* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Performance Evaluation of VoIP and TCP over wireless networks
Distributed firewall wikipedia , lookup
Airborne Networking wikipedia , lookup
Wireless USB wikipedia , lookup
Network tap wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
IEEE 802.11 wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Quality of service wikipedia , lookup
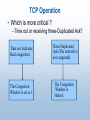
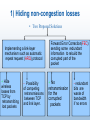
Performance Evaluation of VoIP and TCP over wireless networks Presented By : Ala’ Khalifeh Friday, March,17,2006 University of California-Irvine Note: 1) This presentation is a brief description for the papers I have read and mentioned in the reference page. 2)I have sent other presentation which I have prepared but did not present. The Big Picture Industry Approach The infrastructure of the Next generation Internet is expected to provide an interface to the wireless services through well-defined standards and schemes. The Third Generation Partnership Project (3GPP/3GPP2) has suggested the the IP Multimedia Subsystem (IMS) standard . IMS defines a generic architecture for offering Voice over IP (VoIP) and multimedia services over the wireless environment and define the architecture of integrating the wireless network with the Internet. For operators, IMS takes the concept of layered architecture one step further by defining a horizontal architecture. It is well integrated with existing voice and data networks, while adopting many of the key benefits of the IT domain. IMS Architecture This is on the service providers side, on the the userend sides, many mobile companies are designing their new mobile sets to make them capable of conducting VoIP calls over wireless network and to support many multimedia services on the mobile sets. One important thing to consider is the performance of TCP on carrying data over the wireless environment,on one hand, and the performance of the real-time services such as VoIP that are carried on top on UDP on the other hand, and finally the co-existent between the two . The Roadmap of my research : VoIP Technology TCP Over Wireless Problems TCP Behaviour Wireless Tech. VoIP over Wireless Problems Suggested Solutions The Network Architecture VoIP Requirements • Definition: Using the Internet to carry phone conversations, known as Internet telephony or voice over IP (VoIP). • Quality of Service Requirements – End-to-end delay, or called latency.(150 and 400 ms ) – Packet loss • uses UDP as transport protocol. • Packet loss Not to exceed 10-15 %) – called jitter delay TCP Operation • TCP is the main transport protocol designed for the wired environment • Reliable transmission (Require Ack). • Uses mechanisms for congestion control and detection (Congestion Window). • TCP uses an Algorithm called AIMD (Additive Increase, Multiplicative Decrease) for changing its window size. • The congestion window climbs exponentially fast during slow start and hits the threshold . • The congestion window then climbs linearly until loss occurs, two scenarios might take place – The transmitor does not receive an ACK within the time-out period – The transmitor receive duplicated ACK (3 duplicated ACK ).(ON BOARD ILLUSTRATION) TCP Operation • Which is more critical ? – Time out or receiving three-Duplicated Ack? Time out indicates Real congestion The Congestion Window is set to 1 Three Duplicated Ack (The network is not congested) The Congestion Window is Halved TCP Congestion Window Wireless Networks • 802.11 Protocols Standards – IEEE 802 Network Technology Family Tree 802.11 is a member of the IEEE 802 family, which is a series of specifications for local area network (LAN) technologies. WiFi Network Architecture Accessing The Network CSMA/CD: carrier sensing, deferral as in CSMA – collisions detected within short time – colliding transmissions aborted, reducing channel wastage • collision detection: – easy in wired LANs: measure signal strengths, compare transmitted, received signals – difficult in wireless LANs: receiver shut off while transmitting • human analogy: the polite conversationalist • Why no collision detection in Wireless? – difficult to receive (sense collisions) when transmitting due to weak received signals (fading) – can’t sense all collisions in any case: hidden terminal, fading • Goal: avoid collisions: CSMA/C(collision)A(voidance) Accessing The Network RTS/CTS