* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Ağ Güvenliği - Dr. Mustafa Cem Kasapbasi
TCP congestion control wikipedia , lookup
Server Message Block wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Computer security wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Airborne Networking wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Wireless security wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Real-Time Messaging Protocol wikipedia , lookup
Distributed firewall wikipedia , lookup
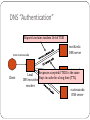
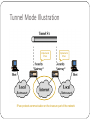
Ağ Güvenliği Hafta 5-6 Yrd. Doç.Dr. M.Cem KASAPBAŞI Partly extracted from Vitaly Shmatikov •CISSP study guide James Michael Stewart, Ed Tittel, Mike Chapple •“Network Security and Privacy” lecture notes of ISO Model, Protocols, Network Security, and Network Infrastructure TCP (Transmission Control Protocol) Sender: break data into packets Sequence number is attached to every packet Receiver: reassemble packets in correct order Acknowledge receipt; lost packets are re-sent Connection state maintained on both sides book slide 4 mail each page remember received pages and reassemble IP (Internet Protocol) Connectionless Unreliable, “best-effort” protocol Uses numeric addresses for routing Typically several hops in the route Alice’s computer Bob’s ISP Alice’s ISP 128.83.130.239 Packet Source 128.83.130.239 Dest 171.64.66.201 Seq 3 Bob’s computer slide 5 171.64.66.201 ICMP (Control Message Protocol) Provides feedback about network operation “Out-of-band” messages carried in IP packets Error reporting, congestion control, reachability, etc. Example messages: Destination unreachable Time exceeded Parameter problem Redirect to better gateway Reachability test (echo / echo reply) Message transit delay (timestamp request / reply) slide 6 Security Issues in TCP/IP Network packets pass by untrusted hosts Eavesdropping (packet sniffing) IP addresses are public Smurf attacks TCP connection requires state SYN flooding TCP state is easy to guess TCP spoofing and connection hijacking slide 7 Packet Sniffing Many applications send data unencrypted ftp, telnet send passwords in the clear Network interface card (NIC) in “promiscuous mode” reads all passing data network slide 8 Solution: encryption (e.g., IPsec), improved routing “Smurf” Attack Looks like a legitimate “Are you alive?” ping request from the victim 1 ICMP Echo Req Src: victim’s address Dest: broadcast address Every host on the network generates a ping (ICMP Echo Reply) to victim Stream of ping replies overwhelms victim gateway Solution: reject external packets to broadcast addresses slide 9 victim “Ping of Death” If an old Windows machine received an ICMP packet with a payload longer than 64K, machine would crash or reboot Programming error in older versions of Windows Packets of this length are illegal, so programmers of Windows code did not account for them slide 10 Solution: patch OS, filter out ICMP packets “Teardrop” and “Bonk” TCP fragments contain Offset field Attacker sets Offset field to overlapping values Bad implementation of TCP/IP stack will crash when attempting to re-assemble the fragments … or to very large values Target system will crash slide 11 Solution: use up-to-date TCP/IP implementation “LAND” Single-packet denial of service (DoS) attack IP packet with source address, port equal to destination address, port SYN flag set Triggers loopback in the Windows XP SP2 implementation of TCP/IP stack Locks up CPU slide 12 Solution: ingress filtering TCP Handshake C S SYNC SYNS, ACKC Listening… Spawn thread, store data (connection state, etc.) Wait ACKS Connected slide 13 SYN Flooding Attack S SYNC1 Listening… SYNC2 Spawn a new thread, store connection data SYNC3 … and more SYNC4 SYNC5 … and more … and more … and more … and more slide 14 SYN Flooding Explained Attacker sends many connection requests with spoofed source addresses Victim allocates resources for each request New thread, connection state maintained until timeout Fixed bound on half-open connections Once resources exhausted, requests from legitimate clients are denied This is a classic denial of service attack Common pattern: it costs nothing to TCP initiator to send a connection request, but TCP responder must spawn a thread for each request - asymmetry! slide 15 Preventing Denial of Service DoS is caused by asymmetric state allocation If responder opens new state for each connection attempt, attacker can initiate thousands of connections from bogus or forged IP addresses Cookies ensure that the responder is stateless until initiator produced at least two messages Responder’s state (IP addresses and ports of the con- nection) is stored in a cookie and sent to initiator After initiator responds, cookie is regenerated and compared with the cookie returned by the initiator slide 16 SYN Cookies C S SYNC Compatible with standard TCP; simply a “weird” sequence number scheme [Bernstein and Schenk] Listening… SYNS, ACKC Does not store state sequence # = cookie F=Rijndael or crypto hash F(source addr, source port, dest addr, dest port, coarse time, server secret) ACKS(cookie) More slide 17 info: