* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download COS 338_day17
Computer and network surveillance wikipedia , lookup
Cross-site scripting wikipedia , lookup
Security-focused operating system wikipedia , lookup
Quantum key distribution wikipedia , lookup
One-time pad wikipedia , lookup
Unix security wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cyberattack wikipedia , lookup
Public-key cryptography wikipedia , lookup
Computer security wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Wireless security wikipedia , lookup
Web of trust wikipedia , lookup
Mobile security wikipedia , lookup
Cryptanalysis wikipedia , lookup
Cryptography wikipedia , lookup
Denial-of-service attack wikipedia , lookup
History of cryptography wikipedia , lookup
Certificate authority wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Digital signature wikipedia , lookup
Authentication wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
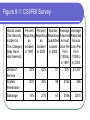
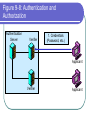
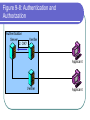
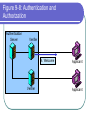
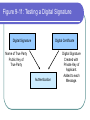
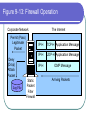
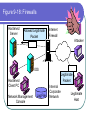
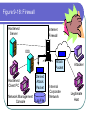
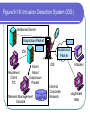
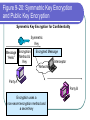
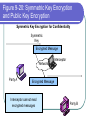
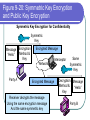
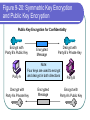
COS 338 Day 16 DAY 16 Agenda Capstone Proposals Overdue 3 accepted, 3 in mediation Capstone progress reports still overdue I forgot to mark in calendar so I will grant a reprieve Second capstone progress report over due Lab 5 write-up not graded Will be corrected by next class Assignment 5 Due Today we will begin discussing Security Security Chapter 9 Copyright 2004 Prentice-Hall Panko’s Business Data Networks and Telecommunications, 5th edition Trends in Computer and Network Security Figure 9-1: CSI/FBI Survey Survey conducted by the Computer Security Institute (www.gocsi.com). Based on replies from 530 U.S. Computer Security Professionals. If fewer than twenty firms reported quantified dollar losses, data for the threat are not shown. Link to 2005 CSI/FBI Survey Figure 9-1: CSI/FBI Survey Had at Least Percent Percent Number Average One Security Reporting Reporting Reporting Reported Incident in an an Quantified Annual This Category Incident Incident Losses Loss Per (May Have in 1997 in 2003 in 2003 Firm Had Several) (1000s) in 1997 Viruses Insider Abuse of Net Access Average Reported Annual Loss Per Firm (1000s) in 2003 82% 82% 254 $76 $200 Not Asked 80% 180 Not Asked $136 Figure 9-1: CSI/FBI Survey Had at Least Percent Percent Number Average One Security Reporting Reporting Reporting Reported Incident in an an Quantified Annual This Category Incident Incident Losses Loss Per (May Have in 1997 in 2003 in 2003 Firm Had Several) (1000s) in 1997 Average Reported Annual Loss Per Firm (1000s) in 2003 Laptop Theft 58% 59% 250 $38 $47 Unauthorized Access by Insiders 40% 45% 72 Not Asked $31 Figure 9-1: CSI/FBI Survey Had at Least Percent Percent Number Average One Security Reporting Reporting Reporting Reported Incident in an an Quantified Annual This Category Incident Incident Losses Loss Per (May Have in 1997 in 2003 in 2003 Firm Had Several) (1000s) in 1997 Average Reported Annual Loss Per Firm (1000s) in 2003 Denial of Service System Penetration 24% 42% 111 $77 $1,427 20% 36% 88 $132 $56 Sabotage 14% 21% 61 $164 $215 Figure 9-1: CSI/FBI Survey Had at Least Percent Percent Number Average One Security Reporting Reporting Reporting Reported Incident in an an Quantified Annual This Category Incident Incident Losses Loss Per (May Have in 1997 in 2003 in 2003 Firm Had Several) (1000s) in 1997 Average Reported Annual Loss Per Firm (1000s) in 2003 Theft of Proprietary Information 20% 21% 61 $954 $2,700 Financial Fraud 12% 15% 61 $958 $329 Figure 9-1: CSI/FBI Survey Had at Least Percent Percent One Security Reporting Reporting Incident in an an This Category Incident Incident (May Have in 1997 in 2003 Had Several) Number Reporting Quantified Losses in 2003 Average Reported Annual Loss Per Firm (1000s) in 1997 Average Reported Annual Loss Per Firm (1000s) in 2003 Telecom Fraud 27% 10% 34 Not Asked $50 Telecom Eavesdropping 11% 6% 0 Not Asked Not Asked 3% 1% 0 Not Asked Not Asked Active Wiretap Figure 9-1: CSI/FBI Survey Conclusion Attacks are like multiple poisons Several of them are fatal Defense is difficult Major Attacks Viruses and Worms Human Hacking (Break-Ins) Denial-of-Service Attacks Figure 9-2: Viruses and Worms Viruses Pieces of code that attach to other programs Virus