idea: allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames • sender first transmits small request-to-send (RTS) packets to AP using CSMA – RTSs may still collide with each other (but they’re short) • AP broadcasts clear-to-send CTS in response to RTS • CTS heard by all nodes – sender transmits data frame – other stations defer transmissions Avoid data frame collisions completely using small reservation packets TCP over Wireless media • TCP considers the loss of packets as a signal of network congestion and reduces its window • Consequently This results in severe throughput deterioration when packets are lost for other reasons than congestion. • Non congestion losses are mostly caused by transmission errors in the wireless environment. • The solutions proposed to this problem can be divided into two main categories: 1)Hiding the lossy parts of the Internet so that only congestion losses are detected at the source 2)Enhancing TCP with some mechanisms to help it to distinguish between different types of losses 1) Hiding non-congestion losses • Two Proposed Solutions Implementing a link-layer mechanism such as automatic repeat request (ARQ) protocol + Hide wireless losses from TCP by retransmitting lost packets - Possibility of competing retransmissions between TCP and link layer. Forward Error Correction(FEC) sending some redundant information to rebuild the corrupted part of the packet + No retransmission for the corrupted packets - redundant bits are waste of bandwidth if no errors 2) Enhancing the TCP (The Snoop Protocol) • These solutions try to improve the link quality by retransmitting packets at the TCP level rather than at the link level. • Snoop Protocol:One of the most efficient improvement to the TCP protocol. • A TCP agent in the router at the input of the lossy link keeps a copy of every data packet. • It discards this copy when it sees the ACK of the packet • A packet is retransmitted locally when three duplicate ACKs are received or when a local Timeout expires. • This local Timeout is set of course to a value less than that of the source. 2) Enhancing the TCP (The Explicit Loss Notification (ELN)) • Here we inform the source explicitly of the occurrence of a non-congestion loss via an Explicit Loss Notification (ELN signal). • The source reacts by retransmitting the lost packet without reducing its window size. • The difficulty with such solution is that a packet corrupted at the link level is discarded before reaching TCP and then it is difficult to get this information. 2) Enhancing the TCP (Congestion Detection and Avoidance) • Here With some additional mechanisms in the network or at the source the congestion is detected and the throughput is reduced before the overflow of network buffers • Examples of this improvement can be found in the Vegas version of TCP and the Explicit Congestion Notification (ECN) proposals. • If all the sources, receivers and routers are compliant according to Vegas or ECN • Congestion losses will considerably decrease • The remaining losses could be considered as mostly caused by problems other than congestion ( transmission losses) which are retransmitted without window reduction. VoIP over 802.11 (Vo802.11) Performance Requirements Two major technical problems that stand in the way are – 1) low VoIP capacity and high access delay in WLAN. – 2)unacceptable VoIP performance in the presence of coexisting traffic from other applications VoIP over 802.11 (Vo802.11) • IEEE 802.11b, which can support data rates up to 11Mbps. • A VoIP stream typically requires less than 10Kbps. • Ideally, the number of simultaneous VoIP streams that can be supported by an 802.11b WLAN is around 11M/10K = 1100, which corresponds to about 550 VoIP sessions, each with two VoIP streams. • However, it turns out that the current WLAN can only support no more than a few VoIP sessions. For example, if GSM 6.10 codec is used, the maximum number of VoIP sessions that can be supported is 12. VoIP over 802.11 (Vo802.11) • This result is mainly due to the added packet-header overheads as the short VoIP packets traverse the various layers of the standard protocol stack, as well as the inefficiency inherent in the WLAN MAC protocol, as explained below. • A typical VoIP packet at the IP layer consists of 40-byte IP/UDP/RTP headers and a payload ranging from 10 to 30 bytes, depending on the codec used. • So the efficiency at the IP layer for VoIP