http://cr.yp.to/syncookies.html Cookie must be unforgeable and tamper-proof (why?) Client should not be able to invert a cookie (why?) Recompute cookie, compare with with the one received, only establish connection if they match Anti-Spoofing Cookies: Basic Pattern Client sends request (message #1) to server Typical protocol: Server sets up connection, responds with message #2 Client may complete session or not (potential DoS) Cookie version: Server responds with hashed connection data instead of message #2 Client confirms by returning hashed data If source IP address is bogus, attacker can’t confirm Need an extra step to send postponed message #2, except in TCP (SYN-ACK already there) slide 18 Another Defense: Random Deletion SYNC half-open connections 121.17.182.45 231.202.1.16 121.100.20.14 5.17.95.155 If SYN queue is full, delete random entry Legitimate connections have a chance to complete Fake addresses will be eventually deleted Easy to implement slide 19 TCP Connection Spoofing Each TCP connection has associated state Sequence number, port number TCP state is easy to guess Port numbers standard, seq numbers predictable Can inject packets into existing connections If attacker knows initial sequence number and amount of traffic, can guess likely current number Guessing a 32-bit seq number is not practical, BUT… Most systems accept large windows of sequence numbers (to handle massive packet losses) Send a flood of packets with likely sequence numbers slide 20 “Blind” IP Spoofing Attack Trusted connection between Alice and Bob uses predictable sequence numbers SYN-flood Bob’s queue Alice Bob Open connection to Alice to get initial sequence number Send packets to Alice that resemble Bob’s packets Can’t receive packets sent to Bob, but maybe can penetrate Alice’s computer if Alice uses IP address-based authentication rlogin and other remote access tools use address-based authentication slide 21 DoS by Connection Reset If attacker can guess the current sequence number for an existing connection, can send Reset packet to close it Especially effective against long-lived connections For example, BGP route updates slide 22 User Datagram Protocol (UDP) UDP is a connectionless protocol Simply send datagram to application process at the specified port of the IP address Source port number provides return address Applications: media streaming, broadcast No acknowledgement, no flow control, no message continuation Denial of service by UDP data flood slide 23 Countermeasures Above transport layer: Kerberos Provides authentication, protects against application-layer spoofing Does not protect against connection hijacking Above network layer: SSL/TLS and SSH Protects against connection hijacking and injected data Does not protect against DoS by spoofed packets Network (IP) layer: IPsec Protects against hijacking, injection, DoS using connection resets, IP address spoofing We will study IPsec in some detail slide 24 DNS: Domain Name Service DNS maps symbolic names to numeric IP addresses (for example, www.cs.utexas.edu 128.83.120.155) www.cs.utexas.edu Client slide 25 Local DNS recursive resolver root & edu DNS server utexas.edu DNS server cs.utexas.edu DNS server DNS Root Name Servers Root name servers for top-level domains Authoritative name servers for subdomains Local name resolvers contact authoritative servers when they do not know a name Feb 6, 2007: DoS attack on root DNS servers slide 26 DNS Caching DNS responses are cached Quick response for repeated translations Other queries may reuse some parts of lookup NS records for domains DNS negative queries are cached Don’t have to repeat past mistakes For example, misspellings Cached data periodically times out Lifetime (TTL) of data controlled by owner of data TTL passed with every record slide 27 Cached Lookup Example ftp.cs.utexas.edu Client slide 28 Local DNS recursive resolver root & edu DNS server utexas.edu DNS server cs.utexas.edu DNS server DNS “Authentication” Request contains random 16-bit TXID www.cs.utexas.edu Client slide 29 root & edu DNS server utexas.edu Response accepted if TXID is the same Local DNS server DNS recursive Stays in cache for a long time (TTL) resolver cs.utexas.edu DNS server DNS Spoofing 6.6.6.6 Trick client into looking up host1.foo.com (how?) Guess TXID, host1.foo.com is at 6.6.6.6 Another guess, host1.foo.com is at 6.6.6.6 Another guess, host1.foo.com is at 6.6.6.6 host1.foo.com Client Local resolver Several opportunities to win the race If attacker loses, has to wait until TTL expires … but can try again with host2.foo.com, host3.foo.com, etc. … but what’s the point of hijacking host3.foo.com? slide 30 ns.foo.com DNS server Exploiting Recursive Resolving [Kaminsky] 6.6.6.6 Trick client into looking up host1.foo.com Guessed TXID, very long TTL I don’t know where host1.foo.com is Ask the authoritative server at ns2.foo.com It lives at 6.6.6.6 host2.foo.com host1.foo.com Client Local resolver If attacker wins, all future DNS requests will go to 6.6.6.6 The cache is now poisoned… for a very long time! No need to win future races! slide 31 ns.foo.com DNS server Triggering DNS Lookup Any link, any image, any ad, anything can cause