The wizard offers five rule types (cont.). Tunnel – Used for securing communications between two peer computers through tunnel endpoints, such as virtual private networking (VPN) Custom – Used to create custom IPsec configurations Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) New Connection Security Rule Wizard Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) Endpoints page of the New Security Connection Wizard with example settings Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) The Requirements page includes: Request authentication for inbound and outbound connections Require authentication for inbound connections and request authentication for outbound connections Require authentication for inbound and outbound connections Do not authenticate Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) The Authentication Method page includes: Default Computer and user (Kerberos V5) Computer (Kerberos V5) Computer certificate Advanced Understanding and Securing Data with IPsec by Using Windows Firewall Using Windows Firewall to Implement IPSec (cont.) The Profile page includes: Domain check box Private check box Public check box Understanding and Securing Data with IPsec by Using Windows Firewall You Learned TCP/IP is the most commonly used network communications protocol in use today. It is used on the Internet and in most other networks, such as enterprise networks. IP addresses are how hosts in a TCP/IP network identify each other. Subnetting enables you to split a network into multiple networks by using a subnet mask. Summary You Learned (cont.) You learned how to convert decimal octets into binary octets and vice-versa. You learned how to perform AND and NOT operations on binary octets. Domain Name System is a user-friendly naming convention. DNS names, called fully qualified domain names, are converted into IP addresses by DNS name servers so that TCP/IP hosts can communicate. Summary You Learned (cont.) Dynamic Host Control Protocol is a protocol by which TCP/IP hosts can automatically obtain IP addresses and supporting information. You learned how to configure IPv4 TCP/IP network settings manually. You learned how to use DHCP to configure IPv4 TCP/IP settings automatically. Summary You Learned (cont.) You learned how to configure an alternate IP address. You learned how to configure Windows Vista wired network policy through Group Policy. You learned the importance of wireless network security and how to implement it. You learned how to configure Windows Vista wireless policy for infrastructure networks. Summary You Learned (cont.) IP security protocol in Windows Vista can be implemented using Windows Firewall with Advanced Security. You can configure custom IP security policies to fit a variety of requirements. You learned how to create connection security rules. Summary