is already less than 50%. • At the 802.11 MAC/PHY layers, the drop of efficiency is much worse. • Consider a VoIP packet with 30-byte payload. The transmission time for it at 11 Mbps is 30 * 8 / 11 = 22 μ sec VoIP over 802.11 (Vo802.11) • The transmission time for the 40-byte IP/UDP/RTP header is 40 * 8 / 11 = 29 μ sec . • However, the 802.11 MAC/PHY layers have additional overhead of more than 800 μ sec , attributed to the physical preamble, MAC header, MAC backoff time, MAC acknowledgment, and inter transmission times of packets and acknowledgments • As a result, the overall efficiency drops to less than 3% VoIP over 802.11 (Vo802.11) • Even when the number of VoIP sessions is limited to just half of the capacity in an 802.11b WLAN, interference from just one TCP connection will cause unacceptably large increases in the delay and packet loss rate of VoIP traffic. • A WLAN can support voice if you implement the system with high performance and quality of service (QoS) in mind. • The 802.11e group is currently working on a QoS upgrade 802.11e will prioritize traffic on the network, making data give way to voice packets. Supporting QoS : 802.11e • Legacy 801.11 MAC protocol operates on “ Distributed Coordination Function (DCF).”Listen before talk Principle “. • To reduce the probability of collisions, the DCF applies a collision avoidance (CA) mechanism. • 1) After detecting the medium as idle for a minimum duration called DCF interframe space (DIFS) • 2) an additional random time called backoff time. A station initiates its transmission only if the medium remains idle for this additional random time. • Stations select the number of slots at random out of an interval between (0 and contention window (CW)). Supporting QoS : 802.11e • This results in no mechanism to differentiate between stations and their traffic, and therefore no QoS support in the DCF. Supporting QoS : 802.11e • 802.11e introduces the enhanced dis- tributed channel access (EDCA), • The QoS support in EDCA is provided by the introduction of access categories (ACs) and multiple independent backoff entities. • The ACs are labelled according to their target application, i.e., AC_VO (voice), AC_VI (video), AC_BE (best effort), and AC_BK (background). • Here also arbitration interframe space (AIFS[AC]) is used instead of DIFS, which is used by legacy stations. • The smaller the AIFS[AC], the higher the medium access priority. Supporting QoS : 802.11e • The minimum size of the contention window, CWmin[AC], is another parameter dependent on the AC . • The smaller the CWmin[AC], the higher the priority in medium access. References • Anthony C.H. Ng,,David Malone,Douglas J. Leith, “Experimental Evaluation of TCP Performance and Fairness in an 802.11e Testbed”,SIGCOMM’05 Workshops, August 22–26, 2005. • Wei wang,soung chang liew,victor o. k. li, “solutions to performance problems in voip over 802.11 wireless lan 1 , IEEE transactions on vehicular technology, vol. 54, no. 1, january 2005. • Mirko Franceschinis, Marco Mellia, Michela Meo, and Maurizio Munafo. Measuring TCP over WiFi: A real case. Proceedings of the First Workshop on Wireless Network Measurements, Trentino, Italy, April 2005. • Sunghyun choi, stefan mangold, ” analysis of IEEE 802.11e for QoS support in wireless LANs “, IEEE wireless communications december 2003. • Chadi Barakat, Eitan Altman, and Walid Dabbous, “On TCP Performance in a Heterogeneous Network: A Survey”, IEEE Communications Magazine January 2000 • George Xylomenos and George C. Polyzos, TCP Performance Issues over Wireless Links, IEEE Communications Magazine. April 2001 References • Computer Networking: A Top Down Approach Featuring the Internet, 3rd edition.Jim Kurose, Keith Ross Addison-Wesley, July 2004. • 802.11® Wireless Networks: The Definitive Guide By Matthew Gast,Publisher : O'Reilly • Wireless LANs, Second Edition ,Copyright 2002 by Sams Publishing. • Cisco Building a Wireless LAN ,Eric Ouellet ,Robert Padjen ,Arthur P fund Ron Fuller Technical Editor ,Tim Blankenship Technical Editor • Wi-Fi Protected Access Data Encryption and Integrity Advanced Encryption Standard, Technical report, by Published: July 29, 2005, Microsoft References • S. Vangala and Miguel A. Labrador. Performance of TCP over Wireless Networks with the Snoop Protocol. In Proceedings of IEEE LCN, pages 600--601, Tampa, FL, November 2002. • http://www.wi-fiplanet.com/tutorials/article.php/2171721