a DNS lookup No Javascript required, though it helps Mail servers will look up what bad guy wants On first greeting: HELO On first learning who they’re talking to: MAIL FROM On spam check (oops!) When trying to deliver a bounce When trying to deliver a newsletter When trying to deliver an actual response from an actual employee slide 32 Reverse DNS Spoofing Trusted access is often based on host names E.g., permit all hosts in .rhosts to run remote shell Network requests such as rsh or rlogin arrive from numeric source addresses System performs reverse DNS lookup to determine requester’s host name and checks if it’s in .rhosts If attacker can spoof the answer to reverse DNS query, he can fool target machine into thinking that request comes from an authorized host No authentication for DNS responses and typically no double-checking (numeric symbolic numeric) slide 33 Internet/Intranet/Extranet Components Firewalls Other Network Devices Repeaters, concentrators, and amplifiers OSI layer 1 , strengthen the communication signal Hubs Bridges OSI layer 2 Switches OSI layer 2 OSI layer 3 (routing) VLANs Routers OSI layer 3 RIP, OSPF, and BGP Brouter Gateways Proxies An extranet for public consumption is typically labeled a demilitarized zone (DMZ) or perimeter network Firewalls Firewalls filter traffic based on a defined set of rules, also called filters or access control lists unable to block viruses or malicious code transmitted through otherwise authorized communication channels capable of hiding the structure and addressing scheme of a private network from the public prevent unauthorized but accidental or intended disclosure of information by users prevent attacks by malicious users already behind the firewall reports A reboot of the firewall Proxies or dependencies that cannot or didn’t start Proxies or other important services that have crashed or restarted Changes to the firewall configuration file A configuration or system error while the firewall is running many of the security mechanisms are concentrated in one place, and thus they may be a single point of failure Firewalls provide protection only against traffic that crosses the firewall from one subnet to another no protection behind a firewall TYPES static packet-filtering firewalls, application-level gateway firewalls, circuit-level gateway firewalls, stateful inspection firewalls. Static Packet-Filtering Firewalls filters traffic by examining data from a message header rules are concerned with source, destination, and port addresses unable to provide user authentication tell whether a packet originated from inside or outside the private network it is easily fooled with spoofed packets screening routers or common routers. first-generation firewalls; they operate at layer 3 Application-Level Gateway Firewalls proxy firewall copies packets from one network into another copy process also changes the source and destination addresses to protect the identity of the internal or private network filters traffic based on application used to transmit or receive the data. Each type of application must have its own unique proxy server so it comprises numerous individual proxy servers negatively affects network performance because each packet must be examined and processed as it passes through the firewall Second generation firewalls Osi layer 7 Circuit-Level Gateway Firewalls used to establish communication sessions between trusted partners Session layer (layer 5) of the OSI model also known as circuit proxies not the content of traffic permit or deny forwarding decisions based solely on the endpoint designations of the communication circuit (the source and destination addresses and service port numbers) Stateful Inspection Firewalls evaluate the state or the context of network traffic Examines source and destination addresses application usage source of origin relationship between current packets and the previous packets of the same session able to grant a broader range of access for authorized users and activities and actively watch for and block unauthorized users and activities Network and Transport layers (layers 3 and 4) Third genereation Multihomed Firewalls more than one interface to filter traffic should have IP forwarding disabled to force the filtering rules bastion host or a screened host = a firewall system logically situated between router and private network. All in bound traffic is routed to the bastion host DMZ= which is a network area (usually a subnet) that is designed to be accessed by outside visitors but that is still isolated from the private network of the organization. The DMZ is often the host of public web, email, file, and other resource servers Firewall Deployment Architectures single-tier, two-tier and three-tier (also known as multitier) Remote Access Security Management ability of a distant client to establish a communication session with a network thin-client connection (terminal)ü Modem RAS VPN through internet address the following issues: Remote connectivity technology DSL MODEM Transmission protection VPNs, SSL, TLS, Secure Shell (SSH), IPSec, and L2TP. Authentication protection (PAP) CHAP EAP RADIUS TACACS Remote user