code executes when infected programs execute Infect other programs on the computer Spread to other computers by e-mail attachments, webpage downloads, etc. Figure 9-2: Viruses and Worms Viruses Many viruses spread themselves by sending fake email messages with infected attachments Antivirus programs are needed to scan arriving files Users often fail to keep their computer antivirus programs up to date Antivirus filtering on the e-mail server works even if users are negligent How Viruses Work Figure 9-2: Viruses and Worms Worms Complete programs Self-propagating worms identify victim hosts, jump to them, and install themselves Can do this because hosts have vulnerabilities Vendors develop patches for vulnerabilities but companies often fail to apply them Figure 9-2: Viruses and Worms Worms Worms take advantage of specific vulnerabilities Firewalls can stop many worms by forbidding access to most ports E-mail worms can get around antivirus filtering Famous Worms Morris worm – the first worm Code Red – went after IIS servers Melissa – e-mail worm Slammer - SQL worm Blaster – Windows RPC worm MyDoom – another e-mail worm that creates a BackDoor on your computer Figure 9-2: Viruses and Worms Blended Threats Combine the spreading characteristics of viruses and worms Payloads Programs that can do damage to infected hosts Erase hard disks, send users to pornography sites if they mistype a URL Trojan horses: exploitation programs disguise themselves as system files Figure 9-3: Human Break-Ins (Hacking) Human Break-Ins: Viruses and worms rely on one main attack method Humans can keep trying different approaches until they succeed Hacking Breaking into a computer Hacking is intentionally using a computer resource without authorization or in excess of authorization Prosecutable if do a certain amount of damage Figure 9-3: Human Break-Ins (Hacking) Scanning Phase Send attack probes to map the network and identify possible victim hosts Like a robber casing a neighborhood Finds active IP addresses Identifies type of computer at that address via open ports, etc. Nmap program is popular (Figure 9-4) Figure 9-4: Nmap Scanning Output IP Range to Scan Type of Scan Identified Host and Open Ports Figure 9-3: Human Break-Ins (Hacking) The Exploit The Term “Exploit” is Used in Two Ways The actual break-in Exploit is the program used to make the break-in Super user accounts (administrator and root) can do anything If application running with super user privileges is compromised, the attacker gains super user privileges Figure 9-3: Human Break-Ins (Hacking) After the Break-In Become invisible by deleting log files http://www.rootkit.com/ Create a backdoor (way to get back into the computer) Backdoor account—account with a known password and super user privileges Backdoor program—program to allow reentry; usually Trojanized Do damage at leisure Denial-of-Service (DoS) Attacks Make a computer or network unavailable to users An exploding threat Rarely: sending a single message to bring down a computer Usually: overload a victim with a flood of messages Figure 9-5: Distributed Denial-of-Service (DDoS) Flooding Attack Attack Command Handler Attacker 1.34.150.37 Zombie Attack Command Attack Command Attack Command Attack Packet Attack Packet Victim 60.168.47.47 Zombie Attack Packet Handler Attack Command Zombie Attackers Figure 9-6: Types of Attackers Traditional attackers: Curious hackers Disgruntled employees and ex-employees Growing number of criminal attackers Potential for far more massive attacks Cyberterror attacks by terrorists Cyberwar by nations Security Management Figure 9-7: Planning Principles Security is a Management Issue, Not a Technical Issue Without good management, technology cannot be effective. Like a car. If you don’t know how to drive, not likely to be able to use effectively. Soldiers are not just given weapons. Must be trained extensively in tactics, etc. Figure 9-7: Planning Principles Plan-Protect-Respond Cycle Three phases endlessly repeating Planning: preparing for defense Protecting: implementing planned protections Responding: stopping attacks and repairing damage when protections fail Figure 9-7: Planning Principles Risk Analysis Cost of protections should not exceed probable damage Annual probability of damage Damage from a successful incident (Say, $50,000) Times the annual probability of success (say 10%) Gives the probable annual loss ($5,000) Figure 9-7: Planning Principles Risk Analysis Cost of protection If a protection can reduce the annual probability of damage by a certain amount, up to this amount can be spent on the protection Example Protection A can reduce the annual probability of damage by 50% ($2,500) If