* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Slide 1
Survey
Document related concepts
TCP congestion control wikipedia , lookup
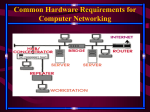
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Deep packet inspection wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
1 NET 536 NETWORK SECURITY Networks and Communication Department Introduction to the course Course objectives: 1 Analyze and address a number of situations in which security in networks can be compromised. Understand and apply selected technologies used to ensure security. Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed knowledge of TCP/IP. 25-May-17 Networks and Communication Department Topic to be covered Foundation of Network Security: what network security is? goals of network security, secure network architecture, network security policies, network security components Overview of TCP/IP protocol: TCP/IP architectural models, TCP protocol layers. TCP/IP possible attacks: packet sniffing, spoofing, process table attack. TCP/IP security components: packet rule, proxy server, VPN, SSL. IPSec IPSec architecture, benefits and limitations of IPSec. DNS overview of DNS, DNS security extensions. Topic to be covered Firewalls: Packet filtering, Stateful, and proxy firewalls Intrusion: intrusion prevention, intrusion detection (host based intrusion detection systems, network based intrusion detection systems) Application and transport layers security: (Pretty Good Privacy (PGP ), Secure Multipurpose Internet security Mail Exchange (S/MIME), Secure HTTP, Secure socket layer (SSL), transport layer security (TLS). Text books • William Stallings, ”Cryptography and Network Security”, Prentice Hall, The Latest Edition. • Behrouz A. Forouzan “ Data Communications and Networking”, McGrew-Hill, fourth edition,2007 • Computer security: art and science’, Matt Bishop, ISBN10:0201440997, 2002. • ‘Network Security, Firewalls, and VPNS’, Michael Stewart, 2nd Edition. ISBN: 9781284047431 Grade information 6 Comments 17/2/2015 Taking the average of the quizzes 17/3/2015 7/4/2015 14/4/2015 Percentage from overall grade Grade Assessment method (Write an essay - test - a collective project - a final test ...) 5% Quiz#1 5 4 15 7 15% Mid#1 5% 15% 10% 15% 40% 25-May-17 Assessment Week Quiz#2 5 10 15 12 10 3,6,9 15 13 40 After week 15 Mid#2 Lab Assignments Final lab Final Exam Networks and Communication Department Instructor Information 7 Office hours: Sun: 11:00-12:00 Mo: 11:00-2:00 Tu: 11:00-12:00 Thur: 11:00-12:00 Email : [email protected] Course website: net536.yolasite.com 25-May-17 Networks and Communication Department