assistance Network and Protocol Security Mechanisms Secure Communications Protocols Simple Key Management for IP (SKIP) Software IP en cryption (SWIPE) Secure Remote Procedure Call (S-RPC) Secure Sockets Layer (SSL) Secure Electronic Transaction (SET) Dial-Up Protocols Point-to-Point Protocol (PPP) full-duplex transmitting TCP/IP packets over various non-LAN connections (modems, ISDN, VPNs, Frame Relay) PPP is a replacement for SLIP Serial Line Internet Protocol (SLIP) Authentication Protocols Challenge Handshake Authentication Protocol (CHAP) over PPP encrypts usernames and passwords Password Authentication Protocol (PAP) ppp PAP transmits usernames and passwords in the clear Extensible Authentication Protocol (EAP) framework customized authentication security solutions, such as supporting smart cards, tokens, and biometrics. Centralized Remote Authentication Services Remote Authentication Dial-In User Service (RADIUS) Terminal Access Controller Access Control System (TACACS) Avoiding Single Points of Failure Redundant Servers Failover Solutions Rollover /cold Rollover Network Attacks and Cuntermeasures harm includes more than just destruction or damage; it also includes disclosure, access delay, denial of access, fraud, resource waste, resource abuse, and loss Eavesdropping simply listening to communication traffic for the purpose of duplicating it usually requires physical access Cuntermeasures physical access security using encryption one-time authentication methods Second-Tier Attacks it is an attack that is launched only after some other attack is completed Impersonation/Masquerading one-time pads and token authentication systems, using Kerberos, and using encryption to increase the difficulty of extracting authentication credentials from network traffic Replay Attacks one-time authentication mechanisms and sequenced session identification. Modification Attacks digital signature verifications and packet checksum verification Address Resolution Protocol Spoofing Static ARP mappings for critical systems monitoring ARP caches for MAC-to-IP address mappings using an IDS DNS Spoofing only authorized changes to DNS restricting zone transfers All privileged DNS activity Hyperlink Spoofing Communications Security and Countermeasures Virtual Private Network (VPN) communication tunnel that provides point-to-point transmission of both authentication and data traffic over an intermediary untrusted network but encryption is not necessary can link two networks or two individual systems can link clients, servers, routers, firewalls, and switches provide confidentiality and integrity do not provide or guarantee availability. Tunneling network communications process that protects the contents of protocol packets by encapsulating them in packets of another protocol The Need for Tunneling bypassing firewalls, gateways, proxies, or other traffic control devices bypass is achieved by encapsulating the restricted content inside packets that are authorized for transmission often used to enable communications between otherwise disconnected systems SSL or TLS VoIP systems, Tunneling Drawbacks inefficient means of communicating using more than one protocol at a time compounds the overhead required to communicate a single message creates either larger packets or additional packets : network bandwidth not designed to handle broadcast traffic How VPNs Work can be established over any other network communication connection a client can perform the same activities and access the same resources connect two individual systems or two entire networks Remote access servers or firewalls on the network’s border act as the start points and endpoints for VPN Implementing VPNs often significantly less than the cost of any other connection means available. implemented using software or hardware solutions Four common VPN protocols: PPTP, L2F, L2TP, --layer 2--- and IPSec ---IP networks, L2F and L2TP can be used to encapsulate any LAN protocol PPTP point to point tunneling protocol PPTP is for dial-up protocol Point-to-Point Protocol (PPP). encapsulates PPP packets same authentication protocols supported by PPP Microsoft Challenge Handshake Authentication Protocol (MS-CHAP), Challenge Handshake Authentication Protocol (CHAP), Password Authentication Protocol (PAP), Extensible Authentication Protocol (EAP), Shiva Password Authentication Protocol (SPAP) initial tunnel negotiation process used by PPTP is not encrypted Layer 2 Tunneling Protocol (L2TP) Cisco developed Layer 2 Forwarding (L2F). L2F does not offer encryption. replaced by L2TP combining elements from both PPTP and L2F No built-in encryption scheme relies upon IPSec as its security mechanism supports TACACS+ and RADIUS but PPTP not IPSec (brief) 4 primary components or functions Authentication Header (AH) AH provides authentication, integrity, and nonrepudiation Encapsulating Security Payload (ESP) ESP provides encryption to protect the confidentiality of transmitted data it can also perform limited authentication Network layer (layer 3) be used in transport mode or tunnel mode transport mode:the IP packet data is encrypted but the header of the packet is not.. p2p In tunnel