Protection A costs $1,000 per year, use it. If Protection A costs $4,000 per year, don’t use it. Figure 9-7: Planning Principles Comprehensive Security Attacker is intelligent Attacker only has to find one weakness Firm needs comprehensive security to close all avenues of attack Figure 9-7: Planning Principles Defense in Depth Every protection breaks down sometimes Attacker should have to break through several lines of defense to succeed Providing this protection is called defense in depth Defense 1 (fails) Defense 2 Authentication Figure 9-8: Authentication and Authorization Authentication Server Verifier 1. Credentials (Password, etc.) Applicant Verifier Applicant Figure 9-8: Authentication and Authorization Authentication Server 2. OK? Verifier Applicant Verifier Applicant Figure 9-8: Authentication and Authorization Authentication Server Verifier 3. OK and Authorizations Verifier Applicant Applicant Figure 9-8: Authentication and Authorization Authentication Server Verifier 4. Welcome Verifier Applicant Applicant Figure 9-9: Password Authentication Passwords Strings of characters Typed to authenticate use of a username (account) on a computer Benefits Ease of use for users (familiar) Inexpensive because built into operating systems Figure 9-9: Password Authentication Often weak (easy to crack) Word and name passwords are common Can be cracked quickly with dictionary attack Passwords should be complex Mix case, digits, and other keyboard characters ($, #, etc.) Can only be cracked with brute force attacks (trying all possibilities) Figure 9-9: Password Authentication Passwords should be long Six to eight characters minimum Each added character increases the brute force search time by a factor of up to 75 http://www.umfk.maine.edu/password/password .ppt Figure 9-10: Digital Certificate Authentication Digital Certificate User gets secret private key and non-secret public key Digital certificates give the name of a true party and his or her public key Figure 9-10: Digital Certificate Authentication Testing a Digital Signature Applicant performs a calculation with his or her private key Verifier tests calculation using the public key found in the true party’s digital certificate If the test succeeds, the applicant must be the true party Figure 9-11: Testing a Digital Signature Digital Signature Digital Certificate Name of True Party Public Key of True Party Authentication Digital Signature Created with Private Key of Applicant. Added to each Message. Figure 9-10: Digital Certificate Authentication Strong Authentication The strongest method today Expensive and Time-Consuming to Implement Software must be added to clients and servers, and each computer must be configured Expensive because there are so many clients in a firm Figure 9-10: Digital Certificate Authentication Client Weaknesses Sometimes, only server gets digital certificate Client uses passwords or something else Figure 9-11: Testing a Digital Signature Verifier must test the digital signature with the public key of the true party. If the test succeeds, the applicant must have the true party’s private key. Only the true party should know this private key; so the applicant must be the true party. Figure 9-12: Biometric Authentication Biometric Authentication Based on bodily measurements Promises to dramatically simplify authentication Figure 9-12: Biometric Authentication Fingerprint Scanning Simple and inexpensive Substantial error rate (misidentification) Often can be fooled fairly easily by impostors Dominates biometrics today Figure 9-12: Biometric Authentication Iris Scanners Scan the iris (colored part of the eye) Irises are complex, so strong authentication Expensive (Do NOT shine light in your eyes; scanner is a camera.) Figure 9-12: Biometric Authentication Face Recognition Camera allows analysis of facial structure Can be done surreptitiously— without the knowledge or consent of person being scanned Very high error rate and easy to fool Figure 9-12: Biometric Authentication Error Rates and Deception Error and deception rates are higher than vendors claim Usefulness of biometrics is uncertain Firewalls, IDSs, and IPSs Figure 9-13: Firewall Operation Corporate Network Permit (Pass) Legitimate Packet Deny (Drop) Attack Packet Log File Static Packet Filter Firewall The Internet IP-H TCP-H Application Message IP-H UDP-H Application Message IP-H ICMP Message Arriving Packets Figure 9-14: Access Control List (ACL) for a Packet Filter Firewall 1. If destination IP address = 60.47.3.9 AND TCP destination port = 80 OR 443, PASS 2. If ICMP Type = 0, PASS [connection to a public webserver] [allow incoming echo reply messages] 3. If TCP destination port = 49153 AND 65535, PASS [allow incoming packets to ephemeral TCP port numbers] Figure 9-14: Access Control List (ACL) for a Packet Filter Firewall 4. If UDP destination port = 49153 AND 65535, PASS [allow incoming packets to ephemeral UDP port numbers] 5. DENY ALL [deny all other packets] Figure 9-15: Stateful Firewall Default Operation Internally initiated communication is allowed. Internal Host X Externally initiated communication is stopped. External Host Figure 9-16: Application Firewalls Application Firewalls Examine application layer messages in packets Packet filter firewalls and stateful firewalls do not look at application messages at all This makes them vulnerable to certain attacks Figure 9-16: Application Firewalls Application Fidelity Requiring the application using a well-known port to be the application that is supposed to use that port For instance, if an application uses Port 80, application firewall requires it to be HTTP, not a peer-to-peer file transfer program or something else This is called enforcing application fidelity Figure 9-16: Application Firewalls Limited Content Filtering Allow FTP Get commands but stop FTP Put commands Do not allow HTTP connections to black-listed (banned) websites E-mail application server may delete all attachments Figure 9-16: Application Firewalls Antivirus Scanning Few application firewalls do antivirus filtering Packets also must be passed through separate antivirus filtering programs Figure 9-17: Defense in Depth with Firewalls Internet Client with Host Firewall Software Application Firewall e-mail, HTTP, etc. Main Firewall: Stateful Inspection Firewall Screening Border Router with Packet Filter Firewall Software Site Figure 9-18: Firewalls Hardened Server Allowed Legitimate Packet Internet Firewall Attacker IDS Legitimate Packet Hardened Client PC Network Management Console Log File Internal Corporate Network Legitimate Host Figure 9-18: Firewall Hardened Server Internet Firewall IDS Attack Packet Hardened Client PC Denied Attack Packet Network Management Log File Console Internal Corporate Network Attacker Legitimate Host Figure 9-18: Intrusion Detection System (IDS) Hardened Server Suspicious Packet Suspicious Packet IDS Hardened Client PC Alarm About Suspicious Packet Network Management Console Log File IDS Internal Corporate Network Attacker Legitimate Host Figure 9-18: Intrusion Prevention Systems (IPSs) Firewalls stop simple attacks IDSs can identify complex attacks involving multiple packets But many false positives (false alarms) Intrusion prevention systems (IPSs) Like IDSs, can identify complex attacks Unlike IDSs, also stop these attacks Only allowed to stop clearer complex attacks Figure 9-19: Cryptographic System (SSL/TLS) Applicant (Customer Client) without Digital Certificate Verifier (Merchant Webserver) with Digital Certificate Provides Protection at Transport Layer Protects all Application Traffic That is SSL/TLS-Aware (Mostly HTTP) Figure 9-19: Cryptographic System (SSL/TLS) Applicant (Customer Client) without Digital Certificate Verifier (Merchant Webserver) with Digital Certificate 1. Negotiation of Security Options (Brief) 2. Merchant Authenticates Self to Customer Uses a Digital Certificate Customer Authentication Is Optional and Uncommon Figure 9-19: Cryptographic System (SSL/TLS) Applicant (Customer Client) without Digital Certificate Verifier (Merchant Webserver) with Digital Certificate 3. Client Generates Random Session Key Client Sends to Server Encrypted by Merchant’s Public Key 4. Ongoing Communication with Confidentiality and Merchant Digital Signatures Figure 9-19: Cryptographic System (SSL/TLS) Perspective Initial Hand-Shaking Phases are Very Brief (Milliseconds) The Last Phase (Ongoing Communication) Is Almost All Total Communication Encryption for Confidentiality Figure 9-20: Symmetric Key Encryption and Public Key Encryption Symmetric Key Encryption for Confidentiality Symmetric Key Message Encryption Method & “Hello” Key Encrypted Message Interceptor Network Party A Party B Encryption uses a non-secret encryption method and a secret key Figure 9-20: Symmetric Key Encryption and Public Key Encryption Symmetric Key Encryption for Confidentiality Symmetric Key Encrypted Message Interceptor Network Party A Encrypted Message Interceptor cannot read encrypted messages Party B Figure 9-20: Symmetric Key Encryption and Public Key Encryption Symmetric Key Encryption for Confidentiality Symmetric Key Message Encryption Method & “Hello” Key Encrypted Message Interceptor Network Party A Encrypted Message Receiver decrypts the message Using the same encryption message And the same symmetric key Same Symmetric Key Decryption Message Method & “Hello” Key Party B