mode : the entire IP packet is encrypted and a new header is added to the packet to govern transmission through the tunnel..getway to getway Tunnel Mode Illustration Implements IPsec Implements IPsec IPsec protects communication on the insecure part of the network slide 63 Security Association (SA) One-way sender-recipient relationship Two SAs required for a two-way conversation SA determines how packets are processed Cryptographic algorithms, keys, IVs, lifetimes, sequence numbers, mode (transport or tunnel) – read textbook! SA is uniquely identified by SPI (Security Parameters Index)… Each IPsec implementation keeps a database of SAs SPI is sent with packet, tells recipient which SA to use …destination IP + protocol identifier (AH or ESP) slide 64 The IP Payload Compression (IPcomp) : protocol allows IPSec users to achieve enhanced performance by compressing packets prior to the encryption operation. The Internet Key Exchange (IKE) protocol provides for the secure exchange of cryptographic keys between IPSec participants accomplished through manual preshared keys or by a CA-controlled key distribution service (ISAKMP) IPsec: Network Layer Security IPcoIPsec = AH + ESP + mp + IKE Protection for IP traffic AH provides integrity and origin authentication ESP also confidentiality Compression Sets up keys and algorithms for AH and ESP AH and ESP rely on an existing security association Idea: parties must share a set of secret keys and agree on each other’s IP addresses and crypto algorithms Internet Key Exchange (IKE) slide 66 Goal: establish security association for AH and ESP If IKE is broken, AH and ESP provide no protection! IPsec two systems, two routers, two gateways, or any combination of entities Also individual computers, such as a server and a workstation or a pair of workstations primary use of IPSec isVPN Network Address Translation hiding the identity of internal clients masking the design of your private network keeping public IP address leasing costs to a minimum mechanism for converting Local addressPublic address It also provides protection by restricting connections so that only connections originating from the internal protected network are allowed back into the network from the Internet. So with NAT, you must lease as many public IP addresses as simultaneous communications you want to have PAT port addresss translation maps one internal IP address to an external IP address and port number combination 65,536 (232) simultaneous communications from internal clients over a single external leased IP address Private IP Addresses RFC 1918 Managing Email Security Simple Mail Transfer Protocol (SMTP) Post Office Protocol version 3 (POP3) Internet Message Access Protocol (IMAP) All Internet-compatible email systems rely upon the X.400 standard for addressing and message handling. Email Security Goals confidentiality, integrity, or even availability Email Security Issues protocols used to support email do not employ encryption first step recognize the vulnerabilities specific to email cripting languages, autodownload capabilities, and autoexecute features has transformed hyperlinks within the content of email and attachments into a serious threat to every system no native integrity checks to ensure that a message was not altered between its source and destination mail-bombing Email Security Solutions S/MIME Secure Multipurpose Internet Mail Extensions (S/MIME) public key encryption and digital signatures. X.509 digital certificates. 2 TYPES formed using signed messages and integrity authentication secured enveloped messages integrity authentication confidentiality MOSS MIME Object Security Services (MOSS) authenticity, confidentiality, integrity, and nonrepudiation for email messages MD2-.md5,RSA, DES PEM Privacy Enhanced Mail (PEM) provides authentication, integrity, confidentiality, and nonrepudiation RSA, DES, and X.509. PGP Pretty Good Privacy (PGP) IDEA algorithm not a standard pivate Securing Voice Communications important to implement mechanisms to provide for authentication and integrity Web security SSL/TSL Former SSL, later Transport Layer Security (TLS) developed by Netscape (HTTPS) uses port 443 to negotiate encrypted communications sessions between web servers and browser clients relies upon the exchange of server digital certificates to negotiate RSA encryption/decryption parameters between the browser and the web server. Secure HTTP Secure HTTP (S-HTTP) is the second major protocol used to provide security on the World Wide Web. SHTTP is not nearly as popular as SSL, but it has two major differences: S-HTTP secures individual messages between a client and server rather than creating a secure communications channel as SSL does. S-HTTP supports two-way authentication between a client and a server rather than the server-only authentication supported by SSL. Secure Electronic Transactions developed jointly by Visa and MasterCard SET utilizes a combination of RSA public key cryptography and DES private key cryptography in conjunction with digital certificates to secure electronic transactions. The original SET standard was published in 1997. SET is no longer used by anyone, anywhere