Figure 9-20: Symmetric Key Encryption and Public Key Encryption Public Key Encryption for Confidentiality Encrypt with Party B’s Public Key Party A Encrypted Message Decrypt with Party B’s Private Key Note: Four keys are used to encrypt and decrypt in both directions Decrypt with Party A’s Private Key Encrypted Message Party B Encrypt with Party A’s Public Key Figure 9-21: Other Aspects of Protection Hardening Servers and Client PCs Setting up computers to protect themselves Server Hardening Patch vulnerabilities Minimize applications running on each server Use host firewalls Backup so that restoration is possible Figure 9-21: Other Aspects of Protection Hardening Servers and Client PCs Client PC Hardening As with servers, patching vulnerabilities, minimizing applications, having a firewall, and implementing backup Also, a good antivirus program that is updated regularly Client PC users often make errors or sabotage hardening techniques Figure 9-21: Other Aspects of Protection Vulnerability Testing Protections are difficult to set up correctly Vulnerability testing is attacking your system yourself or through a consultant There must be follow-up to fix vulnerabilities that are discovered Incident Response Dealing with attacks that succeed Figure 9-22: Incident Response Response Phases Detecting the attack If not detected, damage will continue unabated IDS or employee reports are common ways to detect attacks Stopping the attack Depends on the attack Reconfiguring firewalls may work Figure 9-22: Incident Response Response Phase Repairing the damage Sometimes as simple as running a cleanup utility Sometimes, must reformat a server disk and reinstall software Can be very expensive if the attacker has done much damage Figure 9-22: Incident Response Response Phase Punishing the attackers Easier to punish employees than remote attackers Forensic tools collect data in a manner suitable for legal proceedings Figure 9-22: Incident Response Major Attacks and CSIRTs Major attacks cannot be handled by the on-duty staff On-duty staff convenes the computer security incident response team (CSIRT) CSIRT has people from security, IT, functional departments, and the legal department Figure 9-22: Incident Response Disasters Natural and attacker-created disasters Can stop business continuity (operation) Data backup and recovery are crucial for disaster response Dedicated backup facilities versus real-time backup between different sites Figure 9-22: Incident Response Disasters Business continuity recovery is broader Protecting employees Maintaining or reestablishing communication Providing exact procedures to get the most crucial operations working again in correct order Topics Covered Topics Covered A Wide Variety of Attacks Viruses and Worms Hacking (Break-in) Scanning Break-In Exploitation (delete log files, create backdoors, do damage) Denial-of-Service (DoS) Attacks Employee misuse of the Internet Growing in frequency (and viciousness) Topics Covered A Wide Variety of Attackers Traditional Attackers Wizard attackers Employees and Ex-Employees Criminals (Exploding) Cyberterrorists and National Governments Topics Covered A Management Issue, not a Technical Issue Technology does not work automatically Planning Risk analysis Comprehensive security Defense in depth Topics Covered Authentication and Authorization Authentication servers give consistency Passwords (weak) Digital signatures and digital certificates High security but difficult to implement Biometric authentication Could eliminate passwords Error rates and deception Topics Covered Firewalls Drop and log packets Packet filter firewalls and ACLs Stateful firewalls (dominate for main firewalls today) Application firewalls filter application content Usually do NOT provide antivirus filtering Defense in depth with multiple firewalls IDSs to detect complex attacks IPSs to stop some complex attacks Topics Covered Cryptographic Systems Negotiate security parameters Authentication Key exchange Ongoing communication (dominates) SSL/TLS Cryptographic system used in e-commerce Protects HTTP communication Topics Covered Encryption for Confidentiality Symmetric key encryption Both sides use the same symmetric key Dominates because fast and efficient Public key encryption Each side has a secret private key and a nonsecret public key Topics Covered Hardening Servers and Client PCs Patching vulnerabilities Minimize applications Host firewalls Backup Clients: antivirus filtering (users may sabotage) Vulnerability Testing Topics Covered Incident Response Detection, stopping, repair, punishment CSIRTs for major attacks to big for the on-duty staff to handle Disaster response and business continuity recovery